
A safety researcher from Koi Safety stumbled upon a crucial zero-day buried deep within the infrastructure powering right this moment’s AI coding instruments. Had it been exploited, a non-sophisticated attacker might’ve hijacked over 10 million machines with a single stroke.
AI coding assistants like Cursor and Windsurf have exploded in recognition, promising supercharged productiveness for builders all over the world. Behind their smooth interfaces lies a shared basis: community-built VS Code forks and an open market of extensions that powers the magic. However, with this new wave of developer tooling comes a harmful blind spot.
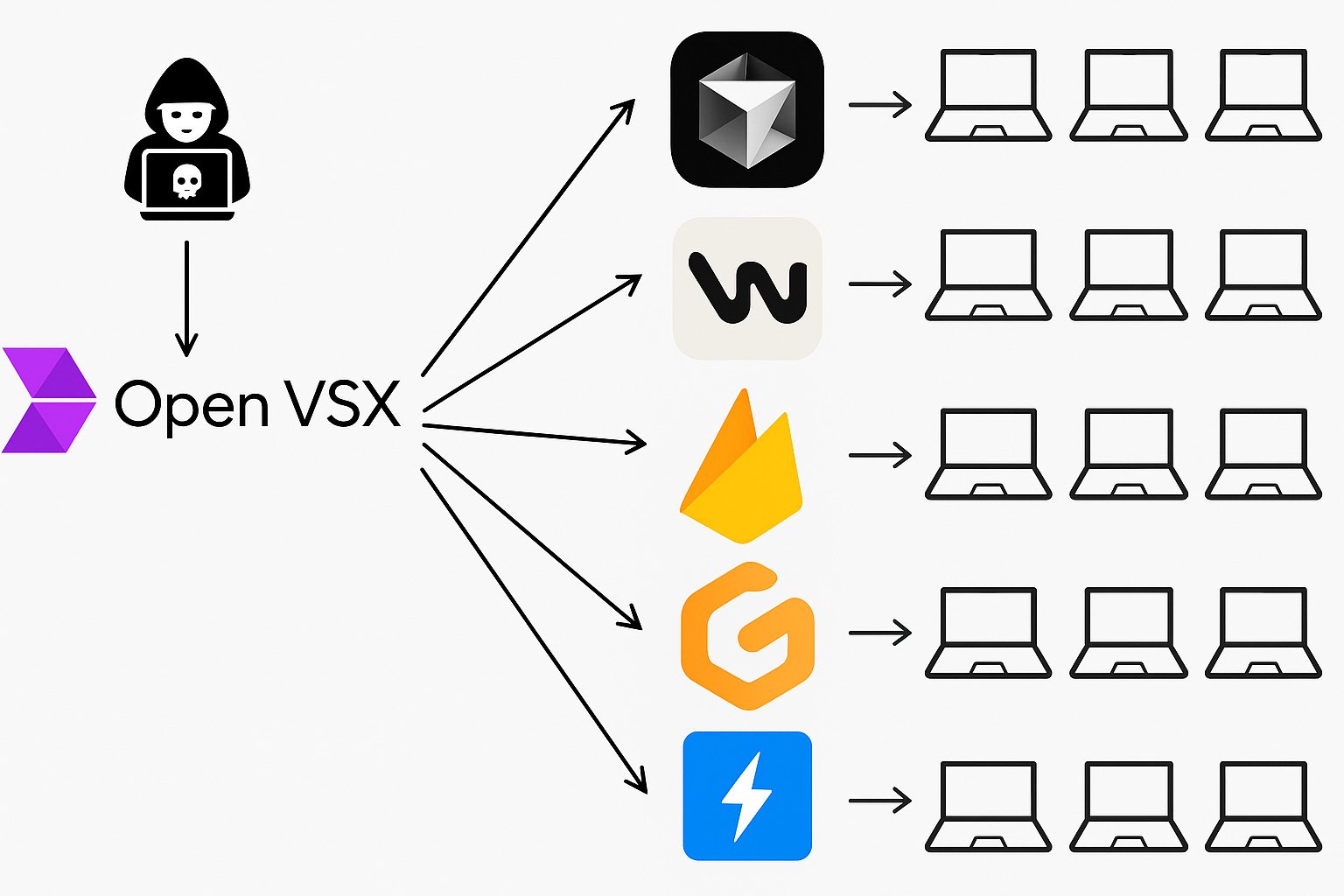
Dubbed VSXPloit: A single neglected flaw in OpenVSX – a crucial part within the developer provide chain – allowed silent, full-system compromise on any machine working a VS Code fork. One bug. Whole management.
