
The information-theft extortion group often called Luna Moth, aka Silent Ransom Group, has ramped up callback phishing campaigns in assaults on authorized and monetary establishments in the USA.
In accordance with EclecticIQ researcher Arda Büyükkaya, the final word purpose of those assaults is information theft and extortion.
Luna Moth, recognized internally as Silent Ransom Group, are menace actors who beforehand carried out BazarCall campaigns as a technique to acquire preliminary entry to company networks for Ryuk, and later, Conti ransomware assaults.
In March 2022, as Conti began to close down, the BazarCall menace actors separated from the Conti syndicate and fashioned a new operation referred to as Silent Ransom Group (SRG).
Luna Moths’s newest assaults contain impersonating IT assist by e-mail, pretend websites, and telephone calls, and rely solely on social engineering and deception, with no ransomware deployment seen in any of the instances.
“As of March 2025, EclecticIQ assesses with excessive confidence that Luna Moth has probably registered not less than 37 domains by GoDaddy to assist its callback-phishing campaigns,” reads the EclecticIQ report.
“Most of those domains impersonate IT helpdesk or assist portals for main U.S. legislation corporations and monetary providers corporations, utilizing typosquatted patterns.”
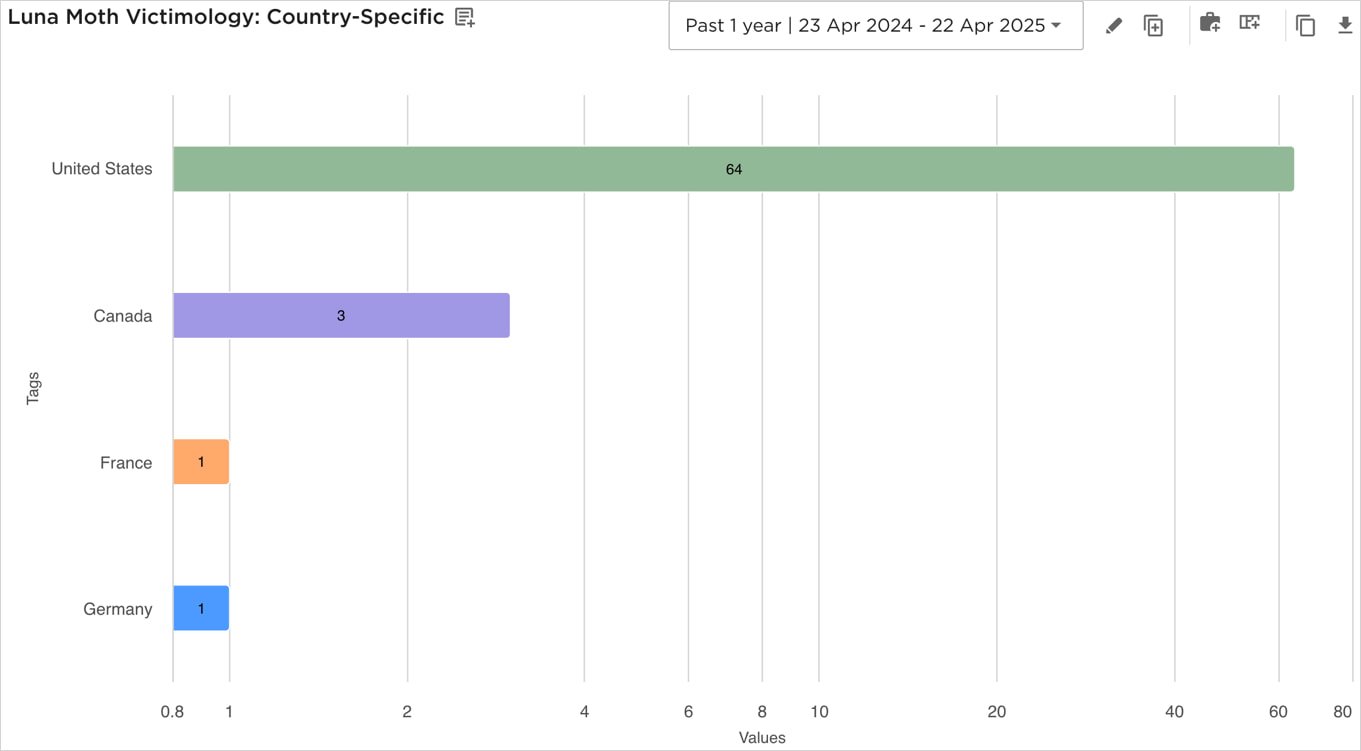
Supply: EclecticIQ
The most recent exercise noticed by EclecticIQ begins in March 2025, concentrating on U.S.-based organizations with malicious emails that comprise pretend helpdesk numbers recipients are urged to name to resolve non-existent issues.
