Becoming a member of the Safety Operations Centre (SOC) staff in Cisco Dwell Melbourne was a brand new expertise for me as a Cisco Technical Advertising Engineer (TME). I primarily watched the SOC in operation in a number of earlier events Cisco Dwell, Black Hat and others and it was sufficient to look at the joy from exterior, becoming a member of them this time was a fantastic expertise, and I don’t assume watching will fulfill my pleasure anymore. I had the position to be a part of the Tier1 (Triage) /Tier 2 (Investigator) analyst staff incidents at first hand, on this weblog I’ll concentrate on few factors throughout this expertise:
- Onboarding: Getting onboard, accessing the instruments, verifying information, fixing integration
- Means of Escalation: SOC escalation course of
- Innovation: Develop and implement new integrations, processes, workflows, and automations
Getting onboarded in a SOC for any organisation is a giant job, however not with the Cisco SOC staff. Gaining access to the instruments took lower than 20 minutes, leveraging the only portal of Duo Listing to login to a lot of the cloud-based (and even on-prem) portals, XDR, Splunk and others made the onboarding expertise fast, straightforward and straight ahead.


The second section of the Onboarding was to get to know the instruments and the method to make use of when escalating.
- As a Tier1 / Tier 2 analyst the primary display to have a look at is Cisco XDR, that can carry incidents from the completely different information sources together with Splunk Core. The incidents are enriched menace intel and findings utilizing both native integrations or personalized workflows.
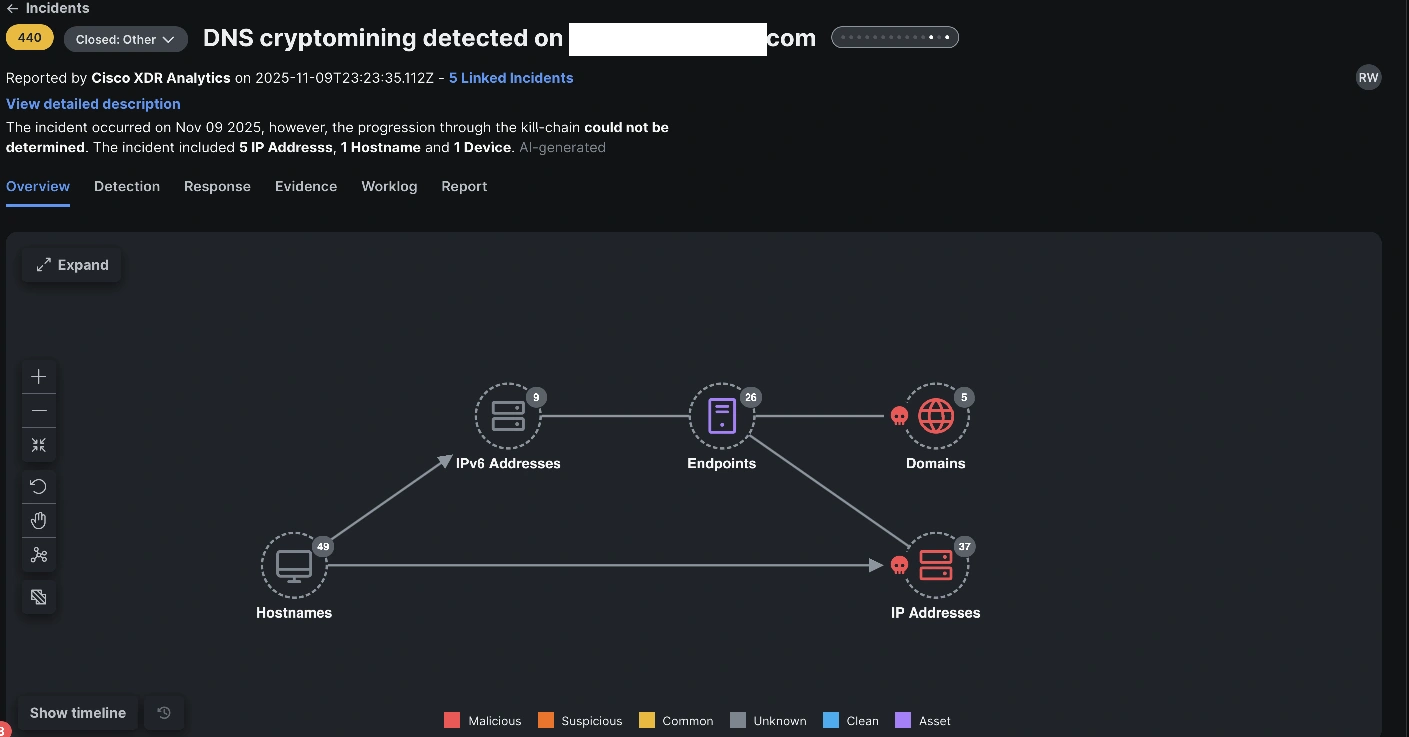

- Investigating begins inside the XDR Interface with the examine characteristic and pivots onto public instruments or personal instruments reminiscent of VirusTotal (for repute) or Endace (for community packet investigation and connection evaluation) relying on the suspected menace.
