
Clorox is suing IT large Cognizant for gross negligence, alleging it enabled a large August 2023 cyberattack by resetting an worker’s password for a hacker with out first verifying their identification.
The incident was first made public in September 2023, reportedly carried out by hackers related to Scattered Spider, who utilized a social engineering assault to breach the corporate.
The lawsuit says Cognizant supplied IT companies to Clorox, together with service desk assist and identification administration, which was the purpose of compromise that led to a devastating and expensive cyberattack for the corporate.
Clorox is a serious shopper items firm, finest recognized for family cleansing merchandise, bleach, disinfectants, and private care gadgets. Cognizant is a worldwide IT companies and consulting firm, offering cloud companies, software program growth, and cybersecurity.
In line with the grievance, from 2013 to 2023, Cognizant was contracted by Clorox to deal with its IT operations.
“Cognizant supplied the service desk (“Service Desk”) that Clorox staff might contact once they wanted password restoration or reset help,” reads the grievance shared with BleepingComputer.
“Cognizant’s operation of the Service Desk got here with a easy, common sense requirement: by no means reset anybody’s credentials with out correctly authenticating them first. Clorox made this straightforward for Cognizant by offering them with straight-forward procedures to comply with every time offering credential restoration or reset help.”
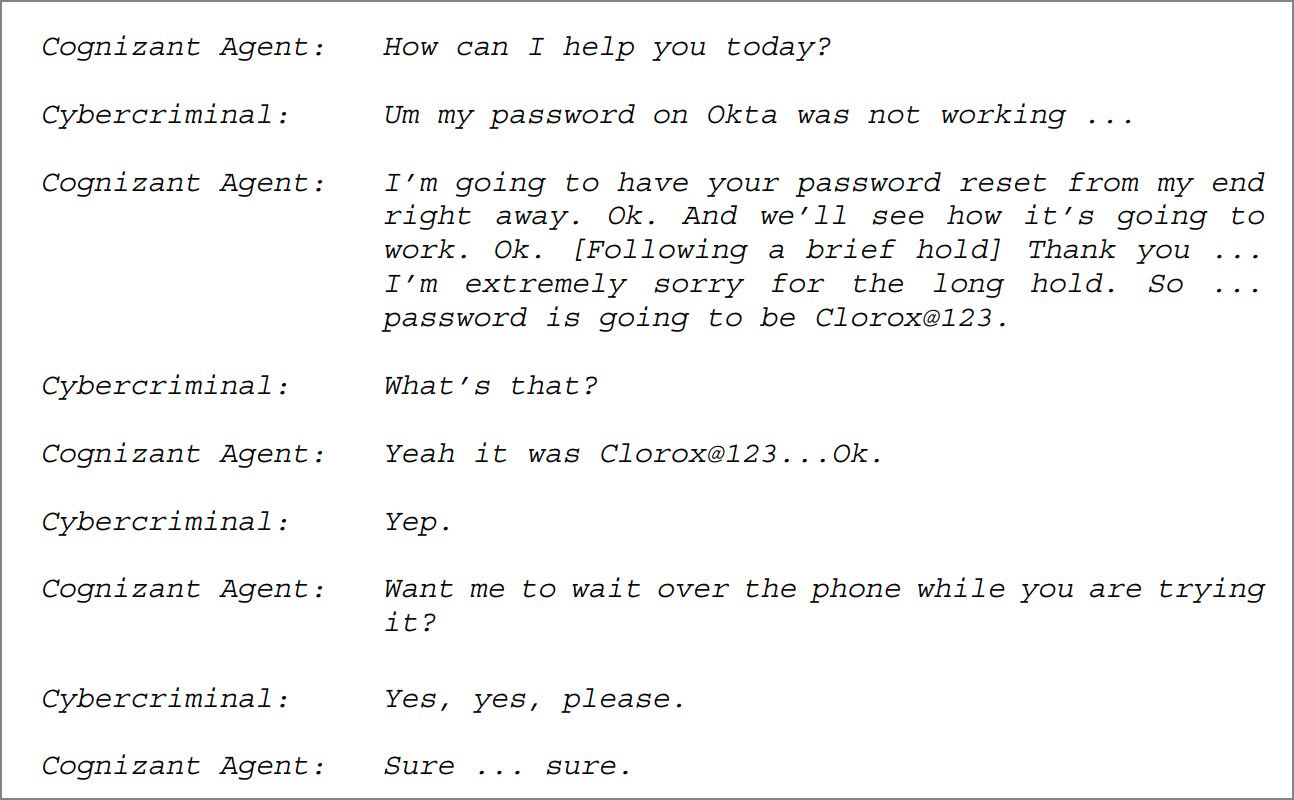
Nevertheless, the grievance alleges that on August 11, 2023, recordings present {that a} cybercriminal referred to as Cognizant’s Service Desk a number of instances, pretending to be a Clorox consultant requesting password and multi-factor authentication resets.
“At no level throughout any of the calls did the Agent confirm that the caller was in truth Worker 1. At no level did the Agent comply with Clorox’s credential assist procedures—both the pre-2023 process or the January 2023 replace—earlier than altering the password for the cybercriminal. The Agent additional reset Worker 1’s MFA credentials a number of instances with none identification verification in any respect. And at no level did the Agent ship the required emails to the worker or the worker’s supervisor to alert them of the password reset. “Clorox claims within the grievance.
The sort of social engineering assault has turn into the hallmark of Scattered Spider assaults, just lately utilized in UK retail assaults on Marks & Spencer and Co-op.
After allegedly failing to confirm the caller’s precise identification, Cognizant reset the credentials and multi-factor authentication (MFA) for the hacker, granting them entry to Clorox’s IT community.
To make issues worse, Clorox alleges that the menace actors used the identical playbook to reset the password and MFA for an additional worker who labored in IT safety, which was performed with out verification as soon as once more. This reportedly gave the attackers privileged entry to the community, which they used to unfold to additional units.
Supply: Clorox grievance in opposition to Cognizant
Clorox states that Cognizant’s actions paralyzed its company community, halted manufacturing, and triggered widespread product shortages and enterprise interruption.
Along with this, Clorox described Cognizant’s response and restoration assist as overly incompetent, leading to delays within the utility of containment measures, failure to close down compromised accounts, and sending underqualified personnel on premises.
“The ensuing Cyberattack was debilitating. It paralyzed Clorox’s company community and crippled enterprise operations,” describes the authorized grievance.
“And to make issues worse, when Clorox referred to as on Cognizant to offer incident response and catastrophe restoration assist companies, Cognizant botched its response and compounded the injury it had already triggered.”
Clorox’s grievance alleges breach of contract because of Cognizant’s failure to fulfill ITSA obligations, breach of fine religion and truthful dealing, gross negligence, and intentional misrepresentation of employees coaching on the consumer’s credential reset procedures.
For these actions, which resulted in lots of of tens of millions of {dollars} in misplaced gross sales because of enterprise disruption, in addition to reputational injury with long-term penalties, Clorox is looking for $49 million in direct remediation damages and $380,000,000 in whole damages.
[Update 7/24 03:00 AM EST] – A Cognizant spokesperson despatched BleepingComputer the beneath remark:
“It’s stunning {that a} company the scale of Clorox had such a clumsy inner cybersecurity system to mitigate this assault. Clorox has tried responsible us for these failures, however the actuality is that Clorox employed Cognizant for a slim scope of assist desk companies which Cognizant fairly carried out. Cognizant didn’t handle cybersecurity for Clorox.” – Cognizant