A Luna Moth operator solutions the decision, impersonating IT employees, and convinces the sufferer to put in distant monitoring & administration (RMM) software program from pretend IT assist desk websites that provides the attackers distant entry to their machine.
The pretend assist desk websites make the most of domains that observe naming patterns like [company_name]-helpdesk.com and [company_name]helpdesk.com.
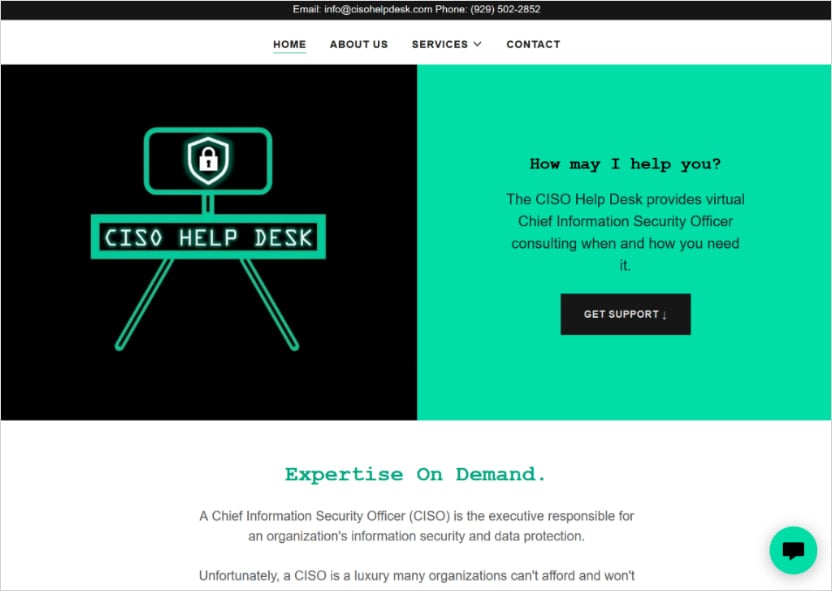
Supply: EclecticIQ
Some instruments abused in these assaults are Syncro, SuperOps, Zoho Help, Atera, AnyDesk, and Splashtop. These are professional, digitally signed instruments, in order that they’re unlikely to set off any warnings for the sufferer.
As soon as the RMM instrument is put in, the attacker has hands-on keyboard entry, permitting them to unfold to different gadgets and search native information and shared drives for delicate information.
Having situated precious information, they exfiltrate them to attacker-controlled infrastructure utilizing WinSCP (by way of SFTP) or Rclone (cloud syncing).
After the info is stolen, Luna Moth contacts the victimized group and threatens to leak it publicly on its clearweb area until they pay a ransom. The ransom quantity varies per sufferer, starting from one to eight million USD.