Let’s dive in.
In the present day’s AI-powered editors closely depend on extensions to ship their most simple performance. Options like syntax highlighting, linting, and debugging aren’t hardcoded into the editor – they’re offered by extensions.
Every of those extensions runs with full privileges on the developer’s machine. This in flip signifies that a single compromised extension can result in full machine takeover of anybody who installs it.
This actual nightmare situation is what safety researcher Oren Yomtov from Koi Safety, an organization offering a platform for securing software program provisioning and extensions, stumbled upon.
In a latest put up Yomtov explains that whereas analyzing the construct course of behind OpenVSX, the open-source market powering extensions for instruments like Cursor, Windsurf, VSCodium, and others, he found a crucial flaw.
The vulnerability allowed any attacker, not solely to realize management over a single extension, however an provide chain armageddon, gaining full management over your complete market.
Given this flaw, any attacker might push malicious updates below the trusted @open-vsx account. At first, Yomtov assumed it needed to be a mistake, this code had been working for years, utilized by tens of thousands and thousands. However when he recreated the assault in his lab, the simulation labored flawlessly.
What appeared unthinkable was out of the blue very actual: a silent, full-scale safety catastrophe was sitting in plain sight.
Find out how Koi helps organizations uncover, assess, and govern dangerous extensions throughout VSCode, OpenVSX, Chrome, and different marketplaces.
Achieve full visibility and defend your growth provide chain.
The Vulnerability: A Variation On The Traditional “Pwn Request”
To know how the vulnerability labored, you first want to know how extensions make their approach into OpenVSX within the first place.
If you wish to publish an extension to Open VSX, you may have two choices:
-
Add it to Open VSX your self
-
Request an extension to be auto-published by making a pull request that provides the extension to the record within the extensions.json file
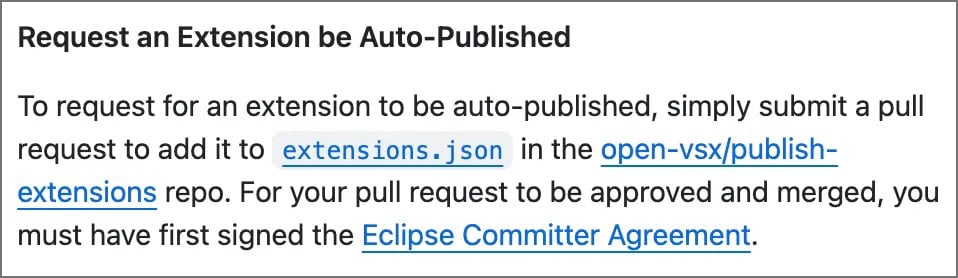
“The nightly construct is the place the issue lies,” says Yomtov.
Each night time, OpenVSX runs an automatic course of that fetches the most recent variations of community-submitted extensions, builds them, and publishes them to {the marketplace}. It’s meant to make life simpler for builders, however on this case, it launched a crucial flaw.
To get an extension auto-published, all a developer has to do is submit a easy pull request including it to a public record. From there, OpenVSX takes over: it pulls the code, installs the dependencies, builds the extension, and publishes it utilizing a strong secret token that belongs to the trusted @open-vsx account.
This token was meant to remain hidden, solely seen by trusted infrastructure. Sadly, on account of how the construct course of runs arbitrary code from public repositories, any extension creator might craft a malicious replace that silently captures the token.
