
Safety researchers have disclosed a brand new Safe Boot bypass tracked as CVE-2025-3052 that can be utilized to show off safety on PCs and servers and set up bootkit malware.
The flaw impacts practically each system that trusts Microsoft’s “UEFI CA 2011” certificates, which is just about all {hardware} that helps Safe Boot.
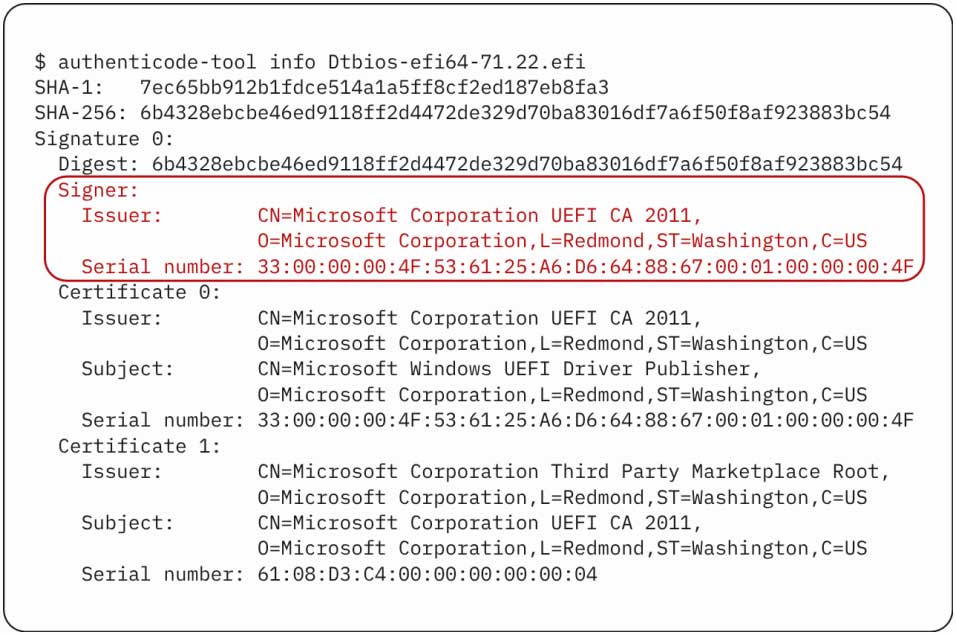
Binarly researcher Alex Matrosov found the CVE-2025-3052 flaw after discovering a BIOS-flashing utility signed with Microsoft’s UEFI signing certificates.
The utility was initially designed for rugged tablets however because it was signed with Microsoft’s UEFI certificates, it could actually run on any Safe Boot-enabled system.
Additional investigations found that the susceptible module had been circulating within the wild since a minimum of late 2022 and later uploaded to VirusTotal in 2024, the place Binarly noticed it.
Binarly disclosed the flaw to CERT/CC on February 26, 2025, with CVE-2025-3052 being mitigated right this moment as a part of the Microsoft June 2025 Patch Tuesday.
Nonetheless, throughout this course of, Microsoft decided that the flaw impacted 13 different modules, which had been added to the revocation database.
“In the course of the triage course of, Microsoft decided that the problem didn’t aect only a single module as initially believed, however truly 14 dierent modules,” explains Binarly.
“Because of this, the up to date dbx launched through the Patch Tuesday on June 10, 2025 accommodates 14 new hashes.”
The Safe Boot bypass
The flaw is attributable to a authentic BIOS replace utility signed with Microsoft’s UEFI CA 2011 certificates, which is trusted on most trendy techniques using UEFI firmware.
Supply: Binarly
This utility reads a user-writable NVRAM variable (IhisiParamBuffer) with out validating it. If an attacker has admin rights to an working system, they’ll modify this variable so arbitrary information is written to reminiscence areas through the UEFI boot course of. That is completed earlier than the working system, and even the kernel, is loaded.
Utilizing this vulnerability, Binarly created a proof-of-concept exploit to zero out the ‘gSecurity2’ world variable, which is used to implement Safe Boot.
“For our proof of idea (PoC), we selected to overwrite the worldwide variable gSecurity2,” explains the Binarly report.
“This variable holds a pointer to the Security2 Architectural Protocol, which the LoadImage operate makes use of to implement Safe Boot. By setting it to zero, we eectively disable Safe Boot, permitting the execution of any unsigned UEFI modules.”
As soon as disabled, attackers can set up bootkit malware that may cover from the working system and switch off additional security measures.
To repair CVE-2025-3052, Microsoft has added the affected module hashes to the Safe Boot dbx revocation checklist. Binarly and Microsoft urge customers to put in the up to date dbx file instantly by right this moment’s safety updates to guard their units.
Additionally right this moment, one other Safe Boot bypass affecting UEFI-compatible firmware based mostly on Insyde H2O was disclosed by Nikolaj Schlej. The flaw, dubbed Hydroph0bia and tracked as CVE-2025-4275, was reported to Insyde and patched 90 days after disclosure.
Binarly has shared a video demonstrating how their PoC can disable Safe Boot and trigger a message to show earlier than the working system boots.



