Segmentation has emerged as a foundational expertise for cybersecurity groups all over the world as a solution to cease threats from spreading laterally by way of the community, mitigate their influence and implement zero belief methods. Dozens of segmentation options have flooded {the marketplace} – all claiming the very best method for defining, figuring out and isolating particular workloads primarily based on conduct and id.
The evolution of segmentation has been swift – dizzying even. And prospects are having hassle breaking by way of the hype. What’s the finest segmentation method for my group? What resolution finest matches our wants? How can we measure and consider our segmentation technique? And the way does segmentation align with enterprise aims?
Consequently, we’re launching a brand new weblog collection particularly targeted on segmentation. Over the subsequent a number of months, we’ll discover use circumstances, challenges and methods so you may evaluate, deploy and handle segmentation options extra successfully throughout your numerous IT environments. We would like you to make knowledgeable choices – choices that improve total safety posture, assist more and more complicated compliance efforts and improve zero-trust safety fashions.
Segmentation is Evolving to Meet Safety Challenges within the AI World
Segmentation was developed a long time in the past as a solution to implement visitors administration and stop threats from shifting laterally throughout the community. Since then, as digital transformation, distributed computing and the cloud have modified the best way we work, segmentation has developed to permit safety groups to isolate particular workloads primarily based on conduct or id.
This capacity to implement micro-segmentation at scale has turn out to be foundational to trendy enterprise safety methods and the zero belief safety mannequin – enabling the containment of breaches, the enforcement of entry insurance policies and improved visibility throughout more and more complicated IT environments and risk panorama.
That is very true within the age of AI. At this time’s extremely refined threats can unfold laterally throughout the community in a matter of seconds, and static segmentation insurance policies are unable to reply rapidly to evolving threats. New AI-powered micro-segmentation options can pace response occasions immensely. Safety groups have taken discover, embracing these micro-segmentation instruments to cease assaults earlier than they’re able to unfold all through the community.
A Communication Downside for Distributors, Integrators and Clients
The evolution of segmentation has created an enormous ecosystem of assorted applied sciences, strategies, infrastructures and enforcement methods – contributing to a lot confusion within the market. Distributors and integrators use completely different phrases, push completely different approaches and make conflicting guarantees. The ensuing incapacity to absolutely grasp the subtleties of segmentation prevents organizations from having fruitful conversations round segmentation wants, challenges and options – finally placing segmentation tasks liable to failure or not realizing their full worth.
As cybersecurity threats proceed to develop in quantity, sophistication and influence, organizations are going to want to get a greater grasp of this foundational expertise to allow them to make higher choices according to enterprise aims and danger.
Let’s Agree on a Normal Taxonomy for Segmentation
Step one is to standardize how we speak about segmentation. A current paper printed at TechRxiv takes a primary stab at defining a typical taxonomy. Written by a Cisco colleague, the paper “introduces a taxonomy and shared vocabulary for discussing and evaluating segmentation approaches throughout real-world deployment contexts.”
Talking the identical language is essential as a result of it ensures that each one stakeholders are in settlement about what’s being mentioned and the way it’s being mentioned. When somebody makes use of a label, they’re assuming their subjective interpretation is similar because the viewers’s interpretation. If they don’t align, miscommunication can happen, resulting in confusion, disconnected expectations and, typically, harm emotions. Normal taxonomies be certain that everybody is talking the identical language, communication is clear and everyone seems to be aligned.
