
Fashionable organizations face mounting challenges in securing their public-facing belongings. From the rise of shadow IT to third-party provider exposures, the array of dangers and pitfalls in at this time’s digital environments make it almost inconceivable to keep up significant cyber resilience utilizing conventional protection strategies.
To remain forward of rising threats and preserve a powerful safety posture, safety groups are turning to exterior assault floor administration (EASM) as a key part of their digital danger safety technique.
This text examines the vital function EASM performs in digital danger safety (DRP), and the way safety groups can successfully use instruments like these to reinforce ongoing digital resilience efforts and mitigate potential vulnerabilities.
Bridging the hole
Safety groups nowadays are repeatedly tasked with managing complicated, sprawling public-facing digital assault surfaces that aren’t solely troublesome to handle, however typically laborious to totally perceive and map. This problem is amplified in hybrid environments, the place blurred strains of possession and accountability make efficient safety oversight much more troublesome.
Current information highlights simply how fragmented the fashionable digital footprint has turn into. Organizations now depend on a variety of applied sciences to assist their operations, however this variety typically results in visibility gaps and an elevated danger of publicity. With out clear and steady visibility into these increasing assault surfaces, vulnerabilities turn into simpler to miss – and for attackers to use.
Unsurprisingly, 83% of cyberattacks originate from exterior actors, lots of whom exploit weaknesses on the community perimeter. With Gartner naming EASM because the high cybersecurity development for the subsequent 5 to 10 years, it’s clear that managing these exterior entry factors has turn into a vital precedence for safety groups.
Understanding EASM
EASM is the continued observe of figuring out and addressing vulnerabilities and safety gaps throughout a corporation’s internet-facing digital footprint. Crucially, this entails the continual discovery, analysis, and mitigation of externally accessible assault vectors—lots of that are neglected in conventional safety approaches.
Key parts of an efficient EASM strategy embody:
- Asset Discovery – Mapping all public-facing digital belongings, together with web sites, purposes, cloud providers, and uncovered infrastructure parts.
- Vulnerability Evaluation – Evaluating IT belongings to uncover misconfigurations, outdated software program, or different weaknesses that could possibly be exploited. Common penetration testing mixed with EASM can also be essential for additional figuring out safety gaps that automated instruments or excessive stage scans might miss.
- Menace Intelligence – Amassing and analyzing information on rising threats and TTPs of risk actors to higher perceive potential dangers.
- Steady Monitoring – Sustaining real-time visibility to detect adjustments, new exposures, or indicators of malicious exercise as they happen.
Collectively, these parts allow safety groups to keep up a proactive safety posture by repeatedly decreasing publicity and staying forward of potential threats.
Achieve a constant and clear view of your ENTIRE organizations digital presence and any cyber threats hiding inside.
Outpost24s modern mixture of Cyber Menace Intelligence and Assault Floor Administration affords a full overview of exterior threats & dangers going through your group. This makes it simpler to prioritize threats and combat them proactively.
The significance of DRP
Whereas EASM is centered on uncovering vulnerabilities in public-facing IT belongings to strengthen a corporation’s safety posture, DRP takes a broader strategy by proactively figuring out and mitigating exterior threats that emerge from a corporation’s digital footprint—spanning public sources in addition to Social Media presence and deep and darkish net channels.
DRP improves cyber resilience by means of 4 key aims:
- Threat Identification – Detecting potential threats to digital belongings throughout varied exterior environments.
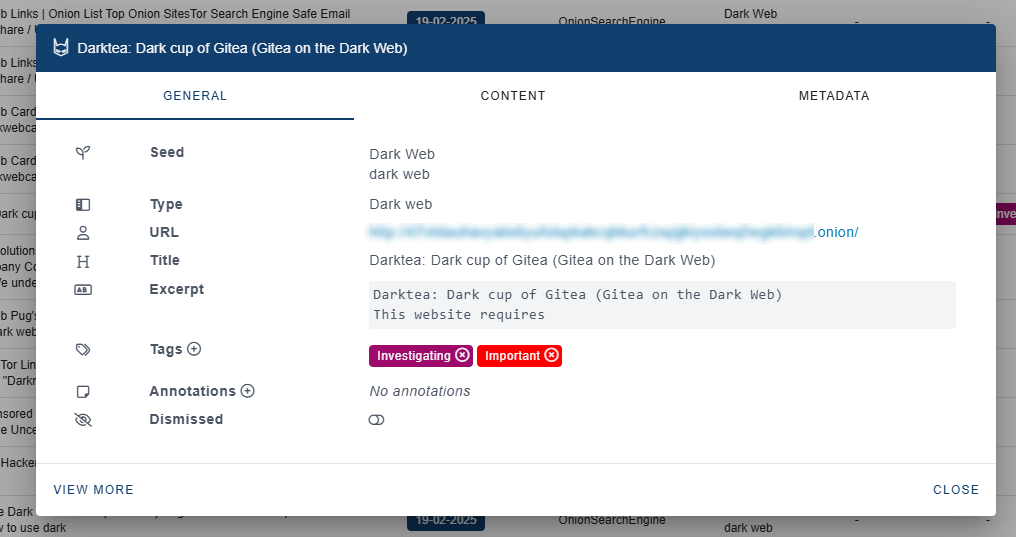
Detect and monitor Cyber Threat exterior of your owned belongings. - Threat Mitigation – Taking proactive steps to attenuate the chance and affect of recognized dangers.
