
Europol has confirmed {that a} Telegram channel impersonating the company and providing a $50,000 reward for info on two Qilin ransomware directors is pretend. The impostor later admitted it was created to troll researchers and journalists.
“We have been additionally shocked to see this story gaining traction,” Europol informed BleepingComputer on Monday. “The announcement did not come from us.”
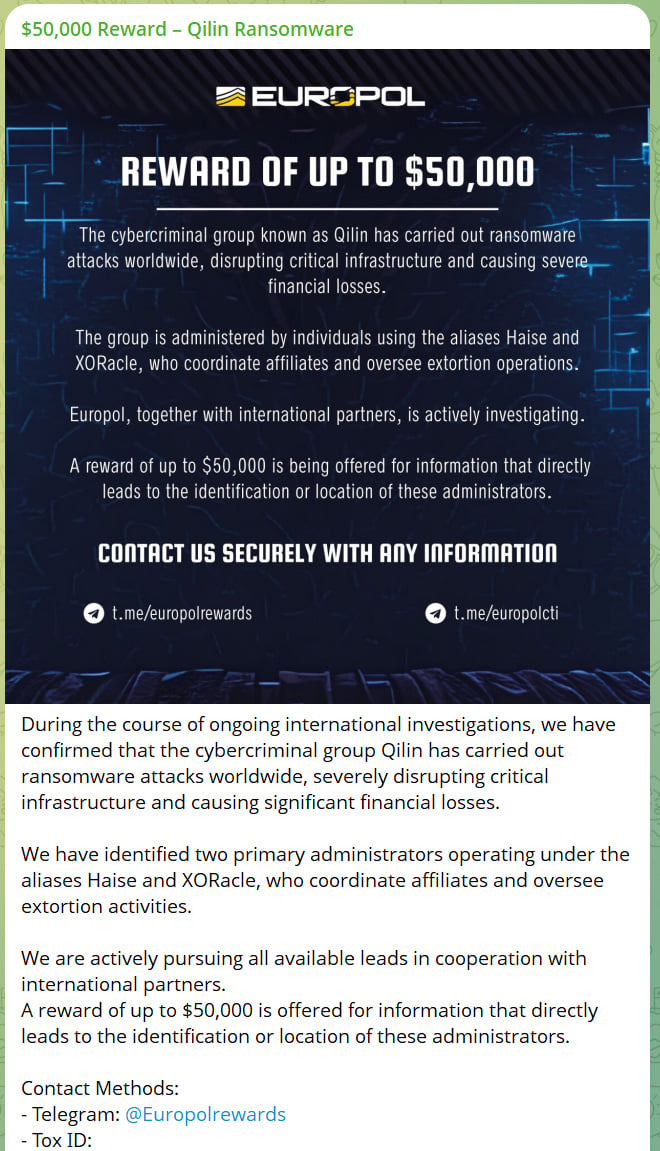
The assertion comes after a brand new Telegram channel referred to as @europolcti was created on August sixteenth, claiming to supply a $50,000 reward for info on two Qilin ransomware admins generally known as “Haise” and “XORacle”.
“Throughout the course of ongoing worldwide investigations, now we have confirmed that the cybercriminal group Qilin has carried out ransomware assaults worldwide, severely disrupting important infrastructure and inflicting important monetary losses,” reads the imposter’s Telegram submit.
“We’ve recognized two major directors working beneath the aliases Haise and XORacle, who coordinate associates and oversee extortion actions.”
“We’re actively pursuing all obtainable leads in cooperation with worldwide companions.”
“A reward of as much as $50,000 is obtainable for info that straight results in the identification or location of those directors.”
Supply: BleepingComputer
Haise is believed to be one of many operators of the Qilian ransomware gang, beforehand recruiting associates on the RAMP cybercrime discussion board.
The Qilin ransomware operation was initially launched as “Agenda” in August 2022. Nevertheless, by September that 12 months, it had rebranded beneath the title Qilin, which it continues to make use of to today.
The ransomware operation is among the most lively, at the moment concentrating on corporations worldwide.
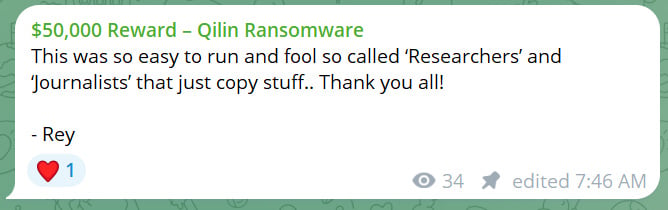
Nevertheless, after Europol confirmed it was pretend, a brand new submit appeared on the imposter channel claiming it was created to troll researchers and journalists, a few of whom wrote articles in regards to the claims.
“This was really easy to run and idiot so referred to as ‘Researchers’ and ‘Journalists’ that simply copy stuff.. Thanks all!,” reads the brand new submit.
Supply: BleepingComputer
The submit was signed by Rey, a hacker beforehand linked to breaches at Telefonica and Orange Group.
Nevertheless, the really trolling began in August fifteenth posts on a Telegram channel impersonating menace actors from “Scattered Spider”, “ShinyHunters”, and “Lapsus,” the place somebody had begun calling out Haise and the ransomware operation.
This isn’t the primary time menace actors tried to mislead the media about cybercrime.
In 2021, a RAMP admin generally known as ‘Orange’ or ‘boriselcin’ and who ran the “Groove” ransomware web site, referred to as on menace actors to assault the USA. This menace actor was later sanctioned by the US for his involvement in three ransomware operations that focused victims throughout america.
After the media lined this submit, together with BleepingComputer, the menace actor claimed it was pretend and was created to troll and manipulate the media and safety researchers.
Nevertheless, safety researchers from McAfee and Intel 471 consider that it was seemingly the menace actor making an attempt to cowl up for a failed ransomware-as-a-service.
In 2023, BleepingComputer receieved a “tip” about an alleged arrest of two Canadian teenagers over a crypto-theft assault.
Whereas BleepingComputer discovered that the information was pretend and didn’t cowl the story, we have been informed it was completed to control the media and “troll” the individuals accused of the theft.



