Extra Contributor: Apaar Sanghi
Cisco Safe Firewall (CSF) is constantly including new options and integrations, with many latest enhancements involving logging and Splunk. One space of integration between CSF and Splunk that we labored on at Cisco Stay Melbourne concerned Enterprise Safety Content material Replace (ESCU) detections in Splunk Enterprise Safety (ES). On this weblog submit we’ll check out what Splunk ESCU detections are, some modifications we made to get these detections to work with our SOC logging configuration, and take a look at an instance of how we used these ESCU detections in our SOC workflows.
Splunk ES has round two dozen ESCU detections for Cisco Safe Firewall. These might be accessed from ES by navigating to Safety Content material > Content material Management after which trying to find ‘Safe Firewall’.
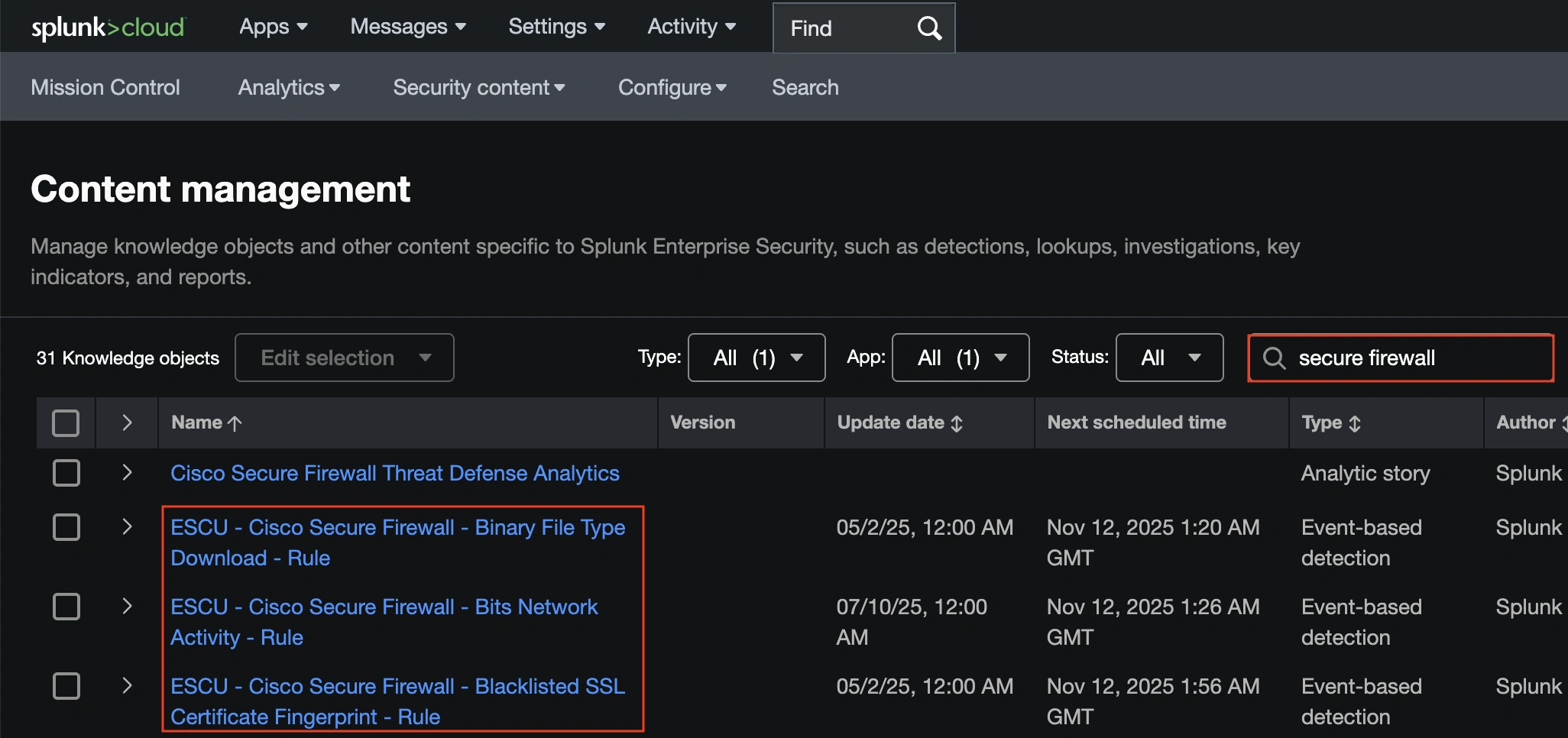

All ESCU detections for Safe Firewall reference the identical macro, ‘cisco_secure_firewall’.
