Authored by Aayush Tyagi
Online game hacks, cracked software program, and free crypto instruments stay standard bait for malware authors. Lately, McAfee Labs uncovered a number of GitHub repositories providing these tempting “rewards,” however a more in-depth look reveals one thing extra sinister. Because the saying goes, if it appears too good to be true, it in all probability is.
GitHub is commonly exploited for malware distribution resulting from its accessibility, trustworthiness, and developer-friendly options. Attackers can simply create free accounts and host repositories that seem official, leveraging GitHub’s repute to deceive customers.
McAfee Labs encountered a number of repositories, providing recreation hacks for top-selling video video games similar to Apex Legends, Minecraft, Counter Strike 2.0, Roblox, Valorant,
Fortnite, Name of Obligation, GTA V and or providing cracked variations of standard software program and providers, similar to Spotify Premium, FL Studio, Adobe Specific, SketchUp Professional, Xbox Sport Cross, and Discord to call a number of.
Government abstract
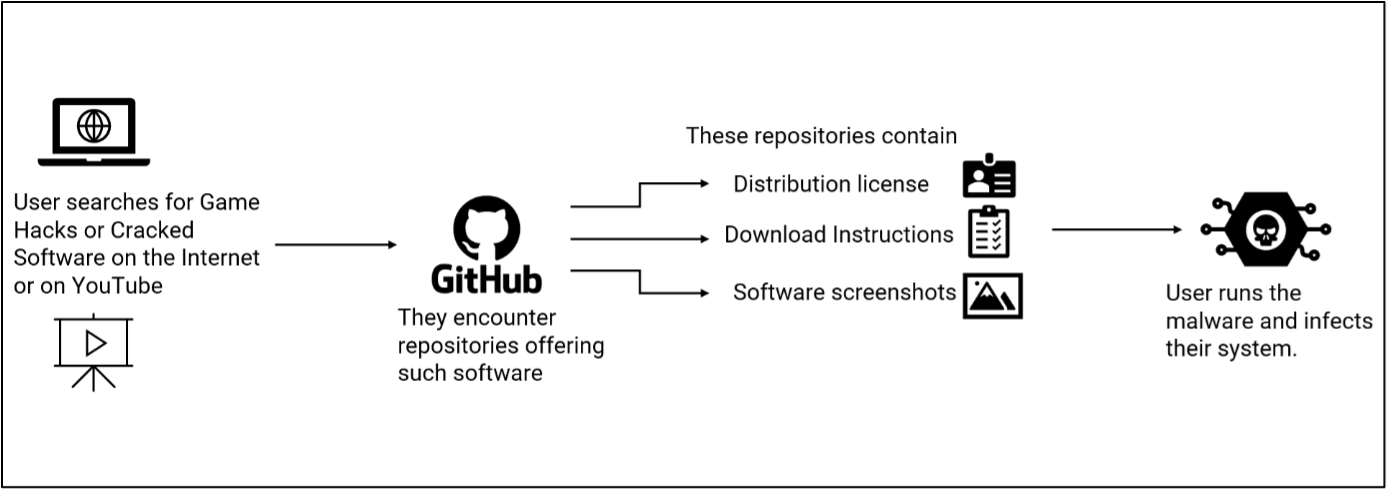
These assault chains start when customers would seek for Sport Hacks, cracked software program or instruments associated to Cryptocurrency on the web, the place they’d finally come throughout GitHub repositories or YouTube Movies resulting in such GitHub repositories, providing such software program.
We observed a community of such repositories the place the outline of software program retains on altering, however the payload stays the identical: a Lumma Stealer variant. Each week, a brand new set of repositories with a brand new malware variant is launched, because the older repositories are detected and eliminated by GitHub. These repositories additionally embrace distribution licenses and software program screenshots to boost their look of legitimacy.
