
Ivanti warned clients at the moment to patch their Ivanti Endpoint Supervisor Cell (EPMM) software program in opposition to two safety vulnerabilities chained in assaults to achieve distant code execution.
“Ivanti has launched updates for Endpoint Supervisor Cell (EPMM) which addresses one medium and one excessive severity vulnerability,” the corporate stated.
“When chained collectively, profitable exploitation may result in unauthenticated distant code execution. We’re conscious of a really restricted variety of clients whose resolution has been exploited on the time of disclosure.”
The primary safety flaw (CVE-2025-4427) is an authentication bypass in EPMM’s API element, permitting attackers to entry protected sources on weak units. The second (tracked as CVE-2025-4428) is a distant code execution vulnerability that permits risk actors to execute arbitrary code on focused techniques through maliciously crafted API requests.
Ivanti says clients can mitigate the 2 zero-day flaws by putting in Ivanti Endpoint Supervisor Cell 11.12.0.5, 12.3.0.2, 12.4.0.2, or 12.5.0.1.
The corporate added that, whereas it is nonetheless investigating these assaults and may’t present indicators of compromise, clients ought to attain out to the help workforce for additional steering.
Whereas Ivanti stated the 2 vulnerabilities are “related” with two open-source libraries utilized by EPMM, it did not share their names within the advisory. A spokesperson directed BleepingComputer to at the moment’s advisory for additional info.
“The problem solely impacts the on-prem EPMM product. It isn’t current in Ivanti Neurons for MDM, Ivanti’s cloud-based unified endpoint administration resolution, Ivanti Sentry, or some other Ivanti merchandise,” Ivanti added in a separate advisory. “We urge all clients utilizing the on-prem EPMM product to promptly set up the patch.”
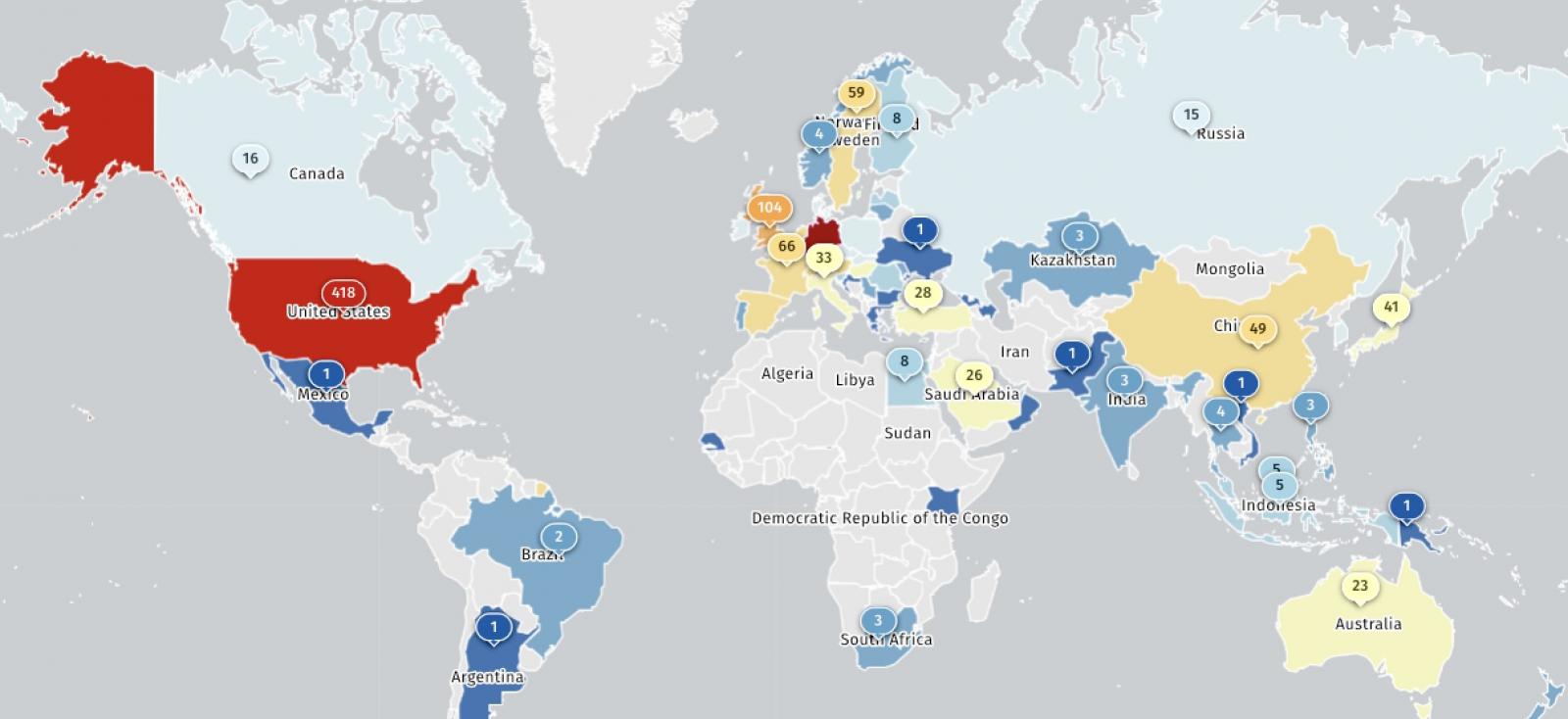
The Shadowserver risk monitoring platform presently tracks lots of of Ivanti EPMM situations uncovered on-line, most in Germany (992) and the USA (418).
Right now, Ivanti additionally launched safety updates to deal with a crucial authentication bypass vulnerability (CVE-2025-22462) impacting its Neurons for ITSM IT service administration resolution that may let unauthenticated attackers acquire administrative entry.
It additionally urged clients to patch a default credentials flaw (CVE-2025-22460) in its Cloud Companies Equipment (CSA) that lets native authenticated attackers escalate privileges on weak techniques.
Lately, a number of different safety vulnerabilities have been exploited in zero-day assaults focusing on Ivanti’s VPN home equipment and ICS, IPS, and ZTA gateways.
The FBI and CISA additionally warned in a joint advisory issued in January that risk actors are nonetheless exploiting months-old Ivanti Cloud Service Home equipment (CSA) safety vulnerabilities to breach weak networks.



