
Two crucial vulnerabilities affecting the open-source discussion board software program vBulletin have been found, with one confirmed to be actively exploited within the wild.
The failings, tracked beneath CVE-2025-48827 and CVE-2025-48828, and rated crucial (CVSS v3 rating: 10.0 and 9.0 respectively), are an API technique invocation and a distant code execution (RCE) through template engine abuse flaws.
They influence vBulletin variations 5.0.0 by means of 5.7.5 and 6.0.0 by means of 6.0.3 when the platform runs on PHP 8.1 or later.
The vulnerabilities have been seemingly patched quietly final 12 months with the discharge of Patch Degree 1 for all variations of the 6.* launch department, and model 5.7.5 Patch Degree 3, however many websites remained uncovered as a result of not upgrading.
Public PoC and lively exploitation
The 2 points have been found on Might 23, 2025, by safety researcher Egidio Romano (EgiX), who defined the right way to exploit it through an in depth technical put up on his weblog.
The researcher confirmed that the flaw lies in vBulletin’s misuse of PHP’s Reflection API, which, as a result of behavioral modifications launched in PHP 8.1, permits protected strategies to be invoked with out specific accessibility changes.
The vulnerability chain lies within the capacity to invoke protected strategies through crafted URLs and the misuse of template conditionals inside vBulletin’s template engine.
By injecting crafted template code utilizing the weak ‘replaceAdTemplate’ technique, attackers bypass “unsafe operate” filters utilizing methods like PHP variable operate calls.
This leads to totally distant, unauthenticated code execution on the underlying server — successfully granting attackers shell entry as the online server person (www-data on Linux, for instance).
On Might 26, safety researcher Ryan Dewhurst reported seeing exploitation makes an attempt on honeypot logs exhibiting requests to the weak ‘ajax/api/advert/replaceAdTemplate’ endpoint.
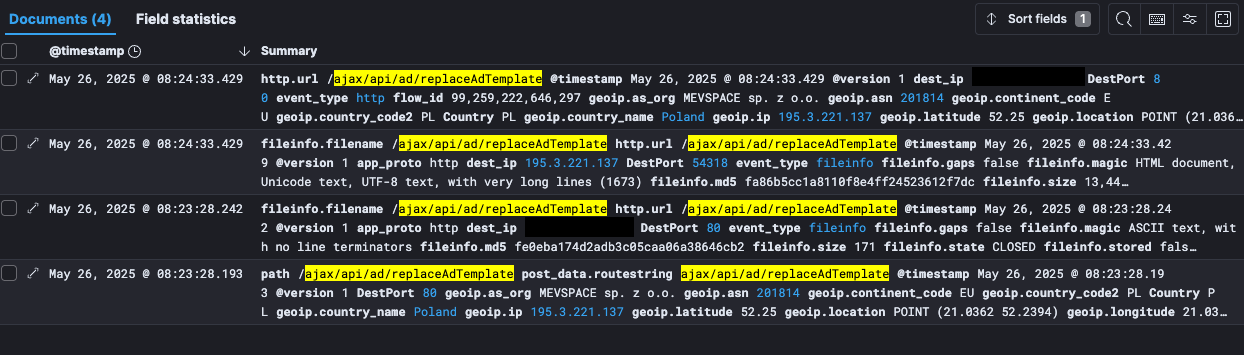
Supply: weblog.kevintel.com
Dewhurst traced one of many attackers to Poland, seeing makes an attempt to deploy PHP backdoors to execute system instructions.
The researcher famous that the assaults seem like leveraging the exploit printed earlier by Romano, although there have been Nuclei templates obtainable for the flaw since Might 24, 2025.
It is very important make clear that Dewhurst solely noticed exploitation makes an attempt for CVE-2025-48827, however no proof exists but that attackers have efficiently chained it to the total RCE, though that is extremely seemingly.
vBulletin troubles
vBulletin is among the most generally used business PHP/MySQL-based discussion board platforms, powering 1000’s of on-line communities globally.
Its modular design, together with cellular APIs and AJAX interfaces, makes it a posh and versatile platform. Nonetheless, it additionally exposes a broad assault floor.
Previously, hackers have leveraged extreme flaws within the platform to breach in style boards and steal the delicate knowledge of giant numbers of customers.
Discussion board directors are beneficial to use the safety updates for his or her vBulletin set up or transfer to the newest launch, model 6.1.1, which isn’t affected by the mentioned flaws.



