Items, companies, and other people merely can not get to the place they’re wanted with out efficient logistics. Logistics are important to almost all elements of the financial system and nationwide safety. Regardless of this, numerous challenges can disrupt logistics from extreme climate and world pandemics to distribution bottlenecks. On this weblog publish we’ll give attention to cyber assaults to logistics choice fashions.
Nationwide safety and army organizations take into account contested logistics as “the surroundings through which an adversary or competitor deliberately engages in actions or generates circumstances, throughout any area, to disclaim, disrupt, destroy, or defeat pleasant pressure logistics operations, amenities, and actions.” For instance, in World Battle II, the Allied Transportation Plan included strategic bombing of main highway junctions, bridges, tunnels, rail traces, and airfields to hamper German actions to the Normandy space. This performed a decisive function within the success of the D-Day landings.
Whereas defending the bodily elements of logistics operations is essential, fashionable logistic programs additionally embrace in depth software-based choice assist that’s important to logistics planning phases, and this software program additionally have to be protected against assault.
Past basic cybersecurity, there are not any commonplace strategies for monitoring, detecting, and stopping cyber assaults to logistics choice fashions. Nonetheless, there are well-studied adjoining fields equivalent to synthetic intelligence (AI) safety, machine studying operations (MLOps), and extra broadly AI engineering that may contribute to the securing of our logistics choice fashions.
Hypothetical Assault to a Logistics Mannequin
Take into account a logistics mannequin that determines the right way to distribute provides to hurricane victims in Florida. We have to resolve the place to find provide storage amenities, in addition to how provides from every facility are to be distributed to surrounding populations.
Within the context of nationwide safety and army operations, situations would possibly embrace designing logistics programs to move gas, munitions, gear, and warfighting personnel from their originating places to the entrance traces of a battle. One other army use case is perhaps figuring out the optimum routing of automobiles, ships, and airplanes in a means that minimizes casualty danger and maximizes mission effectiveness.
Determine 1 illustrates utilizing a variation of the ok-center formulation to compute an optimum coverage for the Florida hurricane state of affairs (left panel). If a cyber-attacker had entry to this mannequin and was capable of modify its coefficients, then we would find yourself with a plan equivalent to depicted in the suitable panel. The really helpful central facility location has modified, which might degrade the effectivity of our hypothetical system, or worse, stop catastrophe victims from receiving wanted provides.
In a army battle, even seemingly refined adjustments like a really helpful facility location may very well be enormously damaging. For instance, if an adversary have been to have some functionality to assault or degrade a selected location unbeknownst to the defender, then manipulating the defender’s choice mannequin may very well be a part of an effort to bodily injury the defender’s logistics system.
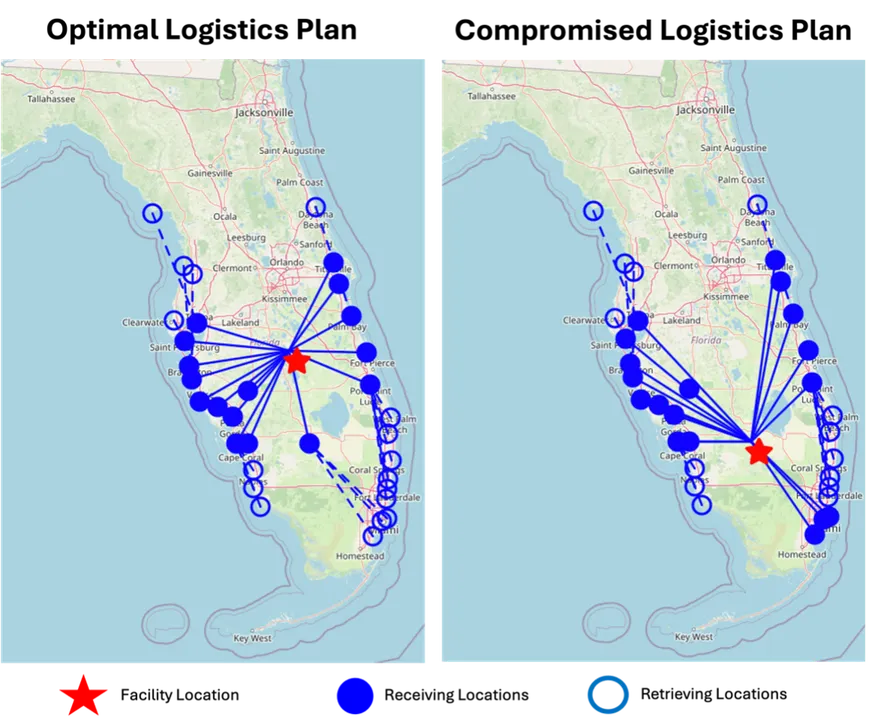
Determine 1: Hypothetical instance of how a cyber attacker would possibly subtly regulate mannequin parameters in such a means that the mannequin recommends suboptimal or in any other case unfavorable insurance policies.
In observe, logistics choice fashions could be extraordinarily giant. For instance, the small linear mannequin used for Determine 1 solves a system of 266 pages of linear equations, which Determine 2 depicts. If 100 places must be coated, the mannequin would have about 20,000 choice variables, about 40,000 constraints, and as much as about 800 million coefficients. Because of the downside of scale, practitioners typically use approximation algorithms that may generate fairly good insurance policies for his or her particular issues.
