Making certain a resilient and reliable communication ecosystem that protects information and maintains privateness for present and future purposes
As we stay up for the subsequent decade of cell connectivity, now is an effective time to think about how safety wants might evolve:
- Developments in connectivity, compute and AI convey unprecedented alternatives, however additionally they demand strong safety measures to guard our digital future.
- Because the world’s main wi-fi innovator, our imaginative and prescient is to proceed making a safe, adaptable and reliable cell ecosystem that meets as we speak’s challenges and is ready for tomorrow’s threats.
- We’re working to ascertain a strong belief framework for 6G on prime of the prevailing safe 5G basis that will facilitate a safe, resilient and adaptable community infrastructure, able to withstanding fashionable cyber threats and making certain the integrity and confidentiality of communications.
Because the basis for safe connectivity was established with 3GPP Launch 15, 5G safety has been repeatedly enhanced. Every subsequent launch strengthened the safety of the connectivity we depend on as we speak. With the rise of huge parallel computing, AI instruments educated on giant datasets and quantum computing, which all make for extra succesful menace vectors, the significance of securing connectivity, compute and AI has by no means been stronger. As efforts to form 6G throughout the 3GPP ecosystem collect momentum, now’s the time to look nearer at securing the way forward for cell connectivity.
Welcome to the seventh installment of the 6G foundry sequence, the place we discover 6G native safety, strong belief frameworks and quantum-safe safety to construct a safe 6G on prime of the prevailing safe 5G basis that’s resilient towards recognized and possible future threats.
6G native safety
On this part, we take a look at methods to essentially enhance safety within the 6G entry stratum (AS), which incorporates the radio entry community (RAN) and the consumer tools (UE). By addressing key areas equivalent to safe management messages, enhanced mobility safety, versatile consumer airplane (UP) safety termination factors and consumer id privateness, we purpose to construct a resilient 6G basis.
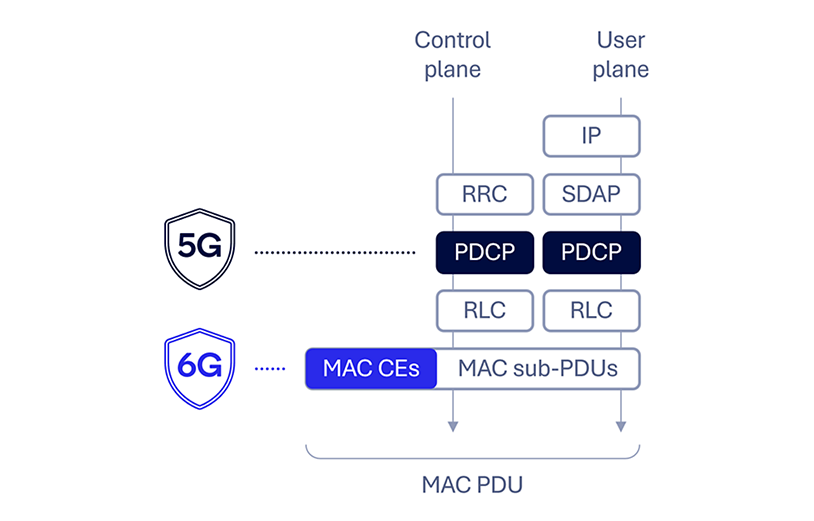
Safe management messages
Making certain the confidentiality and authenticity of management messages is essential to constructing a safe basis for 6G. 5G AS safety at present defines safety on the packet information convergence protocol (PDCP) layer to safeguard management airplane visitors for the radio useful resource management (RRC) protocol and UP visitors equivalent to web protocol (IP). Nevertheless, there isn’t any safety safety for management messages on the decrease layers, equivalent to medium entry management (MAC) parts (CEs). Manipulation of those parts can degrade or disrupt the hyperlink, equivalent to with timing advance, transmission configuration indicator and buffer standing report messages. Moreover, facet channel data leakage, equivalent to UE mobility patterns, has been proven to be potential (e.g., within the paper “Stealthy Location Identification Assaults Exploiting Provider Aggregation (SLIC)”). Radio hyperlink management (RLC) and PDCP standing experiences are additionally at present not protected, the place manipulation can doubtlessly result in packet loss, pointless duplication or radio hyperlink failure.