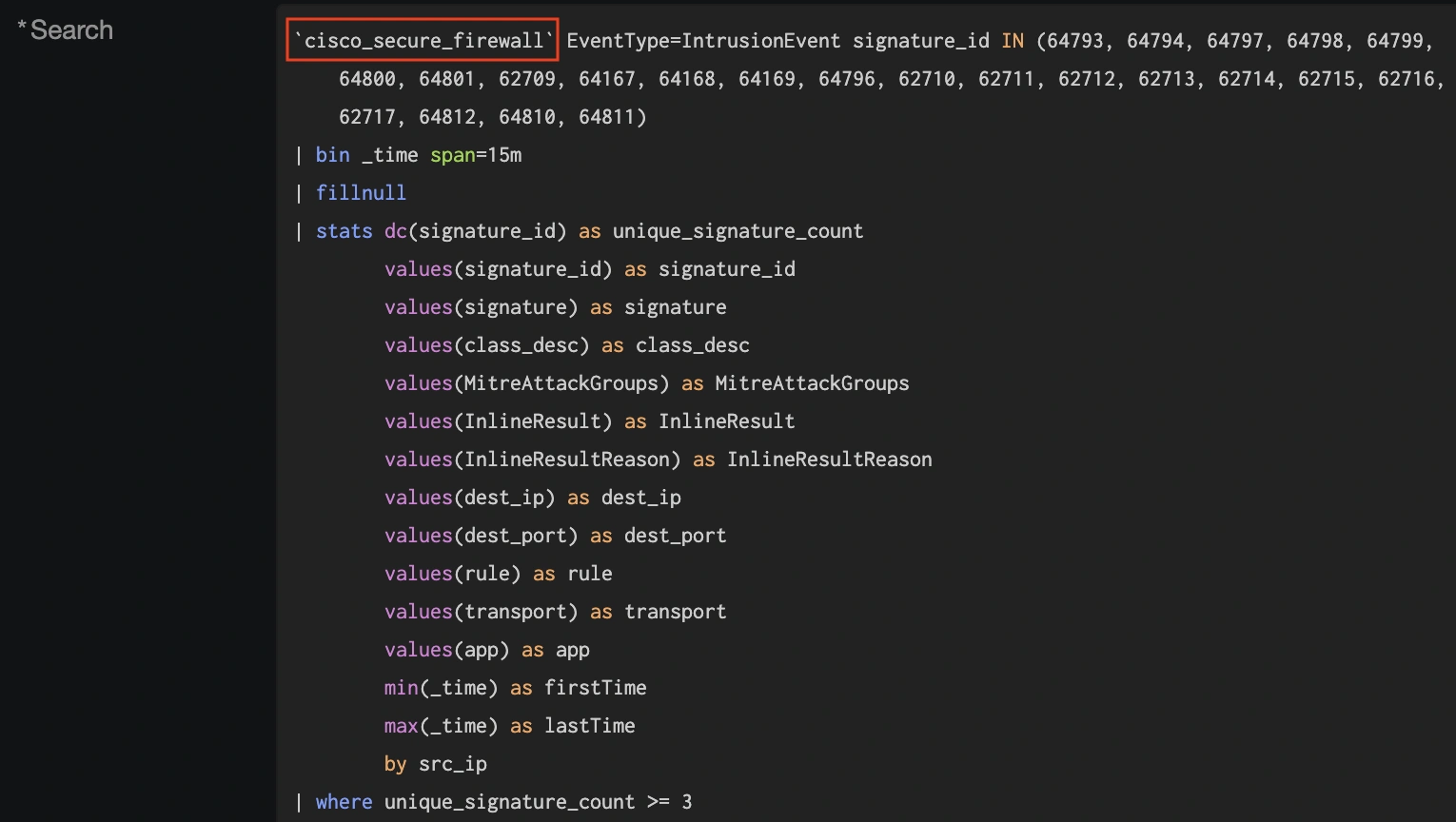

The default configuration for this macro references the eStreamer shopper, which is widespread for information ingest from CSF. Nevertheless, Cisco now recommends syslog for brand spanking new deployments, as syslog can ship higher ingest efficiency over eStreamer, and lots of enhancements to syslog output are included in our 10.0 launch and street mapped for future releases.
