From early 2022 by means of late 2024, a bunch of risk actors publicly often known as APT28 exploited identified vulnerabilities, equivalent to CVE-2022-38028, to remotely and wirelessly entry delicate data from a focused firm community. The assault first compromised much less safe Wi-Fi networks of a number of organizations that had been in shut bodily proximity to the meant goal. This incident brings to mild the essential position that software program performs within the safety of modern-day wi-fi communication programs, each navy and civilian. This assault didn’t require any {hardware} to be positioned within the neighborhood of the focused firm’s community because the attackers had been capable of execute remotely from 1000’s of miles away.
With the ubiquity of Wi-Fi, mobile networks, and Web of Issues (IoT) units, the assault floor of communications-related vulnerabilities that may compromise knowledge is extraordinarily giant and consistently increasing. Anybody who holds digital—checking account data to company mental property, to nationwide safety data—ought to concentrate on the roles of software program and cybersecurity in wi-fi programs and the right way to defend towards software-based assaults.
On this weblog submit, we evaluate widespread radio frequency (RF) assaults and examine how software program and cybersecurity play key roles in these exploitations. We begin with an summary of the Open System Interconnection (OSI) mannequin. Then we’ll delve into safety elements of recent wi-fi communication programs with examples of vulnerabilities, exploitations, weaknesses, and the way these would possibly affect the wi-fi system. We are going to conclude with software program and safety mitigations.
Overview of the OSI Stack
The idea of layering is a type of practical modularity that’s helpful in communication programs. The motivation of a layered strategy is to decompose a posh design drawback into extra manageable ones and facilitate standardization. Just like knowledge representations in computing, a pure layering exists in wi-fi communication networks. Broadly talking, the bottom layers relate to the physics of connectivity (i.e., wi-fi, copper wire, fiber optical, and so forth). Layered on prime of this are encodings to help the illustration of binary bits and their meeting into binary strings. Above this are layers that relate to the switch of binary strings. Above these are layers that give application-specific meanings to the binary strings. Assault surfaces and potential vulnerabilities exist at each degree. As we discover layers of the OSI mannequin all through this part, we additionally have a look at a number of examples of potential software-enabled assaults at every layer.
The Worldwide Group for Standardization (ISO) defines the OSI mannequin as “a standard foundation for the coordination of requirements growth for the aim of programs interconnection.” Whereas the OSI stack is relevant to each bodily wired and wi-fi networks, this weblog submit will deal with the layers of the stack from the wi-fi communication perspective. The OSI mannequin is a really broadly adopted scheme used to explain and handle the layering. The underside three layers (Bodily, Knowledge Hyperlink, and Community) symbolize {hardware} elements of connectivity. The Transport Layer serves because the central mechanism for controlling knowledge switch. As proven in Determine 1 under, the highest three layers (Session, Presentation, and Utility) are sometimes referenced because the software program layers; nevertheless, you will need to be aware that in trendy wi-fi communication programs, software program is prevalent in all seven layers of the OSI mannequin stack.

Determine 1: Abstract of OSI Layers derived from Stallings
Bodily Layer
The Bodily Layer, additionally referred to as the PHY or layer 1, is the bottom layer of the OSI stack and addresses interactions of {hardware}, transmission, and signaling mechanisms. In trendy wi-fi programs, the PHY is usually supported utilizing digital, analog, and/or mixed-signal RF chips, in addition to a digital baseband chip for digital sign processing (DSP) and communication algorithm processing equivalent to channel coding. Channel coding methods, equivalent to Ahead Error Correction (FEC), are employed in digital communications and add managed redundancy to knowledge to detect and proper errors launched by interference or noise on the communication channel. On the transmitter, the encoder provides redundant bits to the unique knowledge that can be despatched. On the receiver, the decoder will use these redundant bits to determine and proper errors. We are going to go into higher element about error detection and correction within the Knowledge Hyperlink Layer part under.
Within the context of wi-fi communication programs, the PHY layer is chargeable for sending and receiving radio frequency alerts. The PHY defines the strategies for transmitting uncooked bits over a wi-fi knowledge hyperlink connecting community nodes and units. The PHY interfaces with the Knowledge Hyperlink Layer, which palms over the info within the type of bits that can be transmitted by the PHY. The PHY layer additionally manages the transition between processing the bitstream within the computational digital realm to the frequencies and emissions which might be the RF realm. A standard model of a binary numerical definition of a waveform will get transformed right into a radiating electromagnetic wave (RF wave) within the PHY. Versus a wired community, no explicit bodily medium is required; nevertheless, RF propagation traits differ primarily based on the surroundings of the wi-fi transmission. A selected RF sign transmitted at a specific frequency in a specific surroundings is named a channel. Relying on the system, a single channel or simultaneous a number of channels could also be used. The PHY of the receiving system captures the radiated modulated RF sign and converts it again into time-sampled digital binary numbers representing the uncooked transmitted sign, together with attainable noise and errors inherited from the shared surroundings of the channel. For many wi-fi programs, body synchronization happens on the PHY after demodulation and ensures alignment of the receiver clocks with corresponding transmitter clocks. Body synchronization specifies how a receiver identifies the beginning and finish of information frames within the acquired bitstream by finding a singular synchronization sample, equivalent to a preamble, embedded at first of every body.