To counter these potential threats, 6G AS safety might be improved by incorporating MAC layer safety alongside the prevailing PDCP safety to make sure complete safety of all management messages and UP visitors.
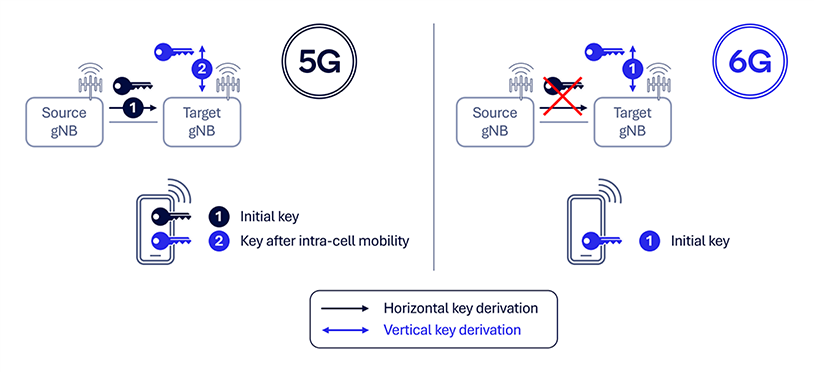
Improve safety for RAN mobility
Safety for RAN mobility is a possible enhancement for 6G native safety, specializing in a strong key hierarchy for enhanced ahead security1 throughout mobility. Within the present 5G framework, key adjustments are facilitated by the Xn interface (i.e., RAN-based mobility necessitate RRC signaling, with the supply gNB supplying the important thing to the goal gNB by way of the Xn interface). Extra RRC signaling for intra-cell handover on the goal gNB is due to this fact required to assist ahead safety. Nevertheless, this course of might delay key separation between gNBs and impacts the preparation of the gNB key (KgNB) at a number of gNBs for options equivalent to subsequent L1/L2 triggered mobility (LTM).
To handle these challenges, 6G key change procedures might be enhanced with ahead and backward security2 by design, with vertical key derivation for a change in gNB throughout handover. This method ensures the connection on the goal gNB node stays safe even when the keys on the supply gNB node are compromised. Moreover, supporting a number of concurrent AS key preparations at completely different RAN nodes (gNBs) will improve the general safety and adaptability of the 6G community.
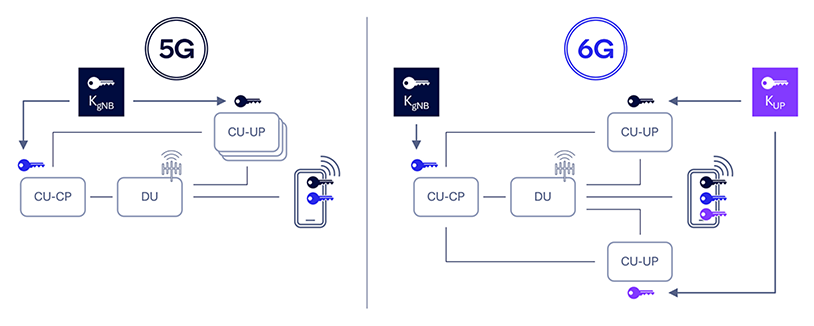
Deliver flexibility to consumer airplane safety termination factors
UP information might be made safer by permitting completely different UP termination factors tailor-made to particular software or service wants. Within the context of 5G, a UE may connect with a number of centralized unit consumer airplane nodes (CU-UPs) of a gNB, every comparable to a distinct protocol information unit (PDU) session. Nevertheless, this setup introduces potential safety threats, equivalent to the dearth of key separation when a number of consumer planes are configured for a single UE, notably for various PDU classes or community slices. Furthermore, binding the UP safety key of a CU-UP to a centralized unit management airplane (CU-CP) managed key (i.e., KgNB) can result in frequent key adjustments particularly for extremely cell UEs, which can incur vital signaling overhead for low-complexity Web of Issues (IoT) units.
