Government Abstract
Cybersecurity specialists usually say that people are the weakest and most simply exploited assault vector. That is normally in reference to the common end-user, and neglects to say that directors and extremely privileged customers may fall sufferer to threats.
As menace actors proceed to evolve their strategies for preliminary entry and compromise, it’s a reminder that we’re all fallible no matter organizational function or safety experience. This weblog underlines the significance of following finest safety practices all through all ranges of the group with out exemption.
Not too long ago, the LevelBlue Managed Detection and Response (MDR) Safety Operations Middle (SOC) group dealt with a number of incidents associated to compromise stemming from privileged consumer exercise via malvertising, masquerading because the professional SSH software PuTTY.
Investigation
A SentinelOne alert for high-risk indicator detection was obtained by the LevelBlue SOC inside USM Anyplace, LevelBlue’s Open XDR platform. Preliminary observations of alarm artifacts displayed a obtain of file ‘PuTTY.exe’ on an endpoint. The SentinelOne menace data indicated the file was signed by ‘NEW VISION MARKETING LLC’ which raised the primary crimson flag, as this doesn’t align with expectations for professional PuTTY. Behavioral indicators detected by SentinelOne included potential Kerberoasting, suspicious PowerShell execution, and persistence established through scheduled activity.
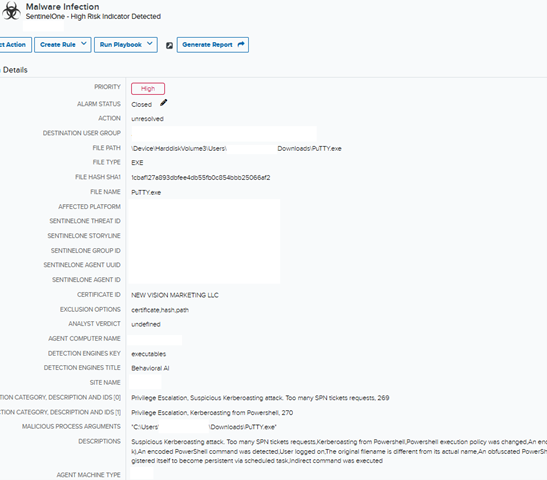
Determine 1: Screenshot of preliminary SentinelOne alarm obtained in USM displaying high-risk indicators
We started reviewing related storyline exercise inside SentinelOne which raised extra crimson flags:
– Visitors from PuTTY.exe to 2 malicious IP addresses, as confirmed in VirusTotal.
– Creation of two suspicious Dynamic Hyperlink Libraries (DLLs) within the consumer’s %appdata% and %temp% directories.
– Institution of persistence through scheduled activity that executed one of many DLLs through “rundll32.exe DllRegisterServer”.
– Proof of hands-on-keyboard (HOK) exercise and Kerberoasting.
Expanded Investigation
We contacted the shopper and established that this exercise was anomalous and certain malicious. We instantly took motion to remediate by disconnecting the affected asset from the community through SentinelOne and advising the shopper to disable the consumer account. We used SentinelOne’s Storyline function to achieve a extra full image of what had occurred. As soon as downloaded, the faux PuTTY executable created a scheduled activity named ‘Safety Updater’ which was scheduled to run at three-minute intervals and executed malicious DLL ‘twain_96.dll’ through rundll32.exe.
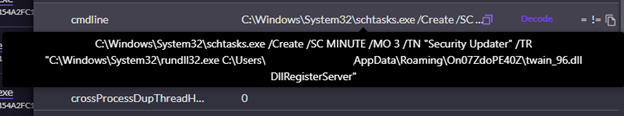
Determine 2: Scheduled activity creation ‘Safety Updater’ and parameters
The second DLL named ‘inexperienced.dll’ was dropped into the consumer’s %temp% folder by ‘twain_96.dll’. This DLL was recorded in a single connection occasion to port 443 of 144.217.206[.]26 and appeared to offer the menace actor with palms on keyboard entry. That is in keeping with VirusTotal outcomes for the file hashes of ‘inexperienced.dll’ and ‘twain_96.dll’, that are reporting these information as Broomstick/Oyster malware. Broomstick/Oyster is thought to offer menace actors distant command execution through cmd.exe, set up persistence through scheduled duties that use rundll32.exe, and make the most of hardcoded C2 servers – all of which have been noticed on this incident. The method tree seen in determine 3 reveals cmd.exe spawning from the execution of rundll32.exe with “inexperienced.dll” and executing a number of discovery and recon instructions through cmd.exe. The next identified ransomware operator discovery TTPs have been noticed:
• nltest /trusted_domains
• internet group “area admins” /area
• nltest /dclist:
The ultimate motion recorded in exercise from the menace actor was the execution of an inline PowerShell script used for Kerberoasting.