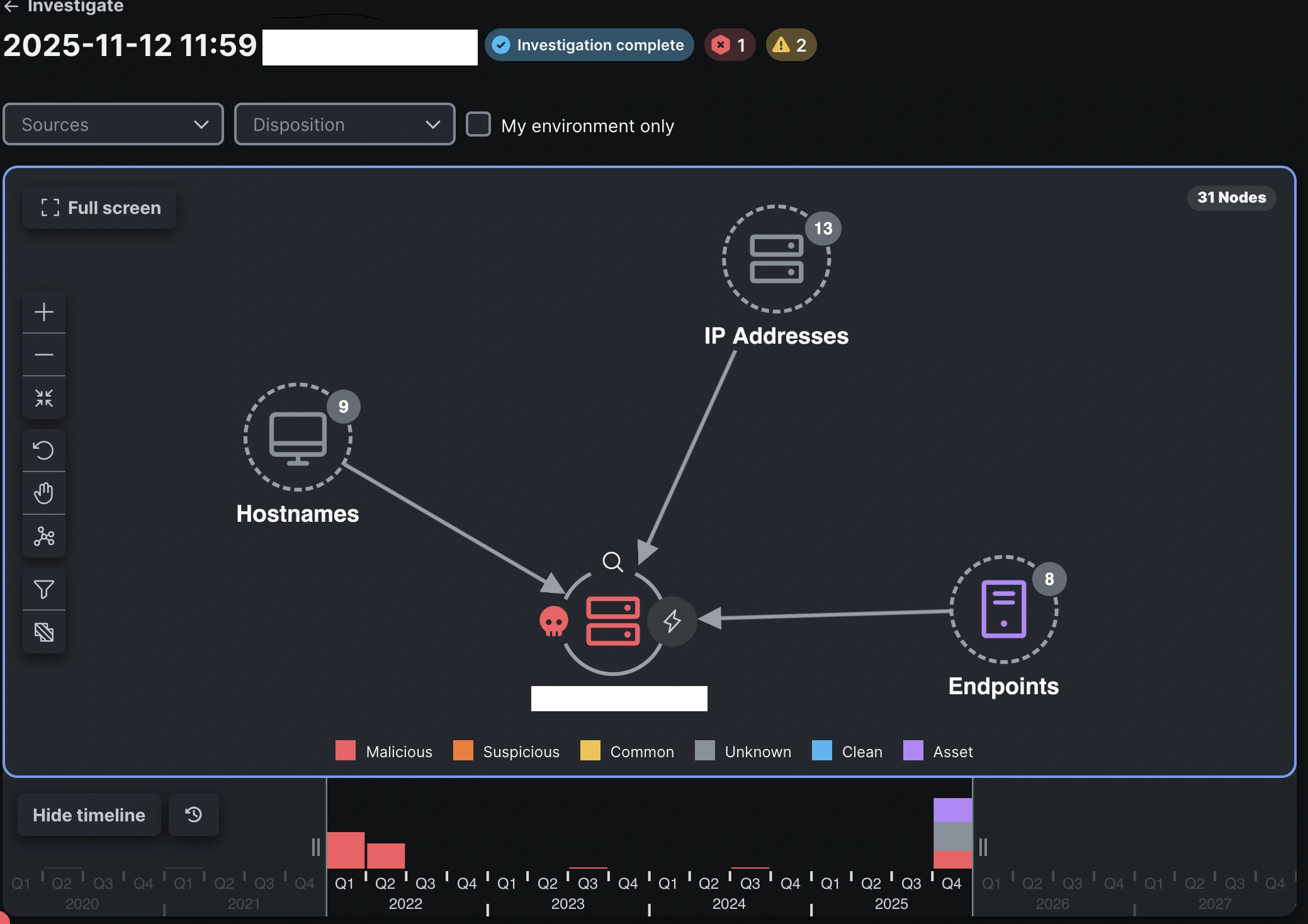

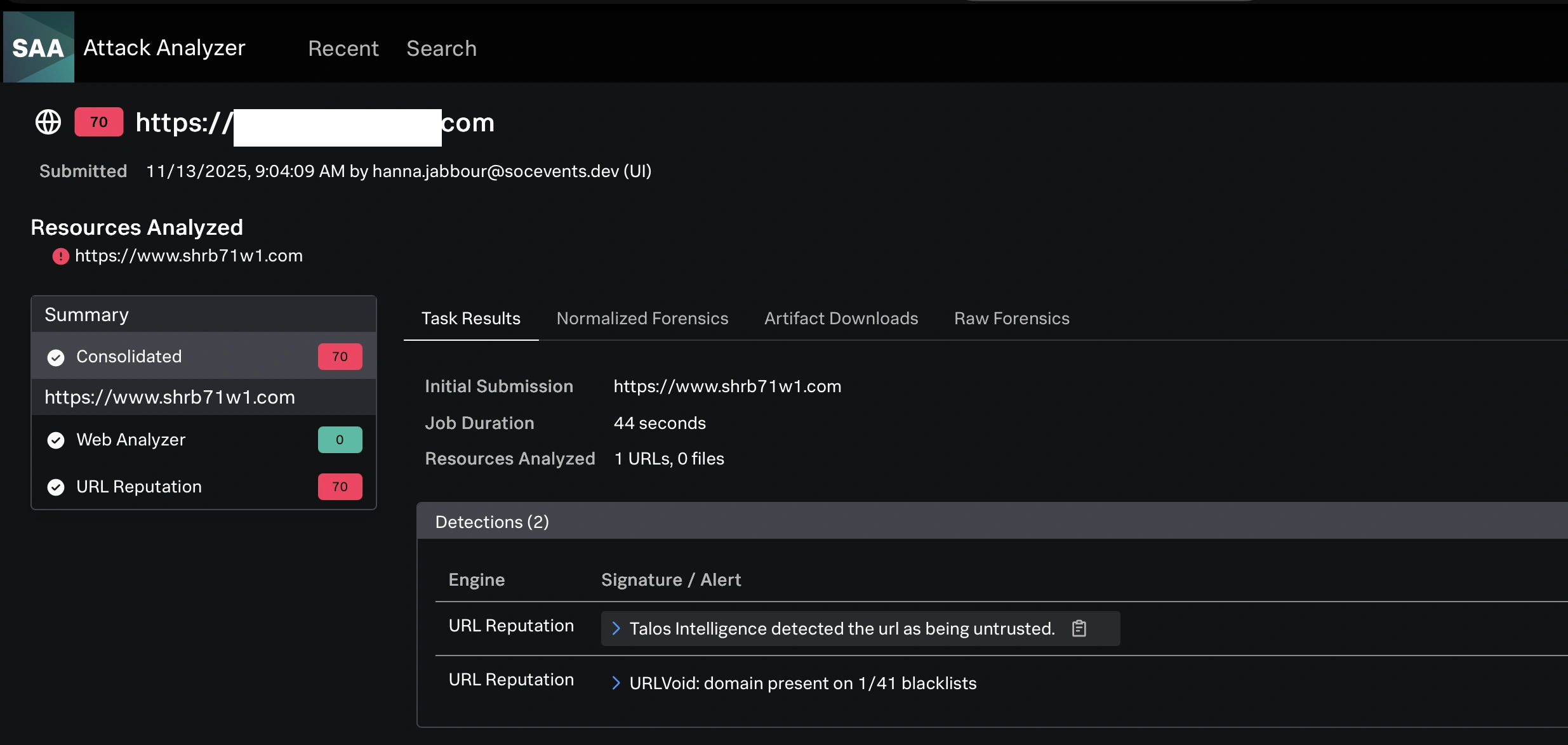

The important thing to that is how straightforward it was to find out how these instruments are leveraged and how briskly we acquired educated in lower than an hour on a typical incident response dealing with and course of. From the start of the onboarding to the tip it took lower than one hour and half earlier than we had been all set.
Escalation course of may be very properly outlined and observe a particular construction and collection of actions briefly summarized under:
- Investigated the incident in XDR, collect the data from all the opposite instruments that present extra context and visibility.