- Compliance – Making certain ongoing alignment with regulatory and industry-specific necessities.
- Status Administration – Safeguarding the group’s model and public notion from reputational threats.
Collectively, these 4 aims allow organizations to proactively safeguard their digital belongings, decrease exterior threats, and preserve a resilient safety posture that protects each operational integrity and model repute.
How EASM will help improve DRP
By aligning DRP with EASM, safety groups can acquire a complete view of their exterior danger panorama —empowering them to reply swiftly, shield vital belongings, and uphold organizational belief in an more and more complicated risk setting.
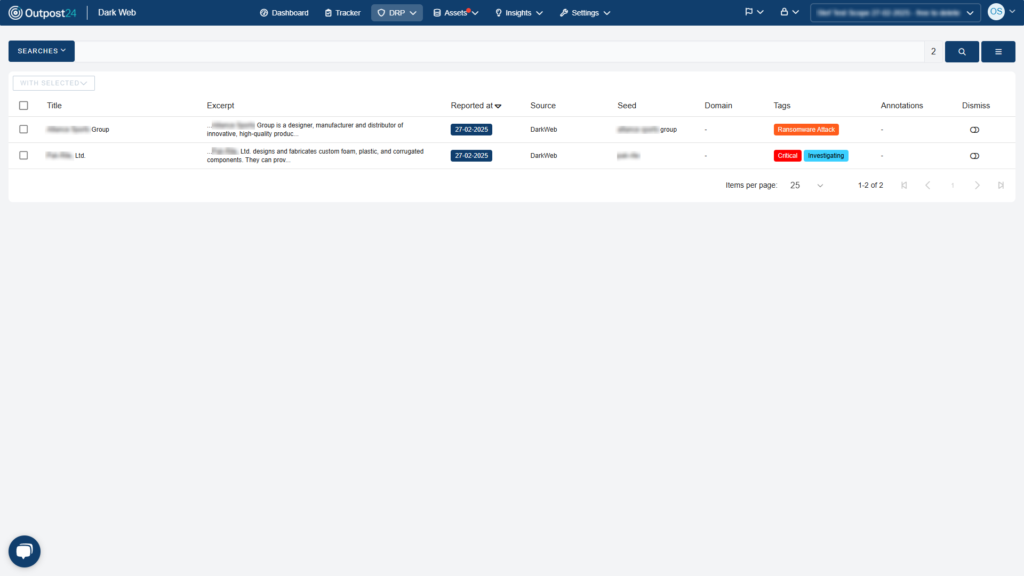
EASM enhances DRP by offering the next essential features:
Complete visibility
EASM supplies organizations with a complete view of their exterior assault floor, a vital aspect for efficient DRP. With clear visibility into all potential exposures, safety groups can higher safeguard towards cyber dangers, laying the inspiration for sturdy cyber resilience.
Proactive risk detection
Undetected safety gaps that elude safety groups are prone to be exploited by cyber attackers. By proactively figuring out and mitigating threats earlier than they are often leveraged by malicious actors, EASM helps decrease dangers that would result in cyberattacks and information breaches.
Threat prioritization
In a really perfect world, organizations would have limitless assets for cybersecurity. Nonetheless, the fact is that safety groups should deal with defending what issues most. EASM empowers them to prioritize dangers based mostly on their potential affect and chance, making certain assets are allotted the place they’re wanted most.
Incident response
Time is vital when responding to safety incidents, as swift motion is vital to limiting the affect of breaches and minimizing information exfiltration. EASM enhances incident response by offering real-time insights and actionable intelligence, enabling groups to behave rapidly and decisively.
Greatest practices for integrating EASM into DRP
To efficiently combine EASM into your DRP technique, contemplate adopting the next greatest practices:
Common assessments
Conduct common EASM assessments to remain forward of rising threats. Steady analysis of your exterior assault floor helps determine new vulnerabilities and permits for well timed mitigation earlier than these dangers are exploited.
Collaboration
Collaboration is vital to efficient EASM integration. Encourage common communication and cooperation between departments like IT, safety, and compliance. By working collectively, totally different groups inside the group can align their efforts and create a extra cohesive strategy to managing digital dangers.
Steady enchancment
Cyber threats are always evolving, so it’s essential to emphasise steady enchancment. Guarantee your EASM and DRP methods are adaptable to new threats, incorporating classes discovered from previous incidents to strengthen your safety posture over time.
Vendor choice
In deciding on an EASM vendor, it is best to contemplate your group’s particular wants and make sure that candidate options present the scalability, flexibility, and capabilities needed for complete assault floor administration.
You also needs to consider its risk intelligence integrations—a broader vary of integrations affords a extra unified strategy to DRP. As an illustration, Outpost24’s EASM answer combines information gathering, enrichment, and AI-driven evaluation right into a seamless, event-driven platform that gives essentially the most complete and actionable view of your assault floor.
To study extra, declare a free assault floor evaluation at this time.
Sponsored and written by Outpost24.


