
An American-Israeli nationwide named Osei Morrell has been arrested in Israel for his alleged involvement in exploiting the Nomad bridge smart-contract in August 2022 that allowed hackers to siphon $190 million.
Blockchain intelligence platform TRM Labs provided key info to worldwide regulation enforcement authorities, resulting in the identification of Morrell, who’s believed to have performed a central position in what is without doubt one of the largest hacks in DeFi historical past.
“The suspect, American-Israeli twin nationwide Osei Morrell, was arrested in Jerusalem by Israeli police working in coordination with the DOJ, the FBI, and Interpol,” defined TRM Labs.
In accordance with the blockchain intelligence agency, Morell will quickly be extradited to the United Statesas the authorized precedures have already been permitted.
Morrell’s hyperlinks to Nomad Bridge hack
The Nomad bridge is a cross-chain communication commonplace that enables customers to switch belongings between totally different blockchains.
On August 1, 2022, attackers exploited a vital vulnerability launched in an replace to its Reproduction sensible contract, particularly within the ‘course of() perform.’
Although the contract was alleged to confirm message proofs earlier than releasing funds, a misconfiguration allowed any message with an accurate root hash to be accepted, even when the underlying proof was invalid.
As soon as a single attacker found out the flaw, the exploit methodology was shortly picked up by lots of of different wallets, because it consisted in merely copy-pasting a particular transaction format.
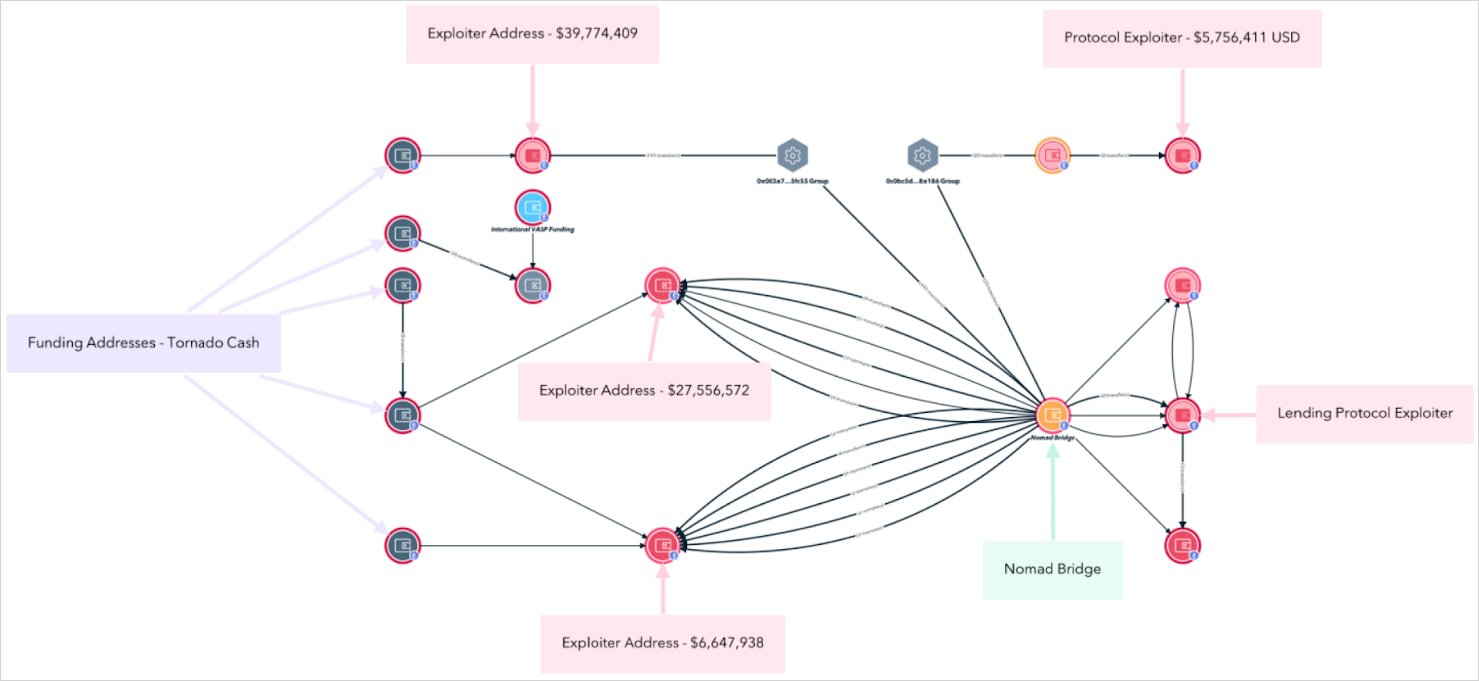
This “mob-style” assault led to a chaotic and decentralized looting of the bridge, draining over $190 million in ETH, USDC, WBTC, and ERC-20 tokens.