Within the Cisco SOC, we attempt to keep on the reducing fringe of configuration in order that we will take a look at new options, detections, and integrations. We transitioned our firewall log export to syslog a number of conferences in the past, and in Melbourne we determined to check the ESCU detections with syslog.
There are a number of methods we will do that.
- We will modify the prevailing ESCU detections to level to a brand new macro.
- We will clone the prevailing ESCU detections and set a brand new macro on the clones.
- we will go away the entire ESCU detections alone and easily change the underlying macro they reference.
We opted for choice 3 (although we did additionally do some customization by way of cloning). This required altering the macro pictured above by navigating to Settings > Superior Search after which clicking ‘Search macros’.

Looking for the macro from the ESCU detections will present the Definition is ready to sourcetype=”cisco:sfw:streamer”.
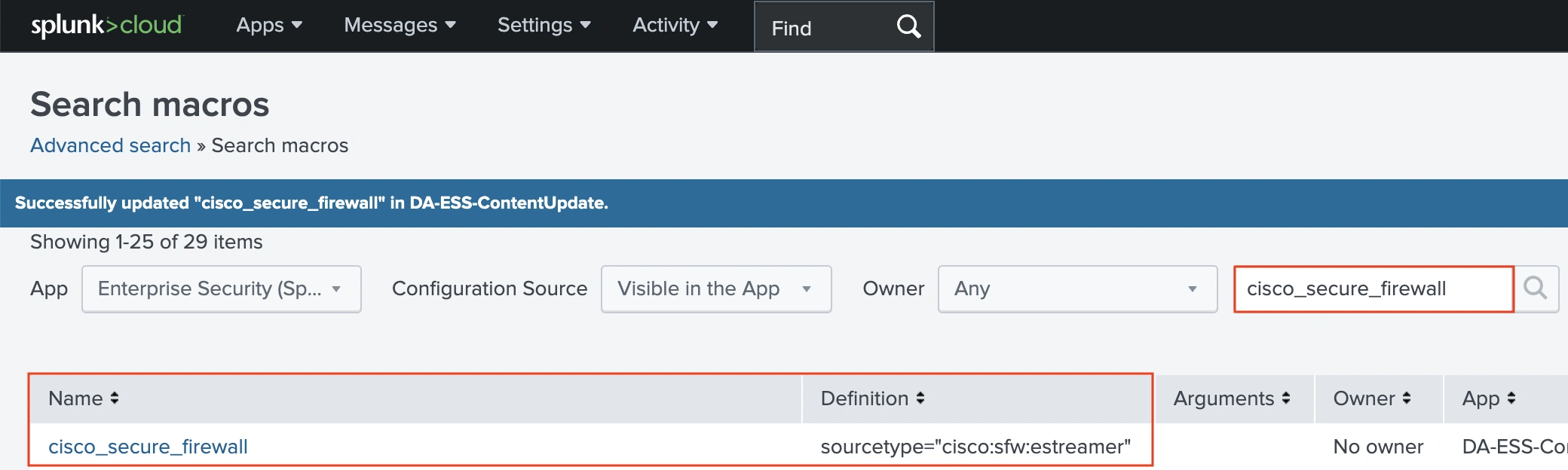

We will change this with the sourcetype for our syslog, and we additionally have to outline the index for our syslog. For the Melbourne SOC, our index is se_network_ftd.
