
Twelve extra suspects had been charged in a RICO conspiracy for his or her alleged involvement within the theft of over $230 million in cryptocurrency and laundering the funds utilizing crypto exchanges and mixing companies.
Two different suspects linked to this conspiracy, 20-year-old Malone Lam (aka “Greavys,” “Anne Hathaway,” and “$$$”) and 21-year-old Jeandiel Serrano (aka “Field,” “VersaceGod,” and “@SkidStar”), had been arrested and charged in September 2024.
In response to court docket paperwork, Lam, Serrano, and others concerned within the scheme allegedly gained unauthorized entry to victims’ cryptocurrency accounts and transferred funds into crypto wallets they managed. In an August 18th assault, they stole over 4,100 Bitcoin from a Washington, D.C., sufferer (price greater than $230 million on the time).
Crypto fraud investigator ZachXBT, who assisted the FBI investigators, revealed that the group focused a creditor of the Genesis crypto change, utilizing spoofed telephone numbers and impersonating buyer assist at Google and Gemini.
Whereas posing as a Gemini assist consultant, they deceived the sufferer into resetting two-factor authentication (2FA) and sharing their display by way of AnyDesk (a distant desktop utility) after claiming the account had been compromised, which gave them entry to non-public keys from Bitcoin Core and allowed them to steal the goal’s cryptocurrency funds.
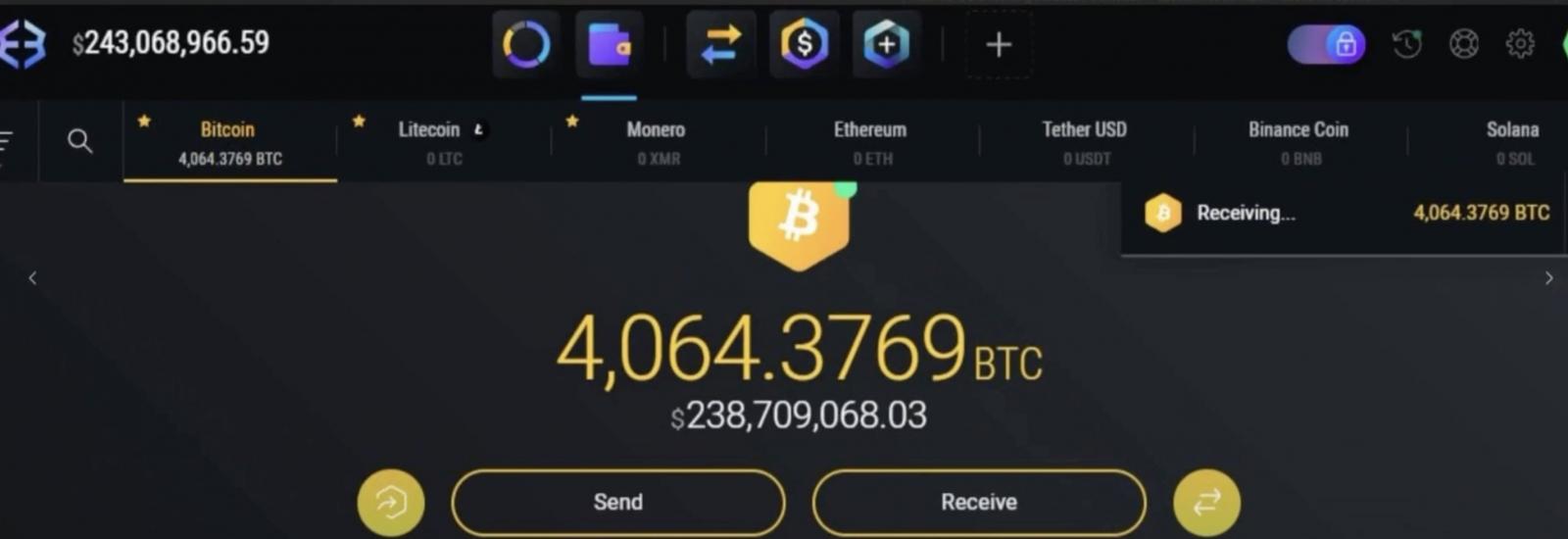
“An preliminary tracing confirmed $243M break up a number of methods between every get together earlier than funds rapidly peeled off to fifteen+ exchanges instantly swapping forwards and backwards between Bitcoin, Litecoin, Ethereum, and Monero,” ZachXBT stated.
Apart from cyber-enabled racketeering conspiracy and cash laundering, the next defendants, who had been indicted this week, additionally face fees of obstruction of justice and conspiracy to commit wire fraud:
- Marlon Ferro, 19 (Santa Ana, California)
- Hamza Doost, 21 (Hayward, California)
- Conor Flansburg, 21 (Newport Seaside, California)
- Kunal Mehta, 45 (Irvine, California)
- Ethan Yarally, 18 (Richmond Hill, New York)
- Cody Demirtas, 19 (Stuart, Florida)
- Aakash Anand, 22 (New Zealand)
- Evan Tangeman, 21 (Newport Seaside, California)
- Joel Cortes, 21 (Laguna Niguel, California)
- First Title Unknown-1, Final Title Unknown-1 aka “Chen” and “Squiggly” (location unknown)
- First Title Unknown-2, Final Title Unknown-2 aka “Danny” and “Meech” (location unknown)
- John Tucker Desmond, 19 (Huntington Seaside, California)
Whereas a lot of the stolen cryptocurrency belongings had been transformed to Monero for added anonymity, the attackers reportedly made some essential errors, linking the laundered funds to the unique stolen quantities.
They reportedly laundered the stolen cryptocurrency utilizing crypto mixers and exchanges, pass-through wallets, “peel chains,” and digital non-public networks (VPNs) to cover their identities and areas.
The stolen cryptocurrency was subsequently used to finance lavish existence, with the defendants allegedly spending the stolen funds on luxurious vehicles, high-end watches, designer purses, nightclub outings, and worldwide journey.
“Members and associates of the enterprise used the stolen digital foreign money to buy, amongst different issues, nightclub companies ranging as much as $500,000 per night, luxurious purses valued within the tens of 1000’s of {dollars} that got away at nightclub events, luxurious watches valued between $100,000 and $500,000,” U.S. Division of Justice prosecutors stated, in addition to “luxurious clothes valued within the tens of 1000’s of {dollars}, rental properties in Los Angeles, the Hamptons, and Miami, non-public jet leases, a group of personal safety guards, and a fleet of at the very least 28 unique vehicles ranging in worth from $100,000 to $3.8 million.”
“Members of the enterprise held completely different tasks. The assorted roles included database hackers, organizers, goal identifiers, callers, cash launderers, and residential burglars focusing on {hardware} digital foreign money wallets.”



