
State-sponsored hackers linked to the Silk Hurricane exercise cluster focused diplomats by hijacking internet site visitors to redirect to a malware-serving web site.
The hackers used an superior adversary-in-the-middle (AitM) method to hijack the captive portal of the community and ship the goal to the first-stage malware.
Google Risk Intelligence Group (GTIG) tracks the risk actor as UNC6384 and, primarily based on tooling, concentrating on, and infrastructure, believes it’s related to the Chinese language risk actor TEMP.Hex, also referred to as Mustang Panda and Silk Hurricane.
Hijacking Chrome requests
GTIG researchers consider that the AitM was doable after compromising an edge gadget on the goal community; nonetheless, they didn’t discover proof to help this concept.
The assault begins when the Chrome browser checks whether it is behind a captive portal, which is an internet web page the place customers of a community authenticate earlier than connecting to the web.
With the hackers able to hijack internet site visitors, they redirect the goal to a touchdown web page impersonating an Adobe plugin replace website.
Victims obtain a digitally signed ‘AdobePlugins.exe’ file, introduced as a required plugin replace, and are directed to step-by-step directions on the positioning to bypass Home windows safety prompts whereas putting in it.
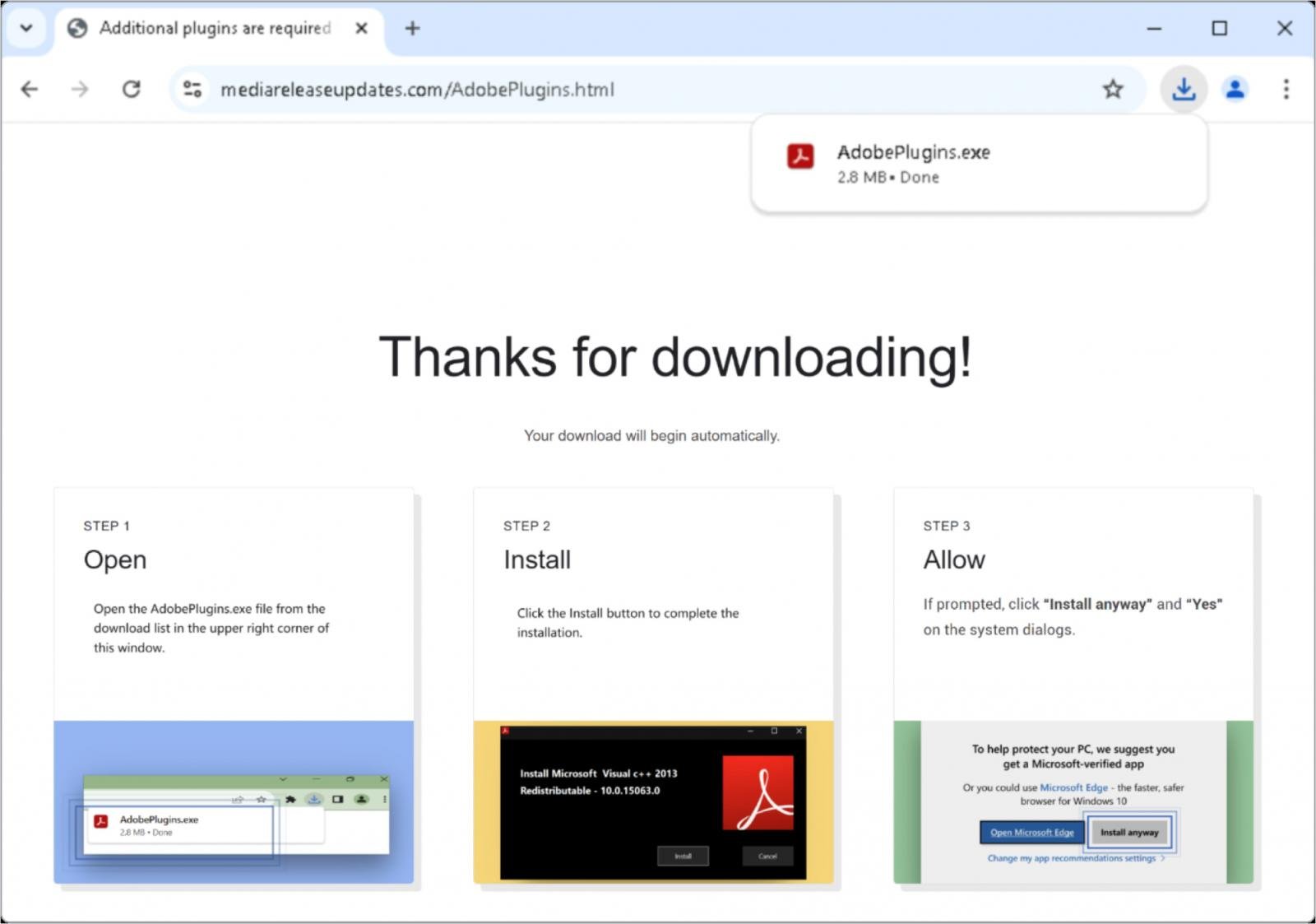
Supply: Google
Launching that file shows a Microsoft Visible C++ installer, but it surely secretly downloads a disguised MSI bundle (20250509.bmp) that accommodates a reputable Canon printer instrument, a DLL (CANONSTAGER), and the SOGU.SEC backdoor in RC-4 encrypted kind.