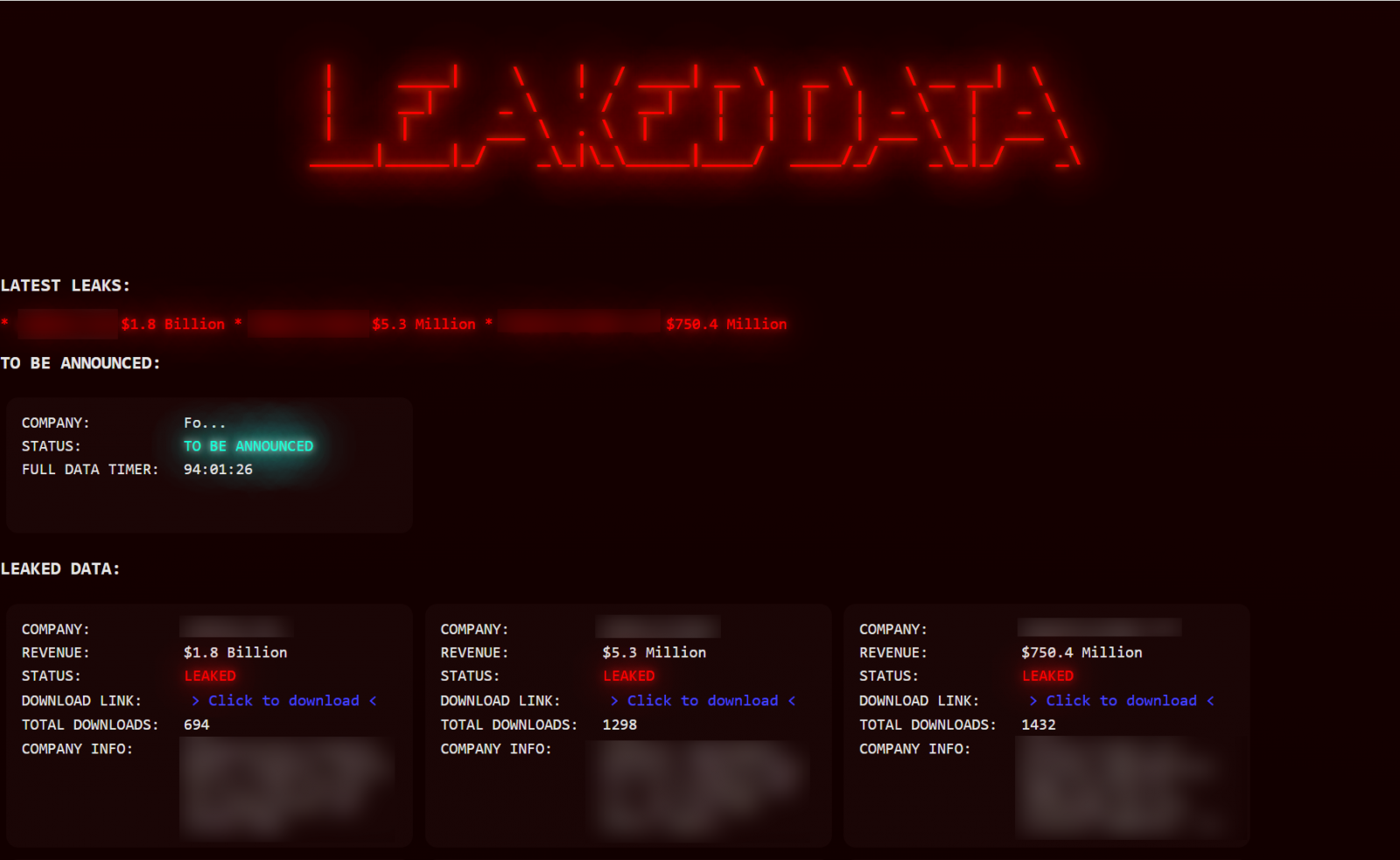
Supply: BleepingComputer
Büyükkaya feedback on the stealth of those assaults, noting that they contain no malware, malicious attachments, or hyperlinks to malware-ridden websites. The victims merely set up an RMM instrument themselves, considering they’re receiving assist desk assist.
Because the enterprise generally makes use of these RMM instruments, they aren’t flagged by safety software program as malicious and are allowed to run.
Indicators of compromise (IoCs), together with IP addresses and phishing domains that ought to be added to a blocklist, can be found on the backside of EclecticIQ’s report.
Other than the domains, it’s also beneficial to contemplate proscribing the execution of RMM instruments that aren’t utilized in a company’s surroundings.