To resolve these points, we suggest designing 6G AS safety to assist key separation for various UP termination factors primarily based on community deployment, UE mobility patterns and repair safety necessities, whereas sustaining protocol consistency to the UE and enabling service-specific configurations.
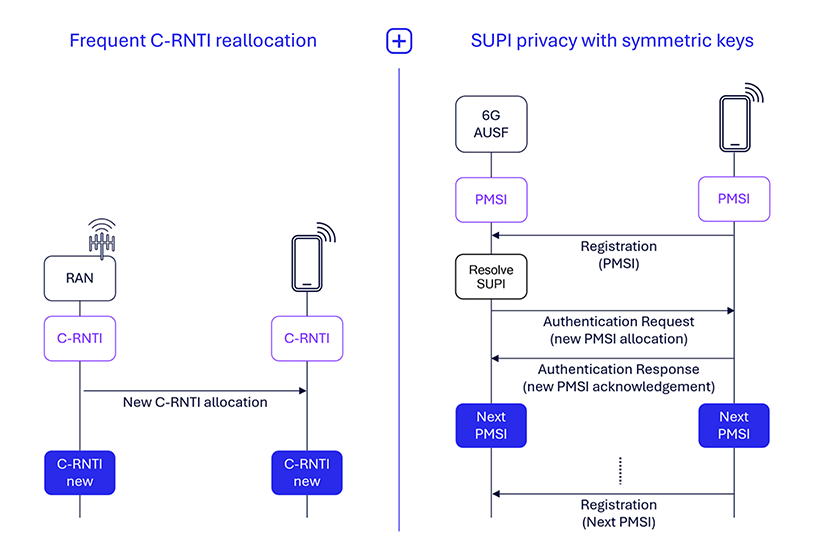
Enhance consumer id privateness within the RAN
A key side of 6G safety is holding consumer identities personal, which incorporates the privateness of RAN short-term identities (RNTIs). In 5G networks, a cell-RNTI (C-RNTI) is assigned through the random entry channel (RACH) process and up to date throughout mobility occasions. Nevertheless, long-lasting C-RNTIs (e.g., if the gadget stays related on the similar cell) can expose UEs to passive eavesdropping, revealing side-channel data equivalent to the kind of UE or energetic companies via over-the-air visitors evaluation. Moreover, focused assaults could happen if a C-RNTI is linked to a UE’s private identifiers, like cellphone numbers or social media accounts.
To mitigate these dangers, along with the strict reallocation of worldwide distinctive short-term identifiers (GUTI) and I-RNTIs for every connection launched in 5G, we suggest to assist extra frequent C-RNTI reallocations in 6G for related UEs with out necessitating a brand new RACH process. That is for enhancing privateness and decreasing the chance of monitoring and focused assaults.
Additionally essential to defending consumer id is sustaining the privateness of subscription everlasting identifiers (SUPI). In 5G, the subscription hid identifier (SUCI) calculation depends on elliptic curve built-in encryption scheme (ECIES), which is anticipated to get replaced by post-quantum cryptography (PQC) in 6G. PQC algorithms, whereas promising, have giant public key and cipher textual content sizes, leading to substantial SUCI sizes. For instance, a PQC algorithm equivalent to Module-Lattice-Primarily based Key-Encapsulation Mechanism (ML-KEM) would end in 100s of extra bytes of overhead in comparison with ECIES utilized in 5G.
