
Hackers are hijacking expired or deleted Discord invite hyperlinks to redirect customers to malicious websites that ship distant entry trojans and information-stealing malware.
The marketing campaign depends on a flaw within the Discord invitation system to leverage multi-stage infections that evade a number of antivirus engines.
“Reviving” expired Discord invitations
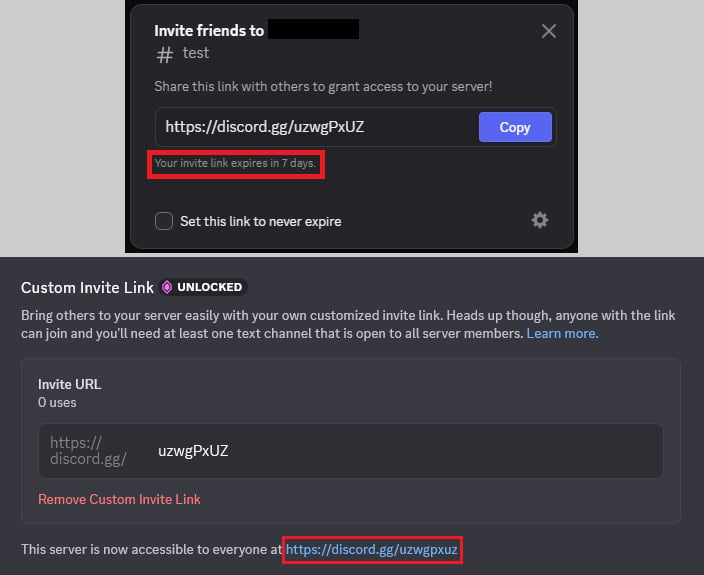
Discord invite hyperlinks are URLs that enable somebody to hitch a particular Discord server. They comprise an invitation code, which is a distinctive identifier that grants entry to a server and could be short-term, everlasting, or customized – vainness hyperlinks obtainable to ‘stage 3’ servers paying for particular perks.
As a part of the perks for stage 3 Discord servers, directors can create a personalised invite code. For normal servers, Discord generates random invite hyperlinks robotically and the possibility of 1 repeating itself could be very low.
Nevertheless, hackers seen that when a stage 3 server loses its enhance standing, the customized invite code turns into obtainable and could be reclaimed by one other server.
Researchers at cybersecurity firm Verify Level say that that is additionally true within the case of expired short-term invitations or deleted everlasting invitation hyperlinks.
They are saying that “the mechanism for creating customized invite hyperlinks surprisingly allows you to reuse expired short-term invite codes, and, in some circumstances, deleted everlasting invite codes.”
Supply: Verify Level
Moreover, the researchers say that Discord’s defective mechanism doesn’t modify the expiration time of an already generated short-term invitation code when reusing it as a everlasting invitation hyperlink.
“Customers typically mistakenly consider that by merely checking this field, they’ve made the present invite everlasting (and it was this misunderstanding that was exploited within the assault we noticed)” – Verify Level
An invitation code with lowercase letters and digits can’t be registered so long as it’s lively. Nevertheless, if the code has uppercase letters, it may be reused in vainness hyperlinks with lowercase, even when the unique continues to be legitimate.
Verify Level researchers clarify that that is attainable as a result of Discord shops and compares vainness hyperlinks in lowercase. In consequence, the identical code with decrease and uppercase letters is legitimate for 2 separate servers on the similar time.
Redirecting to malicious servers
Attackers are monitoring deleted or expired Discord invites and use them in a marketing campaign that has impacted 1,300 customers within the US, UK, France, the Netherlands, and Germany, based mostly on Verify Level’s obtain depend of the malicious payloads.
The researchers say that cybercriminals are hijacking Discord invite hyperlinks from reputable communities, and share them on social media or official comunity web sites. So as to add credibility to the deceit, hackers design the malicious servers to look genuine.
