
Russian state-sponsored espionage group Midnight Blizzard is behind a brand new spear-phishing marketing campaign focusing on diplomatic entities in Europe, together with embassies.
Midnight Blizzard, aka ‘Cozy Bear’ or ‘APT29,’ is a state-sponsored cyberespionage group linked to Russia’s International Intelligence Service (SVR).
Based on Verify Level Analysis, the brand new marketing campaign introduces a beforehand unseen malware loader known as ‘GrapeLoader,’ and a brand new variant of the ‘WineLoader’ backdoor.
A pour of malware
The phishing marketing campaign began in January 2025 and begins with an e-mail spoofing a Ministry of International Affairs, despatched from ‘bakenhof[.]com’ or ‘silry[.]com,’ inviting the recipient to a wine-tasting occasion.
The e-mail incorporates a malicious hyperlink that, if the sufferer focusing on situations are met, triggers the obtain of a ZIP archive (wine.zip). If not, it redirects victims to the legit Ministry web site.
The archive incorporates a legit PowerPoint executable (wine.exe), a legit DLL file required for this system to run, and the malicious GrapeLoader payload (ppcore.dll).
The malware loader is executed by way of DLL sideloading, which collects host information, establishes persistence by way of Home windows Registry modification, and contacts the command-and-control (C2) to obtain the shellcode it hundreds in reminiscence.
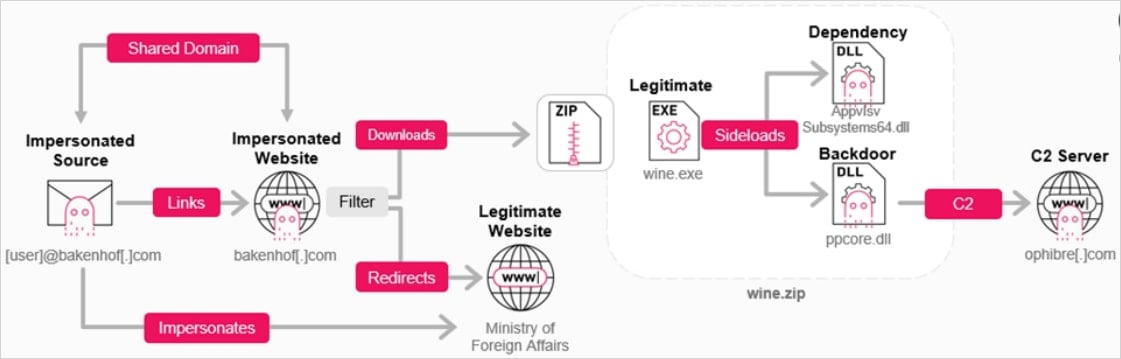
Supply: Verify Level
GrapeLoader possible replaces the beforehand used first-stage HTA loader ‘RootSaw,’ being stealthier and extra refined.
Verify Level highlights its use of ‘PAGE_NOACCESS’ reminiscence protections and 10-second delay earlier than working shellcode by way of ‘ResumeThread’ to cover malicious payload execution from antivirus and EDR scanners.