CANONSTAGER decrypts and masses the ultimate payload within the system reminiscence utilizing the DLL side-loading method.
SOGU.SEC, which Google says is a variant of the PlugX malware, used extensively by a number of Chinese language risk teams, can accumulate system data, add or obtain recordsdata, and supply operatives with a distant command shell.
.jpg)
Supply: Google
The GTIG researchers famous that it’s unclear whether or not the entity that indicators the recordsdata used on this marketing campaign, Chengdu Nuoxin Instances Know-how Co., Ltd, is knowingly taking part in these operations or was compromised.
Nonetheless, GTIG tracks no less than 25 malware samples signed by this entity since early 2023, related to varied Chinese language exercise clusters.
Treating all certificates from Chengdu Nuoxin Instances Know-how Co., Ltd as untrusted is an affordable defensive motion till the state of affairs is clarified.
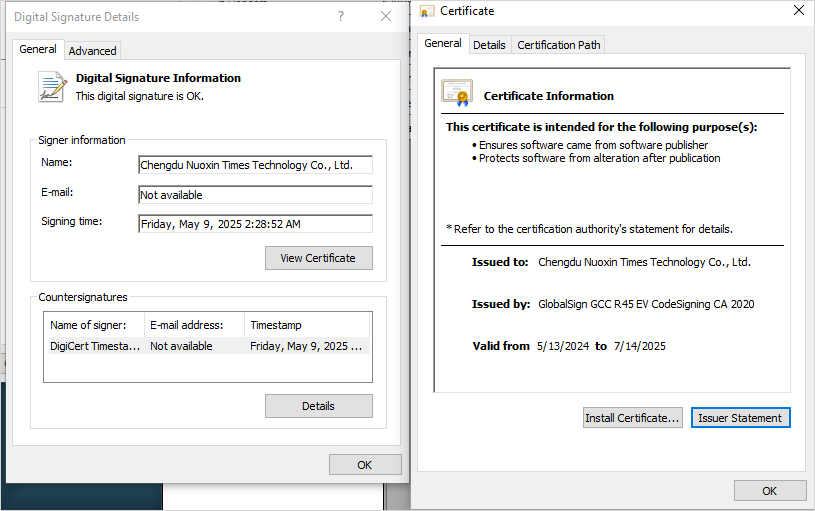
Supply: Google
Google blocked the malicious domains and file hashes through Protected Shopping and issued government-backed attacker alerts to affected Gmail and Workspace customers.
The tech big has additionally shared YARA guidelines for detecting STATICPLUGIN and CANONSTAGER, and indicators of compromise (IoCs) for all recordsdata sampled from these assaults.
This newest marketing campaign is indicative of the growing sophistication of Chinese language-nexus espionage actors, who’re very more likely to change to new infrastructure and binary builds and rebound shortly.