Determine 2: System of linear equations (266 pages) required to generate the optimum coverage in Determine 1. Realistically sized fashions are considerably bigger, and it will be simple for refined mannequin manipulations to go undetected.
There are various varieties of logistics issues, together with facility location, automobile routing, scheduling, machine task, and bin packing. Logistics issues are sometimes formulated as linear applications. Determine 3 reveals the overall type of a linear program, which (1) minimizes an goal operate (the vector of goal coefficients, c, multiplied by a vector of choice variables, x); (2) topic to a set of constraints (the constraint coefficient matrix, A, multiplied by the vector of choice variables, x, is the same as the constraint necessities vector, b); and (3) with the choice variables, x, taking over constructive values. Most logistics issues contain a variation of this mannequin known as a blended integer linear program, which permits a number of the choice variables to be integer or binary. For instance, a binary choice variable would possibly symbolize whether or not to open a provide depot (one) or not (zero) at a given location. Observe that Determine 3 is a compact (small) mannequin illustration, and its use of vectors and matrices ( c, x , b , and A ) can mannequin any sized downside (for instance with hundreds of choice variables, tens of hundreds of constraints, and thousands and thousands of coefficients).

Determine 3: Basic type of a linear program
George Dantzig invented the simplex technique in 1947 to unravel linear applications, that are so pervasive that the simplex technique is taken into account one of many nice algorithms of the twentieth century. Within the early 2010’s, it was estimated that 10-to-25 p.c of all scientific computation was dedicated to the simplex technique. At present, even with computing developments, fixing linear applications at-scale stays an unlimited problem.
In logistics observe, these fashions could be enormous. Not solely are they very tough to unravel, however they are often bodily not possible to unravel with present computing expertise. At present, a lot of the operations analysis discipline is dedicated to growing approximation algorithms that yield top quality (though not essentially optimum) options to real-world logistics issues. Latest analysis (see right here and right here) offers examples of such approximation algorithms. As a result of these mathematical applications are sometimes NP-hard (i.e., the issue measurement grows exponentially, and optimum options can’t be generated in polynomial time), optimization is without doubt one of the promising use circumstances for quantum computing.
Discrete occasion simulation and system dynamics are additionally modeling kinds used to unravel logistics issues. Whereas we talk about linear programming as an exemplar mannequin kind on this weblog, different mannequin kinds could be equally susceptible to cyber assaults.
Idea of Operations
There’s little revealed analysis, and even working expertise, concerning cyber assaults on logistics choice fashions. An assault would require undetected community intrusion; persistence to permit reconnaissance on the goal mannequin and assault planning; adopted by mannequin or knowledge manipulations which might be sufficiently subtle to be undetected whereas strategic sufficient to be damaging.
In observe, a profitable assault would require a complicated mixture of abilities probably solely accessible to motivated and skilled menace teams. Such menace teams do exist, as evidenced by intrusions into U.S. essential infrastructure and expertise enterprises like Google.
The Cyber Kill Chain developed by Lockheed Martin is a 7-step mannequin of how refined cyber assaults are sometimes carried out. The seven steps are: reconnaissance, weaponization, supply, exploitation, set up, command and management, and at last appearing on the attacker’s goals. Attacking a choice mannequin would equally require these steps to ascertain a persistent community intrusion, entry to the mannequin, and at last manipulate the mannequin or its output.
As soon as attackers acquire entry to a logistics mannequin, the injury that they will inflict relies on many elements. Like AI safety, a lot relies on the kind of entry gained (e.g., mannequin read-only entry, mannequin write entry, coaching knowledge read-only entry, coaching knowledge write entry, capacity to exfiltrate a duplicate of the mannequin or knowledge, and so on.). Not like many AI functions, logistics typically introduces sprawling provide chains of contractors and subcontractors. If an higher echelon choice mannequin relies on knowledge from organizations at decrease echelons within the provide chain, then the mannequin might conceivably be attacked by poisoning knowledge in programs past the mannequin operator’s management.
Suggestions for Securing Logistics Choice Fashions
We name on the logistics, cybersecurity, and operations analysis communities to systematically examine the susceptibility of choice fashions to cyber assault and to offer formal suggestions for a way greatest to guard these fashions.
Within the meantime, there are well-studied adjoining fields that supply present logistics mannequin operators alternatives to enhance safety. For instance, machine studying operations (MLOps) is a scientific framework for making certain dependable deployments into manufacturing environments. Extra broadly, the SEI is main the Nationwide AI Engineering Initiative, which systematizes what is required to develop, deploy, and preserve AI programs in unpredictable and chaotic real-world environments. Monitoring is a central tenet of MLOps and AI engineering, together with strategies to establish important mannequin and knowledge adjustments between revisions.
Lastly, we suggest that AI safety organizations take into account logistics choice fashions inside their purview. The linear programing that underpins logistics fashions shares many attributes with AI: each could be huge scale, compute intensive, depend on knowledge, and be tough to interpret. Like AI, assaults to logistics choice fashions can create important, real-world injury.