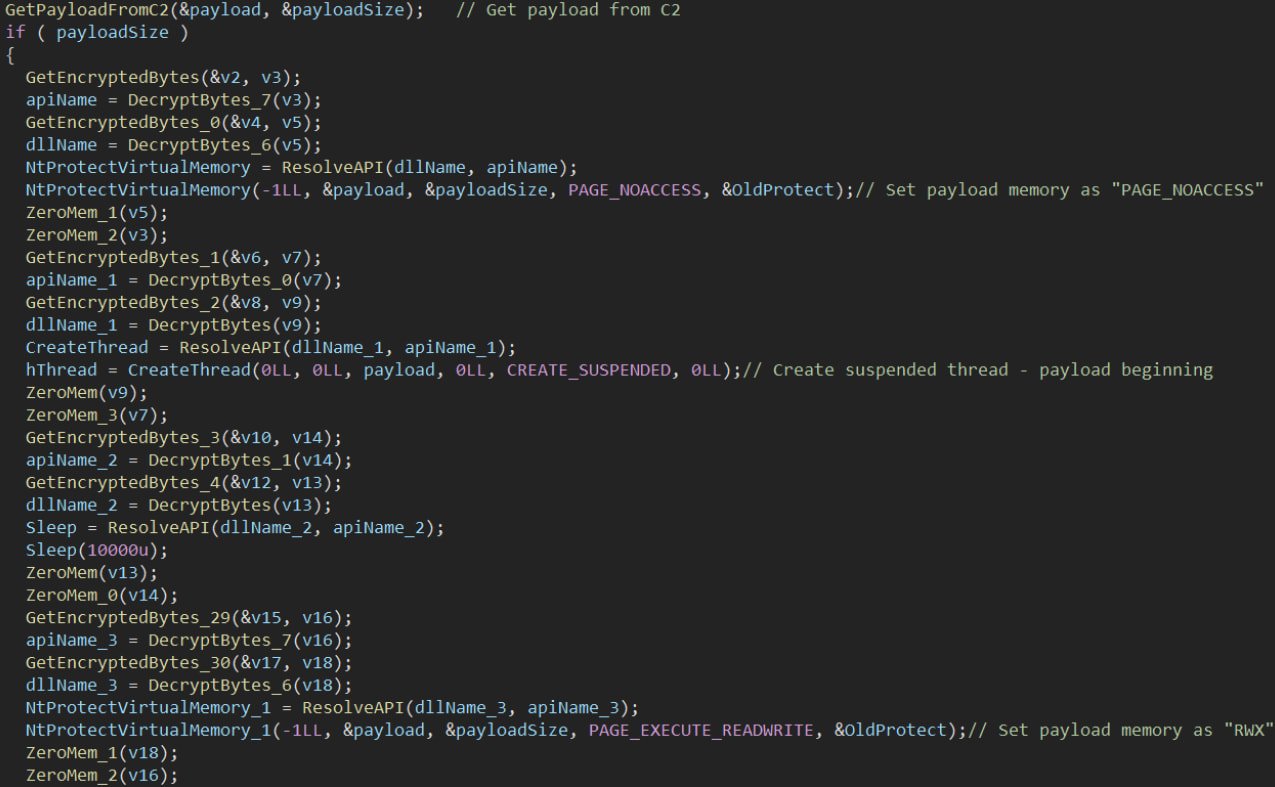
Supply: Verify Level
GrapeLoader’s essential duties on this marketing campaign are stealthy reconnaissance and supply of WineLoader, which arrives as a trojanized VMware Instruments DLL file.
A full-bodied backdoor
WineLoader is a modular backdoor that gathers detailed host info and facilitates espionage operations.
The collected information consists of: IP addresses, identify of the method it runs on, Home windows person identify, Home windows machine identify, Course of ID, and privilege degree.
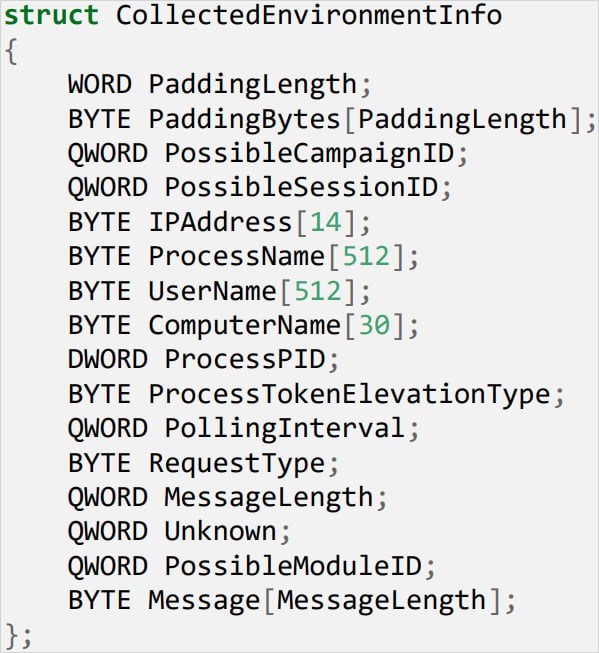
Supply: Verify Level
This info will help establish sandbox environments and consider the goal for dropping follow-up payloads.
The brand new variant noticed within the newest APT29 marketing campaign is closely obfuscated utilizing RVA duplication, export desk mismatches, and junk directions to make it tougher to reverse engineer.
