
A current Home windows safety replace that creates an ‘inetpub’ folder has launched a brand new weak spot permitting attackers to stop the set up of future updates.
After folks put in this month’s Microsoft Patch Tuesday safety updates, Home windows customers abruptly discovered an “inetpub” folder owned by the SYSTEM account created within the root of the system drive, usually the C: drive.
It was unusual to see this folder created as it’s usually used to carry information related to Microsoft’s Web Data Service internet server, which was not put in on these gadgets.
In an replace to a safety advisory, Microsoft later confirmed that the C:inetpub folder was a part of a repair for a Home windows Course of Activation elevation of privilege vulnerability tracked as CVE-2025-21204, with the corporate warning to not delete the folder.
“After putting in the updates listed within the Safety Updates desk in your working system, a brand new %systemdrivepercentinetpub folder might be created in your system,” confirmed Microsoft.
“This folder shouldn’t be deleted no matter whether or not Web Data Companies (IIS) is lively on the goal system. This habits is a part of adjustments that enhance safety and doesn’t require any motion from IT admins and finish customers.”
Nevertheless, cybersecurity knowledgeable Kevin Beaumont has demonstrated that this folder might be abused to stop additional Home windows updates from being put in whether it is created a sure approach.
“I’ve found this repair introduces a denial of service vulnerability within the Home windows servicing stack that permits non-admin customers to cease all future Home windows safety updates,” Kevin Beaumont.
In a brand new report, Beaumont says that Home windows customers, even these with out administrative privileges, can create a junction between C:inetpub and a Home windows file, like C:windowssystem32notepad.exe utilizing the next command.
mklink /j c:inetpub c:windowssystem32notepad.exe
A Home windows junction is a particular kind of folder that redirects entry to a different folder on the identical or one other drive, making it seem as if the content material exists in each places.
When requested why this junction is stopping the replace from being put in, Beaumont says he believes it is as a result of the replace expects a folder relatively than a file.
“It really works with mainly any file, I feel it is as a result of the servicing stack expects c:inetpub to be a listing – however mklink lets you make a junction to a file,” Beaumont advised BleepingComputer.
In line with Microsoft’s documentation, junctions are supposed to be hyperlinks between folders relatively than between information. Nevertheless, as you’ll be able to see from the picture earlier within the article, it’s nonetheless attainable to create one as proven within the picture under.
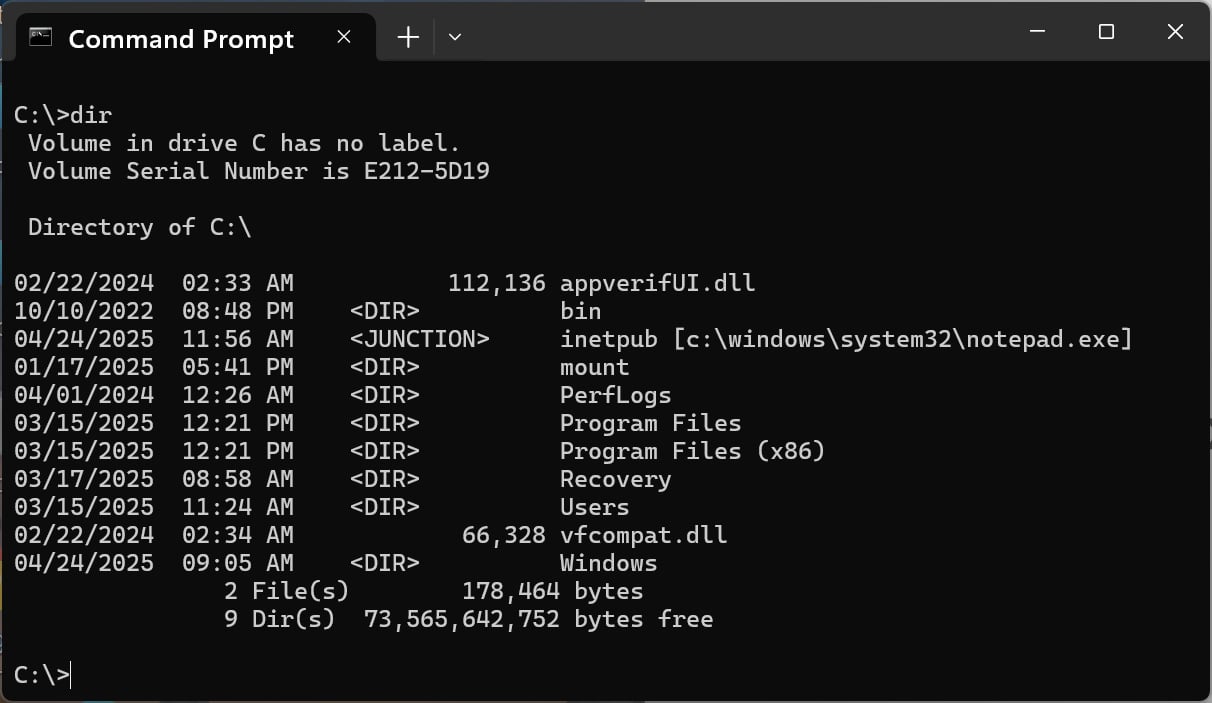
Supply: BleepingComputer
With this junction created, when you try to put in the April safety replace, it won’t set up appropriately, giving a 0x800F081F error code. This code is said to the error “CBS_E_SOURCE_MISSING,” which implies a bundle or file was not discovered.