As we examine the adoption of PQC algorithms for producing SUCI, a symmetric key-based method for 6G that leverages USIM credentials might decrease SUCI dimension overhead. This methodology entails sending an encrypted personal cell subscription id (PMSI) to the UE through the authentication and key settlement (AKA) process, with the UE utilizing the PMSI in subsequent connect or registration processes, making certain strong and environment friendly privateness safety.
Sturdy belief frameworks
Establishing a strong belief framework for 6G would facilitate a safe, resilient and adaptable community infrastructure, able to withstanding fashionable cyber threats and making certain the integrity and confidentiality of communications. On this part, we take a look at some key areas of focus at Qualcomm Applied sciences for attaining such a framework: remoted UE safety contexts at every community operate, zero belief structure (ZTA) primarily based on NIST tenets and strong safety setup by way of message digest.
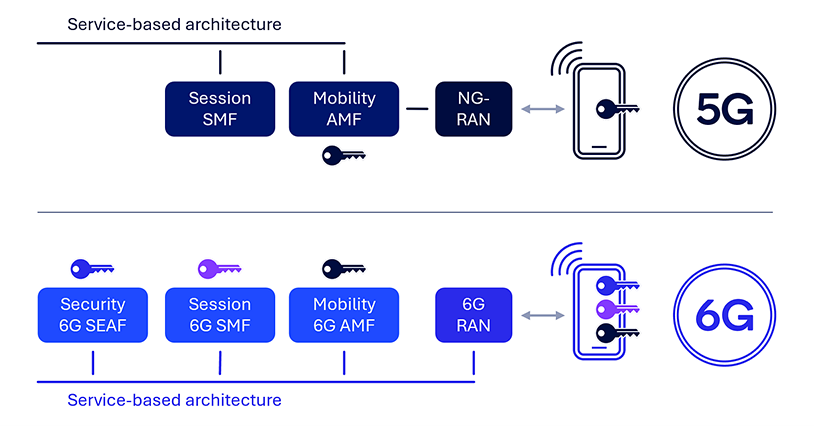
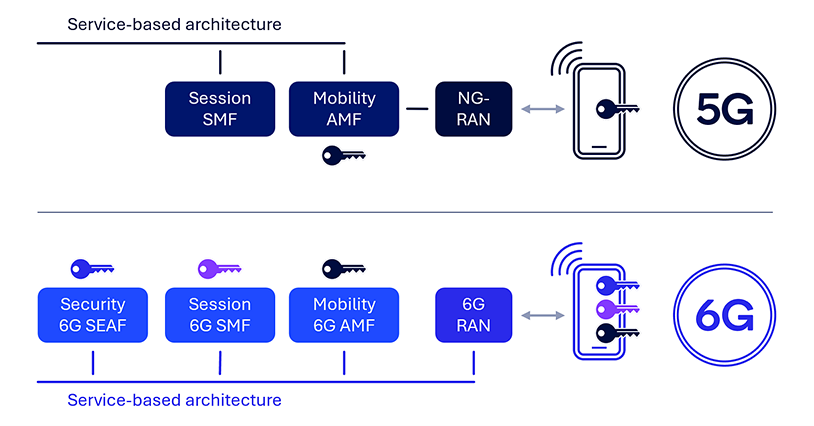
Isolate UE safety contexts at every community operate (NF)
Isolate UE safety contexts at every community operate (NF)
5G NAS messages are securely exchanged between the UE and the AMF. Nevertheless, the present structure has a single NAS safety termination level on the AMF, which presents limitations and potential threats. For example, there isn’t any generic safe communication channel between the house public land cell community (HPLMN) and the UE when the UE is roaming, which necessitates the HPLMN counting on the visited public land cell community (VPLMN) when delivering sure updates to the UE (e.g., UE insurance policies). Moreover, there isn’t any ahead safety with AMF relocation, that means the supply AMF is aware of the NAS key on the goal AMF and past. Moreover, the institution of unbiased and remoted UE safety contexts at completely different community features such because the session administration operate (SMF) can’t be supported, leading to a scarcity of end-to-end safety assist with the UE. Such limitations and threats are as a result of 5G safety anchor operate (SEAF) being collocated with the AMF and solely getting used for preliminary AMF key derivation.