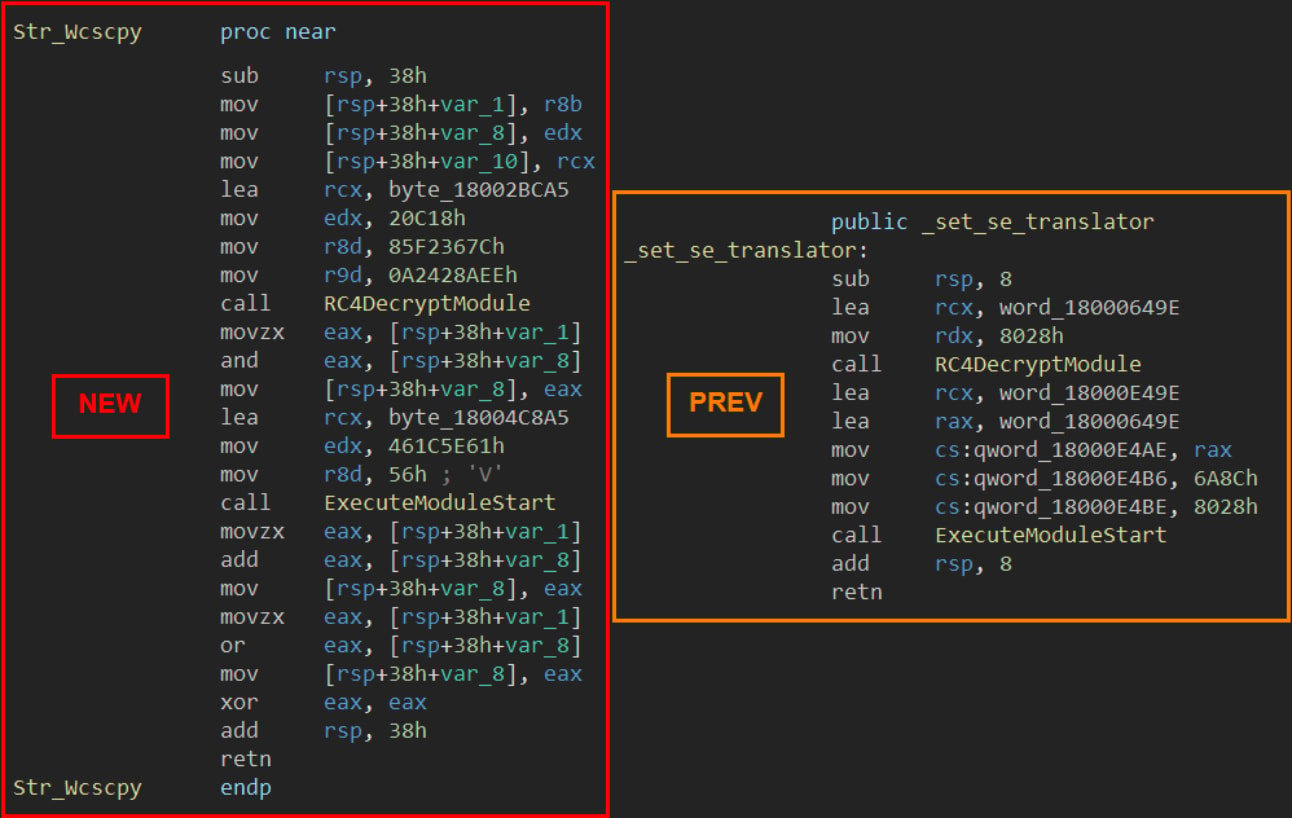
Supply: Verify Level
Verify Level notes that string obfuscation within the new WineLoader variant performs a key anti-analysis function, having considerably advanced in comparison with older variations.
“Beforehand, automated instruments like FLOSS might simply extract and deobfuscate strings from an unpacked WINELOADER pattern,” clarify the researchers.
“The improved implementation within the new variant disrupts this course of, making automated string extraction and deobfuscation fail.”
Because of the marketing campaign being extremely focused and the malware working fully in reminiscence, Verify Level was unable to retrieve WineLoader’s full second-stage payload or extra plugins, so the complete spectrum of its capabilities or tailor-made nature per sufferer stays blurry.
Verify Level’s findings present that APT29‘s ways and toolset evolve, getting stealthier and extra superior, requiring multi-layered defenses and heightened vigilance to detect and cease.


