
An npm bundle named ‘rand-user-agent’ has been compromised in a provide chain assault to inject obfuscated code that prompts a distant entry trojan (RAT) on the consumer’s system.
The ‘rand-user-agent‘ bundle is a instrument that generates randomized user-agent strings, which is useful in net scraping, automated testing, and safety analysis.
Though the bundle has been deprecated, it stays pretty common, averaging 45,000 downloads weekly.
Nonetheless, based on researchers at Aikido, menace actors took benefit of its semi-abandoned but common standing to inject malicious code in unauthorized subsequent releases which might be more likely to have been downloaded by a big variety of downstream initiatives.
Aikido detected the compromise on Might 5, 2025, when its malware evaluation system flagged a brand new model of rand-user-agent, number one.0.110.
Upon deeper examination, the researchers discovered obfuscated code hidden within the ‘dist/index.js’ file that was solely seen if the consumer scrolled horizontally within the supply view on the npm website.
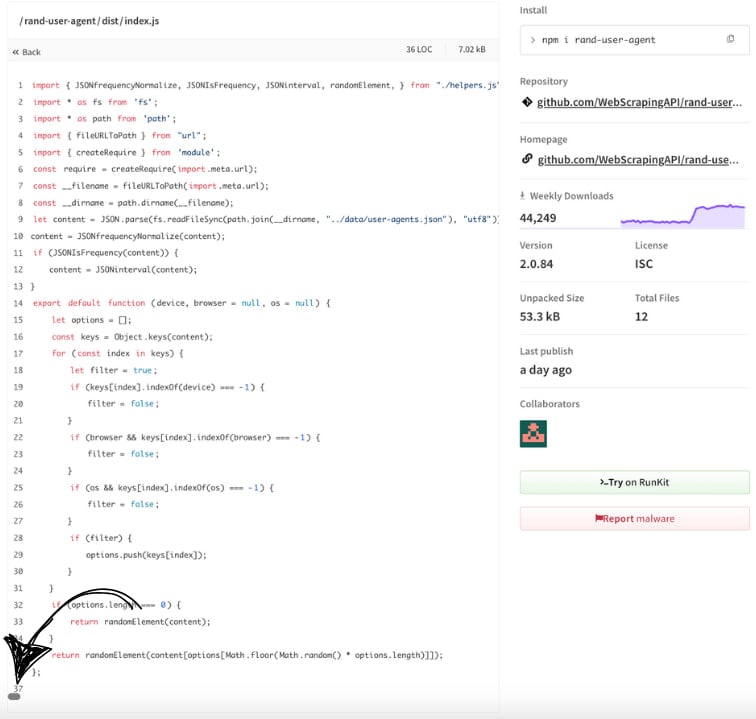
Supply: Aikido
Investigation confirmed that the final legit model of ‘rand-user-agent’ was 2.0.82, launched 7 months in the past.
Variations 2.0.83, 2.0.84, and in addition 1.0.110, which had been printed afterward, had been all malicious and did not have corresponding releases on the mission’s GitHub repository.
The malicious code embedded within the latest variations creates a hidden listing below the consumer’s dwelling folder (~/.node_modules) and extends the ‘module.paths’ in order that this practice path can be utilized for loading dependencies, particularly ‘axios’ and ‘socket.io-client.’
Subsequent, it opens a persistent socket connection to the attacker’s command and management (C2) at http://85.239.62[.]36:3306, and sends machine ID information together with hostname, username, OS sort, and a generated UUID.
As soon as the RAT is energetic, it listens for one of many under instructions:
- cd
– Adjustments present working listing - ss_dir – Resets working dir to script path
- ss_fcd:
– Forcefully modifications to the given listing - ss_upf:f,d – Uploads a single file f to vacation spot d
- ss_upd:d,dest – Uploads all recordsdata in listing d to dest
- ss_stop – Interrupts any ongoing file add
- (every other) – Executes it as a shell command utilizing child_process.exec()
On the time of writing, the malicious variations have been faraway from the bundle’s repository on npm, so the most recent out there model is protected, and customers ought to revert to it.
Nonetheless, when you’ve got upgraded to variations 2.0.83, 2.0.84, or 1.0.110, you will need to carry out a full system scan for indicators of compromise. Be aware that downgrading to the legit model doesn’t take away the RAT out of your system.
Furthermore, think about using forked however nonetheless supported and higher monitored variations of the ‘rand-user-agent’ instrument.
BleepingComputer contacted the developer to find out how their bundle was compromised, and we acquired the next remark:
“On 5 Might 2025 (16:00 UTC) we had been alerted that three unauthorized variations of rand-user-agent had been printed to the npm registry (1.0.110, 2.0.83, 2.0.84). The malicious code was by no means current in our GitHub repository; it was launched solely within the npm artifacts, making this a basic supply-chain assault.
Our investigation (nonetheless ongoing) reveals that the adversary obtained an outdated automation token from an worker and used it to publish releases to npm. That token had not been scoped with 2-factor authentication, permitting the attacker to: Publish variations that didn’t exist in GitHub, Increment the model numbers to look legit, Deprecate nothing, hoping the brand new releases would propagate earlier than anybody observed.
There is no such thing as a proof of a breach in our source-code repository, construct pipeline, or company community. The incident was restricted to the npm registry.
We apologize to each developer and group impacted by this incident. Defending the open-source ecosystem is a duty we take significantly, and we’re dedicated to full transparency as we shut each hole that allowed this assault to happen.”
Replace 5/9 – Added remark from WebScrapingAPI



