
Risk actors are intensifying internet-wide scanning for Git configuration information that may reveal delicate secrets and techniques and authentication tokens used to compromise cloud providers and supply code repositories.
In a brand new report from risk monitoring agency GreyNoise, researchers have recorded a large spike in searches for uncovered Git configs between April 20-21, 2025.
“GreyNoise noticed practically 4,800 distinctive IP addresses each day from April 20-21, marking a considerable improve in comparison with typical ranges,” defined GreyNoise within the report.
“Though exercise was globally distributed, Singapore ranked as each the highest supply and vacation spot for classes throughout this era, adopted by the U.S. and Germany as the subsequent commonest locations.”
.jpg)
Supply: GreyNoise
Git configuration information are configuration information for Git initiatives that may embrace department info, distant repository URLs, hooks and automation scripts, and most significantly, account credentials and entry tokens.
Builders or corporations deploy net functions with out accurately excluding .git/ directories from public entry, inadvertently exposing these information to anybody.
Scanning for these information is a normal reconnaissance exercise that gives quite a few alternatives for risk actors.
In October 2024, Sysdig reported a few large-scale operation named “EmeraldWhale” which scanned for uncovered Git config information, snatching 15,000 cloud account credentials from hundreds of personal repositories.
Stealing credentials, API keys, SSH non-public keys, and even accessing internal-only URLs permits the risk actors to entry confidential information, craft tailor-made assaults, and hijack privileged accounts.
That is the precise technique that the risk actors used to breach Web Archive’s “The Wayback Machine” in October 2024, after which keep their foothold regardless of the proprietor’s efforts to thwart the assaults.
GreyNoise experiences that the latest exercise is usually focused at Singapore, america, Spain, Germany, the UK, and India.
The malicious exercise culminates in waves, with 4 notable circumstances since late 2024 being recorded in November, December, March, and April. The latest one was the best quantity assault wave the researchers logged.
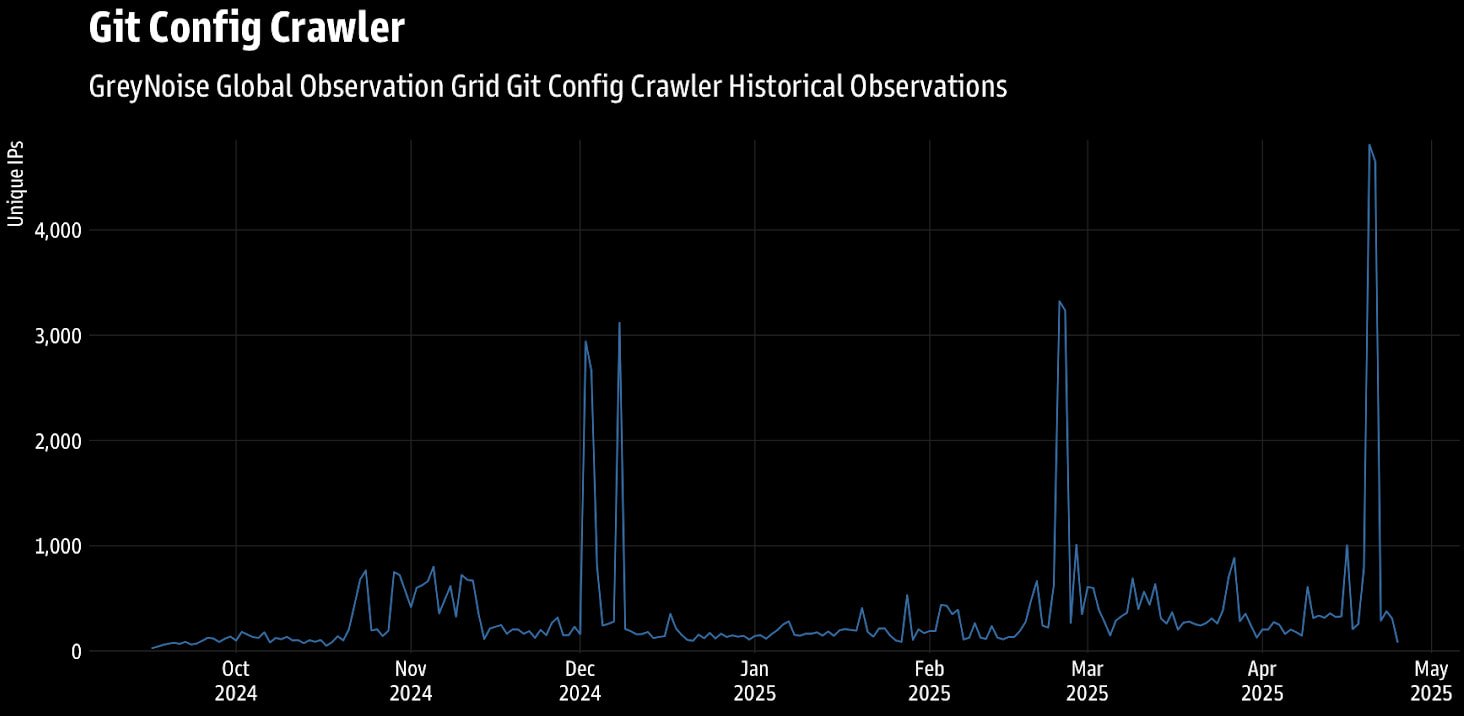
Supply: GreyNoise
To mitigate the dangers that come up from these scans, it is strongly recommended to dam entry to .git/ directories, configure net servers to forestall entry to hidden information, monitor server logs for suspicious .git/config entry, and rotate doubtlessly uncovered credentials.
If net server entry logs present unauthorized entry to Git configs, any credentials saved inside them must be rotated instantly.