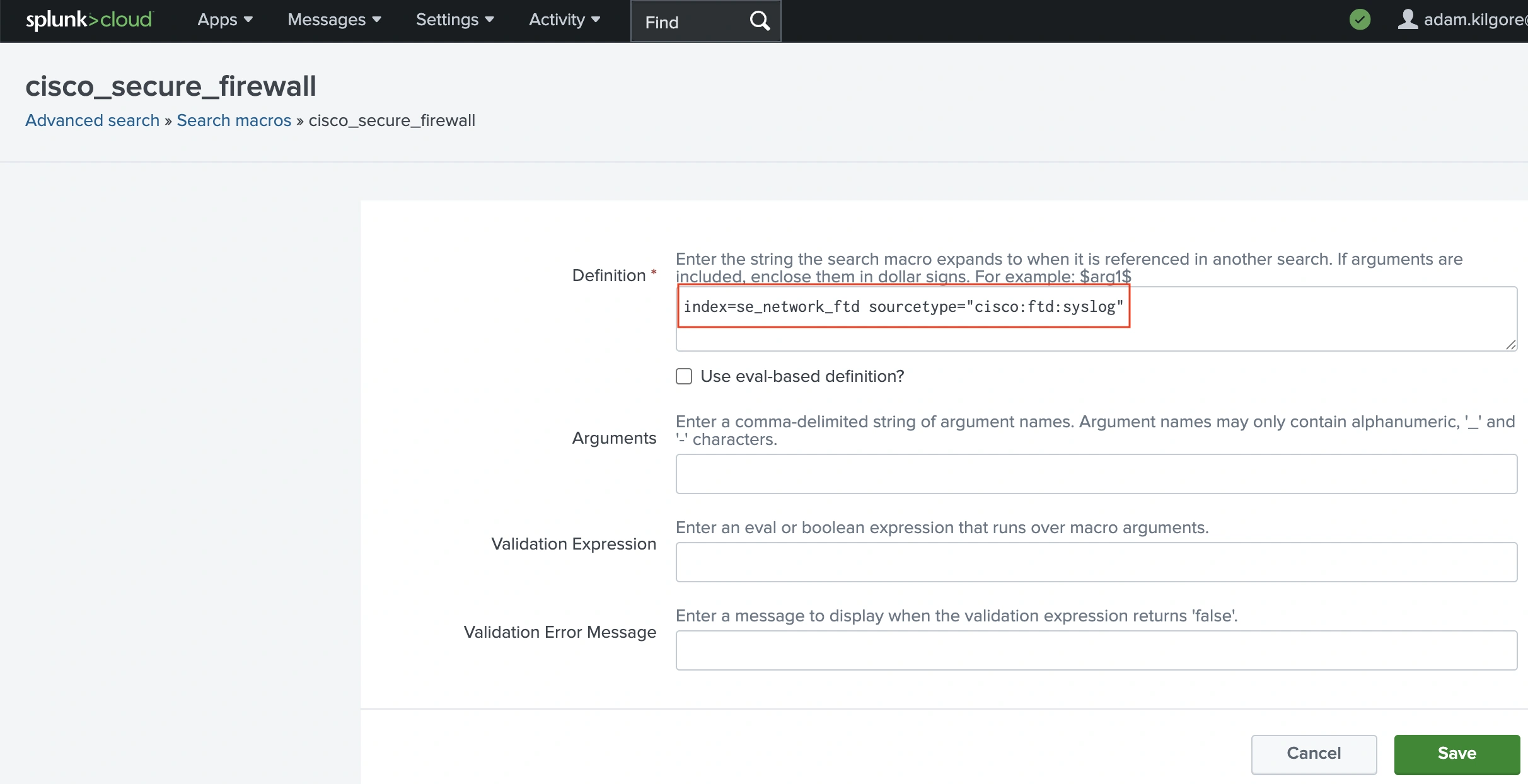

With this setting, the macro utilized by the entire Safe Firewall ESCU detections will now level on the index and sourcetype for our syslog occasions. The searches related to the ESCU detections will nonetheless work after switching from eStreamer to syslog as a result of the Cisco Safety TA makes use of Splunk’s schema-on-read method to supply the identical occasion schema throughout question for each eStreamer and syslog occasions.
