
Menace actors are abusing the ‘Google Apps Script’ improvement platform to host phishing pages that seem respectable and steal login credentials.
This new pattern was noticed by safety researchers at Cofense, who warn that the fraudulent login window is “fastidiously designed to seem like a respectable login display screen.”
“The assault makes use of an e mail masquerading as an bill, containing a hyperlink to a webpage that makes use of Google Apps Script, a improvement platform built-in throughout Google’s suite of merchandise,” Cofense explains.
“By internet hosting the phishing web page inside Google’s trusted atmosphere, attackers create an phantasm of authenticity. This makes it simpler to trick recipients into handing over delicate data.”
Reliable service abuse
Google Apps Script is a JavaScript-based cloud scripting platform from Google that permits customers to automate duties and prolong the performance of Google Workspace merchandise like Google Sheets, Docs, Drive, Gmail, and Calendar.
These scripts run on a trusted Google area underneath “script.google.com,” which is on the allowlist of most safety merchandise.
Attackers write a Google Apps Script that shows a faux login web page to seize the credentials victims enter. The info is exfiltrated to the attacker’s server by way of a hidden request.
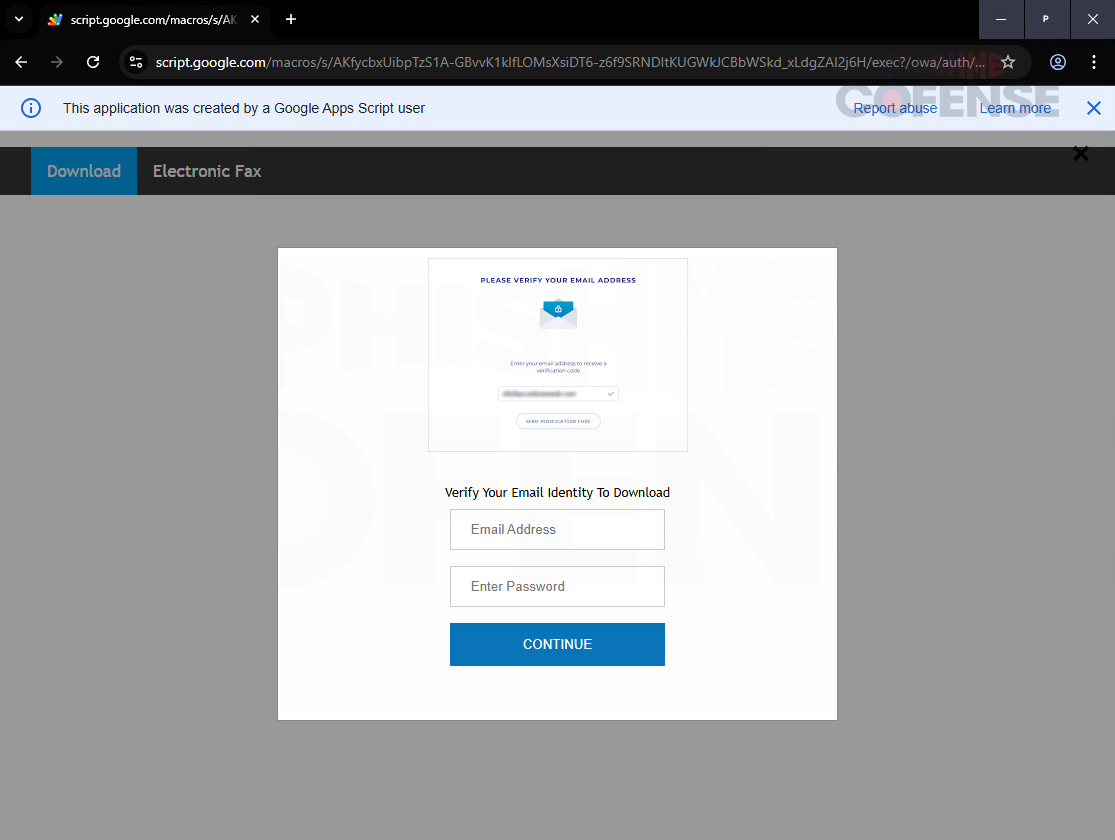
Supply: Cofense
Because the platform permits anybody with an account to publish a script as a public internet app, giving it a Google area, the risk actors can simply share it with the victims by way of a phishing e mail that received’t set off any warnings.
The phishing e mail incorporates an bill cost or tax-related name to motion for the recipient, linking to the malicious Google-hosted phishing web page.
.jpg)
Supply: Cofense
After the sufferer enters their username and password, they’re redirected to the respectable service that was spoofed to decrease suspicion and provides risk actors time to take advantage of the stolen knowledge.
Google Apps Script seems to be the brand new focus of phishing actors that search for respectable platforms to abuse for evasion and operational effectivity.
On this case, it additionally provides the attackers the pliability to remotely modify their script with out having to resend a brand new hyperlink, switching to a special lure with out a lot effort.
An efficient protection measure can be to configure e mail safety to scrutinize cloud service hyperlinks and, if potential, block entry to Google Apps Script URLs altogether, or no less than flag them as doubtlessly harmful.
BleepingComputer has contacted Google to ask in the event that they plan to implement any anti-abuse measures in response to Cofense’s findings, however we’ve not heard again as of publication.