Determine 1: Assault Vector
These repositories additionally include directions on find out how to obtain and run the malware and ask the person to disable Home windows Defender or any AV software program, earlier than downloading the malware. They supply the reasoning that, for the reason that software program is said to recreation hacks or by-passing software program authentication or crypto-currency mining, AV merchandise will detect and delete these purposes.
This social engineering approach, mixed with the trustworthiness of GitHub works properly within the favor of malware authors, enabling them to contaminate extra customers.
Kids are often focused by such scams, as malware authors exploit their curiosity in recreation hacks by highlighting potential options and advantages, making it simpler to contaminate extra programs.
Technical Evaluation
As mentioned above, the customers would come throughout malicious repositories by way of looking out the web (highlighted in purple).
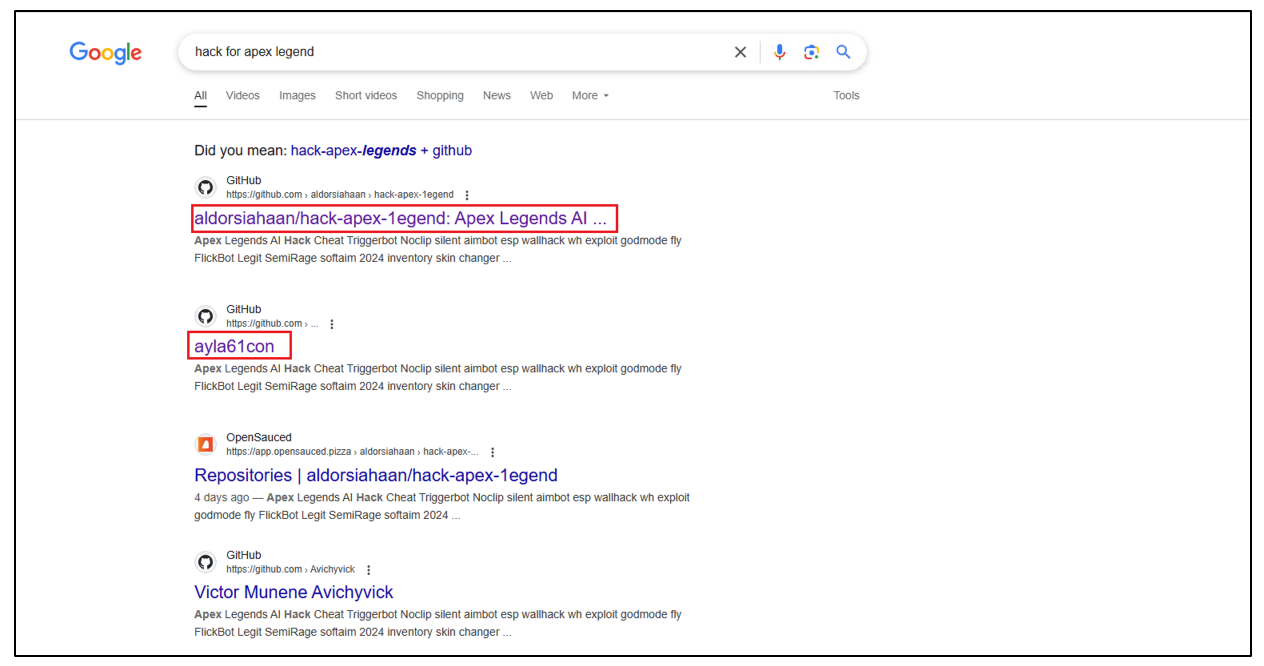
Determine 2: Web Search displaying GitHub outcomes.
Or by way of YouTube movies, that include a hyperlink to the repository within the description (highlighted in purple).
