
Outcomes from Pentera’s 4th Pentesting report, which surveyed round 500 CISOs globally, present that whereas Publicity Administration practices are maturing, there are nonetheless some gaps the market is but to handle.
The fashionable assault floor is sprawling, dynamic, distributed, and dangerously opaque. As enterprises broaden into cloud-native or hybrid architectures, deploy APIs by the 1000’s, and combine IoT and OT units into core operations, the floor space for cyber threats grows each in measurement and complexity. In the present day, the typical enterprise manages 75 safety instruments, and almost half of CISOs report continued development of their safety stacks 12 months over 12 months.
This complexity isn’t deterring attackers. It permits them. Menace actors function opportunistically. No floor is protected as a result of attackers are pushed to take advantage of no matter is uncovered; they’re finally motivated to focus on surfaces which can be comparatively weaker than the subsequent. For safety leaders, this implies it’s not a query of cowl extra floor, however the place to focus for optimum safety – the place throughout the assault floor is the specter of danger most implicated?
The just lately launched 2025 State of Pentesting report by Pentera reveals the relative vulnerability of various assault surfaces, from cloud infrastructure and web-facing property to APIs, endpoints, and even IoT methods. CISOs from 500 enterprises have been requested the place throughout their community they understand danger, the place pentesting efforts are directed, and which areas have been finally breached.
The outcomes present perception for safety groups to sharpen their focus, direct their testing methods, and shut the riskiest exposures quicker.
Take a proactive method to managing and decreasing cyber danger, achieve professional insights from cybersecurity leaders on securing enterprise-wide networks, and listen to how high trade gamers are implementing the levels of Steady Menace Publicity Administration (CTEM).
Xposure delivers a forward-thinking method to cyber resilience.
The Little Realized Fact about Publicity Administration
Even with the best-run publicity administration packages, breaches nonetheless happen. However working inside extra mature safety packages, you notice a breach doesn’t at all times imply compromise.
Take the instance of an uncovered asset. It is likely to be breached within the technical sense—maybe even with a menace actor establishing a foothold on it.. But when that asset isn’t tied to delicate information, manufacturing methods, or crucial companies, the real-world influence is negligible.
Not all breaches are equal. That’s the foundational mindset shift publicity administration brings.
Not like conventional vulnerability administration, the place groups are chasing down CVEs primarily based on severity scores or ticket age, publicity administration is strategic. It considers each exploitability and influence to find out what vulnerabilities really matter. This twin lens permits groups to bypass the noise and zero-in on the exposures that may result in devastating compromise.
The State of Pentesting report reinforces this reality. Regardless of almost 67% of enterprises reporting a breach previously two years, solely 36% confronted downtime, 30% suffered information publicity, and 28% incurred monetary loss. Meaning a good portion of “breaches” had little or no operational consequence. The aim is not to get rid of each breach – however solely those that may harm you.
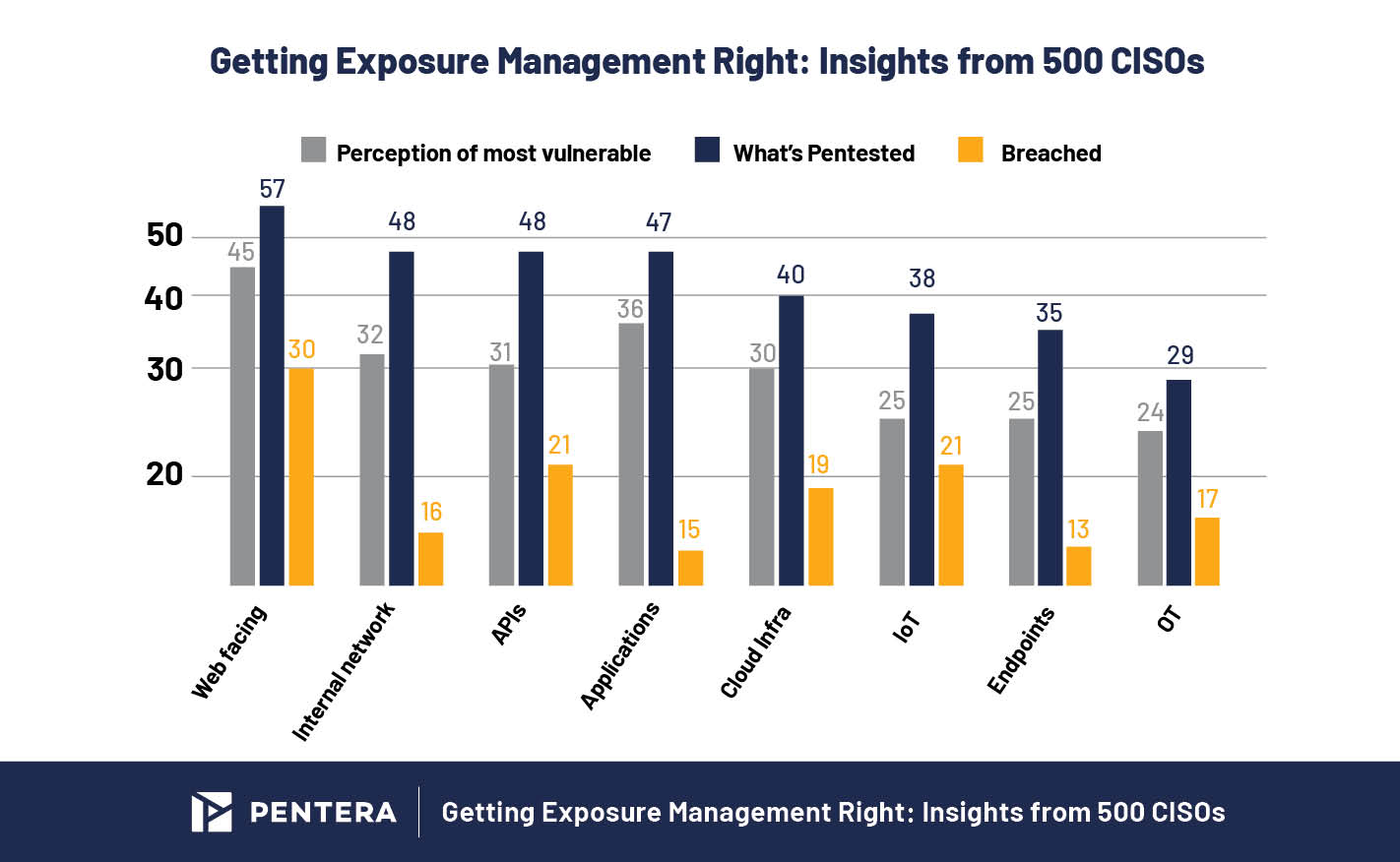
Net-Going through Belongings – Nonetheless the Weakest Hyperlink
If publicity administration is about aligning remediation with danger, web-facing property are the prime instance of a cautionary story.