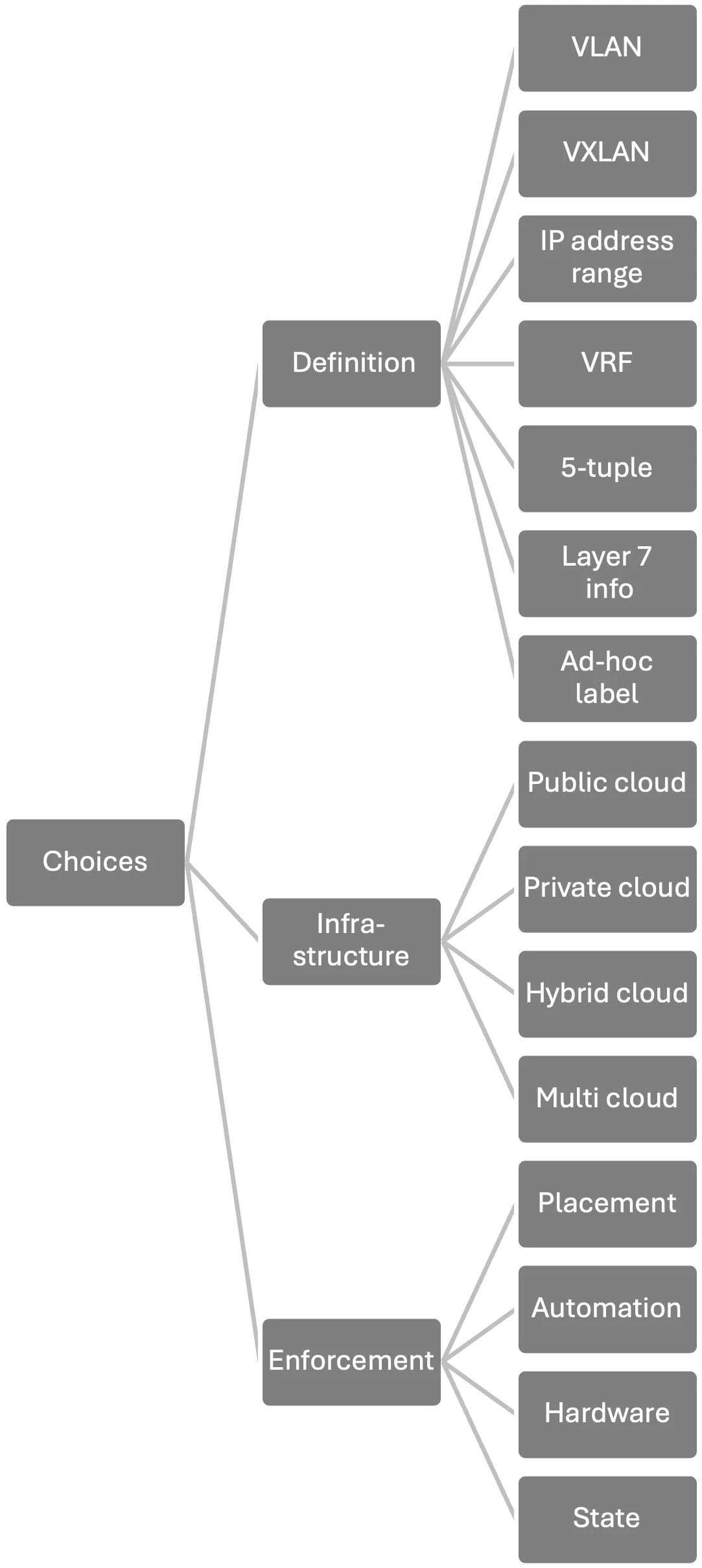
Given the speedy evolution of segmentation, its varied sorts and using jargon by distributors, segmentation is in determined want of a longtime taxonomy. Luckily, the TechRxiv paper does an incredible job of organizing segmentation taxonomy, separating phrases into three buckets:
- How Segments are Delineated: The way in which segments are outlined is a vital differentiation between segmentation sorts. For instance, utilizing VLAN IDs is taken into account macro-segmentation as every VLAN acts as its personal broadcast area. Utilizing 5-Tuples-based segments (the supply and vacation spot IP addresses, the supply and vacation spot port numbers and the protocol ID) works for each macro- and micro- segmentation.
- The Infrastructure Over Which Segmentation is Deployed: Segmentation additionally differs primarily based on the underlying infrastructure. This contains public cloud, non-public cloud, hybrid cloud and multi-cloud environments.
- How Enforcement is Carried out: The way in which segmentation is enforced additionally gives vital differentiation of segmentation sorts. Allowing and blocking visitors might be accomplished on the workload stage (container community interface), near it (top-of-rack switches) or away from it (knowledge middle firewall).

Offering Clients with Readability
Segmentation has developed right into a vital safety instrument that permits enterprises to isolate particular workloads primarily based on conduct or id – offering a stable basis for zero belief methods. Nevertheless, segmentation is a extremely fragmented market with quite a few methods to outline segments throughout a number of infrastructures with various enforcement strategies. Matching the precise instrument to every job would require all stakeholders to come back collectively to agree on a regular taxonomy for the expertise. Solely then will organizations achieve the readability they should align their segmentation tasks with enterprise aims.
I sit up for offering extra content material round segmentation in future posts. Within the meantime, take a learn of the TechRxiv paper.
We’d love to listen to what you suppose! Ask a query and keep linked with Cisco Safety on social media.
Cisco Safety Social Media


