
A number of Fortinet FortiWeb situations lately contaminated with net shells are believed to have been compromised utilizing public exploits for a lately patched distant code execution (RCE) flaw tracked as CVE-2025-25257.
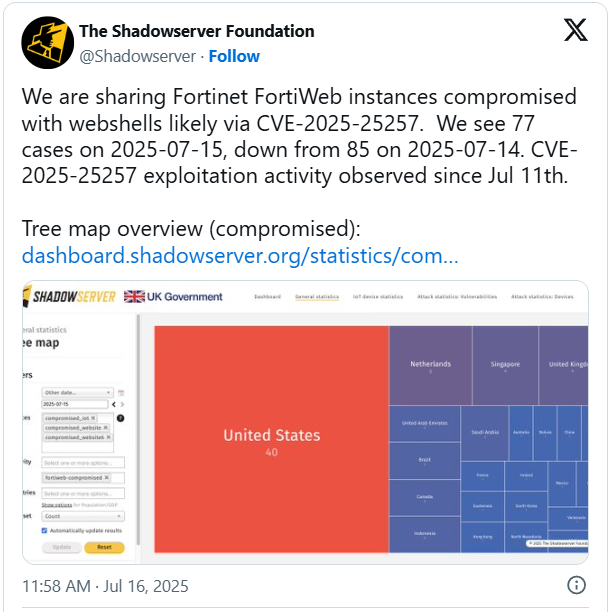
Information of the exploitation exercise comes from menace monitoring platform The Shadowserver Basis, which noticed 85 infections on July 14 and 77 on the subsequent day.
The researchers reported that these Fortinet FortiWeb situations are believed to be compromised by means of the CVE-2025-25257 flaw.
CVE-2025-25257 is a essential pre-authenticated RCE by way of SQL injection (SQLi) affecting FortiWeb 7.6.0 by means of 7.6.3, 7.4.0 by means of 7.4.7, 7.4.0 by means of 7.4.7, and seven.0.0 by means of 7.0.10.
Fortinet launched patches on July 8, 2025, urging customers to improve to FortiWeb 7.6.4, 7.4.8, 7.2.11, or 7.0.11 and later variations of every department.
“An improper neutralization of particular components utilized in an SQL command (‘SQL Injection’) vulnerability in FortiWeb might permit an unauthenticated attacker to execute unauthorized SQL code or instructions by way of crafted HTTP or HTTPs requests,” defined Fortinet.
On July 11, exploits have been made public by cybersecurity agency WatchTowr, and a co-discoverer of the flaw, “defective *ptrrr.” These exploits demonstrated strategies for planting webshells or opening reverse shells on unpatched endpoints.
The exploitation includes performing SQLi by way of crafted Authorization headers in HTTP requests despatched to /api/cloth/gadget/standing, which writes a malicious .pth file into Python’s ‘site-packages.’
A professional FortiWeb CGI script (/cgi-bin/ml-draw.py) is then accessed remotely, inflicting the code within the malicious .pth file to be executed and attaining distant code execution on the gadget.
On the time, there was no proof of lively exploitation within the wild, however the launch of public exploits made patching essential for directors.
At the moment’s affirmation of lively exploitation by The Shadowserver Basis might be seen as a wake-up name for many who have but to put in the newest software program on their gadgets.
In line with the menace intelligence group, 223 FortiWeb administration interfaces have been nonetheless uncovered as of yesterday, though there is no visibility into the model they run.
Of the compromised endpoints, most (40) are positioned in america, adopted by the Netherlands (5), Singapore (4), and the UK (4).
FortiWeb is a Net Software Firewall (WAF) utilized by massive enterprises, authorities businesses, and managed safety service suppliers to dam and detect undesirable HTTP visitors.
If upgrading to a safe model instantly is not possible, it is suggested to show off the HTTP/HTTPS administrative interface to limit entry to the weak element (/api/cloth/gadget/standing).