- Doc the incident and discovering in a structured predefined incident doc format for administration, submit it to a monitored Webex staff room.
- Launch an automation workflow in XDR to escalate the incident to the Tier 3 analyst staff, who had been utilizing Splunk Enterprise Safety.
That course of may be very properly outlined and structured in a means that makes anybody who walks into the SOC discover it straightforward to fill within the boots of a Tier 1/ Tier2 analyst very quickly, however most significantly present worth and be a productive member of this skilled group.
Day 1 at Cisco Dwell and guess what? Distributed Deniel of Service (DDoS) exercise was detected focusing on Cisco TV units related to Cisco Dwell community. Who would have thought that won’t occur?
- DDoS exercise detected: Discovering a DDoS Exercise focusing on Cisco TV units
- Confirmed origin of site visitors: investigating the origin and the affect of this DDos
- Escalation and Remediation: Escalation to NOC and remediation
Detecting DDoS at Cisco Dwell
Found on the primary day at Cisco Dwell, a repetitive variety of connections makes an attempt on port 443 for 3 property utilized by Cisco TV.


Trying on the firewall information, all these requests had been blocked each few seconds.
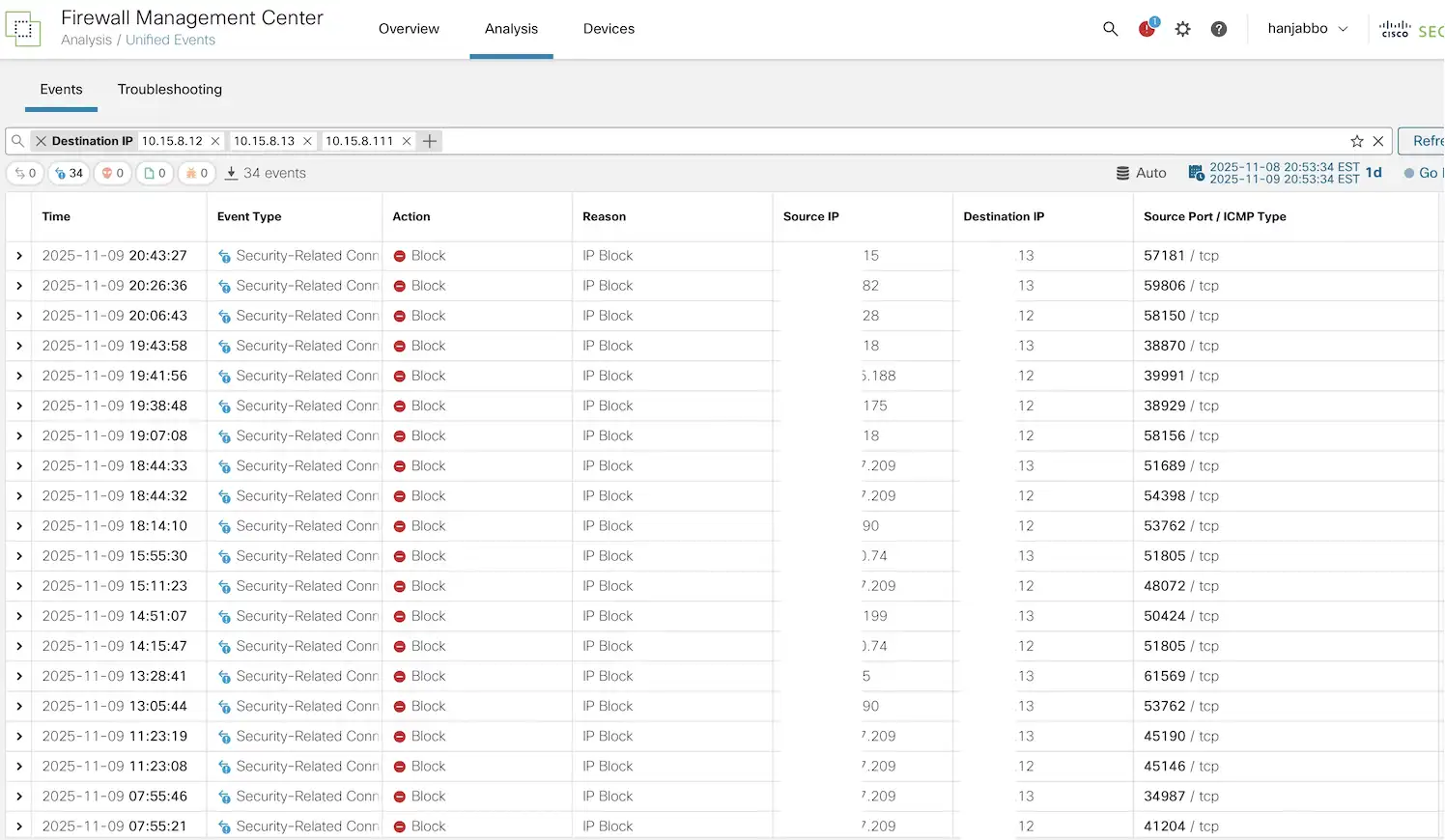

Trying additional forward we seen that the general public IPs focusing on these techniques come from international locations everywhere in the world: India, Germany, Bulgaria, Indonesia and plenty of others.
