
Russian hackers bypass multi-factor authentication and entry Gmail accounts by leveraging app-specific passwords in superior social engineering assaults that impersonate U.S. Division of State officers.
The risk actor focused well-known teachers and critics of Russia in what’s described as a “subtle and customized novel social engineering assault” that didn’t rush the individuals of curiosity into taking motion.
Between April and early June, the hackers delivered meticulously developed phishing messages geared toward convincing recipients to create and share app-specific passwords that would offer entry to their Gmail accounts.
An app-specific password is designed to permit third-party apps (e.g. an e-mail consumer) which might be thought-about much less safe or older purposes permission to entry your Google Account if two-factor authentication (2FA) is lively.
Safety researchers at Google Risk Intelligence Group observe the cyber actor as UNC6293. They imagine they’re state-sponsored and could be related to APT29, a risk group beneath Russia’s International Intelligence Service (SVR).
APT29 is tracked beneath a number of names (NobleBaron, Nobelium, Cozy Bear, CozyDuke, Midnight Blizzard) and has been working since not less than 2008.
Its targets embrace authorities networks, analysis institutes, and assume tanks.
Gradual-paced phishing
Tutorial analysis group The Citizen Lab investigated an incident from UNC6293’s spearphishing marketing campaign that focused Russian info operations professional Keir Giles.
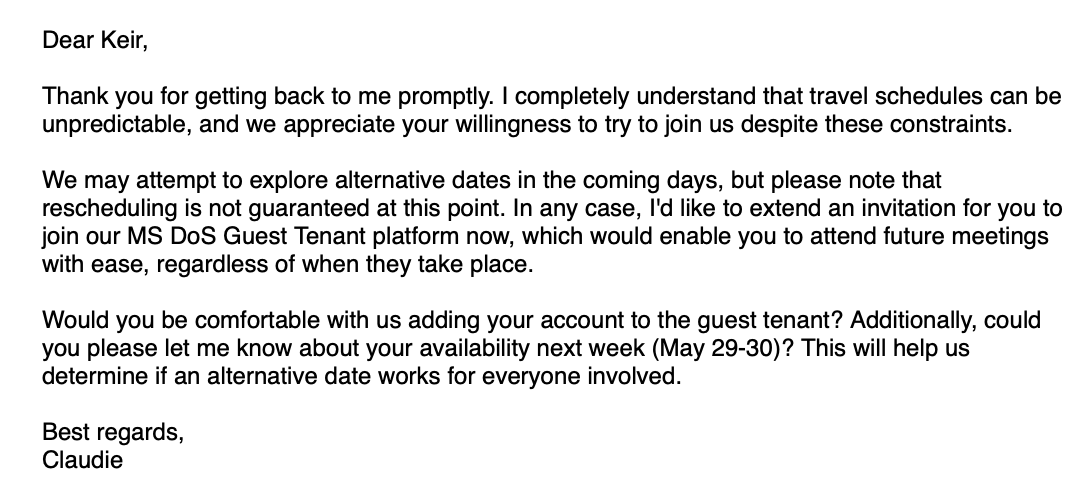
The assault begins with an e-mail signed by Claudie S. Weber, allegedly from the U.S. State Division, inviting Giles to “a personal on-line dialog.”
Though the message is delivered from a Gmail account, a number of @state.gov e-mail addresses are current within the carbon copy (CC) line, together with one for Claudie S. Weber, making it extra credible that the communication was official.
The researchers say that they may not discover any proof of a “Claudie S. Weber” being employed by the U.S. State Division.
“We imagine that the attacker is conscious that the State Division’s e-mail server is seemingly configured to simply accept all messages and doesn’t emit a ‘bounce’ response even when the deal with doesn’t exist” – The Citizen Lab
After a number of e-mail exchanges the place Giles expressed curiosity however disclosed that they may not be out there on the indicated day, the risk actor invited him to hitch the State Division’s “MS DoS Visitor Tenant” platform, “which might allow you to attend future conferences with ease, regardless once they happen.”