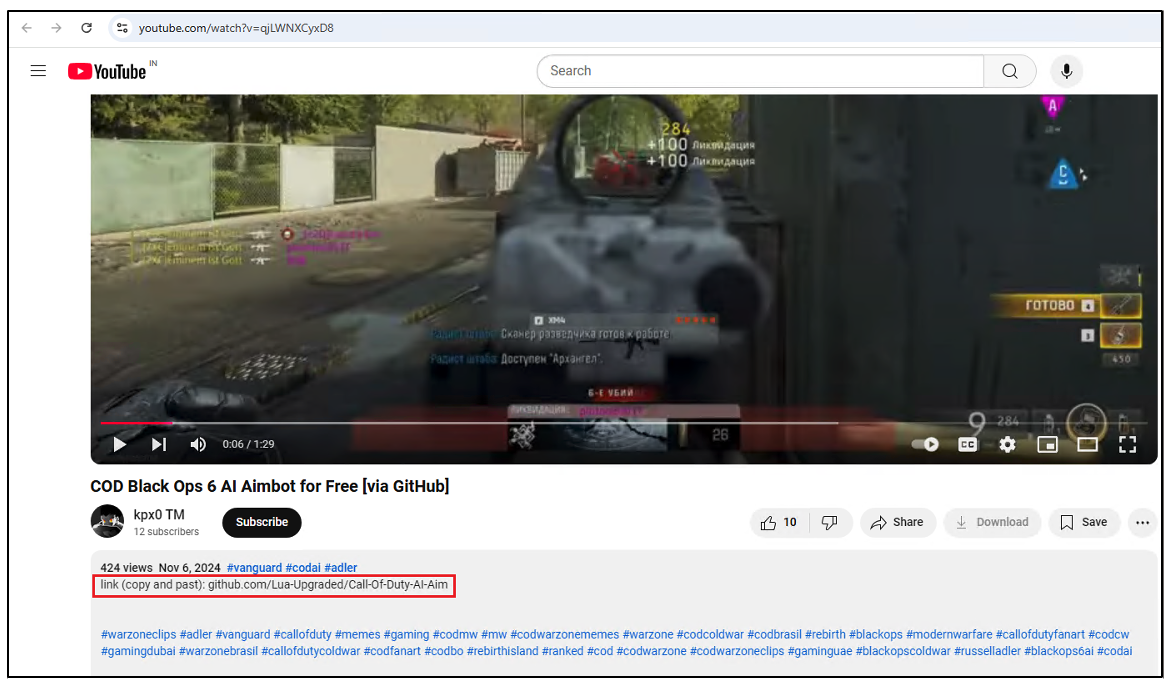
Determine 3: YouTube Video containing malicious URL in description.
As soon as the person accesses the GitHub repository, it accommodates a Distribution license and different supporting recordsdata, to trick the person into considering that the repository is real and credible.
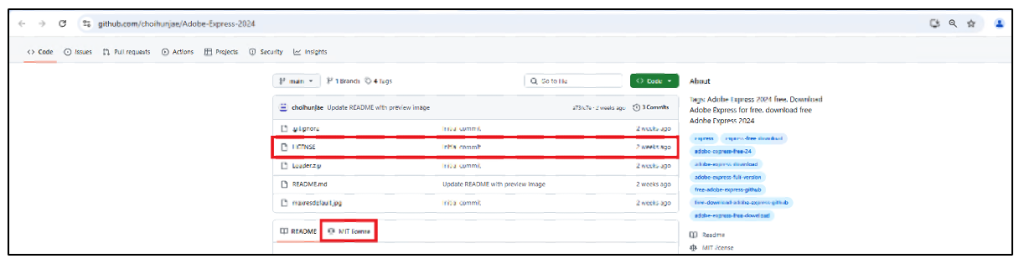
Determine 4: GitHub repository containing Distribution license.
Repositories additionally include an in depth description of the software program and set up course of additional manipulating the person.