What’s much more alarming is that they wouldn’t have to submit a malicious extension straight. They might have hidden their code inside a dependency, or perhaps a dependency-of-a-dependency, and the system would have executed it robotically through the nightly construct. From there, stealing the token was trivial.
And with that token in hand, an attacker wouldn’t simply management their very own extension. They might publish updates, overwrite present ones, and silently hijack your complete market.
The Impression: A Provide-Chain Nightmare That Uncovered Tens of millions of Builders
With entry to the @open-vsx account’s token, an attacker might have created a world huge provide chain nightmare. “That token is a super-admin credential,” explains Yomtov. “It will possibly publish new extensions, overwrite present ones, and impersonate any writer within the ecosystem.”
From that time on, the injury turns into nearly easy. Each time a developer installs an extension or their editor auto-updates one within the background, which repeatedly occurs, the attacker’s payload can be silently delivered to their machine. No alerts. No prompts. No suspicion. Full takeover.
And what might that payload do? “Just about something,” says Yomtov. Extensions in VS Code and its forks run as Node.js processes, which suggests they’ll entry information, launch different applications, make community requests, and execute arbitrary code.
A malicious replace to a well-liked extension, say, the Python plugin, might quietly set up a keylogger, steal browser cookies, swipe supply code, infect builds, or backdoor total growth pipelines.
There have been remoted circumstances of rogue VS Code extensions stealing SSH keys or crypto wallets. However this wouldn’t be one dangerous actor slipping via the cracks. This might be full-scale takeover, supply-chain compromise at ecosystem scale. Like SolarWinds, however for developer instruments.
Whereas the influence can be most extreme for desktop editors like Cursor, Windsurf, and VSCodium, even browser-based environments resembling Gitpod or StackBlitz may very well be affected, relying on how deeply built-in the compromised extensions are.
So What Can You Do About It?
We requested Yomtov what customers and organizations ought to take away from this incident. His reply was blunt: “Assume each extension is untrusted till confirmed in any other case.”
Extensions might really feel like innocent add-ons, however below the hood, they’re highly effective software program elements, usually written by people, working with full permissions, and robotically up to date with out oversight.
“It’s no totally different than pulling in a package deal from npm or PyPI, and customarily even worse” Yomtov says. “If you happen to wouldn’t blindly belief a GitHub repo with root entry to your machine, you shouldn’t belief an extension both.”
To guard ourselves, Yomtov recommends organizations deal with extensions as a part of their assault floor and apply the identical self-discipline they use for some other dependency. Which means:
-
Sustaining an actual stock of what’s put in, throughout which machines, and by whom
-
Assessing danger based mostly on who constructed the extension, the way it’s maintained, and what it really does
-
Imposing clear insurance policies round what’s allowed, and taking motion when one thing drifts out of bounds
-
Monitoring repeatedly, since extensions can replace silently and introduce new dangers in a single day
Koi’s analysis group continues to discover each susceptible and actively malicious extensions – not simply in OpenVSX,or Microsoft’s market, even in different extension marketplaces just like the Chrome Internet Retailer.
“The ecosystem has grown sooner than the guardrails,” says Yomtov. “Till that adjustments, the most secure assumption is zero belief. Each extension is a possible backdoor until you’ve reviewed and are watching it.”
Yomtov and the group at Koi Safety responsibly disclosed the vulnerability to the Eclipse Basis, which maintains the OpenVSX challenge. Over the next weeks, they labored intently with the maintainers to validate the difficulty, design a sturdy repair, and make sure the patch was correctly applied and deployed.
Because of this collaboration, the vulnerability has been closed and {the marketplace} is as soon as once more secure for the thousands and thousands of builders who depend on it day by day.
However the incident serves as a wake-up name – even trusted infrastructure wants fixed scrutiny, particularly when it holds the keys to your complete growth ecosystem.
Find out how Koi helps organizations uncover, assess, and govern dangerous extensions throughout VSCode, OpenVSX, Chrome, and different marketplaces
Chat with us.
Sponsored and written by Koi Safety.


