
Hackers have adopted the brand new method referred to as ‘FileFix’ in Interlock ransomware assaults to drop a distant entry trojan (RAT) on focused methods.
Interlock ransomware operations have elevated over the previous months because the menace actor began utilizing the KongTuke internet injector (aka ‘LandUpdate808’) to ship payloads by means of compromised web sites.
This shift in modus operandi was noticed by researchers at The DFIR Report and Proofpoint since Could. Again then, guests of compromised websites have been prompted to go a faux CAPTCHA + verification, after which paste right into a Run dialog content material routinely saved to the clipboard, a tactic in step with ClickFix assaults.
The trick led customers to execute a PowerShell script that fetched and launched a Node.js-based variant of the Interlock RAT.
In June, researchers discovered a PHP-based variant of Interlock RAT used within the wild, which was delivered utilizing the identical KongTuke injector.
Earlier this month, a major change within the supply wrapper occurred, with Interlock now switching to the FileFix variation of the ClickFix methodology as the popular supply methodology.
Supply: The DFIR Report
FileFix is a social engineering assault method developed by safety researcher mr.d0x. It is an evolution of the ClickFix assault, which grew to become one of the crucial broadly employed payload distribution strategies over the previous yr.
Within the FileFix variation, the attacker weaponizes trusted Home windows UI parts, comparable to File Explorer and HTML Functions (.HTA), to trick customers into executing malicious PowerShell or JavaScript code with out displaying any safety warnings.
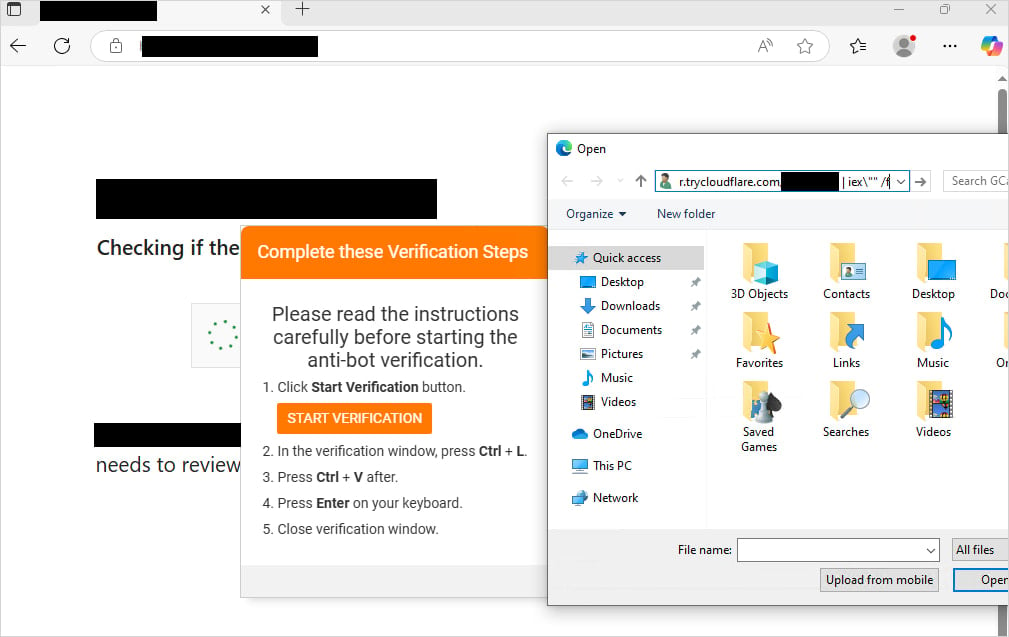
Customers are prompted to “open a file” by pasting a copied string into File Explorer’s tackle bar. The string is a PowerShell command disguised to appear like a file path utilizing remark syntax.
Within the latest Interlock assaults, targets are requested to stick a command disguised with a faux file path onto File Explorer, resulting in the downloading of the PHP RAT from ‘trycloudflare.com’ and its execution on the system.
Submit-infection, the RAT executes a sequence of PowerShell instructions to collect system and community data and exfiltrates this information as structured JSON to the attacker.
The DFIR Report additionally mentions proof of interactive exercise, together with Energetic Listing enumeration, checking for backups, navigating native directories, and inspecting area controllers.
The command and management (C2) server can ship shell instructions for the RAT to execute, introduce new payloads, add persistence through a Registry run key, or transfer laterally through distant desktop (RDP).
Interlock ransomware launched in September 2024, claiming notable victims just like the Texas Tech College, DaVita, and Kettering Well being.
The ransomware operation leveraged ClickFix to contaminate targets, however its pivoting to FileFix signifies that the attacker is fast to adapt to stealthier assault strategies.
That is the primary public affirmation of FileFix being utilized in precise cyberattacks. It’s more likely to acquire extra reputation as menace actors discover methods to include it into their assault chains.