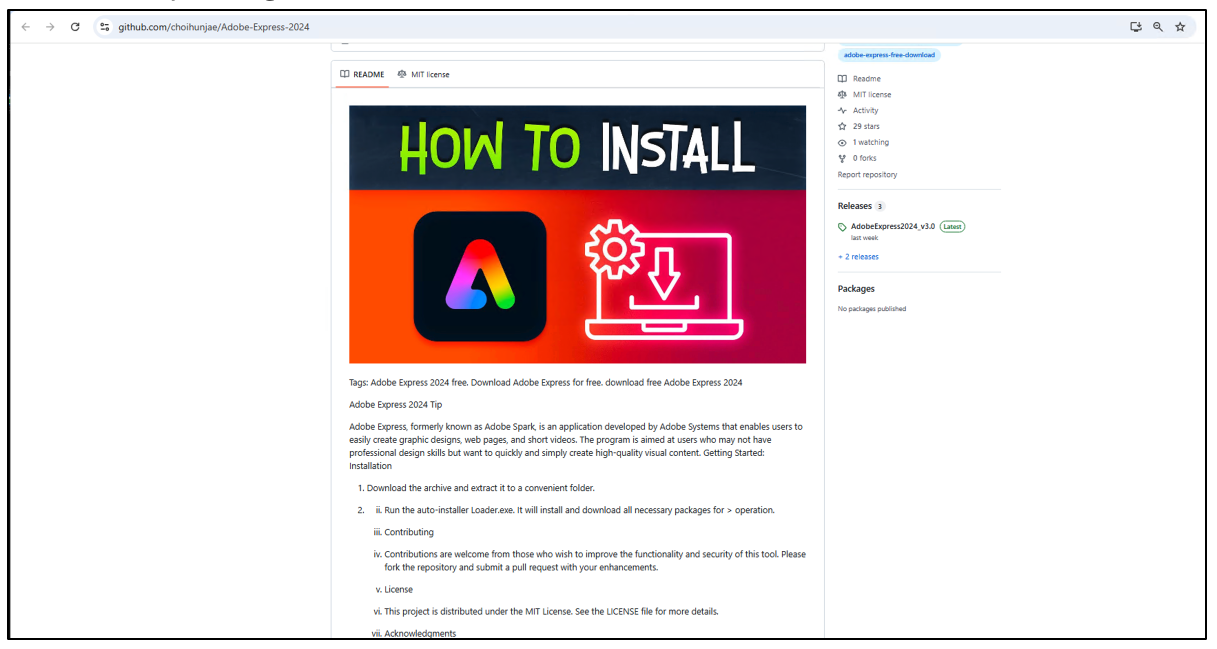
Determine 5: Obtain directions current within the repository.
Typically, the repositories include directions to disable AV merchandise, deceptive customers to contaminate themselves with the malware.
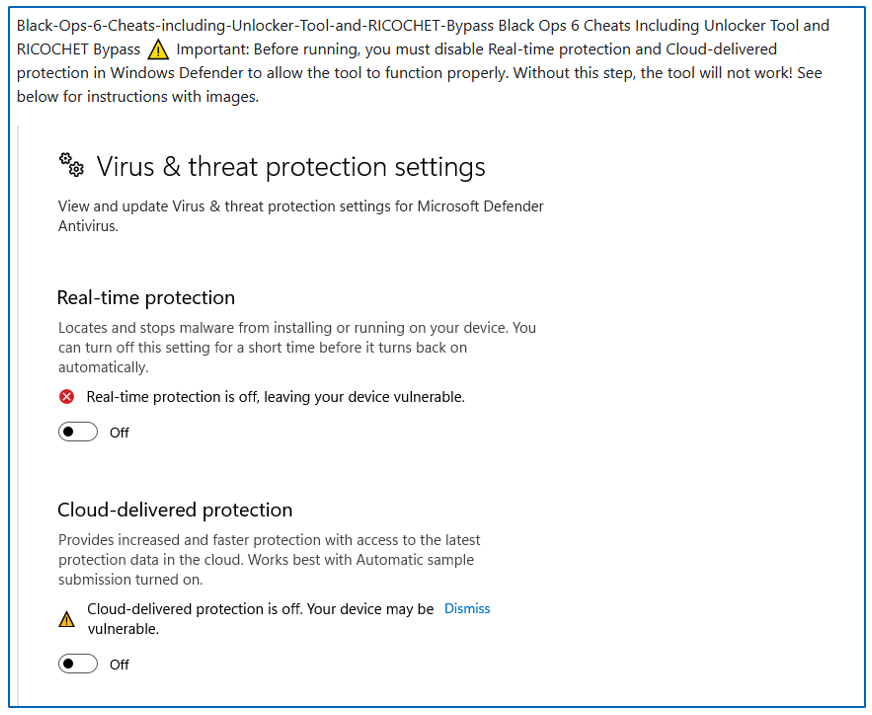
Determine 6: Directions to disable Home windows Defender.
