
A brand new “Convey Your Personal Installer” EDR bypass approach is exploited in assaults to bypass SentinelOne’s tamper safety characteristic, permitting risk actors to disable endpoint detection and response (EDR) brokers to put in the Babuk ransomware.
This system exploits a niche within the agent improve course of that permits the risk actors to terminate operating EDR brokers, leaving gadgets unprotected.
The assault was found by John Ailes and Tim Mashni of Aon’s Stroz Friedberg Incident Response group throughout an engagement with a buyer who suffered a ransomware assault earlier this 12 months.
The approach doesn’t depend on third-party instruments or drivers like we usually see with EDR bypasses however as a substitute abuses the SentinelOne installer itself.
SentinelOne recommends clients allow the “On-line Authorization” setting, which is turned off by default, to mitigate this assault.
“We need to get the phrase out to make sure SentinelOne’s clients know to allow Native Improve safety,” John Ailes, Supervisor, Aon’s Stroz Friedberg DFIR, informed BleepingComputer.
“We have investigated environments with SentinelOne since their steerage was despatched to clients and have seen shoppers that also do not have it enabled. On the finish of the day, getting the phrase out to mitigate this bypass is crucial factor.”
Actively exploited in ransomware assaults
The Stroz Friedberg researchers clarify that SentinelOne protects its EDR agent with an anti-tamper safety characteristic that requires a handbook motion within the SentinelOne administration console or a novel code to take away an agent.
Nonetheless, like many different software program installers, when putting in a unique model of the agent, the SentinelOne installer terminates any related Home windows processes simply earlier than present information are overwritten with the brand new model.
Risk actors found they may exploit this small window of alternative by operating a respectable SentinelOne installer after which forcefully terminating the set up course of after it shuts down the operating agent’s providers, leaving gadgets unprotected.
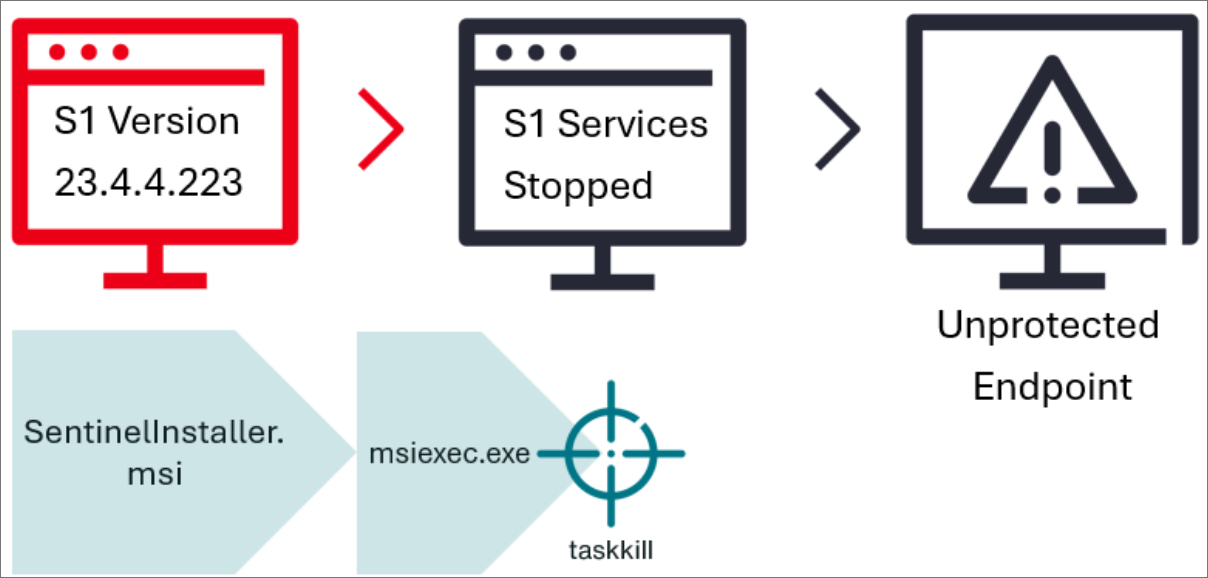
Supply: Stroz Friedberg
Earlier this 12 months, Stroz Friedberg was engaged to research an assault on a buyer’s community, with logs exhibiting that the attackers gained administrative entry to the shopper’s community by way of a vulnerability.
The attackers then used this new bypass by terminating the SentinelOne Home windows Installer (“msiexec.exe“) course of earlier than it may set up and launch the brand new model of the agent. With protections disabled on the gadget, the risk actors have been then in a position to deploy the ransomware.
In a dialog with BleepingComputer, Ailes stated that risk actors can make the most of new or older variations of the agent to conduct this assault, so even when the newest model runs on gadgets, they’re nonetheless susceptible.
“Stroz Friedberg additionally noticed that the host went offline within the SentinelOne administration console shortly after the installer was terminated,” warns Stroz Friedberg’s report.
“Additional testing confirmed that the assault was profitable throughout a number of variations of the SentinelOne agent and was not depending on the particular variations noticed on this incident.”
Stroz Friedberg responsibly disclosed this assault to SentinelOne, who privately shared mitigations with clients in January 2025.
The mitigation is to allow the “On-line Authorization” characteristic within the Sentinel Coverage settings that, when enabled, requires approval from the SentinelOne administration console earlier than native upgrades, downgrades, or uninstalls of the agent can happen.
SentinelOne additionally shared Stroz Friedberg’s advisory on this new approach with all different main EDR distributors, in case they have been additionally affected.
Palo Alto Networks confirmed to Stroz Friedberg that this assault didn’t influence its EDR software program.