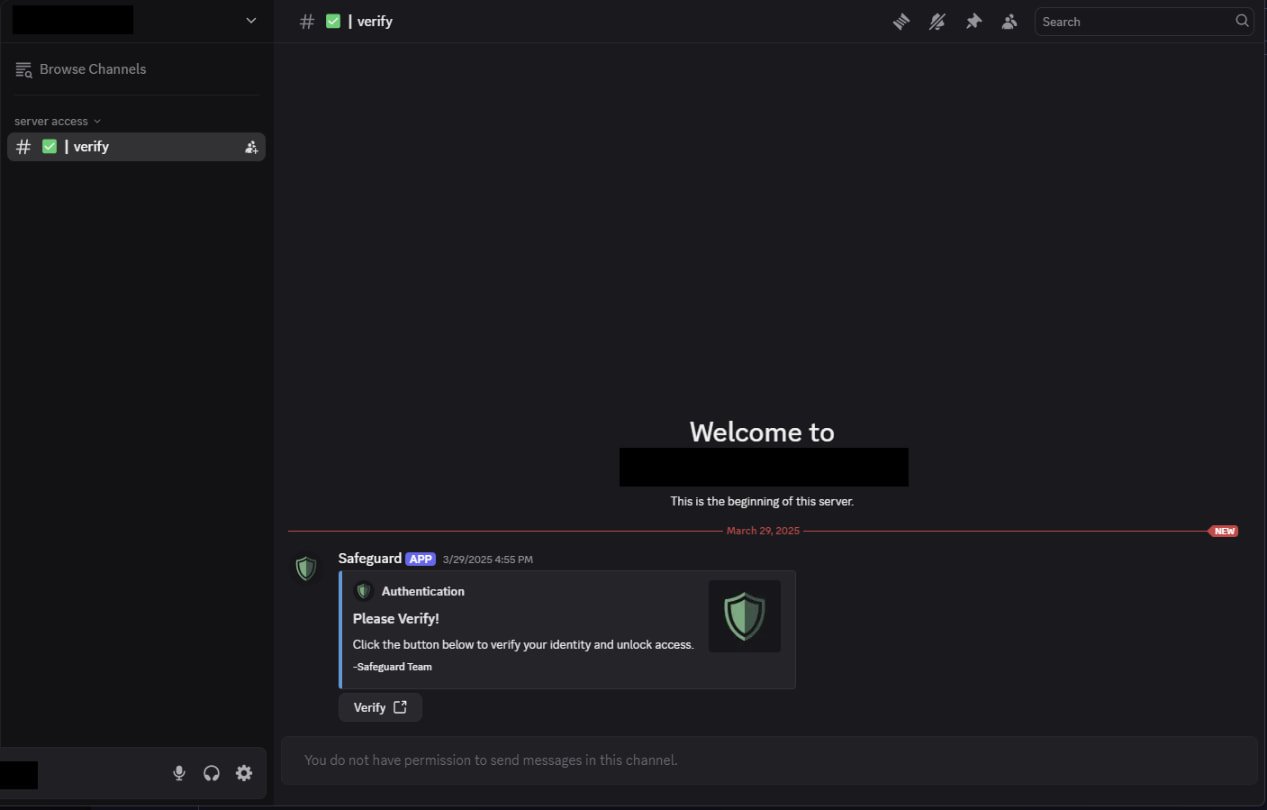
The malicious Discord servers solely present a single channel to the customer, #confirm, and a bot prompts the person to undergo a verification course of.
Supply: Verify Level
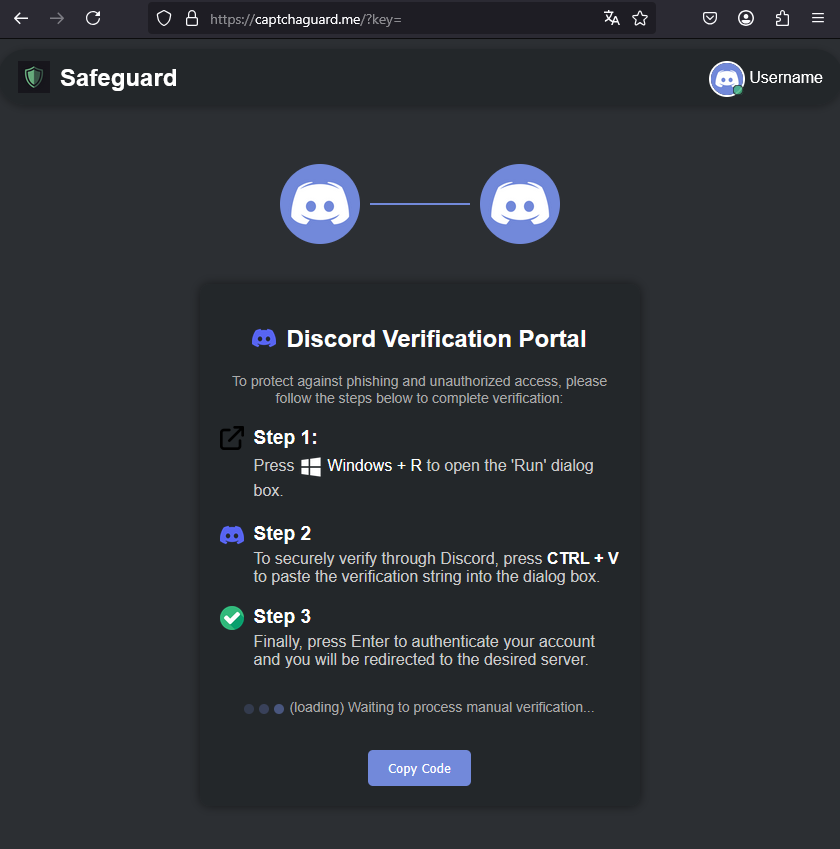
Trying to take action launches a typical ‘ClickFix’ assault the place the person is redirected to a web site that mimics the Discord UI and pretends that the CAPTCHA did not load.