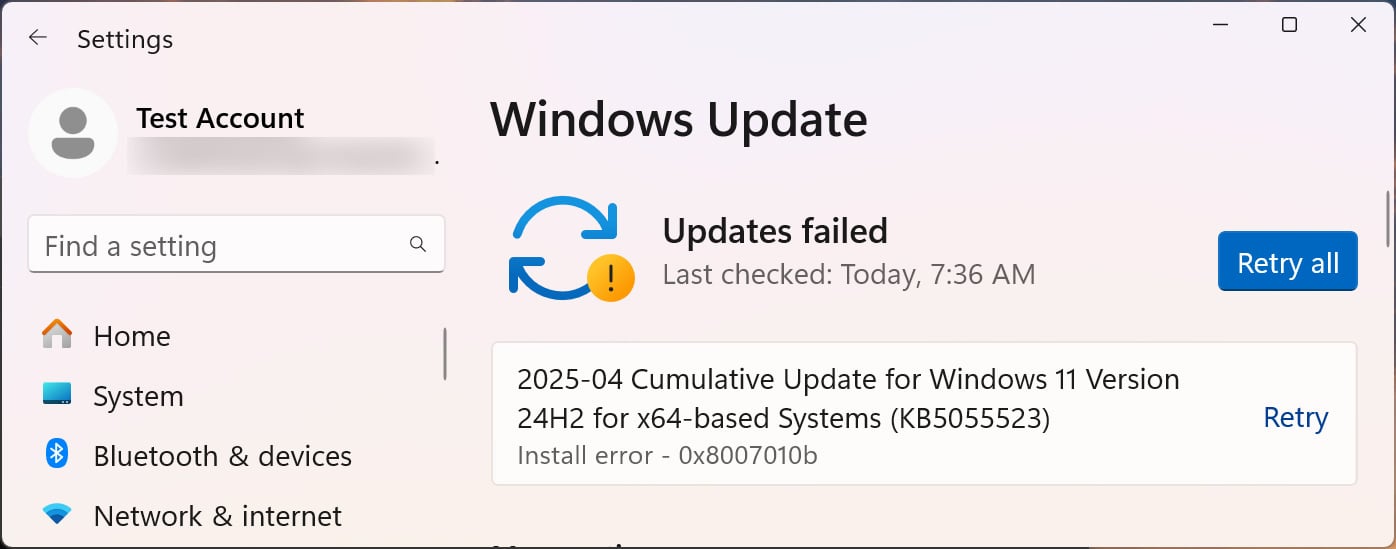
Supply: BleepingComputer:
Beaumont says he reported the bug to Microsoft, who has assigned it a “Medium” severity classification and closed his case, stating they are going to take into account fixing it sooner or later.
“After cautious investigation, this case is at present rated as a Average severity concern,” Microsoft emailed Beaumont.
“It doesn’t meet MSRCs present bar for instant servicing because the replace fails to use provided that the ‘inetpub’ folder is a junction to a file and succeeds upon deleting the inetpub symlink and retrying.”
BleepingComputer additionally contacted Microsoft about this bug on Wednesday however has not obtained a response but.