Investigating this additional to see if these three inner units havd any profitable connections from exterior, from comparable IPs. Utilizing Endace, we found a lot of the site visitors was DDoS associated and solely half open connections.
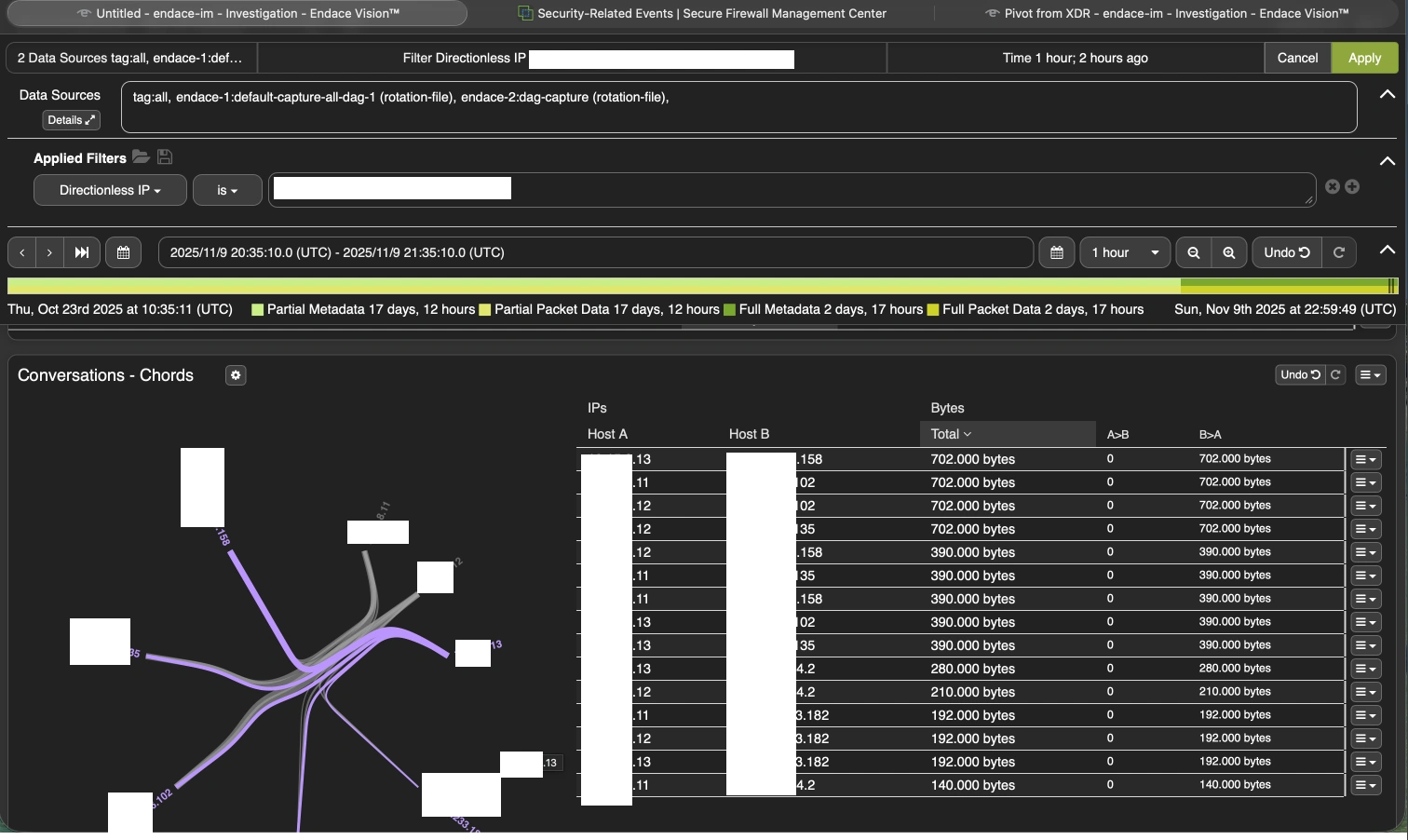

Every one among these IPs had a nasty repute from 4 or extra menace intelligence sources.