To focus on extra kids, repositories include an in depth description of the software program; by highlighting all of the options included throughout the bundle, similar to Aimbots and Velocity Hacks, and the way simply they’ll have the ability to achieve a bonus over their opponents.
They even point out that the bundle comes with advance Anti-Ban system, so their account received’t be suspended, and that the software program has a preferred group, to create a notion that, since a number of customers are already utilizing this software program, it have to be protected to make use of and that, by not utilizing the software program, they’re lacking out.
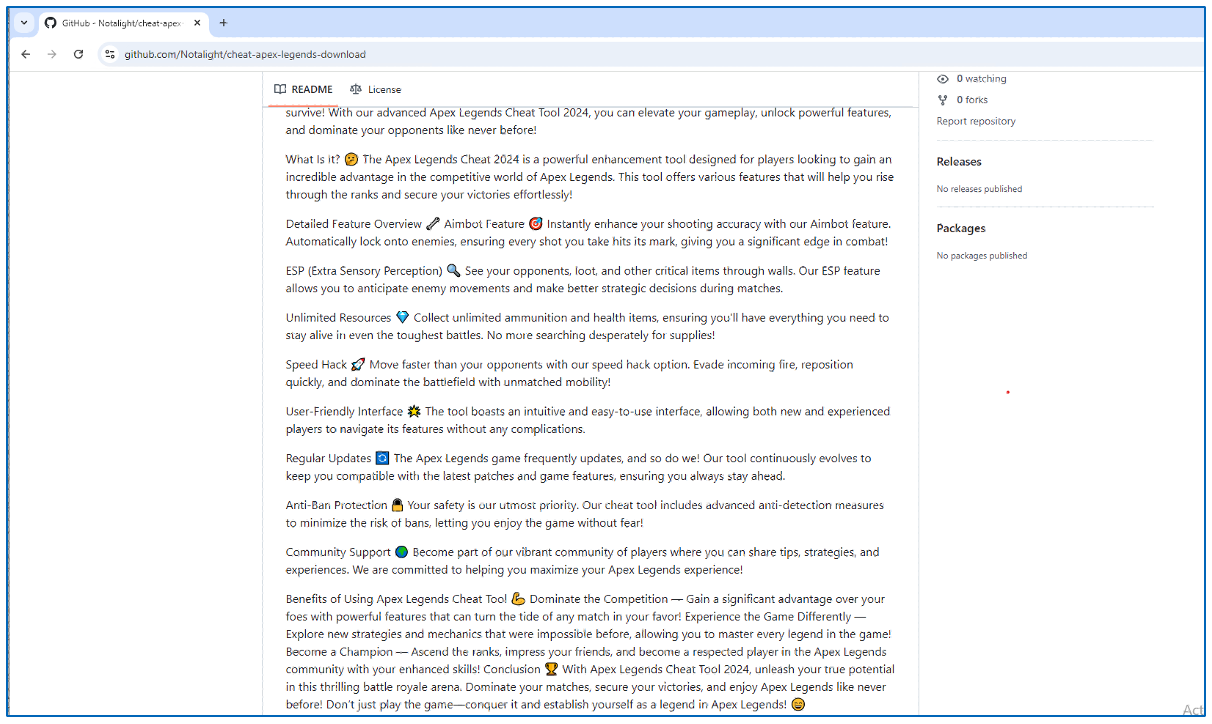
Determine 7: Options talked about within the GitHub repository.