The customers are tricked into manually opening the Home windows Run dialog and pasting a PowerShell command, which that they had already copied to the clipboard for execution.
Supply: Verify Level
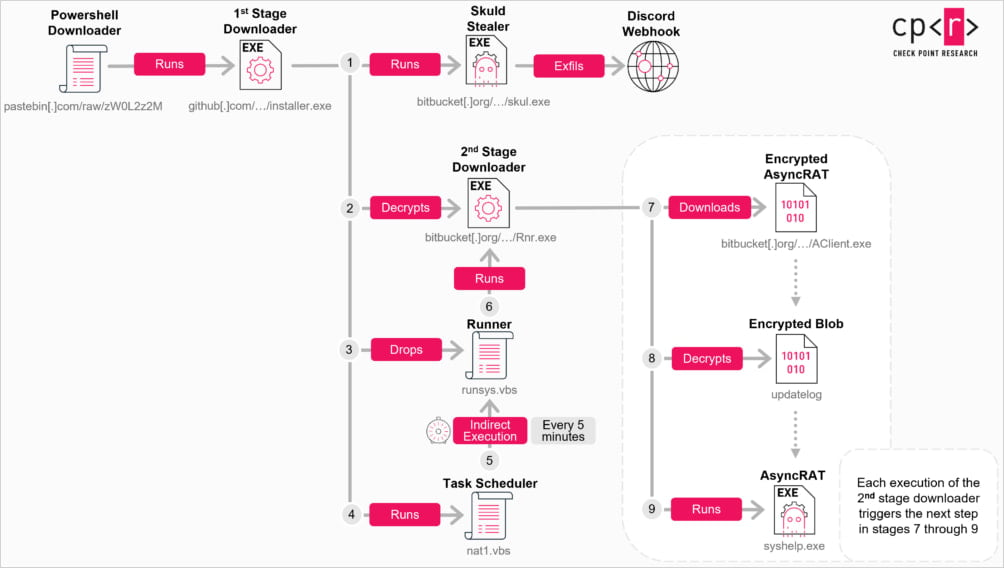
Doing so triggers a multi-stage an infection involving PowerShell downloaders, obfuscated C++ loaders, and VBScript information.
The ultimate payloads are downloaded from the reputable Bitbucket software program collaboration and file internet hosting service, and embrace:
- AsyncRAT: Delivered as ‘AClient.exe,’ that is model 0.5.8 of the malware that makes use of Pastebin to fetch its C2 tackle dynamically. Its capabilities embrace file operations, keylogging, and webcam/microphone entry
- Skuld Stealer: Delivered as ‘skul.exe,’ that is an info-stealer that targets browser credentials, cookies, Discord tokens, and cryptocurrency pockets information (injects JS to steal mnemonic phrases and passwords utilizing Discord webhooks)
- ChromeKatz: A customized model of the the open-source device, delivered as ‘cks.exe’, that may steal cookies and passwords
A scheduled job can be added on the host to re-run the malware loader each 5 minutes, the researchers found.
Supply: Verify Level
To defend in opposition to this risk, it is strongly recommended that Discord customers keep away from trusting previous invite hyperlinks, particularly these from months-old posts, deal with “verification” requests with additional warning, and by no means run copied PowerShell instructions that you do not absolutely perceive.
Moreover, Discord server directors are really useful to make use of everlasting invitations, that are tougher to hijack.
Patching used to imply complicated scripts, lengthy hours, and countless hearth drills. Not anymore.
On this new information, Tines breaks down how fashionable IT orgs are leveling up with automation. Patch quicker, scale back overhead, and deal with strategic work — no complicated scripts required.



