Welcome to Tech Speak, a weekly column concerning the issues we use and the way they work. We attempt to hold it easy right here so everybody can perceive how and why the gadget in your hand does what it does.
Issues could turn out to be a little bit technical at instances, as that is the character of know-how — it may be complicated and complex. Collectively we are able to break all of it down and make it accessible, although!
Tech Speak

The way it works, defined in a manner that everybody can perceive. Your weekly look into what makes your devices tick.
You won’t care how any of these things occurs, and that is OK, too. Your tech devices are private and must be enjoyable. You by no means know although, you may simply be taught one thing…
What’s malware?

it is one thing dangerous, however do you actually know what malware is? It is in all probability not precisely what you are pondering.
Malware is outlined as any software program designed to disrupt or exploit a tool, a community, or information on both. Some shady bootleg app that steals your financial institution data is malware, however below this definition, so is Chrome or Microsoft Edge. It’s essential to go one step additional and describe malware as a factor that does this with out your permission.
The best approach to describe it’s with a easy instance: a boring flashlight app. You obtain and set up a flashlight app to do just one factor: flip in your digicam flash whenever you faucet the icon. To do that, the app solely wants entry to the fundamentals — a capability to take consumer enter and ship a request to toggle the flash on and off.
Now think about the identical app, however this time it desires to entry your contacts. It does not supply any form of group entry to your digicam flash and does not have a purpose for doing it. It simply does and you don’t have any thought why. That is malware. It is planning on doing one thing together with your information, possibly sooner or later, however the essential factor is that it is making an attempt to do issues it does not must do. Substitute some other information on your contacts and the state of affairs is identical.
How does malware unfold?
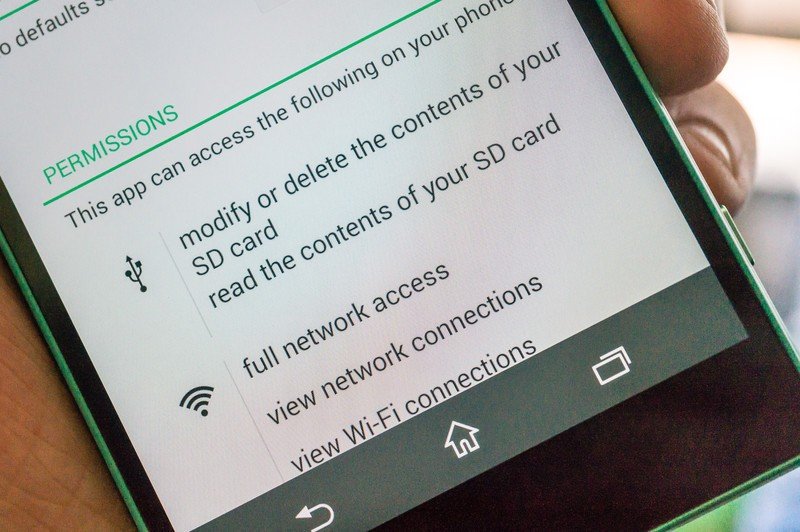
Fortunately, it’s totally troublesome for any software to do what’s described above in secret. Sadly, it in all probability does not should be secretive since you by no means appeared to see what else the app tells you it’ll do down in its wonderful print.
A technique malware is distributed is by counting on you to simply accept all of the issues an app can do with out studying something. Nonetheless, this technique solely works for apps that comply with the difficult and infrequently foolish platform distribution guidelines. And sure, that flashlight app state of affairs occurred on each Android and iOS, in every official app retailer; it adopted the principles, so it was allowed to on the time.
Social engineering (getting you to click on sure, realizing you will not learn all of it is social engineering on the lowest stage) might be the commonest approach to unfold malware. If I can construct an app that does issues it should not, I nonetheless would wish a approach to have you ever set up it. Trickery works as a result of most individuals do not understand the hurt that may come up from their easy actions. You may compromise your data, your family and friends’s data, and even the data of different gadgets utilizing the identical community as you. All you must do is click on sure.
A scarier manner of spreading malware is by exploiting bugs in your cellphone’s OS and putting in software program with out your information. Perhaps you go to the mistaken web site, strive pirating websites for “free” paid apps, and even connect with the mistaken open Wi-Fi community. These are methods malware can discover its manner onto your machine.
As soon as in place, this form of malware could cause severe points. Governments of the world even strive it, so it may monitor the folks they suppose should be monitored as a result of it is highly effective and normally undetectable.
What can I do to attempt to forestall all this?

Fortunately, it is not that troublesome to guard your self. You would set up one of many many malware scanners accessible and hope it catches any and every thing, however you additionally must comply with a couple of easy guidelines should you simply need issues to be simple and malware-free.
Solely use the official app retailer that got here together with your cellphone. Your cellphone comes with at the very least one approach to discover and set up apps to do enjoyable and funky issues with. These shops aren’t good, however they’re 1,000,000 instances higher at catching and eradicating malware earlier than it may get to you than some other distribution mannequin. Apple exams each app earlier than it is positioned within the retailer, whereas Google makes positive the app follows the principles earlier than it is made accessible, after which scans each app earlier than it will get put in in your cellphone. Samsung, Epic, and different app markets even have safeguards in place to verify they don’t seem to be spreading dangerous apps.
By no means click on sure earlier than you learn what you are agreeing with. This cannot be careworn sufficient! These consumer agreements are horrible and infrequently filled with language designed to present one social gathering a bonus within the case of a dispute however drive your self to learn by way of them each single time. You won’t like your choices; you may both must conform to the phrases introduced or not use an app, a service, or perhaps a machine itself. No person desires to place their Galaxy S25 again within the field to ship to Samsung as a result of they do not need Samsung to research the best way they use it, however these are the principles. As soon as you have stated sure, they will and can do what they requested permission to do. Be sure to’re OK with all of it by studying what’s put in entrance of you. (Editor’s be aware: You may belief corporations like Samsung, Apple, and even Google to do solely what they are saying they may do with something they acquire out of your cellphone, so do not let that scare you off.)

All the time settle for updates. If you purchase a tool you are given a promise of software program assist for a selected period of time. An enormous a part of that assist is patching the bugs and exploits used to hijack your cellphone or set up dangerous apps with out your information. Belief that corporations like Google and Apple know what they’re doing but in addition settle for that different sensible individuals are looking for methods to defeat each safety you have got. Exploits will occur and when these get patched, you’ll want to set up the replace immediately.
By no means belief something with out verifying it first. That is the toughest half. Is that message actually out of your little brother asking for $200 or saying he forgot the gate code or is it from another person? Be sure that. The identical goes for any hyperlinks you come throughout — are you positive you may belief them? Be very cautious utilizing public Wi-Fi networks, too. It is simple to make one (you may do it proper in your cellphone!) and with the precise instruments every thing despatched on them may be collected: passwords, 2FA data, bank card data, and so forth. Taking a minute to be sure to know the who and what is loads simpler than making an attempt to repair every thing after somebody steals your id or your bank card quantity.
Actually, it is not as arduous because it sounds to guard your self. It is also not foolproof — anybody can find yourself with malware, even safety professionals or authorities officers with safety groups. Doing all your half makes it loads more durable.