The downloaded recordsdata, typically, have been Lumma Stealer variants, however observing the most recent repositories, we observed new malware variants have been additionally being distributed by way of the identical an infection vector.
As soon as the person downloads the file, they get the next set of recordsdata.
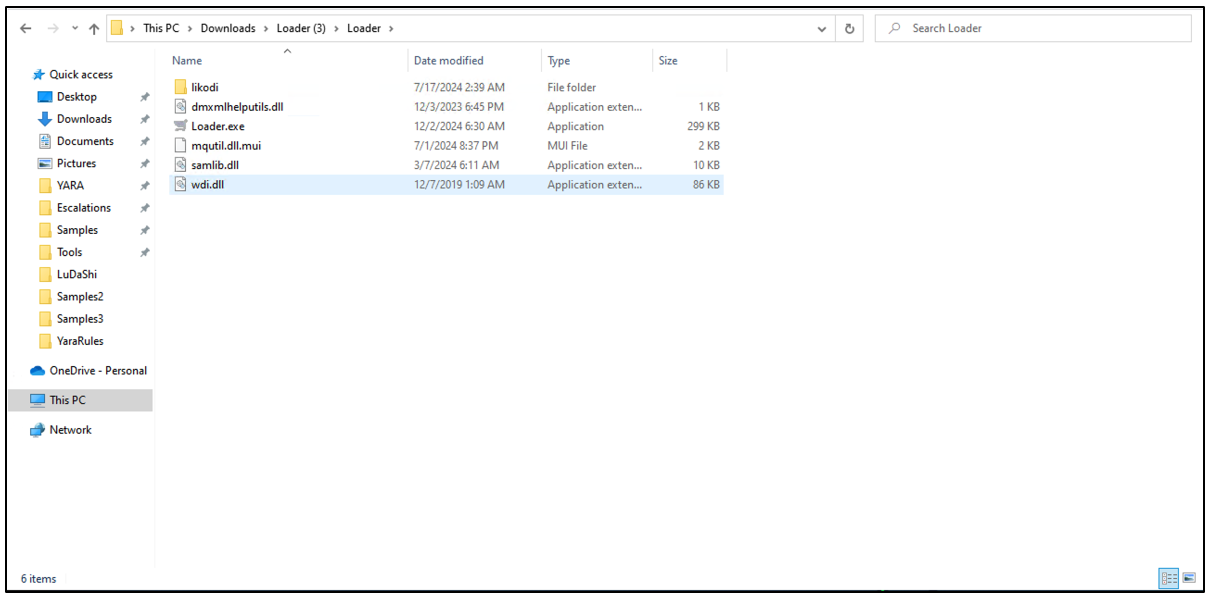
Determine 8: Information downloaded from GitHub repository.
On operating the ‘Loader.exe’ file, as instructed, it iterates by way of the system and the registry keys to gather delicate data.
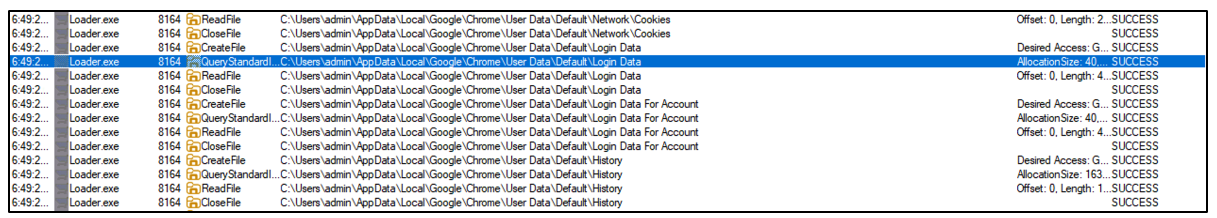
Determine 9: Loader.exe checking for Login credentials for Chrome.