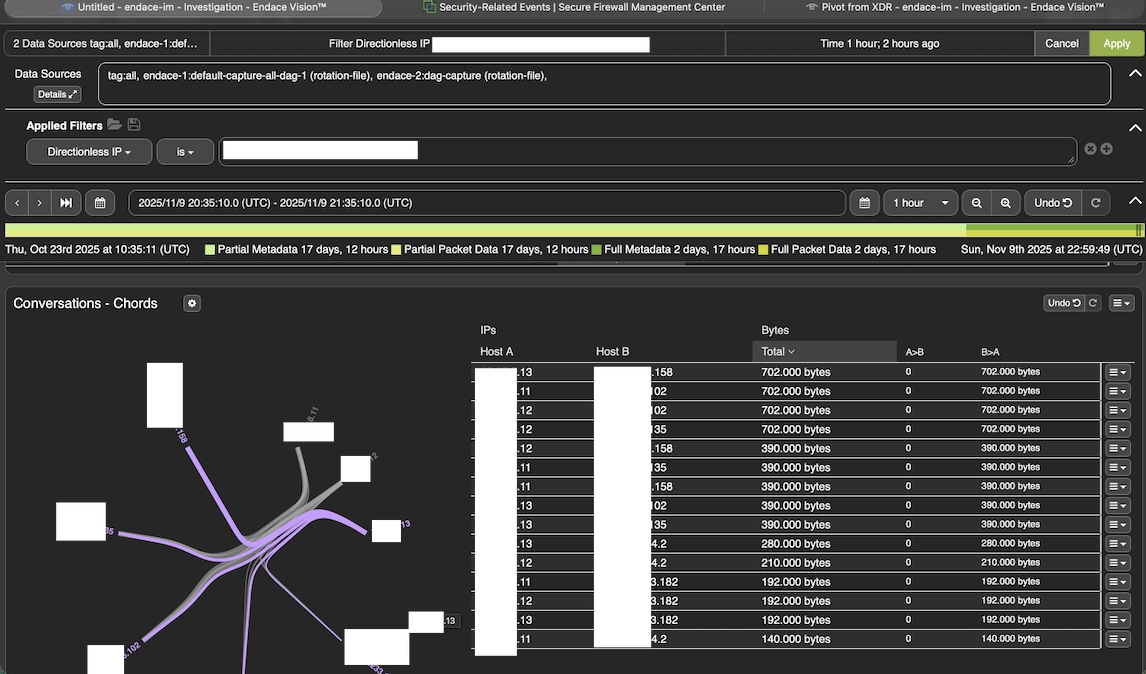

We adopted the escalation course of to establish the affect of such exercise. As soon as we knowledgeable the NOC staff, we had been advised that these units belong to the Cisco TV staff.
Cisco TV staff made the choice to close down these units, and shortly in any case DoS exercise stopped. Blissful days!
Whereas my focus on this engagement was to have a look at the SOC analyst expertise utilizing the Cisco and threerd get together instruments and discover the gaps that we will decrease by means of suggestions to engineering and product enhancements, I skilled first-hand the innovation that this staff is all the time exploring and producing from these engagement by making an attempt the “new” and exploring potentialities to facilitate the SOC work.


My greatest discovering on this involvement is how the expertise worth of this staff continues to prevail just isn’t within the instruments and never in working a SOC; however in how they embrace and empower the brand new SOC members and get them as much as a stage the place they’re environment friendly contributors of this success story, which retains on repeating and elevating with every step ahead.
You may as well be a contributing member of a SOC staff!
Try the opposite blogs by my colleagues within the Cisco Dwell APJC 2026 SOC.
We’d love to listen to what you assume! Ask a query and keep related with Cisco Safety on social media.
Cisco Safety Social Media


