
Microsoft warns {that a} risk actor tracked as Storm-0501 has developed its operations, shifting away from encrypting units with ransomware to specializing in cloud-based encryption, information theft, and extortion.
The hackers now abuse native cloud options to exfiltrate information, wipe backups, and destroy storage accounts, thereby making use of strain and extorting victims with out deploying conventional ransomware encryption instruments.
Storm-0501 is a risk actor who has been lively since at the least 2021, deploying the Sabbath ransomware in assaults towards organizations worldwide. Over time, the risk actor joined numerous ransomware-as-a-service (RaaS) platforms, the place they used encryptors from Hive, BlackCat (ALPHV), Hunters Worldwide, LockBit, and, extra just lately, Embargo ransomware.
In September 2024, Microsoft detailed how Storm-0501 prolonged its operations into hybrid cloud environments, pivoting from compromising Lively Listing to Entra ID tenants. Throughout these assaults, the risk actors both created persistent backdoors via malicious federated domains or encrypted on-premises units utilizing ransomware, comparable to Embargo.
A brand new report by Microsoft right this moment outlines a shift in ways, with Storm-0501 now not counting on on-premises encryption and as an alternative conducting assaults purely within the cloud.
“In contrast to conventional on-premises ransomware, the place the risk actor usually deploys malware to encrypt essential recordsdata throughout endpoints inside the compromised community after which negotiates for a decryption key, cloud-based ransomware introduces a elementary shift,” reads the report by Microsoft Menace Intelligence.
“Leveraging cloud-native capabilities, Storm-0501 quickly exfiltrates giant volumes of knowledge, destroys information and backups inside the sufferer atmosphere, and calls for ransom—all with out counting on conventional malware deployment.”
Cloud-based ransomware assaults
In current assaults noticed by Microsoft, the hackers compromised a number of Lively Listing domains and Entra tenants by exploiting gaps in Microsoft Defender deployments.
Storm-0501 then used stolen Listing Synchronization Accounts (DSAs) to enumerate customers, roles, and Azure sources with instruments comparable to AzureHound. The attackers finally found a World Administrator account that lacked multifactor authentication, permitting them to reset its password and acquire full administrative management.
With these privileges, they established persistence by including malicious federated domains underneath their management, enabling them to impersonate virtually any person and bypass MFA protections within the area.
Microsoft says they escalated their entry additional into Azure by abusing the Microsoft.Authorization/elevateAccess/motion, which allowed them to in the end assign themselves to Proprietor roles, successfully taking up the sufferer’s total Azure atmosphere.
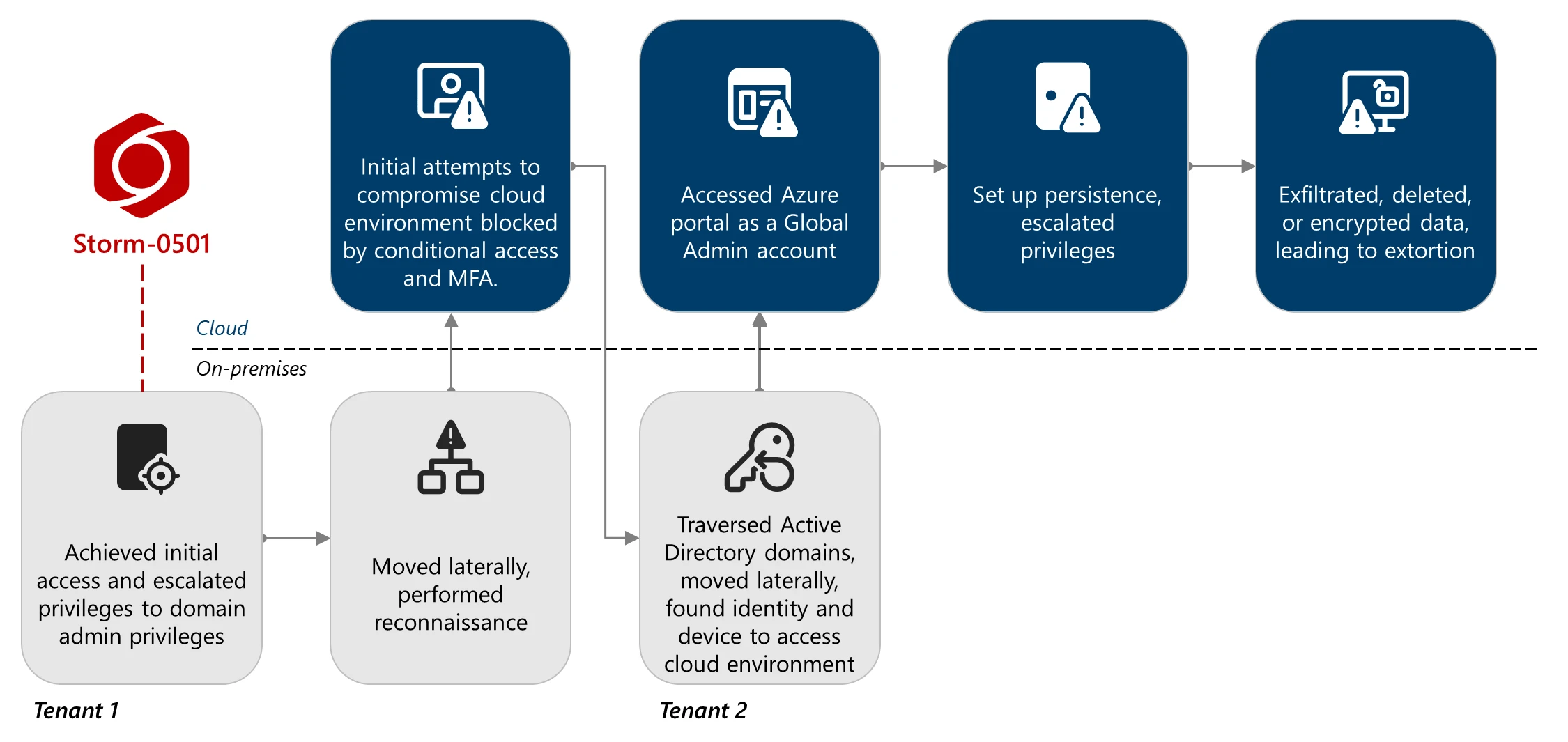
Supply: Microsoft
As soon as in charge of the cloud atmosphere, Storm-0501 started disabling defenses and stealing delicate information from Azure Storage accounts. The risk actors additionally tried to destroy storage snapshots, restore factors, Restoration Providers vaults, and storage accounts to stop the goal from recovering information without spending a dime.
When the risk actor could not delete information from restoration providers, they utilized cloud-based encryption by creating new Key Vaults and customer-managed keys, successfully encrypting the information with new keys and making it inaccessible to the corporate until they pay a ransom.
After stealing information, destroying backups, or encrypting cloud information, Storm-0501 moved to the extortion part, contacting victims via Microsoft Groups utilizing compromised accounts to ship ransom calls for.
Microsoft’s report shares safety recommendation, Microsoft Defender XDR detections, and searching queries that may assist discover and detect the ways utilized by this risk actor.
As ransomware encryptors are more and more blocked earlier than they’ll encrypt units, we might even see different risk actors shift away from on-premise encryption to cloud-based information theft and encryption, which can be more durable to detect and block.