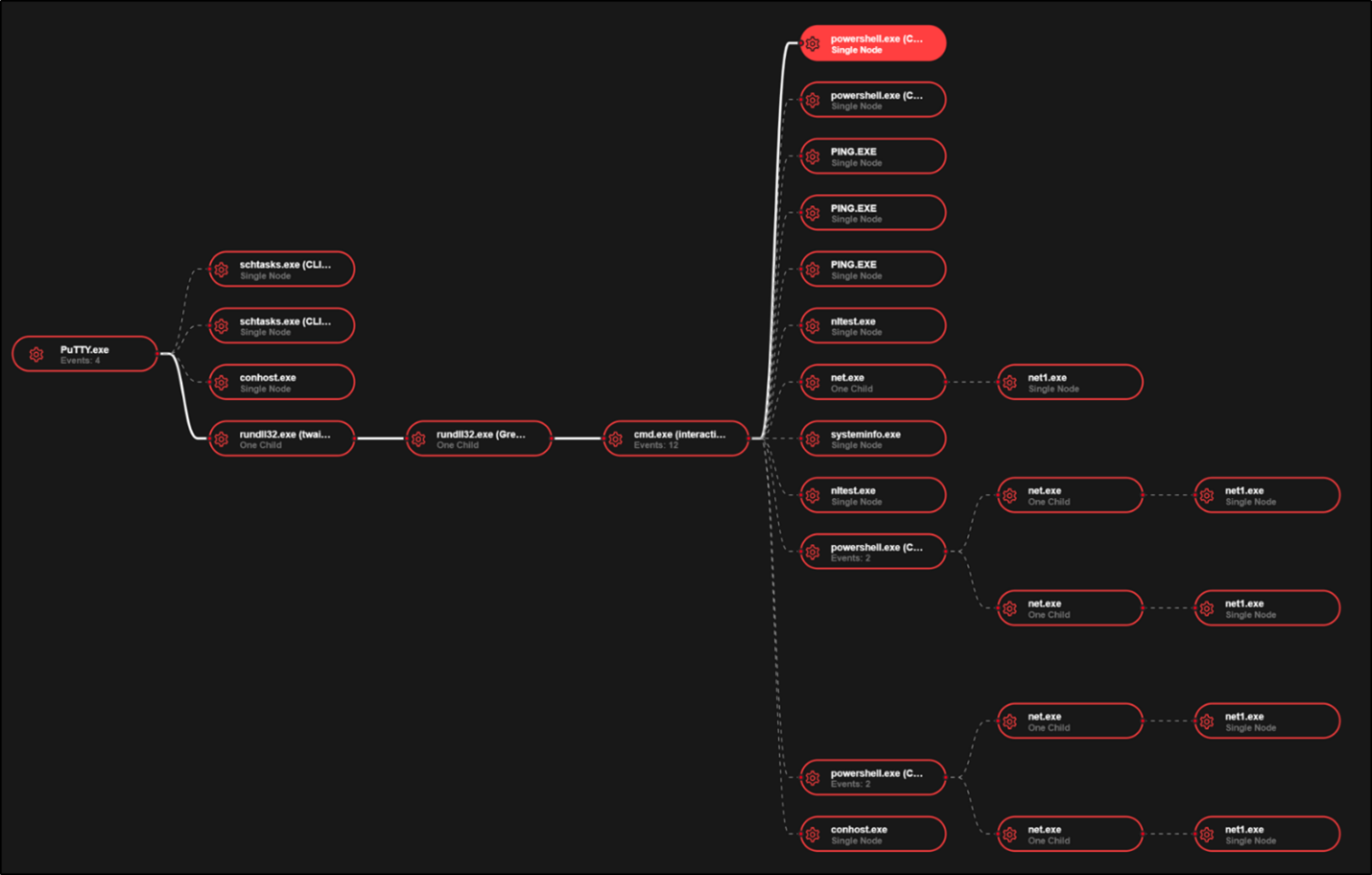
Determine 3: SentinelOne course of tree from incident
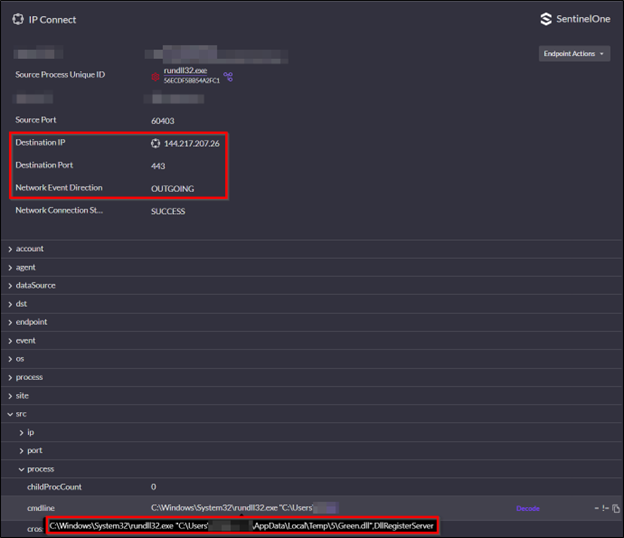
Determine 4: Inexperienced.dll connection occasion in S1
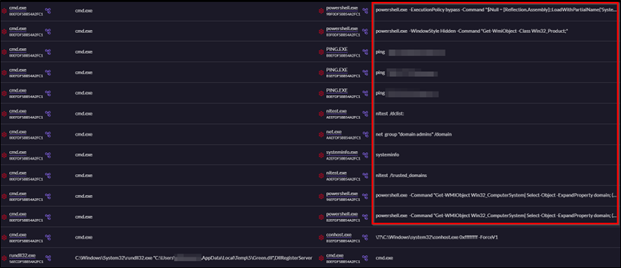
Determine 5: Arms on Keyboard exercise by menace actor
Kerberoasting Script Evaluation:
Kerberoasting is a well known assault approach used to assault Lively Listing service accounts by exploiting the Kerberos authentication protocol. In a Kerberoasting assault, a menace actor who has entry to a legitimate area consumer account requests Kerberos service tickets for accounts which have a SPN (Service Principal Identify) outlined. That is attainable as a result of Lively Listing permits any area consumer to request a Kerberos service ticket for accounts which have an outlined SPN. The Kerberos service ticket obtained is encrypted with a key derived from the service account’s password.
An attacker can then extract the ticket for offline cracking and make the most of a software resembling Hashcat to acquire the service account’s plaintext password. Lively Listing environments that also permit weak RC4-HMAC encryption and should not implementing AES encryption for Kerberos on SPNs are most susceptible to Kerberoasting assaults. Kerberoasting is a beautiful assault approach as service accounts are ceaselessly granted privileged entry in AD environments and infrequently have weak passwords set. A profitable Kerberoasting assault can permit a menace actor to escalate privilege to a legitimate account that may then be used for lateral motion in an surroundings.
There are a lot of well-known instruments that may facilitate a Kerberoasting assault, together with Rubeus, Impacket’s GetUserSPNs.py, and PowerSploit’s Invoke-Kerberoast. The Kerberoasting script used on this incident, depicted in determine 6 beneath, accommodates elements from PowerSploit’s Invoke-Kerberoast, however is streamlined and operates completely in reminiscence with out making any writes to disk. Its utilization highlights how menace actors can adapt identified red-team instruments and leverage LOLBINs (living-off-the-land-binaries) for malicious exercise.
The PowerShell instructions within the noticed Kerberoasting script observe this circulate:
1. Loading of the .NET meeting System.IdentityModule, which is required with the intention to entry the .NET class System.IdentityModule.Tokens.KerberosRequestorSecurityToken used later within the script.
