
Over 1,200 internet-exposed SAP NetWeaver cases are weak to an actively exploited most severity unauthenticated file add vulnerability that enables attackers to hijack servers.
SAP NetWeaver is an utility server and growth platform that runs and connects SAP and non-SAP purposes throughout completely different applied sciences.
Final week, SAP disclosed an unauthenticated file add vulnerability, tracked as CVE-2025-31324, in SAP NetWeaver Visible Composer, particularly the Metadata Uploader part.
The flaw permits distant attackers to add arbitrary executable recordsdata on uncovered cases with out authenticating, reaching code execution and full system compromise.
A number of cybersecurity corporations, together with ReliaQuest, watchTowr, and Onapsis, confirmed the flaw is actively exploited in assaults, with risk actors using it to drop internet shells on weak servers.
A SAP spokesperson instructed BleepingComputer that they had been conscious of those makes an attempt and launched a workaround on April 8, 2024, adopted by a safety replace that addressed CVE-2025-31324 on April 25.
SAP instructed BleepingComputer that they don’t seem to be conscious of any circumstances the place these assaults impacted buyer information or techniques.
Extensively exploited in assaults
Researchers have now confirmed that many weak SAP Netweaver servers are uncovered on the web, making them prime targets for assaults.
The Shadowserver Basis discovered the 427 uncovered servers, warning of the huge uncovered assault floor and the doubtless extreme repercussions of exploitation.
Many of the weak techniques (149) are in the US, adopted by India (50), Australia (37), China (31), Germany (30), the Netherlands (13), Brazil (10), and France (10).
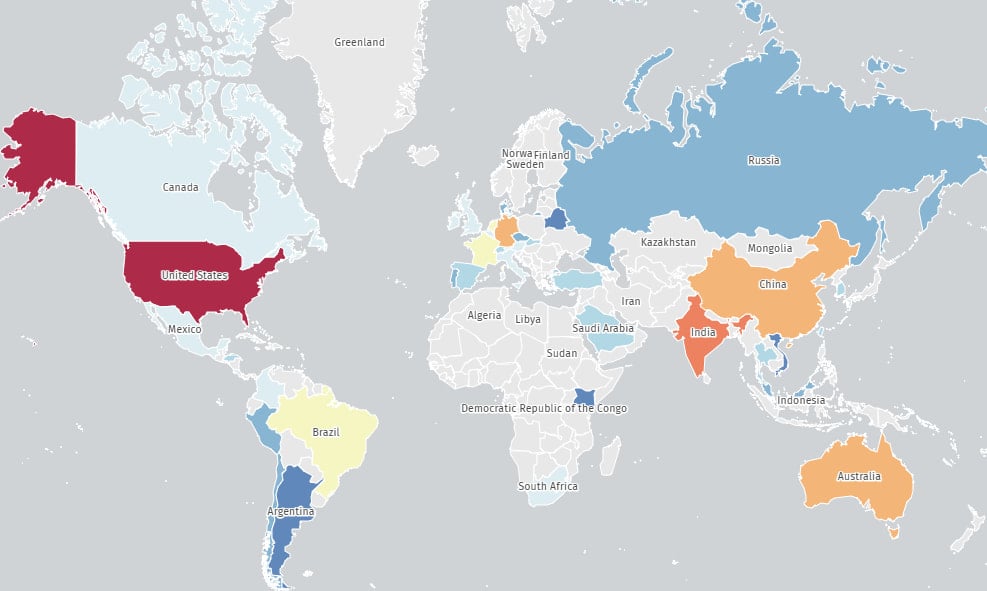
Supply: The Shadowserver Basis
Nevertheless, cyber protection search engine Onyphe paints a extra dire image, telling BleepingComputer that there are 1,284 weak servers uncovered on-line, with 474 already having been compromised with webshells.
“One thing like 20 Fortune 500/International 500 corporations are weak, and lots of them are compromised,” Onyphe CTO Patrice Auffret instructed BleepingComputer.
Researchers reported that the risk actors are using webshells with names like, “cache.jsp” and “helper.jsp.” Howver, Nextron Analysis says they’re additionally utilizing random names, making it tougher to search out weak Netweaver cases.
Whereas the variety of servers just isn’t large, the danger remains to be vital, given that enormous enterprises and multinational firms generally use SAP NetWeaver.
To deal with the danger, it’s endorsed that the newest safety replace be utilized by following the seller’s directions in this bulletin.
If unable to use the replace, the beneath mitigations are beneficial:
- Prohibit entry to the /developmentserver/metadatauploader endpoint.
- If Visible Composer just isn’t in use, take into account turning it off completely.
- Ahead logs to SIEM and scan for unauthorized recordsdata within the servlet path.
RedRays has additionally launched a scanner device for CVE-2025-31324 that may assist pinpoint dangers in massive environments.
BleepingComputer contacted SAP with additional questions concerning the lively exploitation and can replace the story with any response.


