
Information broke as we speak of a “mom of all breaches,” sparking large media protection full of warnings and fear-mongering. Nonetheless, it seems to be a compilation of beforehand leaked credentials stolen by infostealers, uncovered in information breaches, and by way of credential stuffing assaults.
To be clear, this isn’t a brand new information breach, or a breach in any respect, and the web sites concerned weren’t not too long ago compromised to steal these credentials.
As an alternative, these stolen credentials had been seemingly circulating for a while, if not for years. It was then collected by a cybersecurity agency, researchers, or risk actors and repackaged right into a database that was uncovered on the Web.
Cybernews, which found the briefly uncovered compilation, said it was saved in a format generally related to infostealer malware, although they didn’t share samples
An infostealer is malware that makes an attempt to steal credentials, cryptocurrency wallets, and different information from an contaminated gadget. Over time, infostealers have turn out to be a large downside, resulting in breaches worldwide.
Most of these malware impression each Home windows and Macs, and when executed, will collect all of the credentials it may possibly discover saved on a tool and save them in what known as a “log.”
An infostealer log is mostly an archive containing quite a few textual content recordsdata and different stolen information. The textual content recordsdata include lists of credentials stolen from browsers, recordsdata, and different functions.
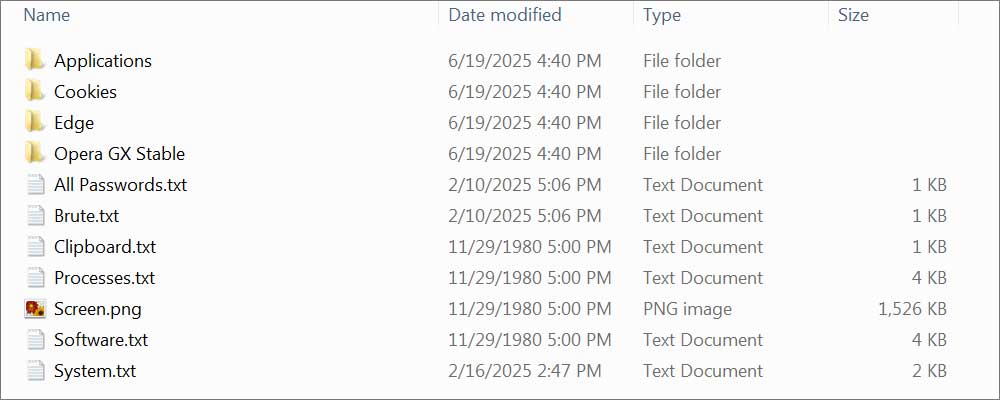
Supply: BleepingComputer
Stolen credentials are often saved one per line within the following format:
URL:username:password
Typically, the delimiter between every part is modified to a comma, semicolon, or sprint.
For instance, the next is how an infostealer will save credentials stolen from a tool to a log:
https://www.fb.com/:[email protected]:Databr3achFUd!
https://www.financial institution.com/login.php:jsmith:SkyIsFa11ing#
https://x.com/i/movement/login:[email protected]:StayCalmCarryOn
If somebody is contaminated with an infostealer and has a thousand credentials saved of their browser, the infostealer will steal all of them and retailer them within the log. These logs are then uploaded to the risk actor, the place the credentials can be utilized for additional assaults or offered on cybercrime marketplaces.
The infostealer downside has gotten so dangerous and pervasive that compromised credentials have turn out to be one of the vital frequent methods for risk actors to breach networks.
We now have a webinar subsequent month titled “Stolen credentials: The New Entrance Door to Your Community” that focuses on infostealers, compromised credentials, and the way organizations can shield themselves.
This downside has additionally led legislation enforcement worldwide to actively crack down on these cybercrime operations in latest actions, akin to “Operation Safe” and the disruption of LummaStealer.
As infostealers have turn out to be so plentiful and generally used, risk actors launch large compilations free of charge on Telegram, Pastebin, and Discord to achieve popularity among the many cybercrime neighborhood or as teasers to paid choices.
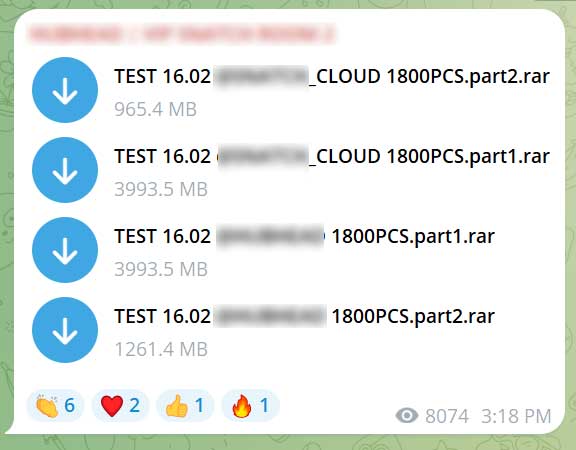
Supply: BleepingComputer
To see what number of passwords are given away free of charge, the only 1,261.4 MB file within the picture above contained over 64,000 credential pairs.
There are hundreds, if not tons of of hundreds, of equally leaked archives being shared on-line, leading to billions of credentials data launched free of charge.
Many of those free archives had been seemingly compiled into the huge database that was briefly uncovered and seen by Cybernews.
Comparable credential collections had been launched up to now, such because the RockYou2024 leak, with over 9 billion data, and “Colection #1,” which contained over 22 million distinctive passwords.
Regardless of the excitement, there is not any proof this compilation incorporates new or beforehand unseen information
What must you do?
So, now that you understand there was a large leak of credentials seemingly stolen via infostealers, information breaches, and credential-stuffing assaults, it’s possible you’ll be questioning what it is best to do.
A very powerful step is to undertake and keep good cybersecurity habits it is best to already be following.
When you’re involved that an infostealer is likely to be current in your laptop, scan your gadget with a trusted antivirus program earlier than altering any passwords. In any other case, newly entered credentials may very well be stolen as nicely.
When you’re assured your system is clear, concentrate on bettering your password hygiene.
Meaning utilizing a singular, robust password for each website you utilize, and counting on a password supervisor to maintain them organized and safe.
Nonetheless, even distinctive passwords will not make it easier to keep protected if you’re hacked, fall for a phishing assault, or set up malware.
Subsequently, it’s essential that you just additionally use two-factor authentication (2FA) together with an authentication app, like Microsoft Authenticator, Google Authenticator, or Authy, to handle your 2FA codes. Some password managers, like Bitwarden and 1Password, additionally embrace authentication performance, permitting you to make use of one software for each.
With 2FA enabled, even when a password at a website is compromised, risk actors can’t entry the account with out your 2FA code.
As a normal rule, it is best to keep away from utilizing SMS texts to obtain 2FA codes, as risk actors can conduct SIM-swapping assaults to hijack your telephone quantity and procure them.
As for this leak, with this many credentials leaked, there’s a probability one of many readers of this text can be listed within the compilation.
Nonetheless, do not panic and stress about it, working round altering all of your passwords. As an alternative, take this chance to enhance your cybersecurity habits.
To examine in case your credentials have appeared in identified breaches, think about using providers like Have I Been Pwned.
And should you use the identical password throughout a number of websites, now’s the time to change to distinctive ones.
That approach, leaks like this turn out to be far much less harmful to you.



