
A hacking group dubbed ‘Elusive Comet’ targets cryptocurrency customers in social engineering assaults that exploit Zoom’s distant management function to trick customers into granting them entry to their machines.
Zoom’s distant management function permits assembly members to take management of one other participant’s laptop.
In response to cybersecurity agency Path of Bits, which encountered this social engineering marketing campaign, the perpetrators mirror methods utilized by the Lazarus hacking group within the huge $1.5 billion Bybit crypto heist.
“The ELUSIVE COMET methodology mirrors the methods behind the latest $1.5 billion Bybit hack in February, the place attackers manipulated respectable workflows fairly than exploiting code vulnerabilities,” explains the Path of Bits report.
Zoom-based interview scheme
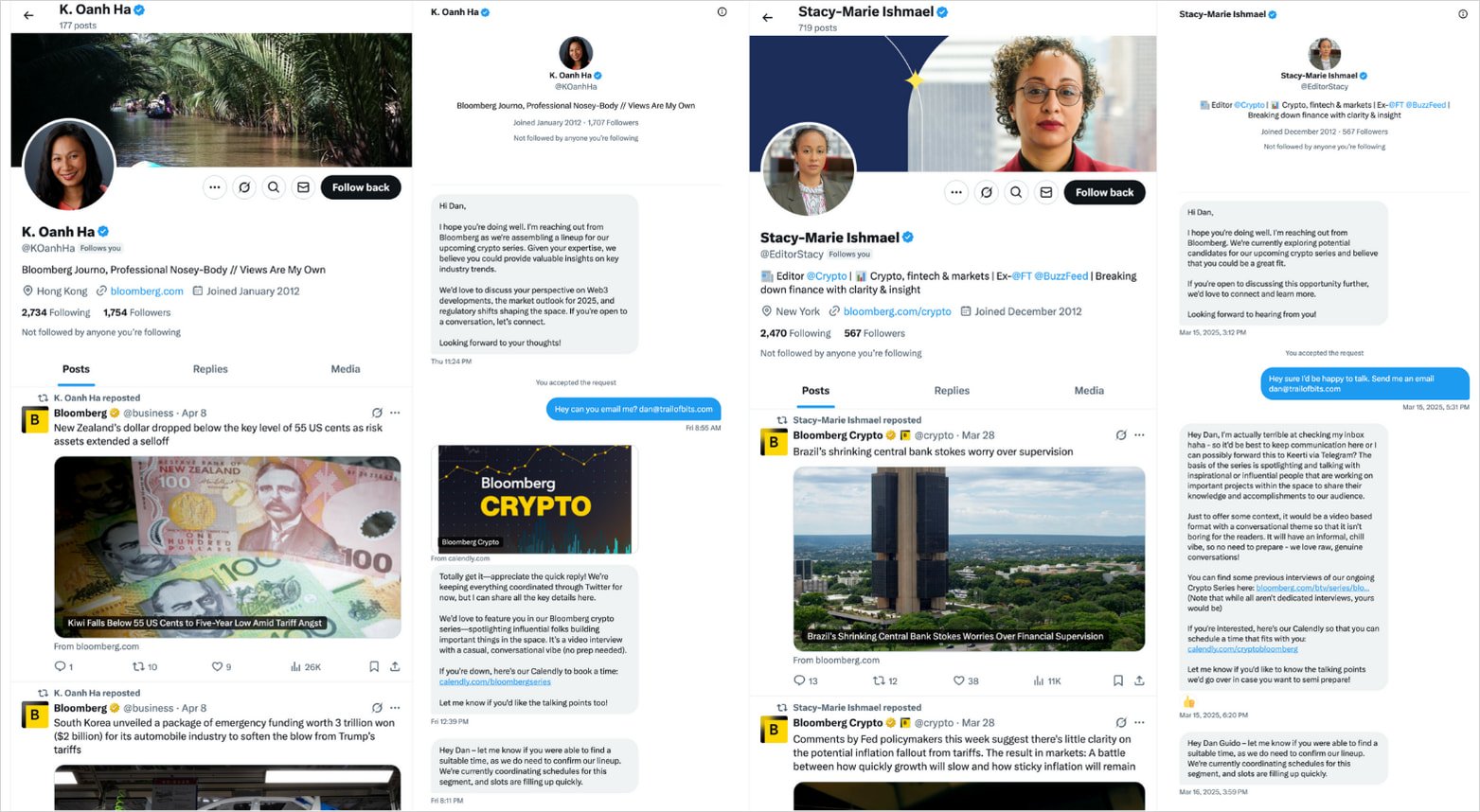
Path of Bits discovered of this new marketing campaign after the menace actors tried to conduct the social engineering assault on its CEO by way of X direct messages.
The assault begins with an invite to a “Bloomberg Crypto” interview by way of Zoom, despatched to high-value targets by way of sock-puppet accounts on X, or by way of e-mail (bloombergconferences[@]gmail.com).