2. Execution of an LDAP question utilizing the .NET class DirectoryServices.DirectorySearcher to enumerate all Lively Listing consumer objects which have a SPN outlined.
3. For every consumer with a SPN, a Kerberos service ticket (TGS) request is made utilizing the .NET class System.IdentityModule.Tokens.KerberosRequestorSecurityToken. Calling this class for the ticket request ends in a ticket that makes use of weak RC4-HMAC encryption until AES encryption is enabled for Kerberos authentication for the SPN account.
4. In-memory extraction of the uncooked bytes of returned Kerberos tickets, adopted by hex parsing through regex and formatting the consequence right into a $krb5tgs$ hash that’s instantly appropriate for utilization with the Hashcat cracking software (Hash Mode 13100). This output is written on to the console.
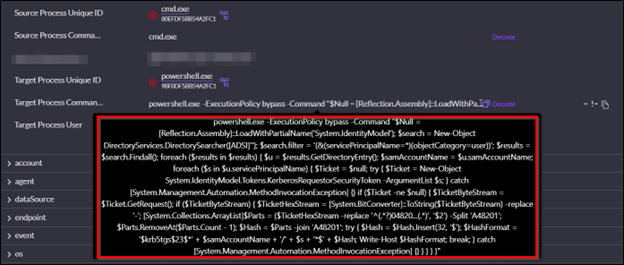
Determine 6: The Kerberoasting script executed by the menace actor
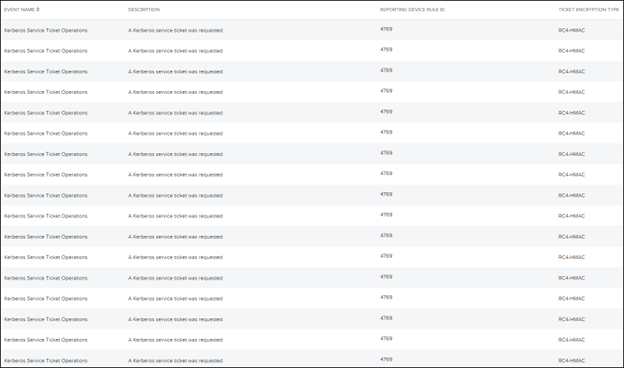
Determine 7: USMA occasions that present the RC4-HMAC encrypted Kerberos service tickets that resulted from the Kerberoasting script
Proof of this exercise was additionally discovered inside the LevelBlue USM Anyplace platform in Kerberos Service Ticket occasions (Occasion ID 4769) that logged RC4-HMAC encrypted tickets. The LevelBlue MDR SOC offered our buyer with an inventory of the SPNs recorded within the ticket requests and beneficial resetting credentials for every account.
Response
Whereas working with the shopper to resolve this incident, extra members of the LevelBlue MDR SOC carried out a menace hunt throughout our buyer fleet for indicators of compromise (IOCs) noticed with this trojanized PuTTY menace.
Our group reached out to affected prospects and helped them to remediate the menace previous to execution.
The LevelBlue SOC additionally used these indicators and noticed TTPs to create new customized detection guidelines inside SentinelOne to boost incident detection and response occasions.
Further Investigation into PuTTY Malvertising
The MDR SOC investigated additional into the malvertising marketing campaign distributing trojanized variations of the PuTTY terminal emulator. The same marketing campaign was lively in Might and June of 2024, and the current exercise seems to observe an identical playbook.
