
TeleMessage, an Israeli firm that sells an unofficial Sign message archiving software utilized by some U.S. authorities officers, has suspended all companies after reportedly being hacked.
In accordance with info on the corporate’s official web site that has been partially eliminated, TeleMessage supplies messaging archiving companies for companies and authorities entities, together with instruments to archive messages exchanged by way of messaging apps like Telegram, WhatsApp, WeChat, and Sign.
Smarsh, the mother or father firm of TeleMessage, confirmed that each one TeleMessage companies have been suspended whereas it is investigating what it described as “a possible safety incident.”
“TeleMessage is investigating a possible safety incident. Upon detection, we acted shortly to include it and engaged an exterior cybersecurity agency to assist our investigation,” an organization spokesperson instructed BleepingComputer.
“Out of an abundance of warning, all TeleMessage companies have been quickly suspended. All different Smarsh services stay totally operational. We’re dedicated to transparency and can share updates as we’re ready. We thank our clients and companions for his or her belief and endurance throughout this time.”
The assertion is available in response to a request to substantiate a 404 Media report saying {that a} hacker breached TeleMessage and gained entry to direct messages and group chats archived utilizing TM SGNL, TeleMessage’s unofficial Sign clone, which former nationwide safety adviser Mike Waltz used for archiving Sign messages.
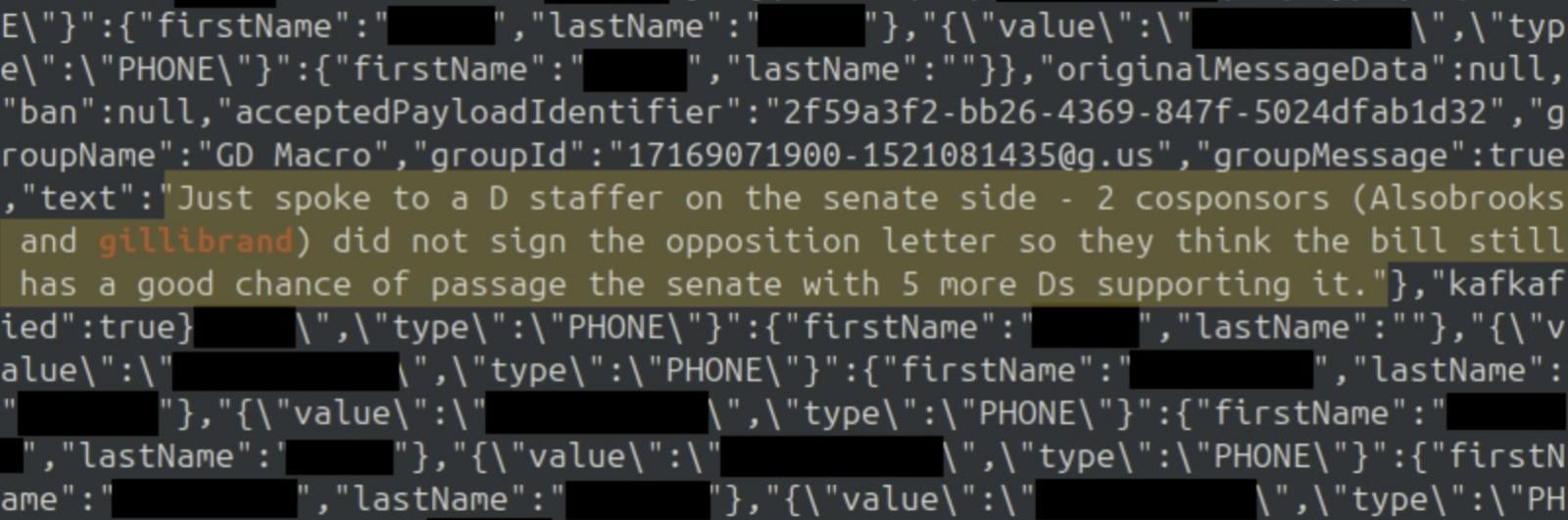
”I might say the entire course of took about 15-20 minutes. It wasn’t a lot effort in any respect,” the hacker instructed 404 Media. “If I may have discovered this in lower than half-hour then anyone else may too. And who is aware of how lengthy it has been susceptible?”
Based mostly on the hacker’s claims, messages of cupboard members and Waltz weren’t compromised; nevertheless, the extracted knowledge allegedly consists of authorities officers’ contact info, some message contents, and TeleMessage back-end login credentials.
Whereas messages from Trump administration officers weren’t uncovered within the breach, screenshots they shared hyperlink the stolen knowledge to the U.S. Customs and Border Safety, crypto trade Coinbase, and varied monetary companies reminiscent of Scotiabank.
Former The Intercept journalist and software program engineer Micah Lee additionally analyzed the supply code of TeleMessage’s TM SGNL backdoored Sign app and located a number of vulnerabilities, together with hardcoded credentials.
“We can not assure the privateness or safety properties of unofficial variations of Sign,” a Sign spokesperson instructed Reuters earlier this week, whereas White Home deputy press secretary Anna Kelly instructed NBC Information that “Sign is an authorised app for presidency use and is loaded on authorities telephones.”