As with AS safety supporting ahead safety, potential 6G NAS safety enhancements embody an unbiased 6G SEAF for supporting ahead safety within the AMF or, extra typically, for community operate relocation. Moreover, a separate safety anchor on the HPLMN would assist safe communication between the UE and the HPLMN when roaming, offering a generic approach for the HPLMN to configure roaming UEs and enhancing residence community management. Introducing an unbiased SEAF can additional facilitate end-to-end safe communication between the UE and varied community features.
Implement zero belief structure
Zero belief structure (ZTA) is constructed on the NIST zero belief tenets. Within the context of 5G, ZTA work by 3GPP is restricted to the Core Community, whereas O-RAN’s ZTA work focuses on the RAN. A spot evaluation has been carried out in 3GPP in addition to in O-RAN Alliance, introducing some enhancements within the 5G system. For instance, safety occasion information and log assortment, and publicity to a Safety Info and Occasion Administration (SIEM) system are being outlined. Safety analysis and coverage enforcement depends on proprietary options, that are out of the usual’s scope.
For 6G, creating structure and options towards enabling ZTA is essential, with potential enhancements wanted to fulfill NIST Tenet 5 and 6. This contains evaluating the safety states of the 6G system and introducing new practical parts, equivalent to a brand new community operate (NF). A converged RAN-Core community structure and a typical structure for 3GPP and O-RAN have to be thought-about for unified safety administration of the 6G system, holding in thoughts that ZTA is an incremental and steady course of.
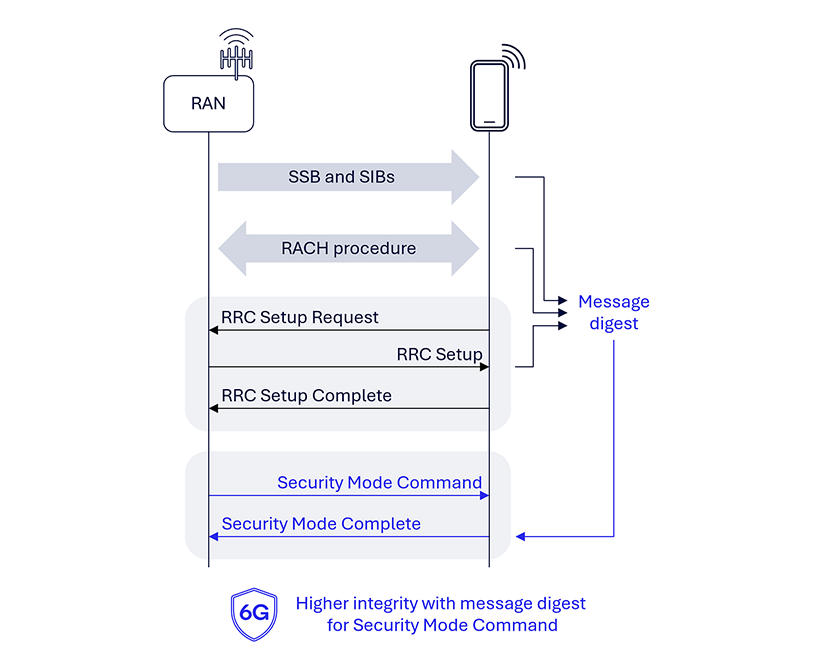
Guarantee strong safety setup by way of message digest
In 5G AS safety, widespread radio configurations and parameters, such because the grasp data block (MIB) and system data block (SIB), will not be protected, doubtlessly prone to false base station (FBS) assaults. The usage of digitally signed system data has been mentioned within the 3GPP as a potential resolution. With the adoption of PQC algorithms, such signature would require hundreds of bytes of extra overhead (e.g., at the very least 2420 bytes for module-lattice-based digital signature algorithm (ML-DSA)), and that compares poorly to present most SIB1 dimension being below 400 bytes. Aside from data broadcasts, RACH and RRC setup messages exchanged previous to the safety mode command (SMC) are additionally not protected, resulting in potential dangers. Manipulation of message contents earlier than the SMC can lead to the UE being misconfigured, and adversaries can relay visitors with out being detected by the UE or RAN, making the system prone to man-in-the-middle assaults.