The LevelBlue group discovered malicious sponsored advertisements utilized by menace actors through Microsoft’s Bing Search to ship the trojanized PuTTY. When performing searches for “putty obtain” or “putty plink obtain”, sponsored advertisements together with these in determine 8 and 9 beneath have been displayed in Bing Search:
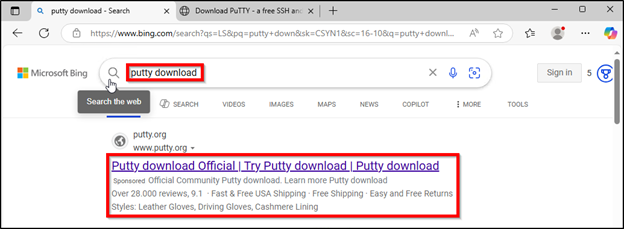
Determine 8: Malicious PuTTY Advert instance
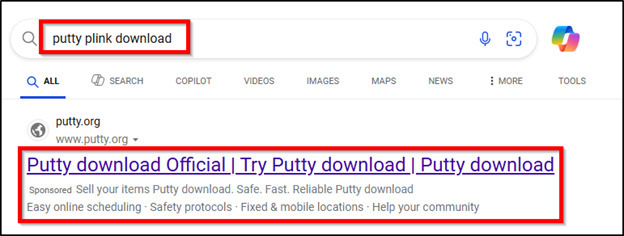
Determine 9: Malicious PuTTY Advert instance
These advertisements have been masquerading as putty[.]org, a website that isn’t affiliated with the official PuTTY Mission however does include obtain hyperlinks to the official PuTTY website www.chiark.greenend.org.uk. Clicking the advert hyperlink resulted in a web page setup to mimic putty[.]org however truly used a typosquatted area resembling puttyy[.]org or puttysystems[.]com. The obtain hyperlinks on these pages have been used to ship the trojanized PuTTY. Within the case of puttysystems[.]com, the LevelBlue MDR SOC noticed that the area heartlandenergy[.]ai was getting used to serve the malicious payload through the ‘Obtain PuTTY’ hyperlink. A subsequent website “putty[.]community” utilized a .js script “download-script.js” that was configured to examine 3 completely different domains (ruben.findinit[.]com, ekeitoro.siteinwp[.]com, and danielaurel[.]television) for payload availability. The MDR SOC discovered that the web sites for these 3 domains have been all constructed with WordPress. WordPress vulnerabilities are generally exploited by menace actors for drive by obtain and different malicious functions and thus it appears doubtless the menace actor compromised these websites for payload supply functions.
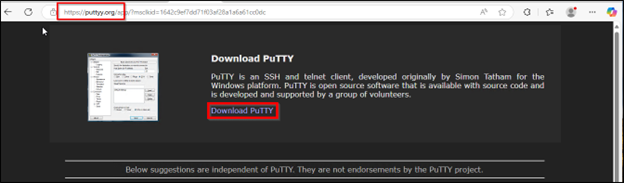
Determine 10: Trojanized PuTTY obtain through puttyy[.]org
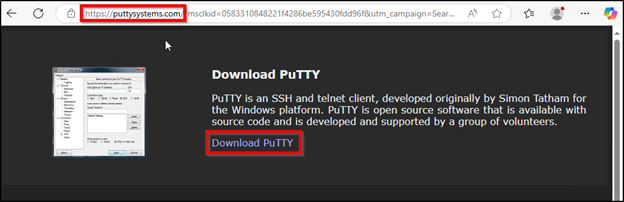
Determine 11: Trojanized PuTTY obtain through puttysystems[.]com
Primarily based on the LevelBlue MDR SOC’s observations and analysis, they recognized the next domains concerned within the malvertising exercise. They’re all newly registered domains aside from these utilized by the menace actors to facilitate payload supply.
• puttyy[.]org
• puttysystems[.]com
• updaterputty[.]com
• putty[.]wager
• puttyy[.]com
• putty[.]run
• putty[.]lat
• putty[.]us[.]com
• heartlandenergy[.]ai
• putty[.]community
• ruben.findinit[.]com
• ekeitoro.siteinwp[.]com
• danielaurel[.]television
Our group additionally noticed that the menace actors behind this marketing campaign persistently deployed variant types of the malicious putty.exe payload. A number of distinct file hashes and code-signing certificates have been seen throughout incidents and in exterior analysis. This system doubtless enhanced the marketing campaign’s effectiveness by circumventing hash-based blocklists and signature-based detection guidelines that relied on beforehand noticed indicators. Moreover, a unique scheduled activity identify was additionally noticed in sandbox detonation of some samples – a activity named “FireFox Agent INC” was noticed in samples present in analysis after the preliminary incident.