In keeping with the information, web-facing property high all three metrics: they’re perceived as probably the most susceptible (45%), examined probably the most (57%), and breached probably the most often (30%).
In some methods that is encouraging. It exhibits that safety groups are precisely prioritizing exterior property, recognizing them as each accessible and engaging targets, and directing pentesting efforts accordingly.
However regardless of all that spotlight, attackers are nonetheless getting in.
Why? As a result of simply on the idea of publicity, web-facing property are dangerous. These methods – DNS, internet portals, and login pages are designed to be reachable. Their openness makes them “low-hanging fruit,” particularly when misconfigurations, uncovered companies, or open ports are left unchecked and with out compensating controls corresponding to MFA.
But this doesn’t imply failure.
If attackers breach a public-facing asset and attain a lifeless finish – no entry to delicate methods, no worthwhile information, no lateral motion – then, so what? The breach had no influence. In publicity administration, it’s not nearly decreasing breach charges – it’s about decreasing the influence of breaches that do happen.
Inside Networks, Endpoints, and Functions – A Contained Entrance
On the subject of methods closest to the crown jewels, organizations are getting it proper. They’re extensively examined (48%) thought-about susceptible (32%), and are seeing low breach charges (16%).
Inside networks, endpoints, and purposes every rank within the high tier for pentesting exercise and present comparatively low breach charges, 16% for inside networks, 13% for endpoints, and 15% for purposes. All suggesting a payoff in targeted effort.
These are methods that home delicate information, energy operations, and characterize a transparent path to lateral motion or privilege escalation. Their perceived criticality earns them a higher stage of focus and a spotlight, with layered safety controls and tooling that’s extra mature. It additionally displays one thing deeper: publicity administration maturity. Organizations aren’t simply scanning these methods for vulnerabilities, they’re pentesting them in context, prioritizing primarily based on potential influence, and validating to substantiate that defenses maintain below strain.
API Threat – Exhibits Hole Between Notion and Actuality
APIs sit on the intersection of enterprise logic and backend methods. They’re important, deeply built-in, and infrequently missed, with information from the survey report indicating APIs could also be extra susceptible than safety groups notice.
Whereas APIs are examined at the same price to inside networks (48%), they present a better breach price, 21%, in comparison with 16% for inside networks. That hole suggests a disconnect: both the perceived danger of APIs is just too low, or present testing approaches aren’t revealing the total image.
The problem is complexity. APIs are dynamic, arduous to stock, and notoriously tough to check properly. Their assault floor isn’t nearly ports or endpoints, it’s about logic flaws, damaged authentication, and misconfigured integrations, all resulting in assault pathways that don’t present up in an ordinary scan.
APIs additionally often bridge methods, whether or not between cloud companies, third-party instruments, cell apps, and inside databases. That makes them prime targets for lateral motion or information exfiltration. And their visibility hole makes them particularly engaging to attackers who perceive transfer beneath the radar.
Closing the hole means leveling up testing, each when it comes to frequency and depth. Steady, adversarial testing of APIs is important to show integration flaws that conventional strategies seem like lacking.
Publicity Administration Exhibits Encouraging Indicators of Alignment
The 2025 State of Pentesting report confirms what we’ve recognized for years – nearer proximity to enterprise danger drives sharper execution.
There’s rising alignment between perceived danger, pentesting exercise, and breaches. A powerful sign that publicity administration practices are maturing, as groups are minimising the hole between assumed and precise danger.
The aim of publicity administration isn’t to forestall each breach. It’s to forestall those that matter. By combining data-driven prioritization with steady validation, safety groups can give attention to actual exposures, not theoretical threats. Making certain that when the attacker comes knocking, there’s nothing worthwhile behind that door.
To be taught extra about how main enterprises are implementing their Publicity Administration packages, attend Xposure, the Nationwide Publicity Administration vSummit.
Sponsored and written by Pentera.


