
The Lumma infostealer malware operation is progressively resuming actions following an enormous regulation enforcement operation in Might, which resulted within the seizure of two,300 domains and elements of its infrastructure.
Though the Lumma malware-as-a-service (MaaS) platform suffered vital disruption from the regulation enforcement motion, as confirmed by early June reviews on infostealer exercise, it did not shut down.
The operators instantly acknowledged the state of affairs on XSS boards, however claimed that their central server had not been seized (though it had been remotely wiped), and restoration efforts had been already underway.
Supply: Pattern Micro
Step by step, the MaaS constructed up once more and regained belief inside the cybercrime group, and is now facilitating infostealing operations on a number of platforms once more.
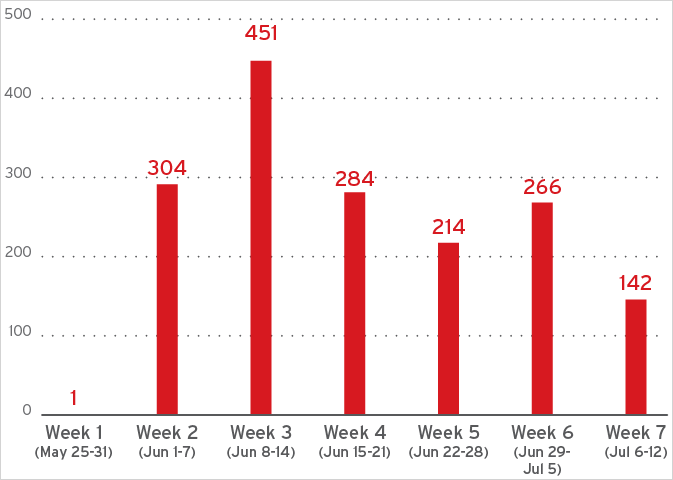
In line with Pattern Micro analysts, Lumma has virtually returned to pre-takedown exercise ranges, with the cybersecurity agency’s telemetry indicating a speedy rebuilding of infrastructure.
“Following the regulation enforcement motion in opposition to Lumma Stealer and its related infrastructure, our staff has noticed clear indicators of a resurgence in Lumma’s operations,” reads the Pattern Micro report.
“Community telemetry signifies that Lumma’s infrastructure started ramping up once more inside weeks of the takedown.”
Supply: Pattern Micro
Pattern Micro reviews that Lumma nonetheless makes use of official cloud infrastructure to masks malicious visitors, however has now shifted from Cloudflare to different suppliers, most notably the Russian-based Selectel, to keep away from takedowns.
The researchers have highlighted 4 distribution channels that Lumma presently makes use of to attain new infections, indicating a full-on return to multifaceted concentrating on.
- Pretend cracks/keygens: Pretend software program cracks and keygens are promoted by way of malvertising and manipulated search outcomes. Victims are directed to misleading web sites that fingerprint their system utilizing Site visitors Detection Programs (TDS) earlier than serving the Lumma Downloader.
- ClickFix: Compromised web sites show pretend CAPTCHA pages that trick customers into working PowerShell instructions. These instructions load Lumma immediately into reminiscence, serving to it evade file-based detection mechanisms.
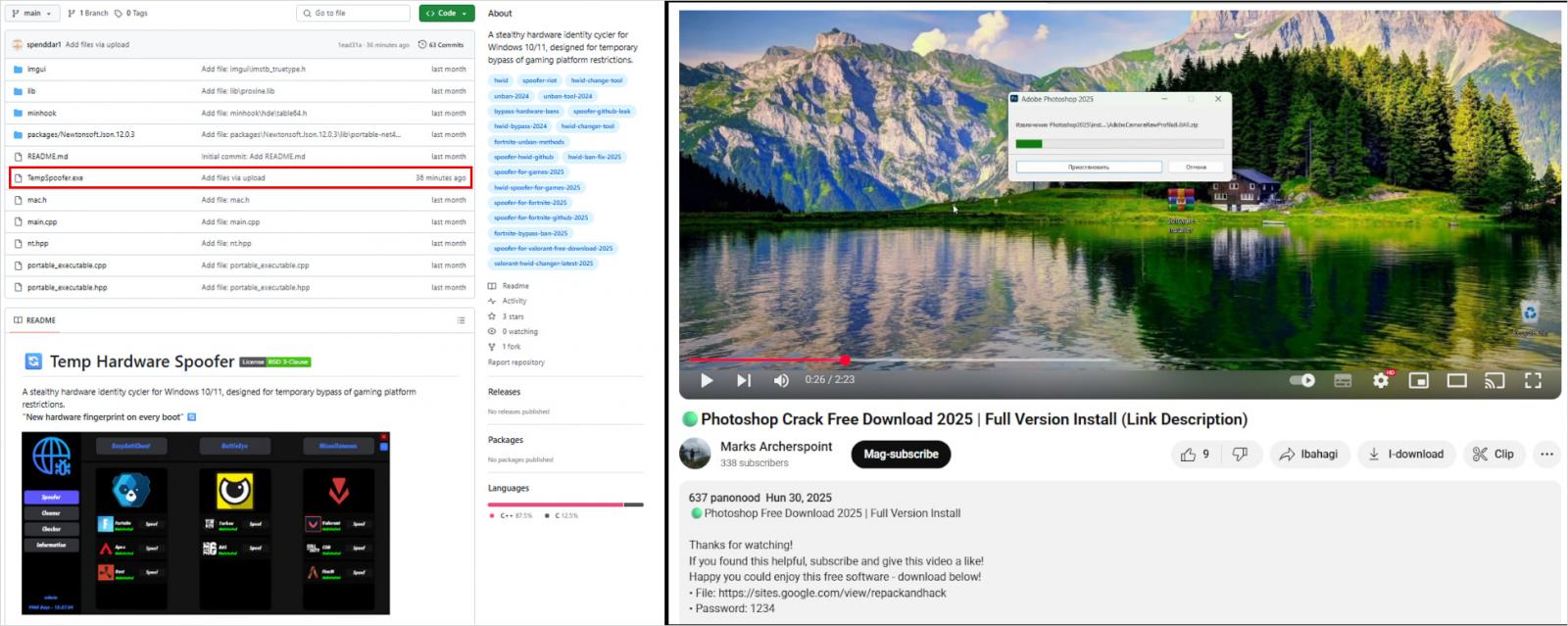
- GitHub: Attackers are actively creating GitHub repositories with AI-generated content material promoting pretend recreation cheats. These repos host Lumma payloads, like “TempSpoofer.exe,” both as executables or in ZIP recordsdata.
- YouTube/Fb: Present Lumma distribution additionally entails YouTube movies and Fb posts selling cracked software program. These hyperlinks result in exterior websites internet hosting Lumma malware, which generally abuses trusted companies like websites.google.com to seem credible.
Supply: Pattern Micro
The re-emergence of Lumma as a big menace demonstrates that regulation enforcement motion, devoid of arrests or at the least indictments, is ineffective in stopping these decided menace actors.
MaaS operations, resembling Lumma, are extremely worthwhile, and the main operators behind them probably view regulation enforcement motion as routine obstacles they merely should navigate.
CISOs know that getting board buy-in begins with a transparent, strategic view of how cloud safety drives enterprise worth.
This free, editable board report deck helps safety leaders current danger, impression, and priorities in clear enterprise phrases. Flip safety updates into significant conversations and quicker decision-making within the boardroom.