The LevelBlue MDR SOC reported the malicious advert to Microsoft Promoting and obtained a response stating that the advert had been faraway from their promoting community. Whereas the advert did seem to have been eliminated, inside a number of days our group uncovered new trojanized PuTTY payloads exhibiting the identical conduct. This recurrence means that the menace actors are doubtless abusing a number of promoting platforms. It additionally underscores the broader challenge that main promoting networks appear to lack strong verification mechanisms able to stopping persistent abuse.
Conclusion
We advocate guaranteeing that every one customers all through your group bear routine coaching about secure practices and system utilization. IT and Safety workers ought to stay up-to-date on rising threats and guarantee data is appropriately disseminated to highly-privileged customers.
Moreover, it is very important be certain that each in-house workers and privileged vendor accounts are utilizing approved and vetted administrative instruments. We advocate creating a trusted repository to be used inside your group and guaranteeing these are commonly up to date and validated.
Lastly, please evaluate the listing of IOCs compiled beneath and add these domains to your organizational blocklist.
IOCs
Domains:
• puttyy[.]org
• puttysystems[.]com
• updaterputty[.]com
• putty[.]wager
• puttyy[.]com
• putty[.]run
• putty[.]lat
• putty[.]us[.]com
• heartlandenergy[.]ai
• putty[.]community
• ruben.findinit[.]com
• ekeitoro.siteinwp[.]com
• danielaurel[.]television
File Hashes (SHA256):
• 0b85ad058aa224d0b66ac7fdc4f3b71145aede462068cc9708ec2cee7c5717d4
• e9f05410293f97f20d528f1a4deddc5e95049ff1b0ec9de4bf3fd7f5b8687569
• d73bcb2b67aebb19ff26a840d3380797463133c2c8f61754020794d31a9197d1
• dd995934bdab89ca6941633dea1ef6e6d9c3982af5b454ecb0a6c440032b30fb
• 03012e22602837132c4611cac749de39fb1057a8dead227594d4d4f6fb961552
• a653b4f7f76ee8e6bd9ffa816c0a14dca2d591a84ee570d4b6245079064b5794
• e02d21a83c41c15270a854c005c4b5dfb94c2ddc03bb4266aa67fc0486e5dd35
• 80c8a6ecd5619d137aa57ddf252ab5dc9044266fca87f3e90c5b7f3664c5142f
• 1112b72f47b7d09835c276c412c83d89b072b2f0fb25a0c9e2fed7cf08b55a41
• 3d22a974677164d6bd7166e521e96d07cd00c884b0aeacb5555505c6a62a1c26
• e8e9f0da26a3d6729e744a6ea566c4fd4e372ceb4b2e7fc01d08844bfc5c3abb
• eef6d4b6bdf48a605cade0b517d5a51fc4f4570e505f3d8b9b66158902dcd4af
File Signers:
• THE COMB REIVERS LIMITED
• NEW VISION MARKETING LLC
• PROFTORG LLC
• LLC Fortuna
• LLC BRAVERY
• LLC Infomed22
IPs:
• 45.86.230[.]77
• 185.208.159[.]119
• 144.217.207[.]26
• 85.239.52[.]99
• 194.213.18[.]89
URLs:
• hxxp[:]//185.208.158[.]119/api/jgfnsfnuefcnegfnehjbfncejfh
• hxxp[:]//185.208.158[.]119/api/kcehc
• hxxp[:]//45.86.230[.]77:443/reg
• hxxp[:]//45.86.230[.]77:443/login
• hxxp[:]//85.239.52[.]99/api/jgfnsfnuefcnegfnehjbfncejfh
• hxxp[:]//85.239.52[.]99/api/kcehc
• hxxp[:]//194.213.18[.]89:443/reg
• hxxp[:]//194.213.18[.]89:443/login
Scheduled Process Creations:
• Safety Updater
• FireFox Agent INC
The content material offered herein is for basic informational functions solely and shouldn’t be construed as authorized, regulatory, compliance, or cybersecurity recommendation. Organizations ought to seek the advice of their very own authorized, compliance, or cybersecurity professionals relating to particular obligations and danger administration methods. Whereas LevelBlue’s Managed Risk Detection and Response options are designed to assist menace detection and response on the endpoint stage, they don’t seem to be an alternative to complete community monitoring, vulnerability administration, or a full cybersecurity program.