To boost 6G AS, we suggest together with a message digest computed from the messages exchanged within the SMC, just like how TLS computes a transcript hash as described in RFC 8446 part 4.4.1. Upon detecting an error, the system can decide whether or not to proceed or launch the connection, thereby enhancing the general safety and integrity of the communication course of.
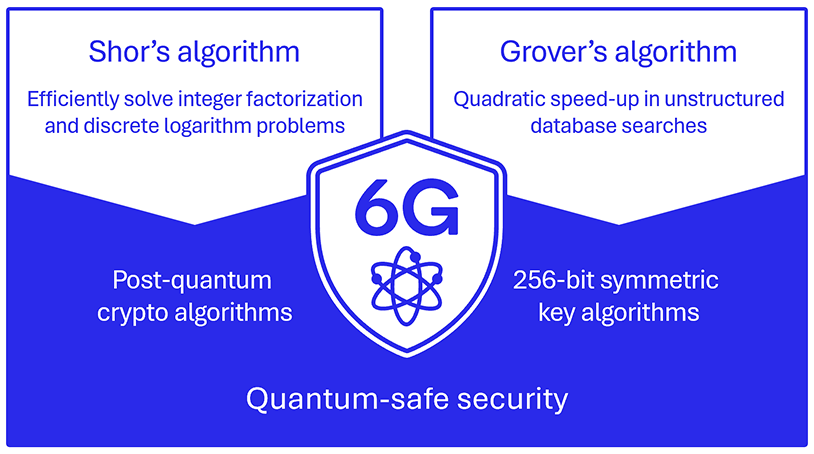
Quantum-safe safety
As quantum expertise progresses, conventional public key algorithms counting on the computational hardness of sure algorithms, equivalent to integer factorization and discrete logarithm issues, face growing threats. Particularly, Shor’s algorithm, which effectively solves integer factorization and discrete logarithm issues, necessitates the event of PQC algorithms. NIST is at present standardizing these algorithms, making certain safety readiness for the Quantum period. Moreover, quantum properties allow a quadratic speed-up in unstructured database searches, posing dangers to symmetric key algorithms. To counter this menace, 256-bit symmetric key algorithms like AES-256, SNOW5G, and ZUC-256 are important for 3GPP air interface safety, together with Authenticated Encryption with Extra Information (AEAD). As we transfer towards 6G, resilience towards quantum assaults positive aspects significance, requiring the adoption of PQC and 256-bit algorithms to safeguard communication safety.
Making connectivity synonymous with safety and belief
Developments in connectivity, compute and AI convey unprecedented alternatives, however additionally they demand strong safety measures to guard our digital future. At Qualcomm Applied sciences, our imaginative and prescient is to create a safe, adaptable and reliable cell ecosystem that meets as we speak’s challenges and is ready for tomorrow’s threats. By addressing alternatives throughout the 6G radio entry stratum and the RAN protocol stack, we’re laying the groundwork for a resilient and safe future.
Be a part of us as we assist form the subsequent decade of cell connectivity with 6G. Keep tuned for extra updates from the 6G Foundry.
Study extra and get the most recent updates:
Take a look at our new 6G content material hub
Join our wi-fi applied sciences e-newsletter to remain updated
Comply with us on X