The bits are additional organized and processed within the Knowledge Hyperlink Layer. Determine 2 depicts a generalized Bodily Layer structure of a transmitter and receiver pair. The PHY considerations point-to-point or point-to-multipoint (i.e., broadcast) connections, versus multi-hop networks, equivalent to wi-fi mesh networks, which is the priority of higher layers within the OSI stack.
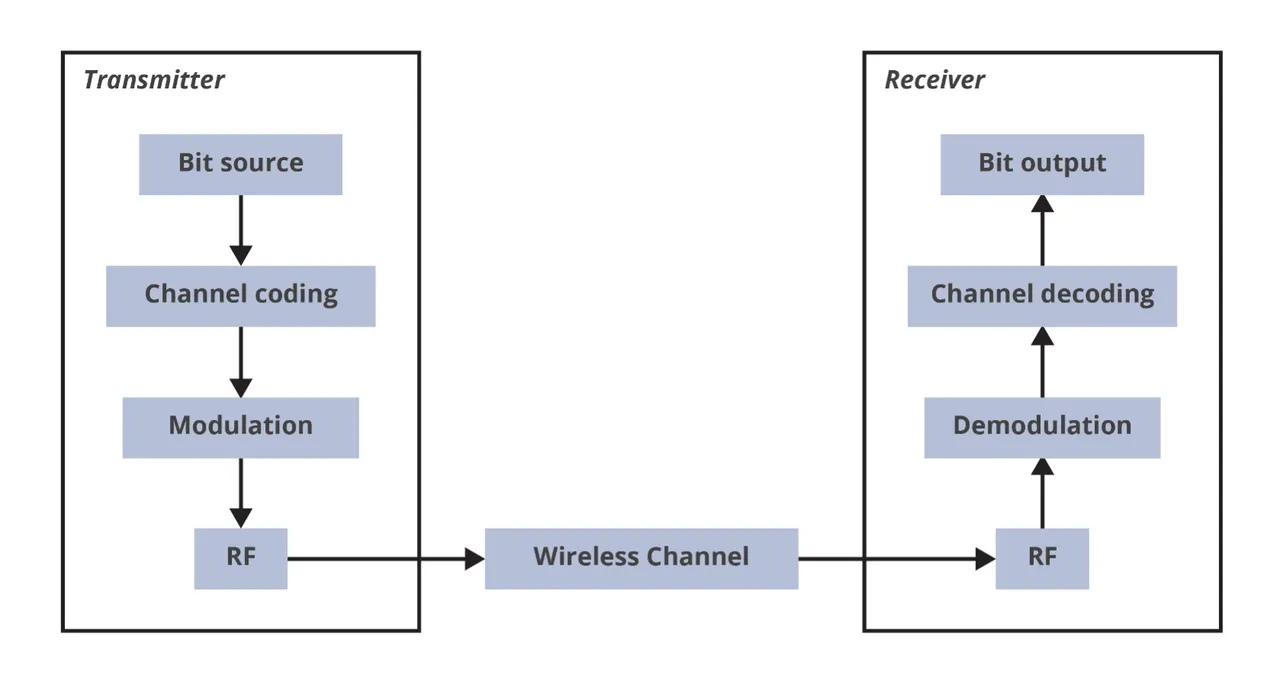
On the PHY Layer, an instance of a software-enabled assault vector is knowledge contamination, by way of sign sniffing. In any such assault, the attacker broadcasts a sign that’s stronger (i.e., increased energy) than the authentic and meant sign and is falsified to deprave the authentic communications hyperlink. This stronger, falsified sign on the bodily layer could be employed such that the software program within the wi-fi community that handles system connection and visitors routing is tricked into rerouting visitors to the attacker. An attacker may additionally disrupt or deny wi-fi communications by focusing on synchronization alerts to disrupt body synchronization. Jamming assaults equivalent to synchronization sign jamming and burst jamming intention to override or trick the authentic synchronization alerts of a wi-fi system. One other strategy is to spoof or manipulate alerts to mislead the receiver. For instance, an attacker may inject right into a Wi-Fi community solid preambles that precede the precise knowledge body. By spoofing the preamble on this approach, the assault can drive units to attend for the expiration of an introduced knowledge body length, successfully silencing the channel. In one other assault strategy, the risk actor may spoof the well-known time synchronization customary of a International Navigation Satellite tv for pc System (GNSS), equivalent to GPS. This assault broadcasts counterfeit GNSS alerts at the next energy degree than authentic satellite tv for pc alerts inflicting the goal receiver synchronization and monitoring to lock onto the pretend sign. This might enable the attacker to control the focused system’s notion of time or location disrupting or denying its skill to obtain and decode knowledge.