Be aware: for organizations transitioning from eStreamer to syslog, the macro might be configured to drag from both eStreamer or syslog by utilizing an ‘or’ situation. For our index, this might seem like the next:
index=se_network_ftd AND (sourcetype=cisco:ftd:estreamer OR
sourcetype=cisco:ftd:syslog)Within the SOC we don’t decrypt attendee site visitors on function, so Encrypted Visibility Engine (EVE) occasions are extremely helpful as an Indicator of Compromise (IoC). One of many Splunk ESCU detections that we used includes EVE occasions instantly.


By default, this ESCU detection will match on a Safe Firewall connection occasion with EVE menace confidence above 80. Nevertheless, this detection will use the EVE occasion as an Intermediate Discovering, which raises the danger ranking of the concerned supply IP with out producing a full incident.
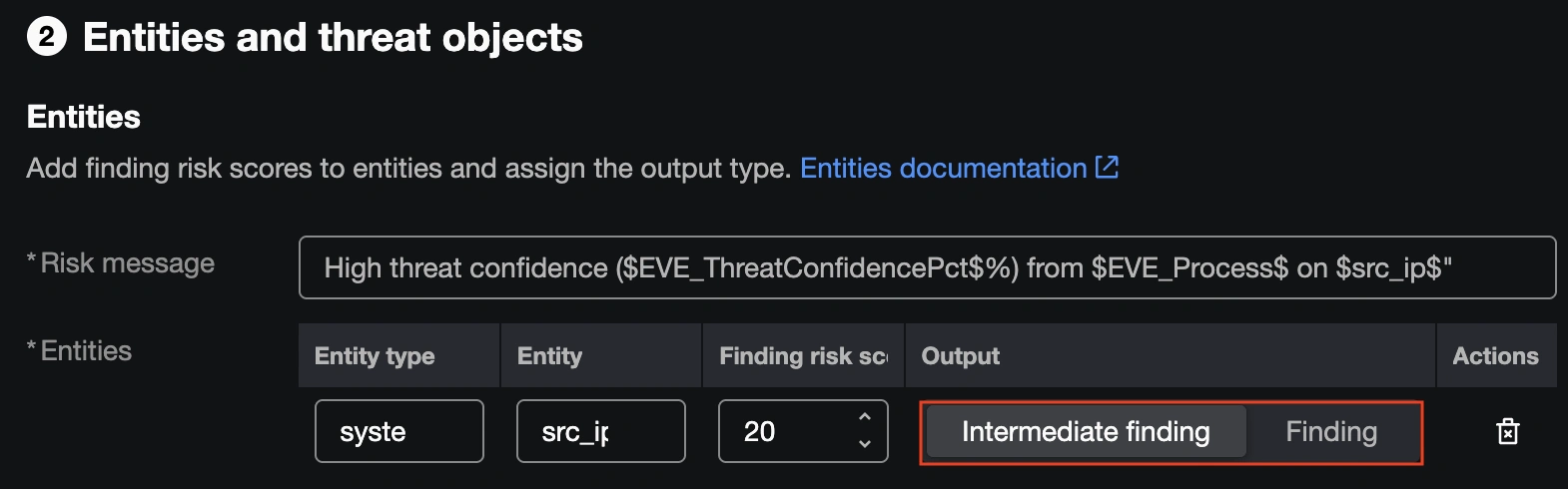

This would be the proper name for a lot of environments, however on the SOC we’ve a low sufficient quantity of excessive confidence EVE occasions and place sufficient worth on them to warrant selling them to full incidents. We opted to alter the setting to Discovering, so {that a} single Safe Firewall connection occasion with a excessive EVE menace confidence rating will generate a Discovering by itself.