supply: The Citizen Lab
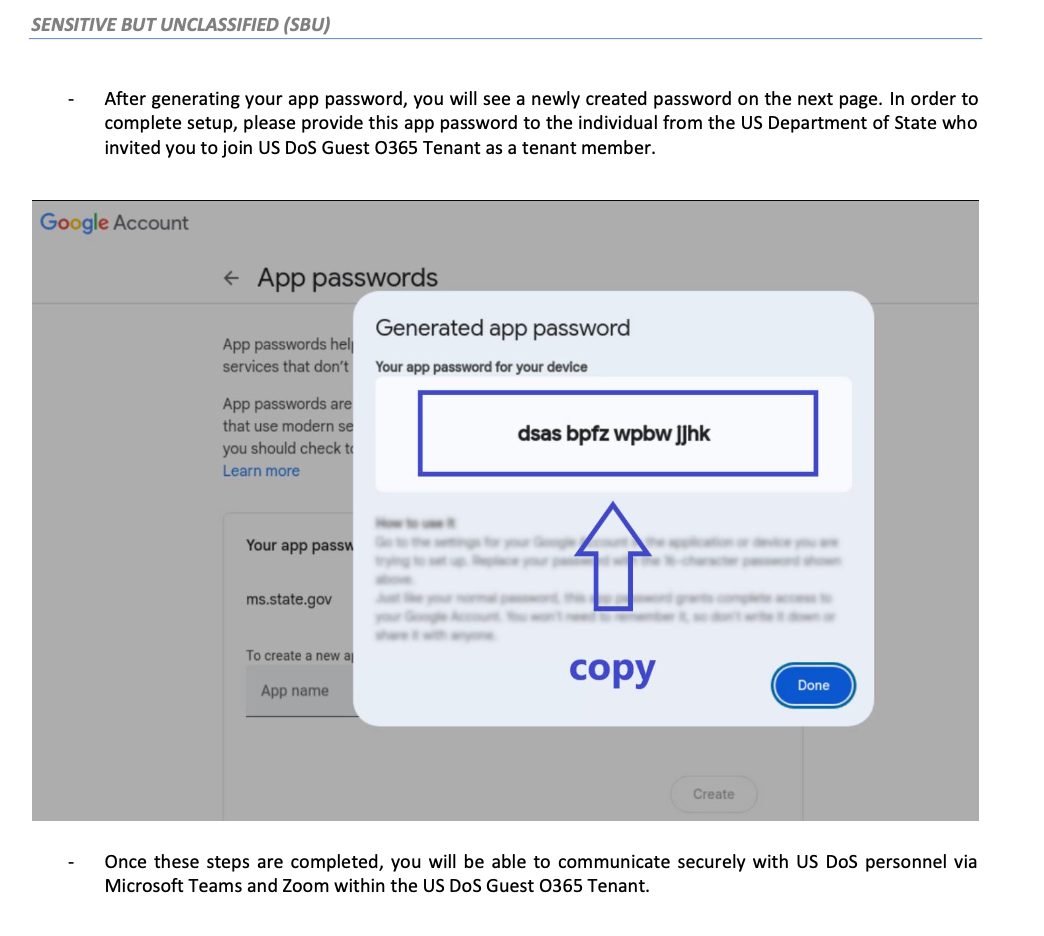
Giles accepted and was despatched a PDF file detailing tips on how to create an app-specific password on a Google account, which was vital for enrolling on the alleged platform as a visitor person.
A later step within the deceit concerned sharing the app-specific passcode “with US DoS directors so as to add the exterior person to the Visitor O365 Tenant.”
An evidence for this was outlined within the directions, saying that it’s an alternate answer that facilitates safe communication over the platform between U.S. DoS staff and exterior customers with Gmail accounts.
Whereas the goal believes that they’re creating and sharing an app-specific password to entry a State Division platform in a safe approach, they’re giving the attacker full entry to their Google account, The Citizen Lab researchers clarify.
supply: The Citizen Lab
Google Risk Intelligence Group (GTIG) researchers decided that this spearphishing marketing campaign began in not less than April and continued by way of the start of June.
Throughout this era, they recognized two campaigns, one counting on themes associated to the U.S. Division of State and one other that used lures related to Ukraine and Microsoft.
Each campaigns included residential proxies (91.190.191[.]117) and digital non-public servers (VPS) servers within the infrastructure, permitting the risk actor to remain nameless when logging into compromised e-mail accounts.
The 2 social engineering campaigns noticed by The Citizen Lab and GTIG had been skilfully crafted and relied on a number of pretend identities, accounts, and numerous supplies designed so as to add to the deception.
Customers focused with superior phishing ways are sometimes people carefully concerned in high-profile points associated to conflicts, litigation, or advocacy.
To maintain them secure from expert attackers, Google recommends enrolling into its Superior Safety Program, which elevates safety measures on the account and doesn’t enable creating an app-specific password, or log in with out offering a sure passkey.