Knowledge Hyperlink Layer
Layer 2 of the OSI mannequin stack, the Knowledge Hyperlink Layer (DLL), manages bodily addressing (versus community addressing) and entry management to the PHY to detect and/or forestall knowledge collisions in a channel. The DLL additionally handles error correction, knowledge circulate management, and the reassurance of dependable knowledge body switch throughout the wi-fi channel. On a typical wi-fi community, equivalent to these outlined by IEEE802, this layer is split into two sublayers: Logical Hyperlink Management (LLC) and the Media Entry Management (MAC). Each linked system is supposed to have a singular MAC deal with, which is 48 bits lengthy for IEEE 802 MAC addresses however might be totally different lengths for different requirements. The DLL-MAC layer makes use of these distinctive addresses to handle how units acquire entry to the community utilizing protocols. The MAC deal with can be utilized to determine meant recipients of the info frames.
Error detection and correction can be dealt with within the Knowledge Hyperlink Layer. Error-correcting codes can be utilized to enhance the efficiency of a digital communication system. The standard measure of efficiency is the bit error fee (BER) versus power per bit to noise density ratio (Eb/No). The BER is the likelihood of the reception of an incorrect bit. Within the easy instance proven in Determine 3, we see that the twelfth bit within the stream (highlighted in blue) despatched from a transmitter (Tx) was acquired incorrectly on the receiver (Rx). By including managed redundancy to the info on the transmitter earlier than sending to the receiver, lack of knowledge (bits) resulting from interference or noise encountered on the channel could be detected on the receiver and reconstructed to forestall the lack of data within the transmission. The DLL additionally handles the speed of information switch (knowledge circulate) to forestall the transmitter from overwhelming the receiver(s) by sending an excessive amount of knowledge or sending knowledge too rapidly.

Determine 3: Easy Bit Error Instance
The Knowledge Hyperlink Layer is inclined to software-enabled assault vectors together with pretend entry level nodes, MAC deal with spoofing, and Wi-fi Native Space Community (WLAN) driver assaults.
In a pretend entry level assault, often known as an evil twin, the attacker establishes a malicious entry level (AP) with the identical Service Set Identifier (SSID) because the authentic AP to trick consumer units into connecting to a pretend community. As soon as a tool is linked to this pretend community, the attacker can execute a person-in-the-middle assault to seize the system’s wi-fi community visitors and the info being despatched and acquired.
MAC spoofing happens when an attacker modifications a tool’s MAC deal with to impersonate one other authentic system on the wi-fi community. This can be utilized to bypass MAC deal with filtering which may be in place or to execute different forms of community assaults.
To conduct a WLAN driver assault, the risk actor exploits software program vulnerabilities within the wi-fi community card drivers of a linked system. These exploitations can expose routes to the attackers on which they’ll execute malicious code and acquire management over wi-fi community or system.
Community Layer
The third layer is the Community Layer, which handles inter-network connections together with managing routes for knowledge packets, pinging servers in different networks to substantiate availability, and addressing and receiving packets from different networks. Routing determines the perfect path for knowledge packets to journey from a supply to a vacation spot, even throughout a number of networks, by utilizing routing protocols and algorithms. Packet forwarding strikes knowledge packets from one community to a different primarily based on routing selections, connecting totally different networks.
In a multi-node wi-fi community, knowledge/communication packets are moved throughout the community from node to node, which is known as hopping. Whereas wired networks extra generally have static routes as a result of bodily wiring between nodes, wi-fi routing could be both static or dynamic in nature. A wi-fi mesh community (WMN) is usually comprised of finish node units/purchasers mixed with routes and gateways. If the mobility of mesh purchasers is minimal, the community topology tends to be principally static. Usually WMNs depend on static nodes to perform as gateways and, on this approach, they’re just like wired networks. By comparability, a decentralized cell advert hoc community (MANET), is designed to not depend on pre-existing or mounted infrastructure equivalent to routers, gateways, or wi-fi entry factors. Fairly, every MANET node actively participates in visitors routing by relaying knowledge for different nodes within the community. The choice of which nodes ahead knowledge is executed dynamically primarily based on community connectivity and the community’s routing algorithm. Because of the dynamic nature of the routing, every node within the MANET can transfer independently of the opposite nodes, and the hyperlinks to different units could also be up to date incessantly.
Packet sniffing or capturing and observing over-the-air knowledge packets, is an instance of a Community Layer software-enabled assault vector. Because of the over-the-air broadcast nature of wi-fi alerts, an attacker can passively seize packets from the community and probably collect data or intercept delicate visitors, even under encryption layer. From this data, the attacker could possibly decide the sample of lifetime of the sign (i.e., how typically it transmits, energy ranges, frequencies, and so forth.). For example, packet sniffing and capturing knowledge could be detrimental to the decentralized MANET beforehand mentioned. To determine and preserve environment friendly and dynamic community routing in a MANET, metadata about every node must be consistently despatched to different nodes throughout the community. This creates potential data leakage if this metadata is captured by way of packet sniffing. As soon as an attacker has captured data associated to the MANET message routing, they can exploit vulnerabilities by focusing assaults on the routing algorithms, by isolating focused nodes from the community, or by inserting a false node on the community with malicious intent.