Supply: TRM Labs
TRM Labs feedback that the vulnerability was very straightforward to leverage, so even individuals with no hacking abilities or deep blockchain data joined within the exploitation. Nevertheless, skilled North Korean actors have been additionally implicated.
Osei Morrell will not be believed to have written or initiated the exploit code itself, however TRM Labs says he “performed a central position,” and proof suggests he conspired with others to launder massive quantities of funds stolen in the course of the exploit.
Wallets linked to Morrell obtained stolen belongings inside hours of the bridge being drained, suggesting shut coordination with early attackers.
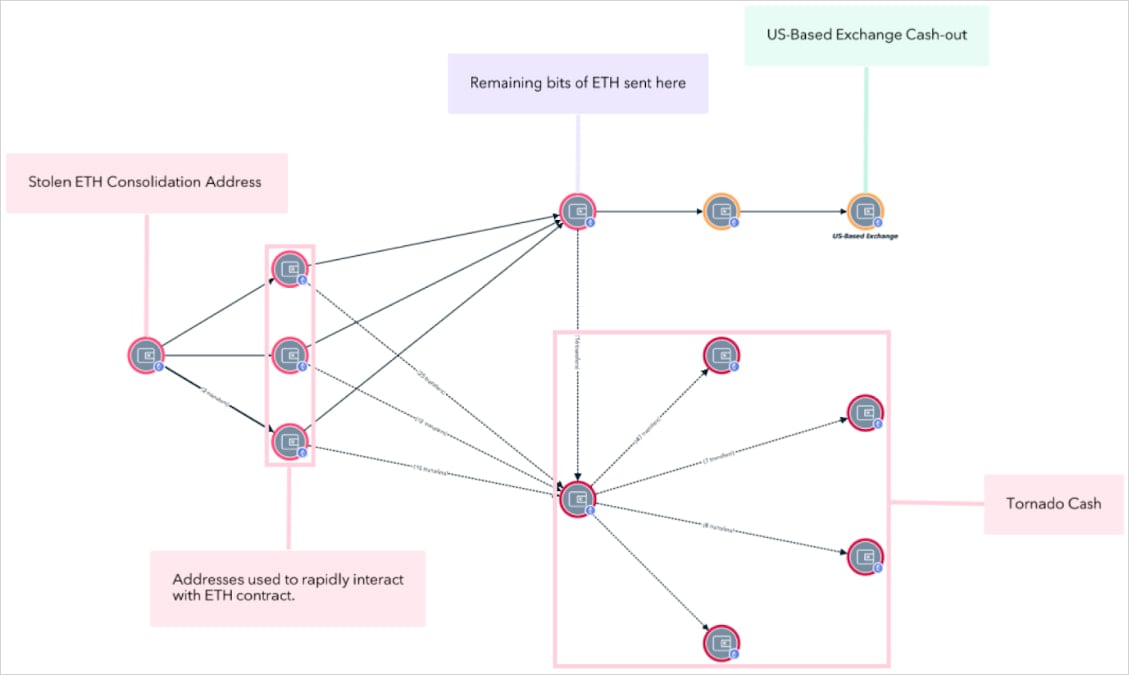
TMR Labs’ knowledge exhibits that Morrell used ‘chain-hopping’ to maneuver the stolen tokens throughout varied blockchains, the Twister Money mixer to obfuscate the origin of the funds, and swapped ETH into the privacy-boosting Monero (XMR) and Sprint.
Supply: TRM Labs
To money out the proceeds, he used non-custodial exchanges, OTC brokers, and offshore financial institution accounts tied to pretend or opaque authorized entities, and in addition transformed some crypto to fiat by suppliers with no KYC requirements.
Regardless of all of the obfuscation efforts and the time that has handed since these occasions, blockchain transaction evaluation nonetheless yielded sufficient clues to uncover Morrell’s id, leading to his arrest.
Morrell’s arrest follows that of one other suspected hacker, a Russian-Israeli citizen named Alexander Gurevich, who was caught on Might 1st on the Ben Gurion airport in Tel Aviv utilizing paperwork beneath a brand new identify, Alexander Block, he had formally modified.
In accordance with prosecutors, Gurevich exploited the Nomad bridge flaw and withdrew about $2.89 million in digital tokens. This was adopted by others discovering the difficulty and leveraging it to siphon belongings.
Jerusalem Put up studies that on August 4, 2022, Gurevich contacted Nomad’s Chief Expertise Officer and admitted he had been probing Nomad for weaknesses, apologizing for the difficulty and later demanding a $500,000 reward for figuring out the vulnerability.