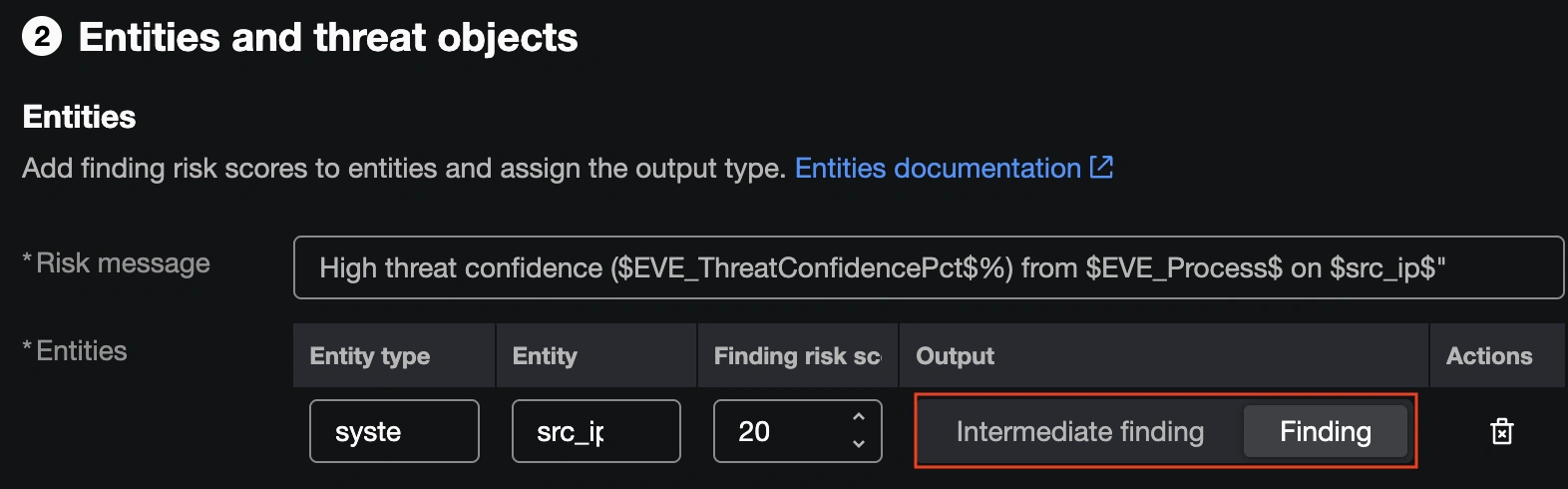

With the Discovering setting in place, all excessive confidence EVE occasions had been routinely promoted to Incidents in Splunk ES, guaranteeing we noticed them rapidly and will reply with an investigation.