Transport Layer
The Transport Layer (TL), or layer 4, resides above the Community Layer and is chargeable for guaranteeing knowledge packets arrive reliably and precisely between purposes operating on units throughout the community. The transmitter TL accomplishes this by breaking giant knowledge streams into smaller, manageable segments, and the receiver TL reassembles these segments. On the TL, the commonest protocols utilized to trade messages over a community are the Transmission Management Protocol (TCP) and the Consumer Datagram Protocol (UDP). TCP is usually used for knowledge streams which might be extremely dependable and have to be absolutely and precisely communicated on the potential value of latency. UDP can be utilized for decrease latency knowledge streams the place the worth of a missed packet may need a negligible impact, equivalent to media streams and real-time knowledge transmission. As soon as the packets and segments have been reassembled, they’re pushed as much as the Session Layer for the corresponding program/utility on the tip system. Whereas TCP and UDP are designed to work on each wired and wi-fi networks, wi-fi variations additionally embody extra safety layers such because the Wi-fi Transport Layer Safety (WTLS) to guard knowledge. This extra layer of safety just isn’t usually required on the similar degree of safety in wired networks the place bodily entry is a barrier to ingress. In wi-fi networks, the Transport Layer might also require extra aggressive error management methods than wired networks as a result of increased probability of packet loss and corruption primarily based on interference.
TCP hijacking is a standard software-enabled assault within the Transport Layer of the OSI mannequin stack. TC/IP hijack assaults intercept and take management of the TCP session established between two wi-fi units on a community by predicting or capturing the sequence numbers used to synchronize and manage authentic connection and interplay. With management of the TCP/IP session, the attacker can take over a consumer session by stealing or predicting the session token. This enables authentic consumer impersonation, entry to delicate knowledge, and skill to execute unauthorized actions on the system or community.
Session Layer
Layer 5 within the OSI mannequin stack is the Session Layer. In a wi-fi system, the Wi-fi Session Protocol (WSP) implements the Session Layer performance and is chargeable for the institution, upkeep, and termination of communication classes between linked units on the wi-fi community. The WSP will even handle the allocation and subsequent launch of community assets throughout the established session.
In the same strategy to the hijacking mentioned within the earlier part, session fixation assaults are an instance of Session Layer software-enabled assaults. In a session fixation assault, the risk actor forces a licensed consumer’s session ID to a predictable worth then, as soon as the consumer offers authentication data, the attacker can use the identical ID to hijack that session with related outcomes to the earlier layer.
Presentation Layer
The Presentation Layer, the sixth layer of the OSI mannequin stack, is chargeable for getting ready knowledge for the receiving utility on the system. This layer handles duties equivalent to knowledge translation, compression, and encryption (though encryption may also be performed at different layers as properly). In wi-fi programs, this layer is essential in guaranteeing interoperability between totally different units and programs, particularly when these units might make the most of differing knowledge codecs or encoding strategies. Knowledge translation converts knowledge between totally different codecs, for instance Unicode or its predecessor, the American Customary Code for Info Interchange (ASCII). Unicode carried out a dramatic growth from ASCII’s unique 7-bit encoding of characters to codecs of 8, 16, or 32 bits, permitting for very giant character units. There are additionally legacy codecs equivalent to Prolonged Binary Coded Decimal Interchange Code (EBCDIC), nonetheless used on some mainframe computer systems. Knowledge compression is employed to enhance effectivity and latency by lowering the quantity of data that’s transmitted over the community. Encryption may also be performed on the Presentation Layer, permitting for confidentiality and safety of the info. The transmitter encrypts the info earlier than transmission, and it’s decrypted upon reception on the receiver node.
On the Presentation Layer, a buffer overflow assault exploits software program vulnerabilities within the areas the place a program writes knowledge to a reminiscence buffer that’s not sufficiently giant sufficient to carry all of the written knowledge. This extra knowledge “overflows” the goal reminiscence buffer to overwrite adjoining reminiscence areas which could be manipulated by an attacker to trigger this system to crash, leak data, or execute arbitrary or malicious code. The malicious code can execute with the identical degree of privileges because the weak utility, probably granting full entry to the system. Overflowing the buffer may also corrupt essential knowledge or expose delicate data saved in adjoining reminiscence. Encryption implementation flaws within the Presentation Layer may additionally expose a vector for assaults. Exploitation of weak or improperly carried out encryption protocols can enable unintended decryption and entry to delicate knowledge.
Utility Layer
The seventh and highest layer within the OSI mannequin stack is the Utility Layer. This layer serves because the interface between the tip consumer and purposes to entry the wi-fi community companies. The Utility Layer handles duties equivalent to e mail companies and protocols utilized for internet searching together with the Easy Mail Switch Protocol (SMTP) and Hypertext Switch Protocol (HTTP). This layer ensures {that a} given utility can successfully talk with different purposes on totally different units and networks. Nevertheless, you will need to be aware that the Utility Layer just isn’t an utility itself.