It searches for crypto wallets and password associated recordsdata. It searches for a listing of browsers put in and iterates by way of person knowledge, to assemble something helpful.

Determine 10: Loader.exe checking for Browsers put in on the system.
Then the malware connects to C2 servers to switch knowledge.

Determine 11: Loader.exe connecting to C2 servers to switch knowledge.
This conduct is much like the Lumma Stealer variants now we have seen earlier.
Detection and Mitigation Methods
McAfee blocks this an infection chain at a number of levels:
- URL blocking of the GitHub repository.
Determine 12: McAfee blocking URLs
- Detecting downloaded malware.
Determine 13: McAfee blocking the malicious file
Conclusion and Suggestions
In conclusion, the GitHub repository an infection chain demonstrates how cybercriminals exploit accessibility and trustworthiness of standard web sites similar to GitHub, to distribute malware like Lumma Stealer. By leveraging the person’s want to make use of recreation hacks, to be higher at a sure online game or receive licensed software program without cost, they trick customers into infecting themselves.
At McAfee Labs, we’re dedicated to serving to organizations shield themselves towards subtle cyber threats, such because the GitHub repository approach. Listed here are our really useful mitigations and remediations:
- Kids are often the prime targets for such scams, you will need to educate the younger ones and educate them find out how to keep away from such fishy web sites.
- Conduct common coaching classes to coach customers about social engineering techniques and phishing schemes.
- Set up and keep up to date antivirus and anti-malware software program on all endpoints.
- Use community segmentation to restrict the unfold of malware throughout the group.
- Guarantee all working programs, software program, and purposes are saved updated with the most recent safety patches.
- Keep away from downloading cracked software program or visiting suspicious web sites.
- Confirm URLs in emails, particularly from unknown or sudden sources.
- Hold antivirus options up to date and actively scanning.
- Keep away from downloading Sport hacks or Crypto software program from unofficial web sites.
- If potential, learn critiques in regards to the software program you’re downloading and see what different customers are saying in regards to the malware.
- Repeatedly patch browsers, working programs, and purposes.
- Monitor the Temp folder for uncommon or suspicious recordsdata.
Indicators of Compromise (IoCs)
As of publishing this weblog, these are the GitHub repositories which are presently lively.
| File Kind | SHA256/URLs |
| URLs | github[.]com/632763276327ermwhatthesigma/hack-apex-1egend |
| github[.]com/VynnProjects/h4ck-f0rtnite | |
| github[.]com/TechWezTheMan/Discord-AllinOne-Device | |
| github[.]com/UNDERBOSSDS/ESET-KeyGen-2024 | |
| github[.]com/Rinkocuh/Dayz-Cheat-H4ck-A1mb0t | |
| github[.]com/Magercat/Al-Photoshop-2024 | |
| github[.]com/nate24321/minecraft-cheat2024 | |
| github[.]com/classroom-x-games/counter-str1ke-2-h4ck | |
| github[.]com/LittleHa1r/ESET-KeyGen-2024 | |
| github[.]com/ferhatdermaster/Adobe-Specific-2024 | |