The faux accounts impersonate crypto-focused journalists or Bloomberg shops and attain out to the targets by way of direct messages on social media platforms.
Supply: Path of Bits
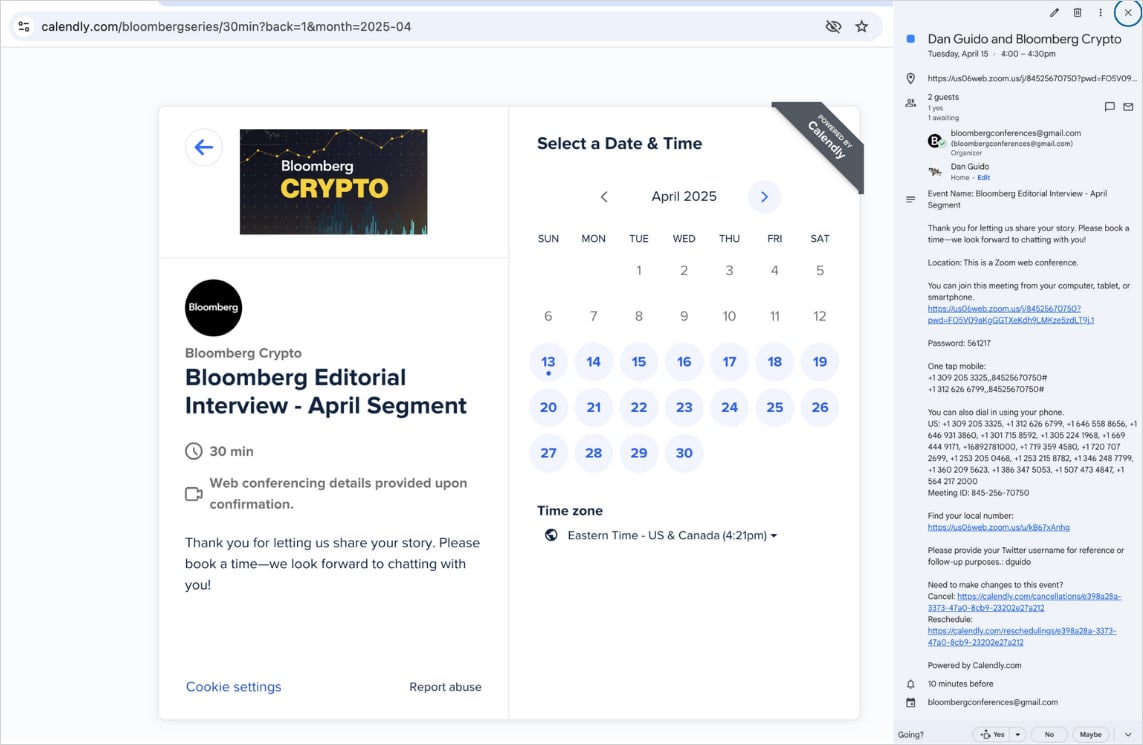
The invites are despatched by Calendly hyperlinks to schedule a Zoom assembly. Since each Calendly and Zoom invitations/hyperlinks are genuine, they work as anticipated and decrease the goal’s suspicions.
Supply: Path of Bits
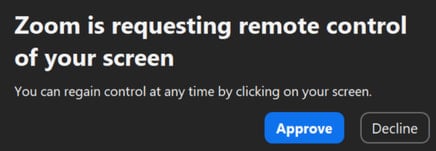
Throughout the Zoom name, the attacker initiates a screen-sharing session and sends a distant management request to the goal.
The trick employed on this stage is that the attackers rename their Zoom show title to “Zoom,” so the immediate the sufferer sees reads “Zoom is requesting distant management of your display,” making it seem as a respectable request from the app.
Supply: Path of Bits
Nonetheless, approving the request offers the attackers full distant enter management over the sufferer’s system, permitting them to steal delicate information, set up malware, entry recordsdata, or provoke crypto transactions.
The attacker might act shortly to ascertain persistent entry by implanting a stealthy backdoor for later exploitation and disconnect, leaving victims with little probability to understand the compromise.
“What makes this assault significantly harmful is the permission dialog’s similarity to different innocent Zoom notifications,” says Path of Bits.
“Customers habituated to clicking “Approve” on Zoom prompts might grant full management of their laptop with out realizing the implications.”
To defend in opposition to this menace, Path of Bits suggests the implementation of system-wide Privateness Preferences Coverage Management (PPPC) profiles that stop accessibility entry, which is feasible through the use of this assortment of instruments.
The agency recommends eradicating Zoom totally from all programs for security-critical environments and organizations that deal with precious digital belongings.
“For organizations dealing with significantly delicate information or cryptocurrency transactions, the chance discount from eliminating the Zoom consumer totally typically outweighs the minor inconvenience of utilizing browser-based options,” explains Path of Bits.