Provided that the Utility Layer is nearly solely composed of software program, there are lots of assault vectors and vulnerabilities that may be exploited. Particular examples embody Structured Question Language (SQL) Injection, Cross-Web site Scripting, and Border Gateway Protocol (BGP) Hijacking.
SQL is a domain-specific language used for database administration programs. In an SQL injection assault, malicious SQL code is injected into the enter fields of the goal utility, probably resulting in unauthorized entry, knowledge theft, or knowledge corruption.
Cross-site scripting employs malicious software program scripts which might be injected into internet purposes which might be then executed by a consumer’s internet browser, typically with out their data. Execution of those malicious cross-site scripts can result in session hijack, as beforehand mentioned, or to unauthorized knowledge exfiltration.
In a BGP hijack assault, the attacker misrepresents possession of a goal web site’s IP deal with to maliciously reroute incoming and outgoing visitors, permitting for the interception or manipulation of information.
Software program Implications for Safety of Wi-fi Communications System
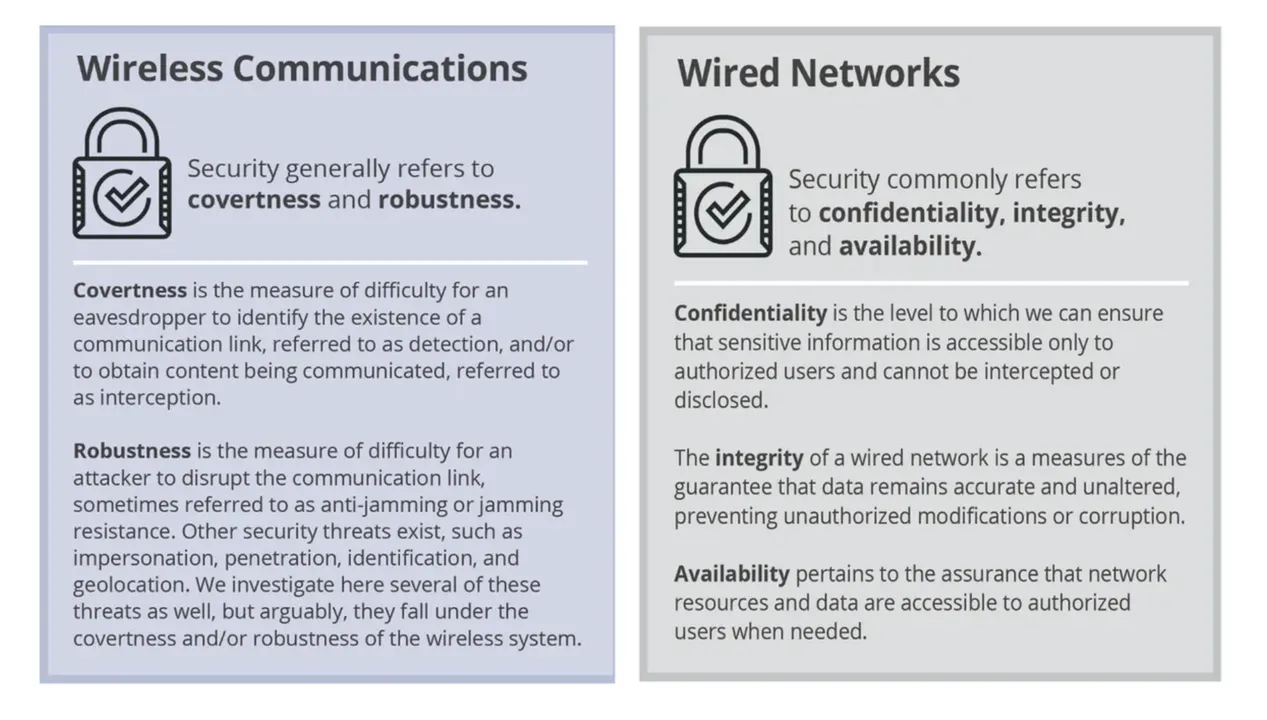
Determine 4: Contrasting Wi-fi and Wired Community Safety
From the safety and knowledge safety perspective, you will need to distinction a number of traits of wired versus wi-fi networks. Determine 4 offers as fast abstract of how safety is usually outlined for each forms of networks. Each communication networks have to do channel coding and sign processing, nevertheless the approaches and methods have to be basically totally different. For instance, in a wired Gigabit Ethernet connection, the standard of the copper wire and winding methods within the Ethernet wire decide how channel coding and sign processing on the community could be performed. Probably the most cheap approach for an attacker to intercept and exfiltrate knowledge is to bodily entry (faucet) the wire. This can be a substantial distinction to wi-fi networks the place the channel and sign is probably extra publicly accessible as a result of over-the-air, wi-fi nature of the hyperlinks and connections. Within the wi-fi case, the implementation must have robustness integrated within the design of the sign and connection to hinder unintentional or malicious interception and exploitation. Desk 1 summarizes similarities and variations between wi-fi and wired networks with respect to the OSI mannequin layers.