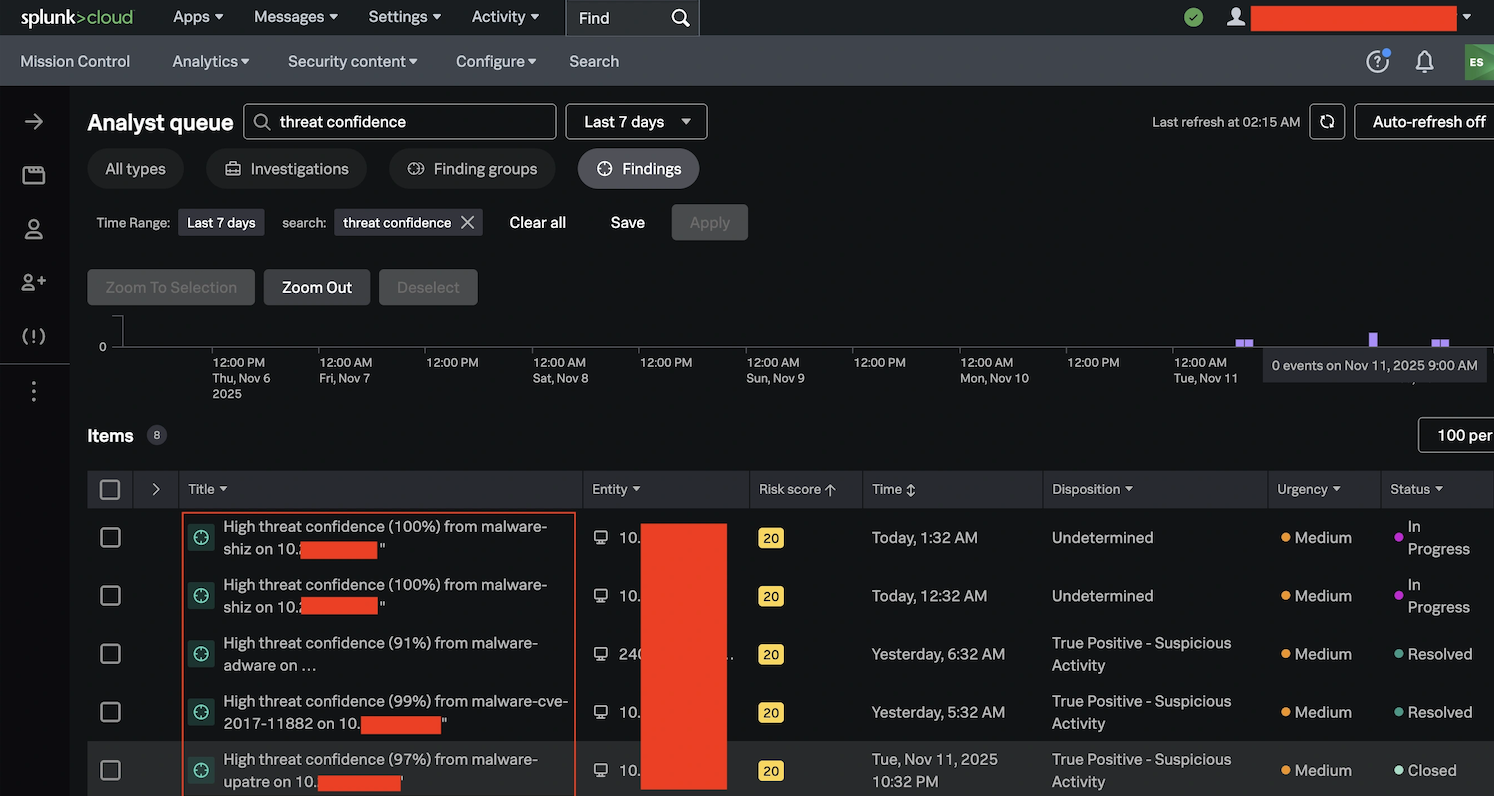

Whereas we run a lot of our incident investigations via Cisco XDR on the SOC, the convenience of use of this workflow and the Splunk ESCU detection capabilities proved to be a helpful software that we’ll increase at future conferences.
Take a look at the opposite blogs by my colleagues within the Cisco Stay APJC 2026 SOC.
We’d love to listen to what you assume! Ask a query and keep related with Cisco Safety on social media.
Cisco Safety Social Media


