The UK Nationwide Cyber Safety Centre (NCSC) has formally attributed ‘Genuine Antics’ espionage malware assaults to APT28 (Fancy Bear), a risk actor already linked to Russia’s navy intelligence service (GRU).
The NCSC revealed in an in depth technical evaluation of the Genuine Antics malware dated Could sixth that it’s stealing credentials and OAuth 2.0 tokens that enable entry to a goal’s e-mail account.
The malware was noticed in use in 2023 and runs contained in the Outlook course of and produces a number of Microsoft login prompts in its makes an attempt to intercept the sufferer’s sign-in information and authorization code.
The company says that as a result of Microsoft 365 apps are configurable per tenant, it’s doable that delicate information additionally works for Trade On-line, SharePoint, and OneDrive.
Genuine Antics exfiltrates the stolen information by utilizing the sufferer’s personal Outlook account to ship it to an attacker-controlled e-mail tackle, and hides the operation by disabling the “save to despatched” possibility.
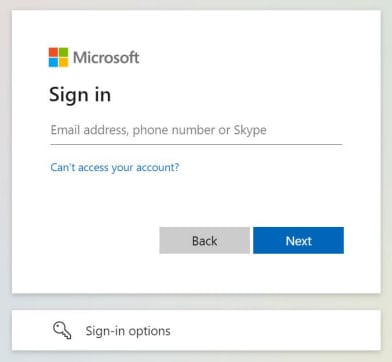
Supply: NCSC
Genuine Antics consists of a number of parts that embrace a dropper, an infostealer, and a number of other PowerShell scripts.
The UK cyber company says that Genuine Antics has a excessive stage of sophistication that permits it to present entry to sufferer e-mail accounts for lengthy durations with out being detected.
That is doable as a result of the malware’s community communication is just with professional providers. Moreover, because it sends the sufferer’s e-mail messages robotically to the attacker, it doesn’t require a command-and-control (C2) server to obtain duties.
“Its presence on disk is restricted, information is saved in Outlook particular registry areas,” the NCSC specialists say within the technical evaluation.
Attribution and sanctions
The NCSC did make any attribution for Genuine Antics however the company introduced at this time that it discovered proof that hyperlinks the malware to the APT28 state group, often known as Fancy Bear, Sednit, Sofacy, Pawn Storm, STRONTIUM, Tsar Group, and Forest Blizzard.
“The Authorities has at this time (July 18) uncovered Russian navy intelligence actors for utilizing beforehand unknown malicious software program to allow espionage in opposition to sufferer e-mail accounts, in a transfer that may preserve the UK and its allies safer,” UK’s NCSC says.
“The Nationwide Cyber Safety Centre – part of GCHQ – has revealed for the primary time that the cyber risk group APT 28 has been liable for deploying a classy malware dubbed AUTHENTIC ANTICS as a part of its operations.”
This attribution has additionally led to the UK Authorities sanctioning three GRU items (26165, 29155, and 74455) and 18 Russian people concerned in these and different associated campaigns.
UK officers condemned GRU brokers for conducting hybrid operations aimed toward destabilizing Europe and endangering British residents, additionally commending that the deployment of Genuine Antics displays a rising sophistication for the Russian intelligence service.
On the identical time, they underlined NCSC’s dedication to exposing these cyber actions and sanctioning the accountable events.
Genuine Antics has been utilized in assaults since