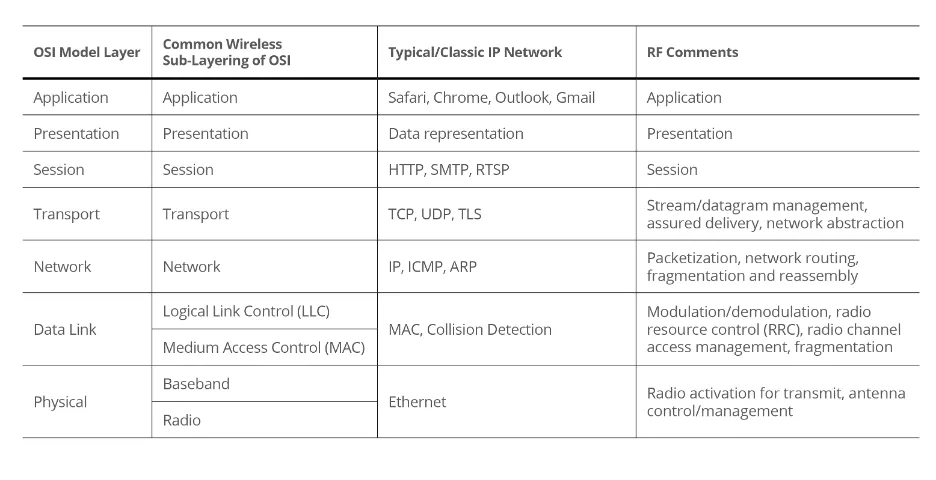
Desk 1: Abstract Comparability of Wi-fi and Wired OSI Mannequin Layers
Software program performs many essential roles in trendy implementation of each wired and wi-fi communication programs. With respect to wi-fi programs, the position of software program within the prime three layers (Session, Presentation, and Utility) ought to be apparent; nevertheless, what could also be much less discernible is the position of software program within the {hardware} layers of the OSI stack (PHY, DLL, and Community). As beforehand mentioned, the PHY layer is primarily centered on {hardware}. Nevertheless, with the rise of software-defined radios, software program is changing into extra prevalent on the decrease layers of the OSI stack as properly. A software-defined radio (SDR) is a radio communication system or system that implements conventional radio {hardware} elements (e.g., filters, mixers, modulators/demodulators, amplifiers, and so forth.), both on a pc or as a part of an embedded system. Determine 4 under reveals a simplified illustration of the SDR idea for a radio receiver. The highest picture reveals a typical analog receiver comprised of conventional {hardware} elements, and the underside picture reveals a SDR receiver with elements carried out in software program.
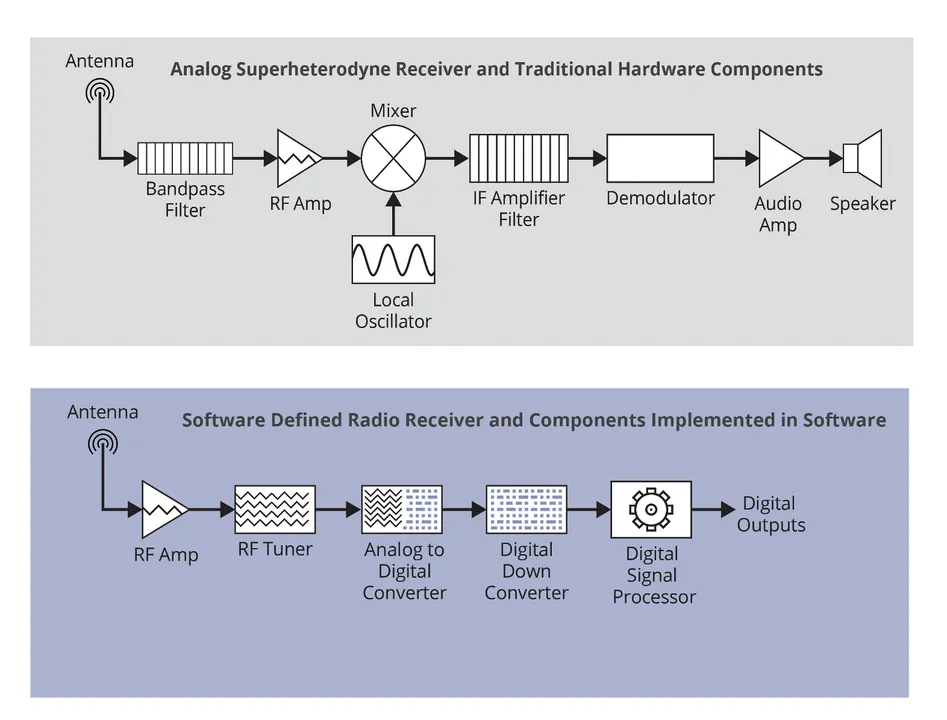
Determine 5: Prime: Analog Receiver with {Hardware} Elements; Backside: SDR Receiver with Software program Applied Elements
One of many key benefits of SDR is using software program, which permits agile reprogrammability and reconfiguration, permitting for elevated flexibility and improved efficiency. This allows the consumer to change performance by downloading and operating new software program at will. It additionally facilitates fast prototyping workouts. Vital parts of the sign processing are dealt with by a general-purpose processor moderately than special-purpose analog {hardware} (e.g., tubes, transistors, chips, and digital circuits).
