
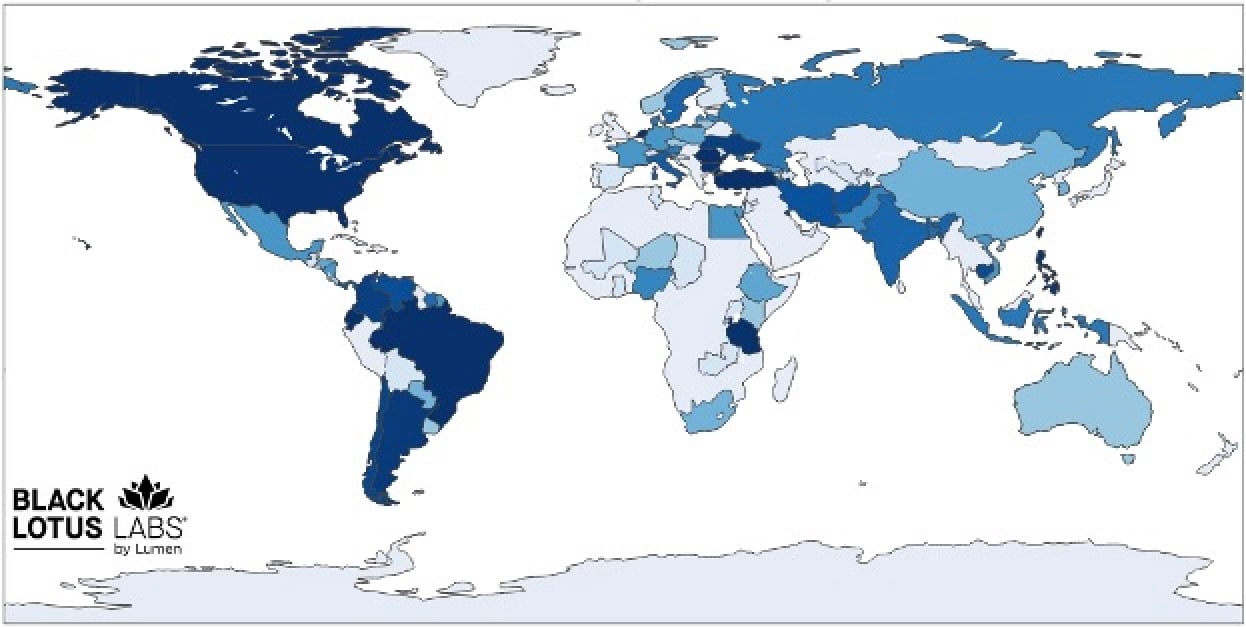
Regulation enforcement authorities have dismantled a botnet that contaminated 1000’s of routers over the past 20 years to construct two networks of residential proxies referred to as Anyproxy and 5socks.
The U.S. Justice Division additionally indicted three Russian nationals (Alexey Viktorovich Chertkov, Kirill Vladimirovich Morozov, and Aleksandr Aleksandrovich Shishkin) and a Kazakhstani (Dmitriy Rubtsov) for his or her involvement in working, sustaining, and taking advantage of these two unlawful companies.
Throughout this joint motion dubbed ‘Operation Moonlander,’ U.S. authorities labored with prosecutors and investigators from the Dutch Nationwide Police, the Netherlands Public Prosecution Service (Openbaar Ministerie), and the Royal Thai Police, in addition to analysts with Lumen Applied sciences’ Black Lotus Labs.
Court docket paperwork present that the now-dismantled botnet contaminated older wi-fi web routers worldwide with malware since at the very least 2004, permitting unauthorized entry to compromised units to be offered as proxy servers on Anyproxy.web and 5socks.web. The 2 domains have been managed by a Virginia-based firm and hosted on servers globally.
“The botnet controllers require cryptocurrency for cost. Customers are allowed to attach immediately with proxies utilizing no authentication, which, as documented in earlier circumstances, can result in a broad spectrum of malicious actors gaining free entry,” Black Lotus Labs mentioned.
“Given the supply vary, solely round 10% are detected as malicious in well-liked instruments equivalent to VirusTotal, which means they constantly keep away from community monitoring instruments with a excessive diploma of success. Proxies equivalent to this are designed to assist conceal a spread of illicit pursuits together with advert fraud, DDoS assaults, brute forcing, or exploiting sufferer’s information.”
Their customers paid a month-to-month subscription starting from $9.95 to $110 per 30 days, relying on the requested companies. “The web site’s slogan, ‘Working since 2004!,’ signifies that the service has been accessible for greater than 20 years,” the Justice Division mentioned at the moment.
The 4 defendants marketed the 2 companies (selling over 7,000 proxies) as residential proxy companies on numerous web sites, together with ones utilized by cybercriminals, they usually allegedly collected over $46 million from promoting subscriptions offering entry to the contaminated routers a part of the Anyproxy botnet.
They operated the Anyproxy.web and 5socks.web web sites utilizing servers registered and hosted at JCS Fedora Communications, a Russian web internet hosting supplier. Additionally they used servers within the Netherlands, Türkiye, and different areas to handle the Anyproxy botnet and the 2 web sites.
They have been all charged with conspiracy and harm to protected computer systems, whereas Chertkov and Rubtsov have been additionally accused of falsely registering a website title.
Concentrating on end-of-life (EoL) routers
On Wednesday, the FBI additionally issued a flash advisory and a public service announcement warning that this botnet was concentrating on patch end-of-life (EoL) routers with a variant of the TheMoon malware.
The FBI warned that the attackers are putting in proxies later used to evade detection throughout cybercrime-for-hire actions, cryptocurrency theft assaults, and different unlawful operations.
The record of units generally focused by the botnet contains Linksys and Cisco router fashions, together with:
- Linksys E1200, E2500, E1000, E4200, E1500, E300, E3200, E1550
- Linksys WRT320N, WRT310N, WRT610N
- Cisco M10 and Cradlepoint E100
“Lately, some routers at finish of life, with distant administration turned on, have been recognized as compromised by a brand new variant of TheMoon malware. This malware permits cyber actors to put in proxies on unsuspecting sufferer routers and conduct cyber crimes anonymously,” the FBI mentioned.
“Such residential proxy companies are notably helpful to legal hackers to offer anonymity when committing cybercrimes; residential-as against industrial—IP addresses are typically assumed by web safety companies as more likely to be professional site visitors,” at the moment’s indictment added. “On this means, conspirators obtained a personal monetary achieve from the sale of entry to the compromised routers.”



