
Hackers are probably beginning to exploit CVE-2025-49113, a essential vulnerability within the broadly used Roundcube open-source webmail utility that enables distant execution.
The safety situation has been current in Roundcube for over a decade and impacts variations of Roundcube webmail 1.1.0 via 1.6.10. It obtained a patch on June 1st.
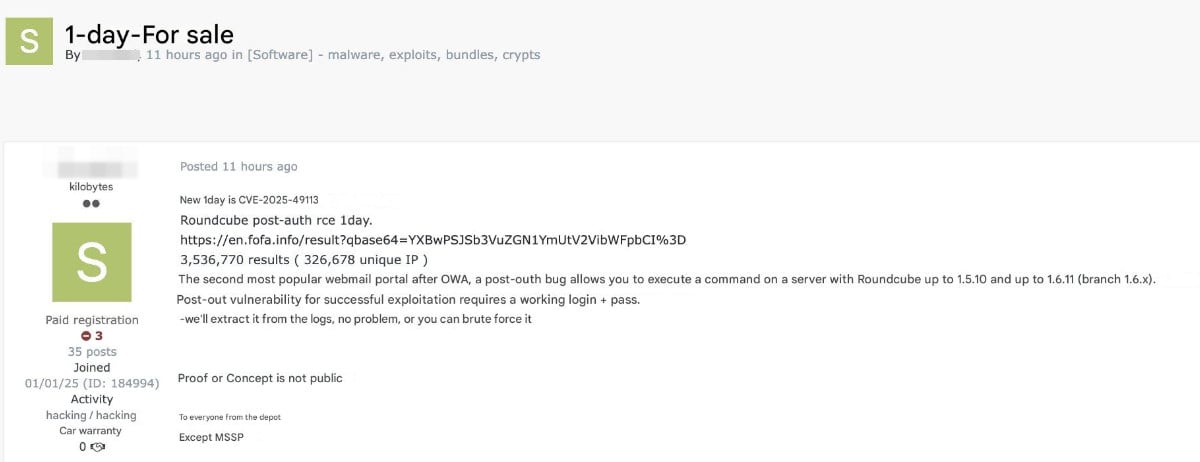
It took attackers simply a few days to reverse engineer the repair, weaponize the vulnerability, and begin promoting a working exploit on a minimum of one hacker discussion board.
Roundcube is without doubt one of the hottest webmail options because the product is included in gives from well-known internet hosting suppliers similar to GoDaddy, Hostinger, Dreamhost, or OVH.
“E-mail armageddon”
CVE-2025-49113 is a post-authentication distant code execution (RCE) vulnerability that obtained a essential severity rating of 9.9 out of 10 and is described as “electronic mail armageddon.”
It was found and reported by Kirill Firsov, the CEO of the cybersecurity firm FearsOff, who determined to publish the technical particulars earlier than the tip of the accountable disclosure interval as a result of an exploit had turn into obtainable.
“Given the energetic exploitation and proof of the exploit being offered in underground boards, I imagine it’s in the very best curiosity of defenders, blue groups, and the broader safety neighborhood to publish a full technical breakdown however with out full PoC for now” – Kirill Firsov
On the root of the safety downside is the shortage of sanitization of the $_GET[‘_from’] parameter, which ends up in PHP Object deserialization.
Within the technical report, Firsov explains that when an exclamation mark initiates a session variable title, the session turns into corrupted and object injection turns into doable.
After Roundcube obtained a patch, attackers analyzed the modifications it launched, developed an exploit, and marketed it on a hacker discussion board, noting {that a} working login is required.
Nevertheless, the necessity for login credentials doesn’t appear to be a deterrent, for the reason that menace actor providing the exploit says that they’ll extract it from the logs, or it may be brute pressured.
Firsov says that the credential mixture may be obtained via cross-site request forgery (CSRF).
supply: Kirill Firsov
In line with Firsov, a minimum of one vulnerability dealer pays as much as $50,000 for an RCE exploit in Roundcube.
The researcher revealed a video to exhibit how the vulnerability may be exploited. It ought to be famous that the researcher makes use of the vulnerability identifier CVE-2025-48745 within the demonstration, which is at the moment rejected as a duplicate candidate for CVE-2025-49113.
Regardless of being a less-known utility amongst customers, Roundcube may be very fashionable, largely as a result of it’s extremely customizable with greater than 200 choices, and it’s freely obtainable.
Other than being supplied by internet hosting suppliers and bundled in internet hosting management panels (cPanel, Plesk), quite a few organizations within the authorities, tutorial, and tech sectors use Roundcube.
Firsov additionally says that this webmail app has such a large presence {that a} pentester is extra prone to discover a Roundcube occasion than an SSL misconfiguration.
Contemplating the ubiquity of the applying, the researcher says that “the assault floor isn’t massive – it’s industrial.”
Certainly, a fast look on serps for locating internet-connected units and companies reveals a minimum of 1.2 million Roundcube hosts.
Handbook patching is outdated. It is sluggish, error-prone, and difficult to scale.
Be part of Kandji + Tines on June 4 to see why outdated strategies fall brief. See real-world examples of how fashionable groups use automation to patch sooner, lower threat, keep compliant, and skip the advanced scripts.