Usually SDRs are full-duplex, which suggests they permit a single system to each transmit and obtain concurrently. Using software program makes it attainable for a single SDR to help quite a lot of protocols and/or waveforms. As well as, an onboard field-programmable gate array (FPGA) can be utilized to encode/decode knowledge from quite a lot of wi-fi requirements in addition to to encrypt or scramble knowledge earlier than transmission. This stuff may also be performed straight in software program; nevertheless, this strategy usually requires a tradeoff in pace and latency. The flexibility to satisfy communication timing necessities, particularly with quick turnaround, can’t be simply performed in a general-purpose course of, nevertheless it’s attainable to create higher flexibility within the protocol to permit for latencies within the general-purpose processor strategy. Alternatively, the system can make use of an FPGA or Utility Particular Built-in Circuit (ASIC) to cut back the timing overhead and get extra environment friendly use of the RF spectrum.
These configurations supply new sorts of vulnerabilities. For instance, malicious software program can be utilized to have an effect on or reprogram an FPGA to change the conduct of a wi-fi communication system. A compromised FPGA may allow attackers to switch configurations or performance to disrupt, degrade, or usurp wi-fi communication programs. For instance, attackers may reconfigure an FPGA to intercept and manipulate knowledge transmitted over wi-fi hyperlinks, jam authentic communication alerts, inject false data into the community visitors, or exploit vulnerabilities in adjoining units or networks.
In a earlier weblog, RF 101: Can You Actually Hack a Radio Sign?, we reviewed a number of of the commonest forms of RF assaults that may be employed to use vulnerabilities and intercept, disrupt, or manipulate wi-fi communication programs and related protocols. Right here we revisit a number of of those RF assaults, in addition to some new ideas, to research how software program and cybersecurity play key roles in these exploitations.
Replay Assault
Replay assaults happen when a sound transmission is captured and retransmitted to impersonate a authentic system or consumer. This assault exploits vulnerabilities in the best way that software program programs deal with knowledge transmission, authentication, and authorization. Delicate knowledge that may be captured can embody session tokens or login credentials. Determine 5 depicts an instance of a primary replay assault. The attacker captures a sound authentication message despatched by a authentic consumer after which retransmits that message at a later time to realize entry to the community.

Determine 6: Replay Assault
An instance of a replay assault is discovered within the safety flaws of the Wi-Fi Protected Setup (WPS), a function designed to simplify the strategies of connecting units to present Wi-Fi networks by way of configuration potentialities equivalent to push-button or PIN-code entry. As soon as initiated, the push-button technique depends on the consumer to push a button on each the shopper system and the Wi-Fi router concurrently inside a set timeframe. An attacker may intercept and retransmit (replay) the authentic shopper system’s alerts, tricking the router into accepting an unauthorized connection.
From a software program and cybersecurity perspective, there are a number of key methods that may be employed to mitigate these exploitations. One step is to enhance software program authorization strategies by utilizing role- or attribute-based entry controls, which restrict consumer permissions, entry to data, and degree of interplay with the system primarily based on their consumer position or consumer profile attributes. Different mitigation steps embody implementing least privilege to customers, denying entry by default, validating or re-validating permissions on each entry request, encrypting delicate knowledge, and implementing robust password insurance policies.
Relay Assault
A relay assault happens when the attacker serves as an middleman by intercepting and relaying communications between the transmitter and meant receiver with out explicitly manipulating the messages. A relay assault in a wi-fi community is analogous to a person-in-the-middle assault for a wired community and is typically referred to this fashion in a wi-fi community as properly. One of these assault can be utilized to realize entry to programs or companies or to bypass safety measures which might be in place. With out correct validation of the origin of communications, software program purposes and protocols counting on authentication and encryption could be exploited by relay assaults. Determine 6 reveals an instance of a relay assault by means of an intercepted and transferred key fob used to unlock a automobile. On this instance, one individual may intercept to key fob sign, which is at all times transmitting, and relay the sign to a second individual that’s near the automobile thus bypassing the necessity for the important thing fob to be in shut proximity to the automobile to unlock it. Equally, the sign to begin the automobile may also be captured and relayed to the second individual.

Determine 7: Relay Assault
Just like the Wi-Fi replay assault mentioned within the earlier part, an attacker may make the most of a relay assault to realize unauthorized entry to Wi-Fi community. On this case, the attacker may use units, equivalent to an SDR, to relay the push-button alerts between the authentic shopper system and the router, thus bypassing bodily proximity necessities.