| github[.]com/CrazFrogb/23fasd21/releases/obtain/loader/Loader[.]Github[.]zip | |
| github[.]com/flashkiller2018/Black-Ops-6-Cheats-including-Unlocker-Device-and-RICOCHET-Bypass | |
| github[.]com/Notalight/h4ck-f0rtnite | |
| github[.]com/Ayush9876643/r0blox-synapse-x-free | |
| github[.]com/FlqmzeCraft/cheat-escape-from-tarkov | |
| github[.]com/Ayush9876643/cheat-escape-from-tarkov | |
| github[.]com/Ayush9876643/rust-hack-fr33 | |
| github[.]com/ppetriix/rust-hack-fr33 | |
| github[.]com/Ayush9876643/Roblox-Blox-Fruits-Script-2024 | |
| github[.]com/LandonPasana21/Roblox-Blox-Fruits-Script-2024 | |
| github[.]com/Ayush9876643/Rainbow-S1x-Siege-Cheat | |
| github[.]com/Ayush9876643/SonyVegas-2024 | |
| github[.]com/123456789433/SonyVegas-2024 | |
| github[.]com/Ayush9876643/Nexus-Roblox | |
| github[.]com/cIeopatra/Nexus-Roblox | |
| github[.]com/Ayush9876643/m0dmenu-gta5-free | |
| github[.]com/GerardoR17/m0dmenu-gta5-free | |
| github[.]com/Ayush9876643/minecraft-cheat2024 | |
| github[.]com/RakoBman/cheat-apex-legends-download | |
| github[.]com/Ayush9876643/cheat-apex-legends-download | |
| github[.]com/cIiqued/FL-Studio | |
| github[.]com/Ayush9876643/FL-Studio | |
| github[.]com/Axsle-gif/h4ck-f0rtnite | |
| github[.]com/Ayush9876643/h4ck-f0rtnite | |
| github[.]com/SUPAAAMAN/m0dmenu-gta5-free | |
| github[.]com/atomicthefemboy/cheat-apex-legends-download | |
| github[.]com/FlqmzeCraft/cheat-escape-from-tarkov | |
| github[.]com/Notalight/h4ck-f0rtnite | |
| github[.]com/Notalight/FL-Studio | |
| github[.]com/Notalight/r0blox-synapse-x-free | |
| github[.]com/Notalight/cheat-apex-legends-download | |
| github[.]com/Notalight/cheat-escape-from-tarkov | |
| github[.]com/Notalight/rust-hack-fr33 | |
| github[.]com/Notalight/Roblox-Blox-Fruits-Script-2024 | |
| github[.]com/Notalight/Rainbow-S1x-Siege-Cheat | |
| github[.]com/Notalight/SonyVegas-2024 | |
| github[.]com/Notalight/Nexus-Roblox | |
| github[.]com/Notalight/minecraft-cheat2024 | |
| github[.]com/Notalight/m0dmenu-gta5-free | |
| github[.]com/ZinkosBR/r0blox-synapse-x-free | |
| github[.]com/ZinkosBR/cheat-escape-from-tarkov | |
| github[.]com/ZinkosBR/rust-hack-fr33 | |
| github[.]com/ZinkosBR/Roblox-Blox-Fruits-Script-2024 | |
| github[.]com/ZinkosBR/Rainbow-S1x-Siege-Cheat | |
| github[.]com/ZinkosBR/Nexus-Roblox | |
| github[.]com/ZinkosBR/m0dmenu-gta5-free | |
| github[.]com/ZinkosBR/minecraft-cheat2024 | |
| github[.]com/ZinkosBR/h4ck-f0rtnite | |
| github[.]com/ZinkosBR/FL-Studio | |
| github[.]com/ZinkosBR/cheat-apex-legends-download | |
| github[.]com/EliminatorGithub/counter-str1ke-2-h4ck | |
| Github[.]com/ashishkumarku10/call-0f-duty-warz0ne-h4ck | |
| EXEs | CB6DDBF14DBEC8AF55986778811571E6 |
| C610FD2A7B958E79F91C5F058C7E3147 | |
| 3BBD94250371A5B8F88B969767418D70 | |
| CF19765D8A9A2C2FD11A7A8C4BA3DEDA | |
| 69E530BC331988E4E6FE904D2D23242A | |
| 35A2BDC924235B5FA131095985F796EF | |
| EB604E2A70243ACB885FE5A944A647C3 | |
| 690DBCEA5902A1613CEE46995BE65909 | |
| 2DF535AFF67A94E1CDAD169FFCC4562A | |
| 84100E7D46DF60FE33A85F16298EE41C | |
| 00BA06448D5E03DFBFA60A4BC2219193 | |
| C2 Domains | 104.21.48.1 |
| 104.21.112.1 | |
| 104.21.16.1 |



