
A brand new variant of the Mirai malware botnet is exploiting a command injection vulnerability in TBK DVR-4104 and DVR-4216 digital video recording gadgets to hijack them.
The flaw, tracked beneath CVE-2024-3721, is a command injection vulnerability disclosed by safety researcher “netsecfish” in April 2024.
The proof-of-concept (PoC) the researcher revealed on the time got here within the type of a specifically crafted POST request to a weak endpoint, reaching shell command execution via the manipulation of sure parameters (mdb and mdc).
Kaspersky now stories having caught lively exploitation of CVE-2024-3721 in its Linux honeypots from a brand new Mirai botnet variant utilizing netsecfish’s PoC.
The attackers leverage the exploit to drop an ARM32 malware binary, which establishes communication with the command and management (C2) server to enlist the gadget to the botnet swarm. From there, the gadget is probably going used to conduct distributed denial of service (DDoS) assaults, proxy malicious visitors, and different habits.
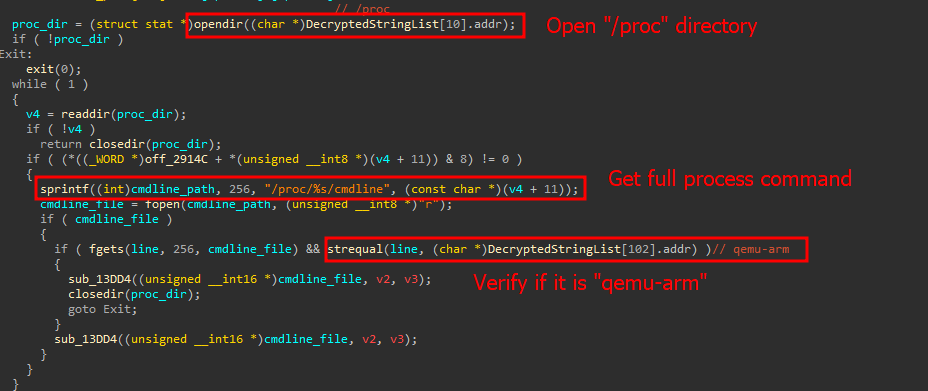
Supply: Kaspersky
Assault impression and fixes
Though netsecfish reported final 12 months that there have been roughly 114,000 internet-exposed DVRs weak to CVE-2024-3721, Kaspersky’s scans present roughly 50,000 uncovered gadgets, which continues to be vital.
Most infections the Russian cybersecurity agency sees as being related to the newest Mirai variant impression China, India, Egypt, Ukraine, Russia, Turkey, and Brazil. Nonetheless, that is based mostly on Kaspersky’s telemetry, and as its shopper safety merchandise are banned in lots of nations, this will not precisely mirror the botnet’s focusing on focus.
At the moment, it’s unclear if the seller, TBK Imaginative and prescient, has launched safety updates to deal with the CVE-2024-3721 flaw or if it stays unpatched. BleepingComputer contacted TBK to ask about this, however we’re nonetheless ready for his or her response.
It is value noting that DVR-4104 and DVR-4216 have been extensively re-branded beneath the Novo, CeNova, QSee, Pulnix, XVR 5 in 1, Securus, Night time OWL, DVR Login, HVR Login, and MDVR manufacturers, so the supply of patches for impacted gadgets is a posh matter.
The researcher who disclosed the TBK Imaginative and prescient flaw found different flaws that fueled exploitation in opposition to end-of-life gadgets final 12 months.
Particularly, netsecfish has disclosed a backdoor account problem and a command injection vulnerability impacting tens of 1000’s of EoL D-Hyperlink gadgets in 2024.
Energetic exploitation was detected in each instances only some days after the PoC’s disclosure. This exhibits how rapidly malware authors incorporate public exploits into their arsenal.