Whereas there are some bodily mitigation approaches within the utilization of bodily safety keys (e.g., YubiKey), software program safety has an essential position as properly. Sturdy authentication strategies, equivalent to multi-factor authentication (MFA), metric verification, and one-time passcodes, may also help to mitigate exploitations from relay assaults. Nevertheless, a few of these bodily mitigation approaches nonetheless require wi-fi communications that may be spoofed. For instance, attackers could possibly intercept after which ship a false passcode to a cellular telephone or spoof the important thing exchanges on a wi-fi multi-factor authentication system.
The APT28 nearest neighbor assault offered within the introduction is a wonderful instance of the power to sidestep MFA units. APT28 had been capable of make the most of brute drive password-spray assaults to acquire legitimate credentials to entry the goal community. Nevertheless, resulting from MFA implementation on the focused firm, the attackers couldn’t straight entry the community with the stolen credentials. Utilizing Distant Desktop Protocol (RDP) from a number of corporations in proximity, the attackers had been capable of compromise and use privileged authentication credentials to hook up with the focused firm community. The assailants had been capable of get across the meant firm MFA units by daisy-chaining collectively much less safe entry factors from close by corporations and exploiting a multihomed community together with the CVE-2022-38028 vulnerability permitting Home windows Working System privilege elevation by way of the print spooler software program. A multihomed community is one which connects a bunch, system, or pc concurrently to a couple of community. Within the case of this multihomed community, Web connectivity was offered by way of a wired Ethernet connection, nevertheless, it additionally offered a Wi-Fi community adapter that might be used concurrently. Whereas Web-facing assets required MFA, the Wi-Fi was not protected with MFA. Because of this, APT28 had been capable of scan for accessible networks inside vary of the Wi-Fi community adapter and connect with the goal firm enterprise Wi-Fi using the compromised credentials. As talked about beforehand, this assault didn’t require {hardware} to be positioned within the neighborhood of any one of many compromised networks or the businesses’ bodily areas. The absolutely distant assault was executed in its entirety from the opposite aspect of the globe utilizing solely software program vulnerabilities and exploitations to acquire privileged credentials and entry the focused firm community and knowledge that it contained.
Mitigations of such exploitations ought to embody implementation of robust encryption and safe wi-fi channels for MFA codes and system communications, employment of multi-device MFA methods, institution of sturdy entry controls, exercise monitoring, incident response processes for MFA units and programs, and common updates to MFA software program and firmware to handle identified vulnerabilities. Intensive consideration must also be given associated to potential dangers that Wi-Fi networks might current to safety.
Purposes and Concerns for Nationwide Protection
For protection purposes, the position of software program safety in wi-fi communication programs is essential. Trendy warfare requires wi-fi communications for command and management (C2), situational consciousness, autonomy, and distributed engagement in a variety of environments. Lack of communication capabilities will virtually actually lead to mission failure. To thwart C2, adversaries will aggressively search methods to disclaim communications. With rising scope, complexity, distribution, and connectivity of wi-fi communication programs and systems-of-systems, the potential assault floor continues to broaden dramatically. An correct understanding of the software program that makes up these programs is more and more essential, from low-level code and libraries to software-defined radios and networks, as much as and together with the applying layer interfaces, and all components in between.
For protection purposes, there are extra concerns equivalent to
- adversarial threats: Adversaries would possibly intentionally intervene with communication programs to disclaim, degrade, or disrupt connectivity in addition to search means to extract essential data/knowledge.
- useful resource constraints: With rising quantities of information required for modern-day warfare, mission ways, methods, and procedures have to be sufficiently environment friendly to execute on edge units with restricted connectivity, computing energy, and storage.
- affect: Communication system failures, both by way of connectivity or loss/theft of data, can have substantial affect on essential operations, probably leading to lack of knowledge, assets, and lives.
Work with the SEI
Understanding the position of software program and safety in wi-fi communication programs is step one in the direction of mitigation to make sure covertness and robustness. Right here on the SEI, we’ve got experience and expertise in each software program and RF engineering, and we’re constantly evolving processes and instruments to determine, assess, and strengthen the safety of wi-fi communication programs. For instance, we’re researching the applying of machine studying and synthetic intelligence methods throughout every layer of the OSI stack together with
- PHY layer propagation prediction and channel estimation
- slice administration of software-defined networks
- wi-fi communication system autonomy
- optimizing end-to-end communications and High quality of Service
- knowledge compression and encryption optimization for wi-fi.
As well as, SEI researchers are setting up wi-fi experimentation ranges that present processes, instruments, and knowledge pipelines to determine and examine potential safety dangers throughout all layers of the wi-fi OSI stack. This work can be more and more essential because the disciplines of conventional cybersecurity operations and wi-fi communications proceed to maneuver in the direction of convergence. To be taught extra about our work researching, testing, and evaluating software program and safety in wi-fi communication programs or to collaborate with us, please e mail [email protected].


